Risky Biz News: New hacker extradition battle begins between the US and Russia
In other news: Ukrainian hackers brick Russian satellite internet operator DoZoR; CyberCom doubles the size of its Under Advisement team; and new npm manifest confusion attack spells major trouble.
This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Authorities in Kazakhstan have decided to kick a hornet's nest and arrested Nikita Kislitsin, the top executive for Russian cybersecurity firm FACCT—the former Russian branch of Group-IB, which split from its parent company earlier this year.
Kislitsin was detained following an international arrest warrant issued by the United States. US authorities are seeking his extradition in relation to a case where he's accused of selling login credentials for Formspring accounts way back in 2012.
All of this happened on June 22. Six days later, on June 28, a Moscow court issued an arrest warrant in absentia in Kislitin's name on some mysterious hacking charge. No details provided.
Now, Russian authorities are seeking Kislitsin's extradition to Russia in what appears to be the start of another diplomatic tug-of-war between US and Russian officials over yet another suspected cybercriminal.
We've seen this before many times. Every time a big Russian hacker gets arrested outside Russia's borders, Russian authorities hocus-pocus some charges out of a hat and try to get him back home like the suspects are some sort of national treasure.
It happened before with Yevgeniy Nikulin, the Russian national behind the hacks of Dropbox and LinkedIn. As soon as Nikulin was detained in Czechia, Russian authorities also realized he was a dangerous hackerm@n and sought his extradition too. This one they lost.
It also happened with Alexander Vinnik, the founder of e-BTC, a cryptocurrency platform that was at the heart of many ransomware payments in the mid-2010s. As soon as Vinnik was detained in Greece, Russian authorities had an epiphany and realized what a dangerous cyberlord Vinnik was and also sought his extradition. This one they initially won, but they lost on the appeal.
It also happened with Aleksei Burkov, the administrator of the CardPlanet carding forum. As soon as Burkov was detained in Israel, Russian officials also sought his extradition in their own hacking case. Russian officials went as far as arresting and sentencing an Israeli woman to seven years in prison on drug-related charges and offering to release her in a prison swap with Burkov.
It also happened with Pyotr Levashov, the Russian national behind the Kelihos botnet. As soon as he was detained in Spain, someone in Russian law enforcement realized he hacked a Russian hospital years before and immediately sought his extradition—even if Levashov said in court he was working with the FSB.
And stuff like this has been happening for years, even as far back as 2012, with Dmitry Zubakha, who was accused of launching DDoS attacks on Amazon and eBay. As soon as Zubakha was detained in Cyprus, Russian authorities waved their wand, made some criminal case appear out of the blue, filed an extradition request, got Zubakha extradited to Russia, and then gave him a suspended sentence.
It's stuff like—"oh, we totally forgot we were prosecuting him too"—that makes it hard to believe that Russian authorities actually have a case against Kislitin.
We're not here to say Kislitsin is guilty. Group-IB and its new Russian incarnation FACCT have both pointed out Kislitin was working as a journalist and security researcher when all of the stuff in the US indictment happened. We're just pointing out that Kislitsin's case in Russia may just be made up.
The most interesting part in this extradition battle isn't actually the case, but if Kazakhstan, a former Soviet republic, will extradite Kislitsin to the US.
Earlier this year, Georgia, another former Soviet republic, broke an invisible line and arrested and extradited a Russian national accused of creating the NLBrute hacking tool to the US. That case came out of the blue and didn't give Russian officials time to react and hocus-pocus a counter-extradition claim. Russia was also busy with some stuff in Ukraine.
If the US manages to extradite another Russian national from a former Soviet republic, things are about to get very interesting in the Russian-speaking cybercrime underground.
Dmitry Smilyanets, director of product management at Recorded Future, says the arrest has already caused some waves, with some calling the arrest a "betrayal" and "backstabbing."
Russian-speaking groups often considered the former Soviet space to be their back garden and a safe space. All of a sudden, the back garden got a lot smaller.
Breaches, hacks, and security incidents
Themis cyber-heist: A threat actor has used a prophecy machine manipulation attack to steal $370,000 worth of crypto-assets from DeFi platform Themis. The hack took place less than two weeks after the project launched. The company is now trying to "work with the hacker" to get some of the stolen funds back.
USPTO data leak: The US Patent and Trademark Office (USPTO) has confirmed it inadvertently exposed the home addresses of almost 61,000 patent filers. The leak occurred following a misconfiguration in one of the agency's APIs. The API endpoint was being used by the USPTO staff and filers to check the status of pending trademark registrations. The leak lasted from February 2020 to March 2023, when the agency discovered and fixed the issue. [Additional coverage in TechCrunch]
Let's Encrypt incident: Let's Encrypt says it found a bug in one of its new systems that led to the incorrect issuances of 645 certificates. Everything has been revoked and fixed. More on this here.
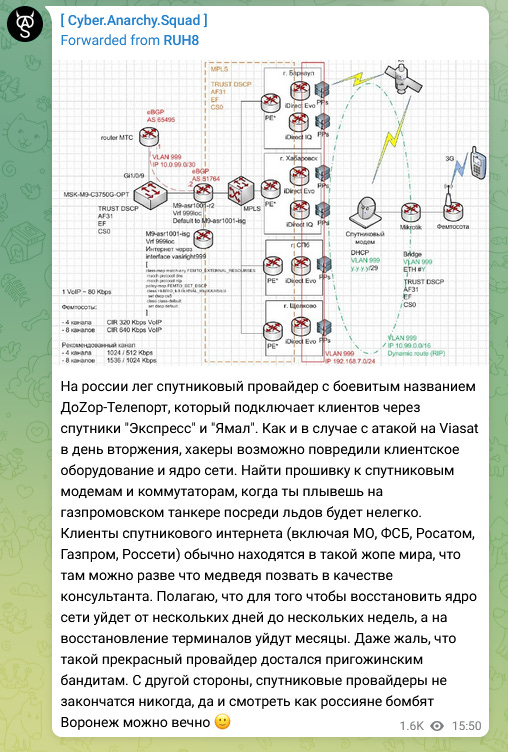
DoZor-Teleport hack: Ukrainian hacking group CyberAnarchySquad says it hacked the network of Russian satellite communications provider DoZor-Teleport. The group claims it destroyed network servers and bricked some of the company's satellite modems. It also stole and leaked more than 700 documents from DoZoR's network. The incident has not been confirmed by either DoZor or Russian authorities, but the company's network went offline for 14 hours on Thursday, June 29. According to the DoZoR website, the company provides internet satellite connectivity to some of Russia's largest organizations, such as Gazprom, Rosatom, the FSB, and the Moscow regional government. CyberAnarchySquad is the same group that hacked and trashed the network of Russian telco Infoteal earlier this month. Infotel needed an entire week to rebuild its network. [Additional coverage in CyberScoop]
General tech and privacy
Brave blocks localhost scanning: Brave Software has announced that version 1.54 of its browser will block websites from running scans of local resources, also known as localhost scanning. The technique has been used by online advertisers to fingerprint users. It has also been used by threat actors to discover locally accessible devices and run exploits that compromise equipment such as routers and switches.
e-Tugra CA removed from Chrome: Google has removed Turkey-based certificate authority e-Tugra from the Chrome root store. Websites that use the company's certificates will be shown an error message when loaded inside Chrome and ChromiumOS. The removal comes after security researcher Ian Carroll disclosed a series of misconfigurations in the company's server infrastructure. Carroll said the misconfigured servers could have allowed a threat actor to get access to the company's backend systems and issue new certificates or steal highly-sensitive customer data. Mozilla is also considering removing the company from its root store. Apple never included the company's certificates in its root store.
NZ internet issues: An apparent "routine" DNSSEC key rollover event triggered a widespread outage for New Zealand (.nz) domains at the end of May. The incident caused resolution failures for NZ domains for 13 hours. A post-mortem of the entire incident is here.
WeChat privacy: A CitizenLab report looks at the privacy-related issues in WeChat, China's largest social media app. The report finds that WeChat collects way more usage data than what they disclose in their privacy policy.
Government, politics, and policy
Russia working on white-hat protections: Russia's Council for the Development of the Digital Economy has asked the Russian Ministry of Digital Development to start working on a bill that would provide legal protections for white-hate security researchers and bug bounty hunters. [Additional coverage in TASS]
CyberCom doubles Under Advisement program: US Cyber Command is set to double the size of an internal team named Under Advisement. Established ahead of the 2020 US Presidential Election, the team has worked with the private sector on cybersecurity topics. Through the years, CyberCom has called the team its "canary in the coal mine" unit as it allowed it to get early warnings on various cyber threats. The team has also helped the private sector confirm attacks carried out by foreign adversaries. According to a report from The Record, the team will grow from a dozen to two dozen people by this time next year.
FY 2025 budget: The White House has announced its cybersecurity priorities for the 2025 budget [PDF]. The Biden administration has asked government agencies to prioritize spending on five areas of interest. These are the same five pillars included in its National Cybersecurity Strategy document, published earlier this year. Agencies are encouraged to prioritize cybersecurity spending budgets on defending critical infrastructure, disrupting threat actor infrastructure, investing in a cybersecurity workforce, using government contracts to shape the cybersecurity market, and the forging and support of international partnerships. [Additional coverage in CyberScoop]
New CISA&NSA guidance: CISA and the NSA have issued another joint security advisory. This one is how companies can secure their DevOps CI/CD environments. CI/CD stands for Continuous Integration / Continuous Delivery, a very common method of writing, building, and delivering apps to customers in today's app landscape. It's basically everywhere and has a lot of moving parts, which makes exploiting it very easily and defending it very hard—just what threat actors like.
Sponsor section
In this sponsored Soap Box podcast, Patrick Gray talks to Airlock Digital co-founders Daniel Schell and David Cottingham about living off the land. The recent Volt Typhoon report out of Microsoft chronicled the adventures of a Chinese APT crew in US critical infrastructure. But one of the most fascinating aspects of the Volt Typhoon campaign was that the attackers almost exclusively used so-called living off the land techniques.
Cybercrime and threat intel
Scam centers dismantled in the Philippines: Philippine police and military commando forces have raided two locations across the country and freed more than 2,700 Filipino and foreign nationals who were forced to work for cybercrime cartels. The raids freed individuals in the cities of Las Pinas and Mabalacat. The workers were forced to carry out cryptocurrency scams, online gaming schemes, and other types of online fraud. The raid marks the first major action across the ASEAN region against criminal cartels and their recent involvement in online fraud schemes known as "pig-butchering." [Additional coverage in the Associated Press]
Project DDoSia: Sekoia has published a summary of Project DDoSia, a program run by the NoName057(16) pro-Kremlin "hacktivist" group that rewards users with cryptocurrency for installing its app and participating in DDoS attacks against the evil West.
Manic Menagerie: PAN's Unit 42 has an update on Manic Menagerie, a threat actor that hijacks web servers for crypto-mining operations. The group has been active since 2018 and was previously documented by the ACSC [PDF].
Q2 2023 spam report: The VirusBulletin spam report for Q2 2023 is out.
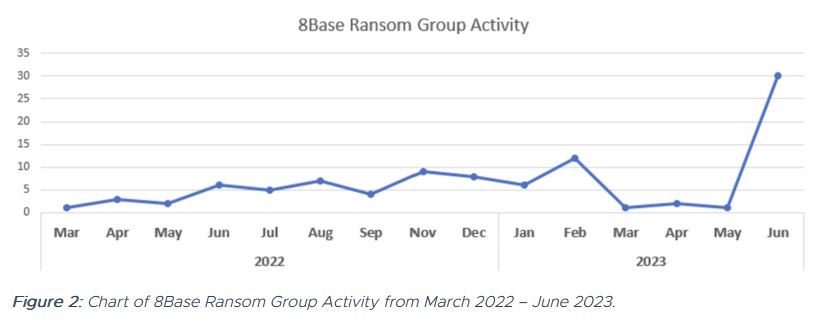
8Base ransomware: The number of attacks and extortions carried out by the 8Base ransomware group has more than doubled in June 2023, making the gang one of today's major players. The group has been operating since March 2022 and now has over 80 victims listed on its dark web leak site, 35 of which were added this month. The figure puts 8Base as the second most-active ransomware gang behind LockBit. Carbon Black researchers believe that based on its ransom notes, the gang may be an offshoot or have some sort of connection to the RansomHouse group.
Malware technical reports
Nothing in this edition. There are actually some malware reports, but they're all APT tools, so we included them in the APT section below.
Risky Business Demo
Airlock Digital is one of this newsletter's supporters and this week's featured sponsor. Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
Kimsuky: AhnLab researchers say they've spotted the Kimsuky North Korean APT install the Chrome Remote Desktop utility in a recent intrusion as a way to control an infected system.
Andariel's EarlyRAT: Kaspersky researchers say that while investigating attacks carried out by the Andariel North Korean hacking group, they discovered a new malware family operated by the group and named EarlyRAT. The malware joins the ranks of previously known Andariel tools such as DTrack, NukeSped, YamaBot, MagicRat, and the Maui ransomware.
Lazarus' Smooth Operator: The UK NCSC has published a technical analysis of Smooth Operator [PDF], the macOS malware used in the 3CX supply chain attack conducted by the Lazarus APT.
Lazarus zero-day campaign: The South Korean National Intelligence Service (NIS) has confirmed that at least 50 local organizations have been hacked by the Lazarus North Korean hacking group. The intrusions have been taking place since the end of 2022, and the victims were compromised using a remote code execution zero-day vulnerability in the MagicLine4NX certificate authentication software. Officials didn't name any of the victims but said that media organizations and public institutions were compromised. NIS has asked Korean organizations to either update or delete the app from their systems. Korea's CERT team has linked the attacks to a Lazarus operation known as GoldGoblin. This is the fourth zero-day in South Korean software exploited by Lazarus hackers over the past year. They previously also exploited zero-days in INISAFE CrossWeb EX, VestCert, and TCO!Stream.
MuddyWater's PhonyC2: DeepInstinct says that Iranian cyber-espionage group MuddyWater has adopted the PhonyC2 command-and-control framework for its recent operations. These included the exploitation of PaperCut NG servers.
Charming Kitten's POWERSTAR: Volexity says Iranian APT group Charming Kitten has updated its POWERSTAR malware to use the InterPlanetary File System (IPFS) protocol for its delivery. This marks the first major APT to adopt IPFS for operations. The protocol has been primarily used to host blockchain technology and was previously adopted by phishing gangs and ransomware operators throughout 2021 and 2022.
Vulnerabilities, security research, and bug bounty
ArcServe: MDSec researchers have published details and information to craft a PoC for an auth bypass and RCE in the ArcServe UDP Backup solution. The vulnerability is tracked as CVE-2023-26258.
Netskope vulnerability: HWD Sec has published details about an LPE in the Netskope client—tracked as CVE-2023-2270.
Linux lateral movement: Akamai delves into all the protocols and techniques that can be abused for lateral movement on Linux.
Manifest confusion attack: The npm ecosystem is vulnerable to a new attack named manifest confusion. Discovered by former GitHub engineer Darcy Clarke, the attack allows threat actors to create npm packages that list clean dependencies but secretly load and execute malicious content when installed. Clarke says threat actors can upload a "clean" version of the package.json manifest file to the npm[.]com website but place a different file in the library's TAR archive. The issue is that these two manifest files are never compared and validated against each other, creating a blind spot for developers and their security tools. Clarke says GitHub has known of this issue since November 2022 but has yet to mitigate it.
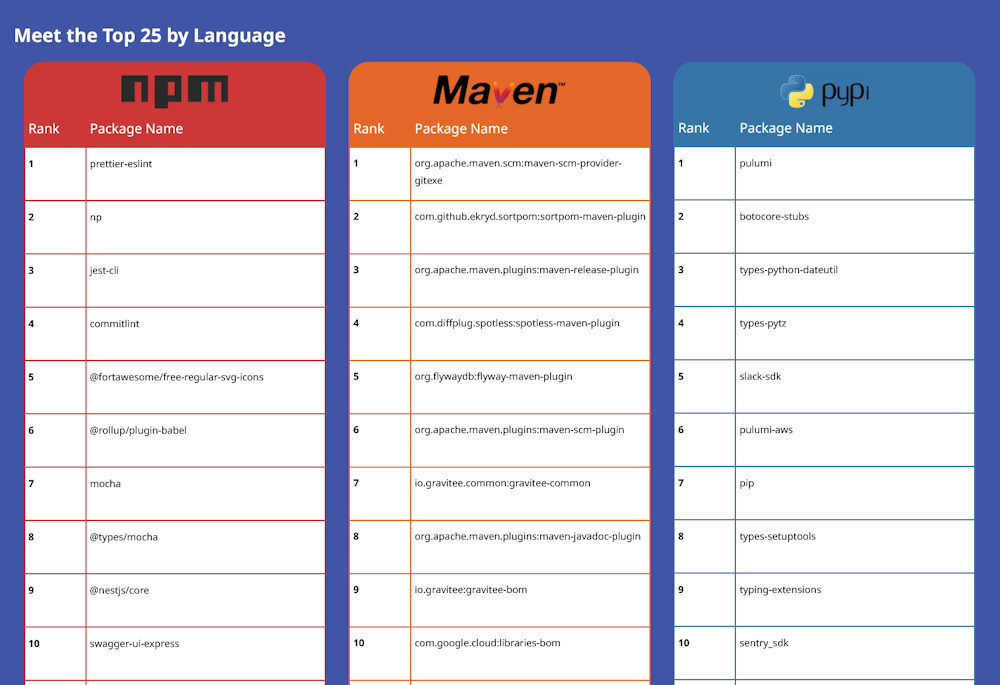
Reliability Top 25: Unlike most research featured in this section, the team at Mend built a ranking for the most reliable libraries on the npm, Maven, and PyPI repositories. These are packages that often receive updates, see active development, use other reliable packages as their dependencies, and are broadly used across their respective ecosystems. We often feature news about the bad packages, so we thought we feature something good for once.
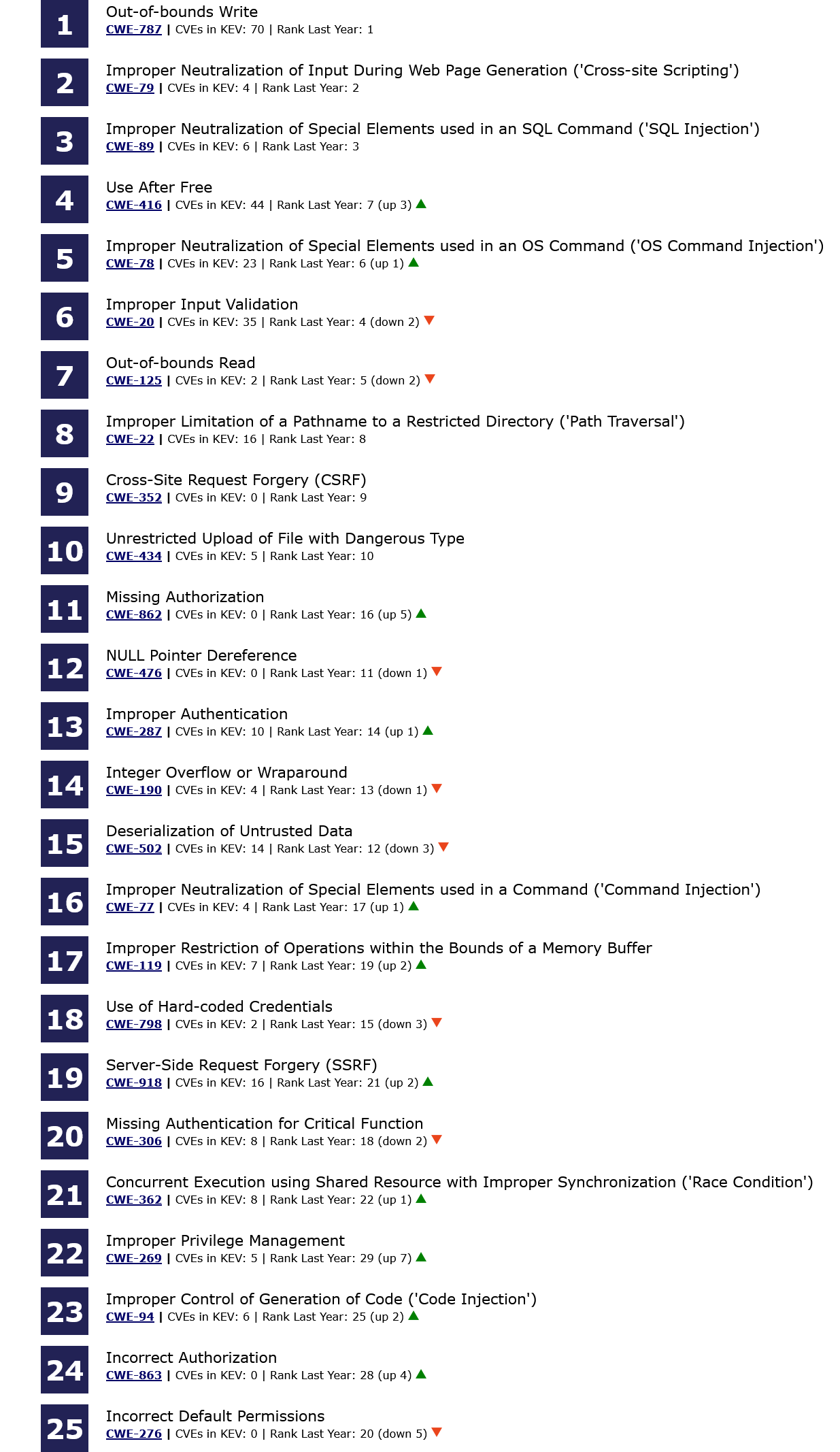
MITRE Top 25 Most Dangerous Vulnerabilities: MITRE has published the 2023 edition of its CWE Top 25 most dangerous vulnerability list. The CWE Top 25 is calculated by analyzing public vulnerability data for the root cause of reported vulnerabilities in the previous two years. While some CWEs have moved up and down, the top three entries on this year's list are the same as last year.
Infosec industry
Acquisition news: Secure infrastructure company HashiCorp has acquired source code security app BluBracket.
"BluBracket's secrets-scanning functionality will complement HashiCorp Vault's secrets management to help prevent accidental leaks and fight secret sprawl."
New tool—TaSK: Germany's cybersecurity agency BSI has open-sourced a new tool named the TaSK that can test TLS conformity based on the agency's own TLS security implementation guidelines.
New tool—Surf: Cybersecurity firm Assetnote has open-sourced Surf, a tool that can be used to identify cloud servers that may be vulnerable to SSRF vulnerabilities.
Sysmon 15 is out: Microsoft has released v15.0 of its advanced host security monitoring tool Sysmon. The new release configures the Sysmon service to run as a protected process, hardening it against tampering. It also adds support for a new detection event named FileExecutableDetected. This new event can allow Sysmon to detect when new executable files are created on disk, which should be useful for detecting stuff like second-stage payloads being dropped on an infected host. More on this here.
Risky Business Podcasts
In this podcast, Patrick Gray and Tom Uren talk about the US Securities Exchange Commission warning SolarWinds executives that it is planning to bring enforcement actions against them. This is a big deal and really signifies that the SEC wants companies to be much more open about cybersecurity incident disclosures.