Risky Biz News: China cracks down on the SE Asia scam call center problem
In other news: MinIO servers exploited to breach cloud infrastructure; Paraguay's National Police hacked; crypto-gambling site Stake loses $41 million in crypto-heist.
This newsletter is brought to you by enterprise browser Island. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Back in June, the Chinese ambassador in Myanmar asked the country's military junta to crack down on the ever-growing number of illegal call centers operating in Myanmar's north conducting online and telecom scams targeting Chinese citizens.
Three months later, Myanmarese officials have delivered on their promise and have put high-profitable criminal operations on alert after a long string of arrests.
Six suspects were detained in June, seven last month, then two, then 24, and now 269 in the largest crackdown to date.
Eleven call centers were raided in the last operation. Officials say the call centers were involved in online scams of at least $16.5 million, but the number is well on the conservative side.
One-hundred-eighty-six Chinese nationals detained in the raids were loaded on buses and immediately sent to China to face charges for their crimes.
Also known as "boiler rooms" or "pig-butchering farms," these are call centers typically run by Chinese criminal gangs in countries across Southeast Asia.
They are staffed with trafficked workers who are forced to conduct online scams under the threat of violence against them or their families.
Workers in these call centers typically operate following a romance scam technique, approaching victims on social media or dating sites, building rapport, and then urging the victim to make a financial transfer or investment in a fraudulent business or cryptocurrency account.
The phenomenon has been going on for more than a decade, but the number of "boiler rooms" has exploded in Southeast Asian countries during the COVID-19 pandemic when many workers became desperate for a job to sustain their families after legitimate businesses closed their doors.
People from tens of countries have been lured to Southeast Asia on the promise of a legitimate job or a romantic date, only to be kidnapped and forced to work in one of these call centers.
A UN report published last week estimates that roughly 220,000 people across Cambodia and Myanmar are being forced to work in call centers as part of online scam operations.
Similar call centers also operate in Laos, Thailand, and the Philippines, but exact numbers aren't available for those operations.
The UN estimates Southeast Asian scam centers are generating revenue in the realm of billions of US dollars each year, most of which is fueling Chinese criminal cartels.
Many call centers target Western countries like Australia, the US, and the EU, but many also operate locally, targeting the workers' native countries.
With a large portion of call center workers being Chinese nationals, China has been one of the most impacted countries by the "boiler room" and "pig butchering" epidemic.
Online fraud campaigns, smishing, and social media social-engineering have been some of the most common reports published by the Chinese cybersecurity industry over the past year.
A Chinese film named "No More Bets" was this summer's highest-grossing movie on China's internal market. The film follows the adventures and inhumane treatment a Chinese programmer goes through after being lured to work for one of these call centers—showing how prevalent these scams and recruitment schemes have become across China.
Even if similar centers operate across all of Southeast Asia, Myanmar has become the poster child for the runaway scam call center problem. Experts believe the country's 2021 military coup created the perfect conditions for criminal syndicates to thrive, with some local authorities turning a blind eye to the problem for the right price.
When officials from China, Myanmar, Thailand, and Laos met in August, they established a joint police operation dedicated specifically to cracking down on Myanmar-based scam call centers.
But China's efforts aren't limited to Myanmar alone, and similar raids have also taken place in Indonesia and the Philippines, both following tips and in collaboration with China's Ministry of State Security.
Breaches, hacks, and security incidents
Freecycle breach: Used item exchange portal Freecycle has suffered a security breach after a hacker gained access to its systems and stole the account details of more than 7 million users. The stolen data includes usernames, emails, and passwords, which is now being sold on underground hacking forums.
NXP breach: Hackers have breached the systems of Dutch chipmaker NXP. The breach lasted from July 11 to July 14, when the company detected the intrusion. The company is now notifying all affected users who had accounts on its website and had data accessed in the incident. NXP is one of the Top 20 largest semiconductor companies in the world.
Stake crypto-heist: Crypto-gaming website Stake lost more than $41 million in crypto assets after an attacker managed to siphon funds from two of its hot wallets. Stake confirmed the hacks in a tweet and resumed operations four hours after the hack. Stake is a crypto gambling protocol that offers dice games, Blackjack, Lingo, and other casino games, as well as sports betting for cryptocurrency owners. [Additional coverage in CoinTelegraph]
Paraguay National Police hack: Hackers have breached and stolen more than 175GB of data from the database of the Paraguay National Police. The hack is believed to have taken place earlier this year and impacted the internal affairs directorate and technology and development division of Paraguay's National Police. The data is said to contain more than 500,000 files, including booking photographs and incident reports. The hackers shared the data with the DDoSecrets project, which said it would only make it available to journalists and researchers. Paraguayan officials said they were investigating the incident but never officially confirmed the hack.
Chastity cage leak: A Chinese smart sex toy company has left one of its databases exposed online and has leaked information on customers who own its male chastity devices (aka penis cages). Exposed data included email addresses, plaintext passwords, home addresses, IP addresses, and even GPS coordinates for some users. The security researcher who found the database says they reported the leak to the company and China's CERT team in June, with little success. The researcher says they went as far as to deface the vendor's homepage to inform the company about its leaky database. The company restored its website but did not secure its database. [Additional coverage in TechCrunch]
Belarusian Red Cross hack: Belarusian hacktivist group Cyber Partisans says it hacked the Belarusian Red Cross organization. The group claims to have stolen documents that show how the Belarusian branch of the Red Cross helped Russian forces forcibly move Ukrainian children to Belarus without their parents. The documents reference children from the city of Lisichansk in Ukraine's Luhansk region. The group says it turned over the stolen documents to the Ukrainian government for "further proceedings."
General tech and privacy
ICO BCC warning: The UK ICO has warned companies about using the BCC field in email campaigns that contain PII data, as many companies have accidentally sent PII data to unintended recipients in the past. Mihaela Jembei, ICO Director of Regulatory Cyber, explains.
"Failure to use BCC correctly in emails is one of the top data breaches reported to us every year – and these breaches can cause real harm, especially where sensitive personal information is involved."
Google to show ads based on browser history: Google is enabling the Privacy Sandbox feature for all Chrome users. Over the past month, Google has notified Chrome users about its intentions to show them ads based on their browsing history. A pop-up informing users of the change is being shown to users. Users who don't want to allow their browsing history to be harvested by Google at the browser level can disable this feature in the browser's settings section—under Ad Privacy. They must uncheck all options.
chrome://settings/adPrivacy
Government, politics, and policy
Dutch government looks at Telegram: The Dutch government is investigating Telegram for its failure to act and take down channels where anonymous users share nude photos of women and their contact details. Dutch officials say that more than 10,000 such messages are published on the platform on a daily basis. Some messages contain the contact details of family members, encouraging users to expose and embarrass the victim. Some groups also shared nude images of girls as young as 13, Dutch TV chanell NOS reported over the weekend.
Bangladesh Cyber Security Act: The Bangladeshi Parliament is in the process of passing a new cybersecurity bill that experts say limits freedom of expression on the internet by allowing the government to crack down on online dissent and journalism under the guise of cybercrime and national security.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Mike Fey, CEO and co-founder of Island, about the idea of an "enterprise browser." Tom and Mike discuss what an enterprise browser actually is, what problems it solves, and why browsers focused on business requirements haven't been a product category until now.
Cybercrime and threat intel
MinIO exploitation: A threat actor is exploiting vulnerabilities in MinIO object storage servers to take over cloud infrastructure. The attacks are using two MinIO vulnerabilities patched in March. The first (CVE-2023-28432) allows the attacker to retrieve MinIO secret keys and passwords, while the second (CVE-2023-28434) allows the attacker to replace the MinIO client with a backdoored version known as Evil MinIO. Once inside cloud infrastructure, the attackers attempt to move laterally inside corporate networks. Security Joes says that of the 50,000 publicly accessible MinIO installations, more than 30,000 are running vulnerable versions. Exploitation of the first vulnerability goes as far back as March, per GreyNoise.
qBittorrent exploitation: A threat actor is exploiting qBittorrent clients to install crypto-mining malware on user devices. The attacks abuse a lesser-known feature of the qBittorrent client that opens and runs a hidden web server on port 8080. Attackers appear to be scanning the internet for this server, using its default username and password, and then modifying qBittorrent client settings to run malicious scripts every time a torrent finishes downloading.
RocketMQ exploitation: VulnCheck takes a look at all the recent exploits for CVE-2023-33246 that are hitting RocketMQ servers.
"To our knowledge, CVE-2023-33246 is only associated with one botnet. However, it's clear there are at least a few active actors, and even more victims. This is a good opportunity to remove your RocketMQ instance from the internet and to examine the broker configuration for signs of exploitation."
Common usernames and passwords: SANS ISC has published a list of the most common usernames and passwords submitted to its honeypot network. Root & admin rule the list by a mile.
New EDR killer: A threat actor named r1z is advertising a new tool that can kill any EDR product and also work as a persistent backdoor and malware dropper. The tool appears to predate Terminator, a similar exploit that was advertised online in June. (h/t Kaushík Pał)
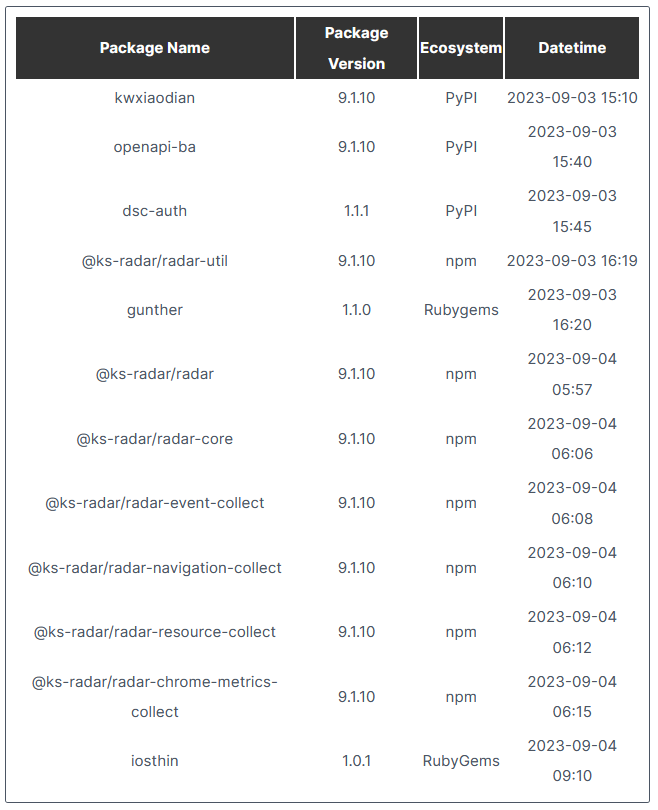
Tri-repo campaign: DevSecOps company Phylum has spotted a threat actor publishing malicious libraries on three package repositories at the same time. The campaign involved three malicious Python packages, seven JavaScript libraries, and two Ruby gems. Phylum says it caught the campaign in its early reconnaissance phase, and it is unclear what the threat actor's final goal is. All libraries contained the same malicious code that gathered information on infected hosts and uploaded it to a Chinese server.
Malware technical reports
Node.js-based stealer: Trend Micro has a look under the hood of a new Node.js-based infostealer its researchers have spotted in the wild.
Chae$ 4: Morphisec has published an analysis of Chae$ 4, the latest version of Chaes, a malware strain designed to infect Chrome browsers and exfiltrate data from users of Latin American online marketplaces since 2020. The malware's new version has been rewritten in Python and also comes with new modules, including one that targets cryptocurrency wallets.
IDAT Loader: Rapid7 has spotted a new malware loader named IDAT being used in the wild since July. Researchers say the loader is being used as an initial infection point that is then used to deploy infostealers such as Amadey, Lumma, and StealC.
Sponsor Section
Island CEO Mike Fey and CSO Brian Kenyon talk about how the Island enterprise browser came to be and its early days.
APTs and cyber-espionage
APT28: CERT-UA published a report on a recent APT28 spear-phishing campaign that targeted a critical energy infrastructure facility in Ukraine.
Influence operations in Africa: Microsoft says it identified two pro-Russian entities involved in online and offline influence operations that took place in the aftermath of Niger's military coup that took place in July this year. The two groups are named PARADE Niger and the Union of Pan-African Patriots. The first is a construct of the Russian Ministry of Foreign Affairs (MFA), while the second group is run by a single local politician. Microsoft says the two groups defended the coup online through bot networks, organized offline protests in support of the military, and called for greater cooperation with Russia. Microsoft says the same propaganda playbook used in Niger was also used in other African countries where pro-Russian military juntas took power, such as Mali, Burkina Faso, Chad, and, more recently, Gabon.
Vulnerabilities, security research, and bug bounty
SCARF: A group of security researchers has developed a new security system that can prevent side-channel attacks that can leak data from a CPU's cache memory space. Named Secure Cache Randomization Function, or SCARF, the system implements a randomized cache layout that prevents attackers from easily identifying data to leak from a CPU cache. The research team says SCARF outperforms similar systems that heavily rely on cache encryption.
Media Library Assistant RCE: Security company Patrowl has found an unauth RCE vulnerability (CVE-2023-4634) in Media Library Assistant, a popular WordPress plugin installed on more than 70,000 WP sites.
Librsvg vulnerability: The dev team at Canva has found a directory/path traversal vulnerability (CVE-2023-38633) in Librsvg, a Rust library for rendering SVG graphics.
"We use librsvg to quickly render user-provided SVGs into thumbnails later displayed as PNGs. By exploiting differences in URL parsers when rendering an SVG with librsvg, we showed it's possible to include arbitrary files from disk in the resulting image."
Auna internet radio vulnerabilities: Security researcher Naphthalin has discovered several vulnerabilities in Auna IR-160 internet radios. These include a "rudimentary" and insecure API that can be used to take control of devices, an XSS bug in the web UI, and a DoS bug that can be used to crash some device functionality until a device reset.
Mend cross-tenant access: Security firm WithSecure (formerly F-Secure) has found a cross-tenant access vulnerability in the Mend.io (formerly WhiteSource) AppSec platform.
"Mend.io customers could access the data of other customers in the same SaaS environment by guessing or otherwise obtaining a valid email address. An attacker able to open an account with Mend.io could therefore use this vulnerability to obtain information on vulnerabilities contained in Mend.io customers' software for further use (for example, targeted attacks)."
Android security updates: The Android Security Bulletin for September 2023 is out! The security updates are available for Android versions 11, 12, and 13. Google says CVE-2023-35674 has seen active exploitation.
SCADA zero-day: A Chinese security researcher named Y4er has published an analysis of CVE-2023-39476, a pre-auth RCE vulnerability in Inductive Automation Ignition. The Ignition platform is a central hub that can be used to manage and automate SCADA equipment across plant floors. The vulnerability was publicly disclosed in August and has yet to be patched.
API leaks in top sites: Security researchers from Haksec and Truffle Security say that 4,500 of the top one million most visited websites are leaking credentials and API keys via misconfigured source code repositories. AWS and GitHub keys accounted for 45% of all leaked credentials, and the vast majority of GitHub credentials had admin access.
Windows Container Isolation Framework abuse: DeepInstinct researchers describe how threat actors can abuse the Windows Container Isolation Framework to hide their malware from security products inside custom Windows containers. PoC included.
WP zombie plugins: Security firm Patchstack says 404 vulnerabilities disclosed this year in WordPress plugins have yet to receive a patch. The vulnerabilities affect plugins that do not have contact information listed for their developers. Patchstack says it worked with the WordPress team to permanently close and remove 289 of the zombie plugins, but six are still live. The company says it is in the process of trying to get patched more than 200 similar vulnerabilities impacting zombie themes listed on the official WordPress repository.
CISA KEV update: 117 actively exploited vulnerabilities have been added this year to the CISA KEV database, according to Nucleus Security's Patrick Garrity. With four months left to go, expect the number to go over 150 this year.
Infosec industry
New tool—Caldera for OT: CISA and MITRE have released a project named Caldera for OT. The project adds OT-specific plugins to the MITRE Caldera adversary emulation framework.
Geoff Chappell: The cybersecurity industry mourns the passing of Geoff Chappell, a member of the infosec community for more than three decades. He is best known for his early work in reverse engineering Windows internals.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how companies often make unilateral decisions that constrain states' behavior, for better and worse.