Risky Biz News: Santa's here with a bunch of bad news for LastPass and Twitter users
In other news: AT&T exonerates itself from any responsibility in SIM-swapping attacks; BitKeep wallets drained in supply chain attack; TikTok banned on federal networks and lawmakers' devices.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Risky Business team is still on its holiday break, but we thought to put out this weekly edition with some of the past week's biggest infosec stories.
Happy holidays!
Breaches and hacks
LastPass breach: The day after our last newsletter and just ahead of the Christmas holiday, LastPass updated the blog post about its August security breach to add a bunch of bad news. The new text is full of PR misdirections, but translated, the company effectively admits it didn't contain the August intrusion, and since then, the threat actor moved laterally across its network and managed to gain access to a cloud server where the company was storing its users' encrypted password vaults. Yes, your LastPass password vaults are gone, and it's apparently pretty easy to brute-force them if your master password is weak. Sigh! Lots of this is LastPass' fault, btw.
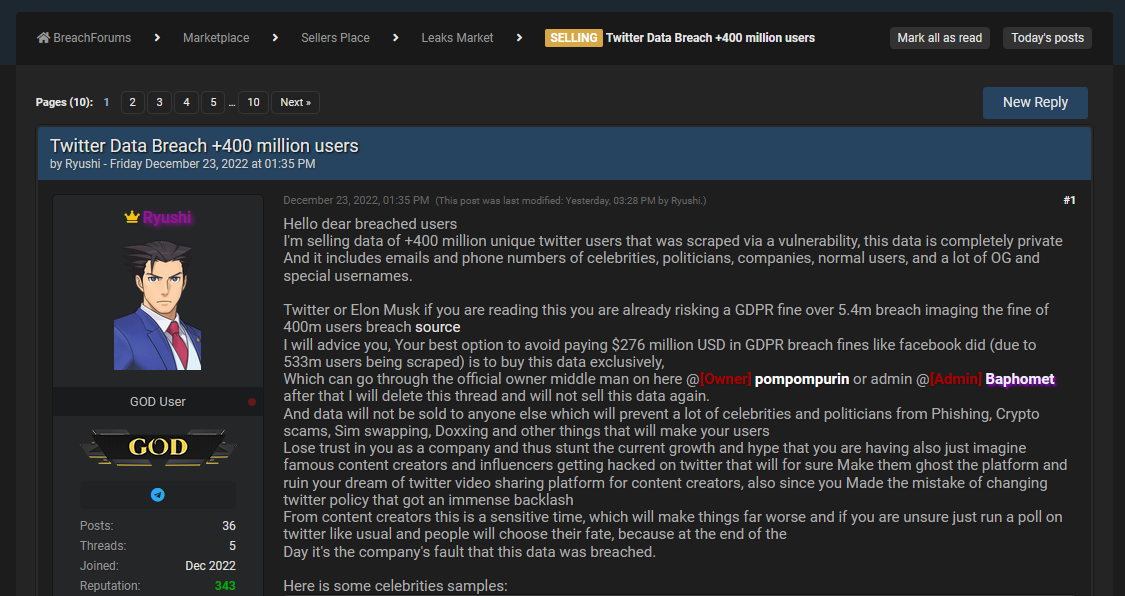
Twitter breach: But that wasn't all of it. On Christmas day, news emerged that a threat actor was selling the personal details of more than 400 million Twitter users. The threat actor said the data was compiled earlier this year by scraping the Twitter API for private account information, such as account stats and phone numbers. Twitter has refused to acknowledge the incident, and the company has applied "context notes" on some of the more popular tweets sharing the bad news, claiming the data comes from an incident it confirmed last month and which only affected 5.4 million users. In the meantime, several people have come out to say that the data sold on Breached is legitimate and that big. A friendly piece of advice is to either change your Twitter-associated phone number or disable SMS-based 2FA and use an authenticator app only for logging into Twitter (if you still use that ring-wing, QAnon, and Kremlin propaganda cesspool).
BitKeep wallet crypto-heists: Cryptocurrency wallet app BitKeep confirmed that hackers modified some of its Android APK files and deployed malicious code on the devices of some of its customers. Losses from this incident are estimated at around $8 million worth of crypto assets.
BTC.com crypto-heist: Cryptocurrency mining pool BTC.com said it was the victim of a cyber-attack that took place at the start of the month.
"In the cyberattack, certain digital assets were stolen, including approximately US$700,000 in asset value owned by BTC.com's clients, and approximately US$2.3 million in asset value owned by the Company."
Defrost Finance crypto-heist: DeFi platform Defrost Finance was the victim of a flash-loan attack. Losses are estimated at $12 million, but the hacker returned the funds after three days.
Rubic crypto-heist: Cross-chain cryptocurrency platform Rubic was also hacked and lost $1.41 million worth of crypto assets. The company confirmed the incident and promised to refund affected users.
Comcast Xfinity account hacks: Several Comcast Xfinity customers said they had their accounts hacked. The accounts were then used to reset passwords and bypass 2FA accounts on cryptocurrency portals like Gemini and Coinbase. [Coverage in BleepingComputer]
RansomHouse claims Vanuatu: The RansomHouse ransomware cartel has claimed the ransomware attack that crippled the network of the Vanuatu government for the past few weeks.
49ers CLA: The San Francisco 49ers NFL team has been sued in a class-action lawsuit for not properly disclosing in a breach notification that they suffered a ransomware attack and that some of their employee and customer PII data might have been exposed and leaked online on the dark web.
General tech and privacy
AWS S3 new defaults: After a quatrabazillion incidents where customers accidentally left S3 buckets exposed on the internet and leaked their companies' sensitive data online, the super-geniuses at AWS have finally decided to change the S3 defaults from open to "block public access." This will become the default policy for all new S3 buckets in April 2023, meaning that if you want the content of your S3 bucket to be publicly accessible, you will have to deploy an ACL rule to make it so.
TikTok spied on journalists: Chinese social media giant TikTok has confirmed that it spied on the real-time location of Forbes journalists who reported on the company in the hopes of identifying some of their sources. [Non-paywall version here]
AT&T legal shenanigans: AT&T has updated its terms of service to exonerate itself in the case of unauthorized access to customer accounts that took place because of "negligence by an AT&T employee, representative, agent, or any person or entity purporting to act on AT&T's behalf." If you don't get what this is about, it's AT&T shielding itself from any responsibility in the case of SIM-swapping attacks, many of which are being carried out with the help of AT&T insiders.
Microsoft fined: French privacy watchdog CNIL has fined Microsoft €60 million for not having a mechanism in place on the Bing search engine through which users could easily refuse tracking cookies as easily as accepting them.
Government, politics, and policy
Japanese police and LockBit: Japanese press is reporting that Japan's National Police Agency has been successfully decrypting networks encrypted with the LockBit ransomware all year.
TikTok banned on US federal devices: The US government has banned federal employees from installing the TikTok app on government devices. So has the US House of Representatives, meaning US lawmakers won't be allowed to install the app on their government-provided devices.
International Counter Ransomware Task Force: An international task force focused on going after ransomware gangs is set to become active in January 2023. The new task force was announced at the second edition of the International Counter Ransomware Summit that took place in November this year and will be led by Australia.
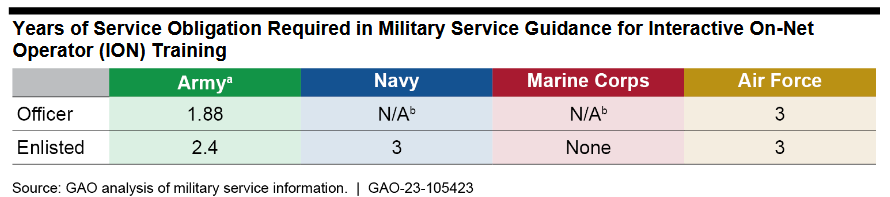
DOD cyber skill exodus: A GAO report has found that "military personnel who complete advanced cyber training—which may take a year or more and costs DOD hundreds of thousands of dollars—may not remain in the military for a significant time after training."
"We found that 2 of the 4 military services are not positioned to ensure adequate return on their investment in advanced cyber training. While the Navy and Air Force require 3 years of active duty, the Marine Corps has no guidance for this area and Army guidance does not clearly define active duty service obligations."
Sponsor section
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.
Cybercrime and threat intel
ShinyHunters extradition: Moroccan authorities have approved the extradition to the US of Sebastien Raoult, a French national suspected of being "Sezyo," a member of the ShinyHunters hacking group. Raoult was detained earlier this year at the airport in Rabat, Morocco, while trying to take a flight to Brussels, Belgium.
Robin Hood stuff: Ukrainian cybersecurity expert Alex Holden claims to have hacked Solaris, a dark web drugs market serving the Russian community, and stolen more than $25,000 worth of cryptocurrency from its users and administrators. Holden told Forbes he donated the stolen funds to charity organizations helping Ukrainians affected by Russia's invasion. [Non-paywall version here]
"Highly profitable trading strategy" hacker detained: The US has charged and detained cryptocurrency trader Avraham Eisenberg, an individual who exploited the Mango Market cryptocurrency platform in what he described as a "highly profitable trading strategy." Mango Market went insolvent after his "trades." Obviously, Mango Market and DOJ officials didn't view his "trading strategy" that way.
New spyware vendor: Reporters from Israeli news outlet Haaretz have a profile on a new surveillance vendor. Named Toka, the company was founded by former Israeli PM Ehud Barak and provides clients with the ability to hack cameras and change their video feeds.
WordPress attacks: A threat actor is using a vulnerability in a WordPress gift card plugin (YITH WooCommerce Gift Cards Premium) to hack and take over WP sites, per Wordfence. The plugin is installed on roughly 50,000 sites, and a security update is available for it.
New IcedID attacks: Trend Micro has a report out on IcedID's new distribution tactics—of using malvertising (Google pay-per-click [PPC] ads) to redirect users to malicious sites hosting IcedID-laced files, usually fake app installers. The campaign has been active since the start of December and is one that triggered the FBI to send out a PSA about this wave of attacks a few weeks back.
MasquerAds: On the same note, Guardio Security also has a report out on another malvertising campaign using Google ads to redirect users to malicious websites peddling fake installers, this one boobytrapped with the Vermux malware. This is a trend, apparently, and other malware gangs are doing it too.
PureLogs campaigns: A new Malware-as-a-Service called PureLogs launched in the cybercrime underworld, and campaigns distributing its payloads have already been seen in the wild, targeting Italian users, per Symantec.
FIN7 report: By far, the best infosec report of last week is Prodaft's analysis of the FIN7 cybercrime cartel. The report covers the gang's membership, various tools, and internal chat logs, including conversations where the FIN7 leaders threaten to hurt their members' family members in case any of them want to leave their "enterprise."
"Another shocking revelation clearly indicates that the group members are not always on good terms among themselves. It has been exposed that the administrator of the group threatens the team members by insisting that they have to work more while giving them ultimatums or even threatening to hurt their family members in case of resigning or escaping from responsibilities."
Malware technical reports
PolyVice ransomware: SentinelOne has put out a report on PolyVice, a new ransomware strain variant that has been used in recent attacks carried out by the Vice Society ransomware group.
Play ransomware: Fortinet researchers have a technical breakdown of the new Play ransomware operation.
Shlayer: Confiant's Taha Karim has a report on a new variant of the Shlayer macOS malware.
Eternity Stealer: Chinese security firm Antiy Group has a report out on the new Eternity infostealer. If you're looking for English-language coverage on this, check out CloudSEK's report from earlier this month.
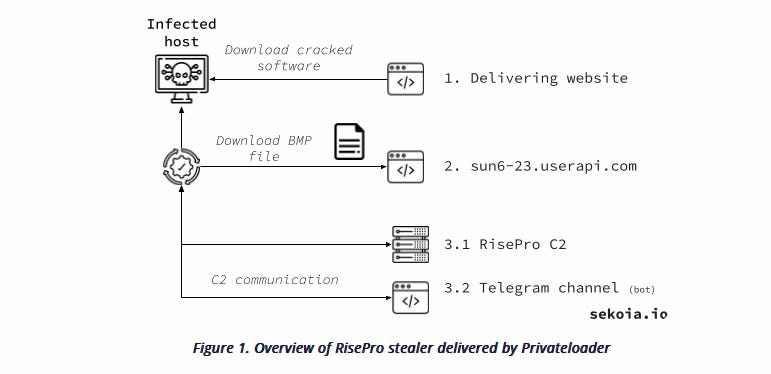
RisePro: Sekoia has a technical breakdown of RisePro, a new infostealer trojan spotted being advertised in underground cybercrime forums by Flashpoint. Per Sekoia, RisePro is currently being deployed as a second-stage payload on systems infected with the PrivateLoader malware.
APTs and cyber-espionage
NK crypto-heists: NIS, South Korea's main intelligence agency, estimated that North Korean hackers stole roughly $1.2 billion worth of cryptocurrency funds over the past five years, with $626 million stolen in 2022 alone. [Coverage in the Associated Press]
North Korean APT campaigns targeting NFT users: SlowMist researchers have published a summary of a large-scale phishing campaign targeting NFT owners that appears to have been carried out by a North Korean APT group. Which one, they don't say.
Lazarus APT: K7 has a report out on recent Lazarus APT operations, namely, one baiting users with job vacancies at Coinbase that try to infect victims with macOS malware. [report/cached]
BlueNoroff APT: Kaspersky has an analysis of recent MOTW bypass techniques used by the BlueNoroff North Korean APT in attacks since this September. This includes hiding malware inside ISO or VHD files and the use of Batch scripts and various LOLbins.
Albanian government attacks: The Iranian APT groups who attacked the Albanian government networks with data wipers this year used stolen certificates from Nvidia and Kuwait Telecommunications Company to sign their malware. According to Kaspersky, while the Nvidia certificates were known to have leaked, it is currently unknown how the hackers got their hands on the KTC certs.
STEPPY#KAVACH APT: Securonix has a report out on a spear-phishing campaign linked to the STEPPY#KAVACH APT that targeted Indian government officials. Securonix researchers described STEPPY#KAVACH as having "many common TTPs with the SideCopy/APT36 threat actors" that were previously linked to the Pakistan government.
APT-C-36 (Blind Eagle): Qihoo 360 researchers have published a report on APT-C-36 (Blind Eagle), a suspected Latin American APT, and its recent spear-phishing campaigns delivering versions of AsyncRAT or NjRAT. Targeting seems to have been aimed at Colombia.
APT-Q-27 (Miuuti Group): QiAnXin researchers have a report out on Operation Dragon Dance [1, 2], a series of attacks that targeted the southeast Asian gaming industry. The report is a continuation of previous reporting on a campaign known as Operation Dragon Breath [1, 2].
Mustang Panda APT: Vietnamese security researcher Soulevil has published an analysis of a PlugX malware sample used in a recent Mustang Panda APT intrusion. Recorded Future has a report on the same thing as well.
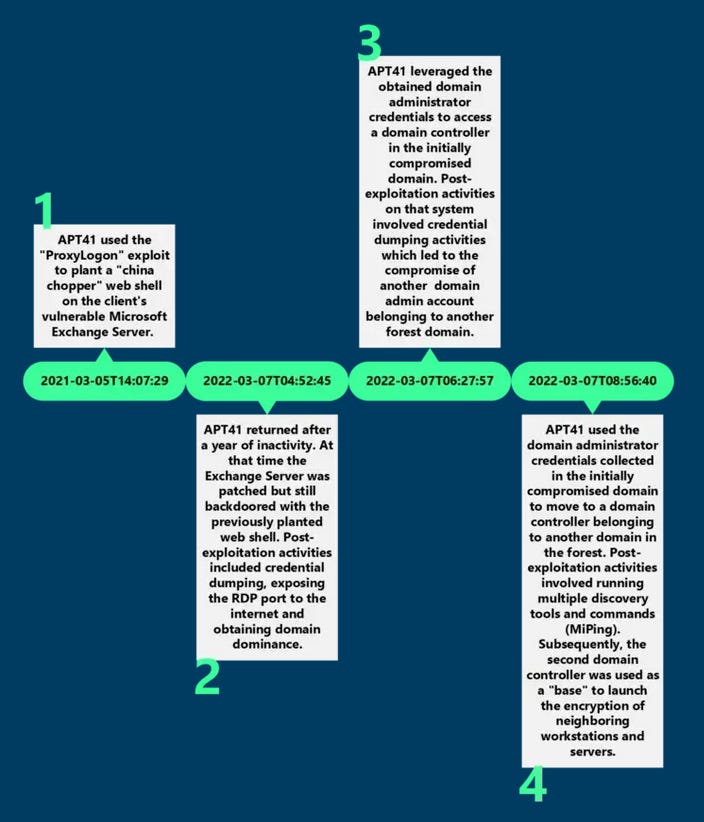
APT41: German security firm DCSO has an IR report from a March 2021 APT41 intrusion where the Chinese espionage group tried and failed to deploy ransomware on the network of one of their victims (German company from the financial sector).
Vulnerabilities and bug bounty
ZyXEL backdoor credentials: Italian security researcher RE-Solver has found several backdoor credentials in the firmware of some ZyXEL routers. This includes hardcoded superuser credentials that can bypass web UI authentication and hardcoded credentials to allow root access via Telnet.
Puckungfu: NCC Group researchers have published a write-up on Puckungfu, a now-patched command injection vulnerability affecting Netgear routers. The bug is pretty serious as it can be exploited via the WAN interface.
CVE-2022-23093: Arch Cloud Labs have published a breakdown of CVE-2022-23093, a vulnerability in the FreeBSD ping utility.
Elastic IP hijacking: Mitiga researchers have found a new attack vector in AWS infrastructure, namely in a new feature named AWS Elastic IP Transfer that allows AWS customers to move IP addresses when migrating server infrastructure.
Citrix exposure: Fox-IT researchers said they found thousands of Citrix ADC and Gateway devices that are currently available online and vulnerable to CVE-2022-27518, a zero-day vulnerability that was exploited in the wild by Chinese state-sponsored hackers earlier this month.
EarSpy attack: Academics from several US universities have developed a new attack called EarSpy that can eavesdrop on Android conversations and other audio using the devices' built-in motion sensors, such as the accelerometer.
AI assistant coding tools are bad: Academics from Stanford have found that code written by AI assistant coding tools like GitHub Copilot produce code that contains more vulnerabilities than code written by actual humans. Color me surprised!
Infosec industry
Cyber-attacks to become uninsurable: Mario Greco, chief executive at insurer Zurich, told the Financial Times last week that cyber-attacks will soon become uninsurable as the number of incidents continue to grow and so do the losses from them. [Non-paywall version here]
New tool—PEACH: Cloud security firm Wiz has open-sourced PEACH, a tenant isolation framework for cloud applications.
New tool—Columbus Project: Elmasy has open-sourced a new tool called the Columbus Project that can help identify and list known subdomains for a particular domain name.
Acquisition news: Cybersecurity firm Netwrix has acquired Remediant, a startup specializing in continuous privilege discovery and remediation.
New newsletter: Datadog's Zack Allen has started a new infosec newsletter. Named Detection Engineering, the newsletter focuses on defending techniques and news.