Risky Biz News: DIALStranger vulnerabilities disclosed after four years
In other news: A Dutch hacker helped drug cartels; security firm COO pleads guilty to hacking; and China hacks the Philippines government after sea scuffle.
This newsletter is brought to you by Yubico. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Turkish security researcher Yunus Çadirci has discovered vulnerabilities in the DIAL protocol and misconfigurations in vendor equipment that can be used to force TVs and other capable devices into forcibly playing an attacker's video content.
The vulnerabilities have been collectively named DIALStranger, and details about the flaws were disclosed for the first time at the Black Hat Middle East and Africa security conference last week.
The DIALStranger flaws were discovered way back in 2019, but Çadirci kept the original report private for four years as the protocol received patches and vendors slowly updated devices.
The flaws impact Discovery and Launch—or DIAL—a protocol primarily co-developed by Netflix and YouTube, with help from Sony and Samsung.
It's a protocol that merges SSDP, UPnP, and HTTP. It is designed to operate on local subnets to allow devices to discover each other. Its primary audience is multimedia device vendors, as DIAL can allow "second screen" devices, such as a smartphone or tablet, to send and play content on "first screen" devices, such as a smart TV, set-top box, or PC.
Back in 2019, Çadirci says he discovered that the DIAL protocol did not have any kind of authentication or strong security mechanisms put in place.
He found that "first screen" devices were exposing a web server URL where "second screen" devices could send playback instructions.
If the "first screen" device was exposed on the internet, anyone could send commands to these endpoints and play any video stream they wanted without any sort of authentication or pairing needed.
At the time, Çadirci says he found "thousands of devices connected to [the] Internet directly that can be controlled by attackers" and that some attacks on devices in local networks were also possible.
Çadirci says that Netflix updated the protocol in 2020 to cover some of the DIALStranger issues, while some vendors either moved away from DIAL or slowly released firmware updates or new devices with a better version of the protocol.
The researcher didn't provide a full list of vulnerable devices, but his PoCs successfully exploited an Xbox One console and smart TVs from Phillips, LG, Vestel, and Samsung.
A scanning script is available for further testing.
The vulnerability's name comes from Çadirci's previous work on CallStranger, a vulnerability in the UPnP protocol that could be abused to bypass security features on IoT devices and abuse them for DDoS attacks.
Obviously, DIALStranger is not an internet-breaking flaw, but anything that can be used for mass-rickrolling is a DEFCON 1 threat level to me.
Breaches, hacks, and security incidents
Canadian government data breach: The Canadian government says that cybersecurity breaches at two of its contractors have exposed the information of government employees. The breaches took place in mid-October and impacted Brookfield Global Relocation Services and SIRVA Worldwide Relocation & Moving Services, two companies that provide relocation services for government employees. Affected individuals include RCMP police forces, military staff, and public servants, going as far back as 1999. The LockBit ransomware gang already took credit for the BGRS attack.
Long Beach cyberattack: The city of Long Beach in California has shut down its IT systems after it suffered a cybersecurity incident on Tuesday. Officials say the incident did not impact public city services.
Postmeds breach: Postmeds, the company behind the Truepill pharmacy prescription fulfilling service, has disclosed a security breach. The data of more than 2.3 million Americans is believed to have been impacted. [Additional coverage in TechCrunch]
dYdX cyber-heist: A threat actor exploited the dYdX cryptocurrency platform to steal $9 million worth of crypto-assets from the company's wallets. A member of the dYdX team described the incident as a price manipulation attack.
Kronos Research cyber-heist: A threat actor stole almost $26 million worth of crypto assets from the Kronos Research trading platform. The Taiwanese company says the hack took place after the attacker gained access to some of its platform's API keys. Kronos says the hack will not jeopardize its operations, and the stolen funds only represent a small portion of its assets. [Additional coverage in The Block]
Poloniex (allegedly) identifies hacker: The Poloniex cryptocurrency exchange has allegedly learned the real-world identity of the hacker who breached its platform and stole $130 million earlier this month. In a message attached to a blockchain transaction, the company has given the hacker until November 25 to return all the stolen funds. The company says if the hacker doesn't comply, they will file charges with law enforcement in China, Russia, and the US. Poloniex has also offered to allow the hacker to keep $10 million as a "white hat reward" in an attempt to entice the hacker to return its funds.
General tech and privacy
iPhone RCS support: Support for the new RCS messaging standard will arrive on iPhones next year. [Additional coverage in 9to5Mac]
Chrome Mv2 phase-out: Google has resumed plans to phase out Manifest V2, the codebase on which most current Chrome extensions are running. Extension developers should look into porting their code to the new Manifest V3 API.
"We will begin disabling Manifest V2 extensions in pre-stable versions of Chrome (Dev, Canary, and Beta) as early as June 2024, in Chrome 127 and later. Users impacted by the rollout will see Manifest V2 extensions automatically disabled in their browser and will no longer be able to install Manifest V2 extensions from the Chrome Web Store. [...] We expect it will take at least a month to observe and stabilize the changes in pre-stable before expanding the rollout to stable channel Chrome, where it will also gradually roll out over time."
Ad-blocking company AdGuard, which has been one of the Mv3's biggest critics, has now toned down its criticism.
Twitter loses advertisers: More than a dozen of the world's largest advertisers have pulled their ads off Twitter after the platform's owner boosted some braindead antisemitic conspiracy theories. Companies that left Twitter include Apple, Sony, Disney, Lionsgate, Paramount, Comcast, Warner Bros, and IBM. [Additional coverage in Deadline]
Tor finances: The Tor Project has published its financial report for fiscal year 2021-2022. As in previous years, the US government still remains the project's main donor.
Government, politics, and policy
Russian internet censorship: The Russian government has granted permission to telecommunications watchdog Roskomnadzor to block access to websites that contain information about circumventing Internet censorship. The ban would primarily impact websites that provide instructions on how to use a VPN. After Russia's invasion of Ukraine, the Rosomnadzor's blocklist has reached a mammoth size of 885,000 URLs. [Additional coverage in Meduza]
New acting national cyber director: The White House has appointed Drenan Dudley as the new White House acting national cyber director while nominee Harry Coker is going through his Senate confirmation process. [Additional coverage in Cyberscoop]
New CISA guide: CISA has released a security mitigation guide for organizations in the healthcare and public health sectors.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Derek Hanson, Yubico VP of Solutions Architecture and Alliances, about the state of authentication and what Passkeys are all about.
Cybercrime and threat intel
Marriott hacker fakes his own death: The FBI has arrested a Kentucky man for hacking two contractors for the Marriott hotel chain, stealing guest data, and then selling it on a Russian hacking forum. Jesse Kipf of Somerset, Kentucky, was detained in July and formally charged at the start of November. The hacks took place in February and June this year and were not publicly disclosed, neither by Marriott nor its contractors. The FBI says Kipf also hacked several US state death certificate registration agencies and successfully faked his own death in both Hawaii and Vermont. It remains unclear why, but Forbes believes this was an attempt to hide his tracks and throw off investigators. [Additional coverage in Forbes/non-paywall]
Securolytics COO pleads guilty: The chief operating officer of cybersecurity firm Securolytics has pleaded guilty to hacking two hospitals in order to boost his company's business. Prosecutors say Vikas Singla hacked two hospitals in the cities of Duluth and Lawrenceville, Georgia, and then immediately started advertising his own company's cybersecurity services to other nearby hospitals. Singla's hacks disrupted phone and network printer services. His hacks and advertising scheme were discovered, and Singla was detained in 2021. As part of the plea deal, Singla has agreed to pay $818,000 in restitution to the two hacked hospitals. In return, prosecutors will ask the judge for 57 months of probation. [Additional coverage in Law360, GovInfoSecurity]
Israeli hacker-for-hire sentenced: A US judge has sentenced an Israeli private investigator to 80 months in prison for his role in organizing global hacking campaigns. Prosecutors say Aviram Azari made $4.8 million by acting as an intermediary between hacking groups and his customers. Azari organized campaigns that targeted climate change activists, and individuals and financial firms that had been a critical part of the German payment processing company Wirecard. The 80-month sentence is the halfway mark between the 100 months asked by the prosecution and the 60 months asked by Azari's legal team.
Dutch hacker helped drug traffickers: A Dutch man named Davy de Valk has hacked the container management systems in the Antwerp and Rotterdam ports to aid criminal cartels smuggle drugs and contraband into the EU. According to the Organized Crime and Corruption Reporting Project, de Valk provided data to cartels about the best containers for hiding contraband. He allegedly hacked the Antwerp port after bribing an employee into inserting a malware-infested USB in the terminal's network. His hacking spree began in 2020, and he provided crucial information to help smugglers pick up their goods on the receiving end. De Valk's story is part of the OCCRP's Narco Files, a collection of reports on how crime groups, and drug cartels specifically, are slowly taking over the world.
Patternz profile: The Irish Council of Civil Liberties says that an Israeli company named ISA Security is selling access to Patternz, a powerful surveillance tool. The ICCL says Patternz taps into real-time bidding information from online advertising platforms to provide customers the ability to track almost anyone around the world. ISA claims Patternz has data points for five billion individuals, including information on their driving routes, children, co-workers, and approximate geo-location. The ICCL warns the data on which Patternz is built freely flows through China and Russia and poses a danger to government, intelligence, and military staff in both the EU and the US.
New npm malware: Thirteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
State of cloud security: Cloud security firm Datadog has published its yearly report on the state of cloud security. The main conclusions are below.
Long-lived cloud credentials continue to be problematic and expose cloud identities.
Multi-factor authentication (MFA) is not always consistently enforced for cloud users.
Adoption of IMDSv2 in AWS is rising, though still insufficient.
Use of public access blocks on storage buckets varies across cloud platforms and is more prevalent in AWS than Azure.
A number of cloud workloads have non-administrator permissions that still allow them to access sensitive data or escalate their privileges.
Many virtual machines are exposed to the internet.
Malware technical reports
SharpLoader: A new version of the SharpLoader malware is now in the wild, distributing versions of the QasarRAT.
Serpent Stealer: ThreatMon has published a report on the new Serpent infostealer, also known as Serpent Stealer.
AlphV malvertising: An AlphV ransomware affiliate is using malicious Google ads to redirect users to enterprise apps laced with malware. Spotted by security firm eSentire, the ads target users searching for apps such as Slack, WinSCP, Advanced IP Scanner, and Cisco AnyConnect. These boobytrapped files contain a version of the Nitrogen backdoor, which the group will use to move laterally across networks and deploy its ransomware. eSentire says the campaign has been running since June. This seems to be the same campaign also spotted by Securonix and Trend Micro.
QazLocker ransomware: Acronis security researchers have published a deep dive into the new QazLocker ransomware. The blog post is the first in a series of write-ups the company plans to publish on currently active ransomware operations.
Rhysida ransomware: Fortinet researchers published an analysis of the Rhysida ransomware, also covered by CISA and the FBI last week here, too.
NoEscape ransomware: The same Fortinet team also looked at the NoEscape gang, a group seen recently employing DDoS attacks to pressure victims.
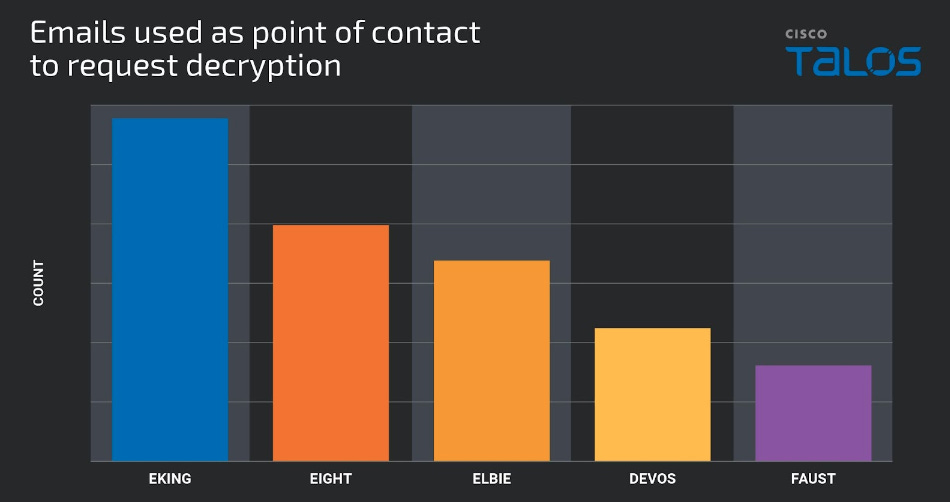
Phobos ransomware: Cisco Talos has published an in-depth analysis of the Phobos (aka Dharma) RaaS platform and its most active affiliate groups, one of which is an extortion group known as 8Base.
"We assess with moderate confidence Eking, Eight, Elbie, Devos and Faust are the most common Phobos variants, as they appeared most frequently across the samples we analyzed. We assess with moderate confidence that the Phobos ransomware is closely managed by a central authority, as there is only one private key capable of decryption for all campaigns we observed."
Sponsor Section
Brought to you by Yubico, the inventor of the YubiKey, a security key that provides the gold standard for multi-factor authentication (MFA) and stops account takeovers in their tracks. Find them at yubico.com
APTs, cyber-espionage, and info-ops
Stately Taurus: A Chinese APT group named Stately Taurus has launched an extensive cyber-espionage campaign against the Philippines government. The intrusions began in August after the Philippines announced joint navy patrols with the US and naval exercises with Australia. Palo Alto Networks says the group managed to compromise at least one government agency for five days in August.
SideCopy: ThreatMon has published a report on recent SideCopy operations that have used the AllaKore RAT for remote access.
Rattlesnake: QiAnXin has published a report on a Rattlesnake (Sidewinder) APT operation targeting South Asian countries with a Nim-based backdoor.
Gamaredon: Russian APT group Gamaredon is conducting a large-scale intelligence collection in Ukraine using a new USB worm named LitterDrifter. The worm's main purpose is to spread to as many systems as possible and then establish a connection from the newly infected host to a Gamaredon command-and-control server. In November 2021, the Ukrainian Security Service linked the Gamaredon group to the Crimean branch of the Russian Federal Security Service, also known as the FSB.
Vulnerabilities, security research, and bug bounty
Havoc C2 vulnerability: Security researcher Ali Beydoun has found a vulnerability in the Havoc C2 framework that can be used to crash C2 servers.
KEV tags on GreyNoise: The GreyNoise service now supports CISA KEV tags for easier threat hunting of actively exploited vulnerabilities, a useful feature for organizations with active threat intel teams and compliance requirements.
Splunk security updates: SIEM maker Splunk released security updates last week to fix seven vulnerabilities.
Infosec industry
New tool—.NetConfigLoader: Mr.Un1k0d3, a member of the RingZer0 CTF team, has published a list of .NET apps signed by Microsoft that can be used for EDR/AV evasion.
New tool—Porch Pirate: Security firm Mand Consulting Group has open-sourced a tool named Porch Pirate that can uncover secrets published to the Postman software development platform.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about International Humanitarian Law, aka the Rules of War in cyberspace. These rules don't really make sense in cyberspace, but despite that, Tom and The Grugq think talking about them (and other norms of behavior) is still worthwhile.