Risky Biz News: ICANN launches RDRS to help cybersecurity professionals with domain investigations
In other news: Ransomware attack cripples ~60 US credit unions; Platypus hackers freed in France; and US sanctions Kimsuky APT.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
ICANN, the non-profit organization that manages domain names and IP addresses, has launched a new service to help law enforcement agencies and cybersecurity professionals obtain redacted and non-public data on domain owners.
Named the Registration Data Request Service (RDRS), the service works as a ticketing system that interconnects investigators with domain registrars—the smaller organizations that manage each TLD domain space.
The new system is designed to create private communication channels where investigators can file requests with domain registrars in a more centralized fashion.
Currently, investigators can file legal requests or abuse reports with each registrar, but the idea behind RDRS is to create a place where requests from "verified" parties can be honored faster and with a higher degree of trust.
The idea is not new, and such systems already exist for social networks, email providers, and cloud-hosting companies. These are specialized portals—managed by either the company or law enforcement—where agents can file requests about a company's users as part of emergency responses or ongoing investigations. Breaches in such systems have usually given hackers access to a wide spectrum of personal data.
ICANN says it launched the service after the EU passed the GDPR, a stringent data protection law that forced domain registrars to redact information on domain owners from their publicly available WHOIS databases.
Such information is still present in the private databases of domain registrars and has been made available to some organizations, but usually only in a very limited fashion, such as court orders, subpoenas, or following intelligence-sharing agreements.
However, the removal of WHOIS data from the public domain has, without a doubt, made the internet a worse place.
It allowed—and still allows—criminal, malware, and online fraud operations to hide and operate for longer times, as law enforcement and infosec professionals get bogged down in paperwork or never get answers from some registrars.
RDRS is most likely a step in the right direction, but as ICANN says on the portal's front page, the service is just a limited two-year "proof of concept" and may be abandoned.
Breaches, hacks, and security incidents
Trellance ransomware attack: About 60 US credit unions are dealing with network outages after a ransomware gang hit Trellance, one of their shared IT providers. The incident took place on Sunday, November 26, and is still ongoing, according to the US National Credit Union Administration. The full extent of the incident is still unknown, but Trellance is said to be rebuilding its systems. [Additional coverage in The Record]
Safe wallet hacks: A threat actor has stolen an estimated $5 million worth of crypto assets from the owners of Safe cryptocurrency wallets. Twenty-one victims have been identified so far. The hacks have taken place over the past four months, with ten victims losing more than $2 million over the past week alone. According to Web3 security firm ScamSniffer, the attackers used a technique known as "address poisoning." The technique involves flooding a victim with smaller transactions in order to poison wallet history and hoping the victim copies one of the wrong addresses and sends money to the threat actor.
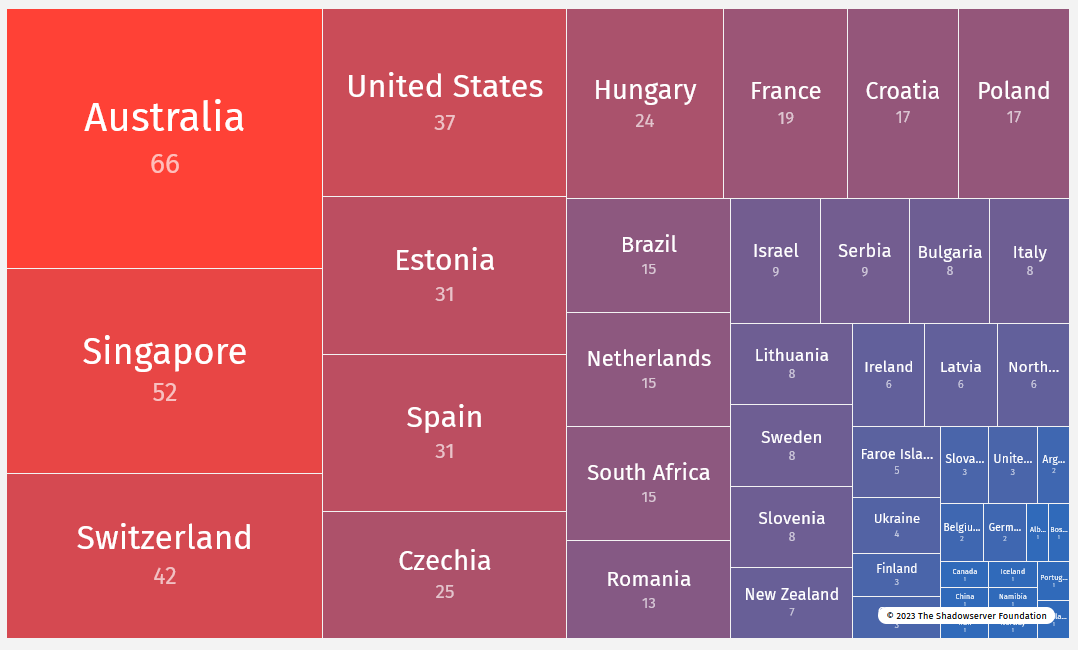
Unitronics hacking spree: The US government has confirmed that an Iranian hacking group named Cyber Av3ngers has gained access to equipment at water facilities across multiple US states. CISA, the FBI, the NSA, and other agencies say the attacks began as far back as November 22 and exploited PLCs manufactured by Israeli company Unitronics. The group targeted Unitronics PLCs that were still using the default password "1111." CISA asked US organizations last week to change the default password, enable MFA, and remove the devices from the internet. US officials say the Cyber Av3ngers group is affiliated with the IRGC, an Iranian military and intelligence organization. According to the Shadowserver Foundation, from 500 to 800 Unitronics PLCs are currently exposed on the internet, with the vast majority in Australia and Singapore.
General tech and privacy
US TikTok ban fails in court: A judge shot down Montana's attempt to formally and fully block the TikTok app across the state. The ban was meant to go into effect on January 1, 2024. The judge ruled that the ban violated the US Constitution's First Amendment in more ways than one. [Additional coverage in NPR]
Google RCS: Google says its RCS messaging system is now enabled on more than one billion Android devices.
Government, politics, and policy
New SSSCIP head: The Ukrainian government has appointed Yurii Myronenko as the new head of the State Service of Special Communications and Information Protection of Ukraine (SSSCIP). Myronenko was appointed after the government sacked the previous head, Yurii Shchyhol, following an investigation into alleged embezzlement. Prior to his appointment, Myronenko was a UAV strike squadron commander for SSSCIP.
UK Online Fraud Charter: Twelve of the world's largest tech companies have agreed to introduce new rules to fight online fraud as part of a new agreement signed with the UK government named the Online Fraud Charter. New measures include verifying new advertisers, promptly removing any fraudulent content, and better user verification for online marketplaces and dating services. The companies will also establish direct lines for law enforcement to report fraudulent content. The 12 signatories include Amazon, eBay, Facebook, Google, Instagram, LinkedIn, the Match Group, Microsoft, Snapchat, TikTok, Twitter, and YouTube.
EU Cyber Resilience Act: The European Council and the European Parliament have reached a political agreement on the Cyber Resilience Act, a piece of legislation meant to improve the security of smart devices sold in the EU. The new regulation applies to products ranging from baby monitors and smartwatches to firewalls and routers. Under the new rules, vendors will have to establish processes to receive reports about vulnerabilities and must support products for at least five years. Products will have to come with free and automatic security updates as the default option, must ensure data confidentiality using encryption, and vendors must inform authorities of any attacks. The new rules will come into effect three years after the CRA is formally voted on the EU Parliament floor.
EU Cyber Force: In a speech last week, European Council president Charles Michel advocated for the creation of an EU cyber force with "offensive capabilities."
Wyden blocks Haugh vote: Oregon senator Ron Wyden says he intends to block the vote for Lt. Gen. Timothy Haugh to serve as director of the National Security Agency (NSA). Sen. Wyden says he intends to block a vote until "the NSA discloses whether it is buying Americans' location data and web browsing records."
US Federal Cybersecurity Workforce Expansion Act: US lawmakers have introduced bipartisan, bicameral legislation that will create two new cybersecurity training programs with the federal government. Named the Federal Cybersecurity Workforce Expansion Act, the bill is one of the many recent attempts by the US government to address its existing cybersecurity workforce shortage. Under the bill, one of the training programs will be run by CISA, while the other will be housed by the Department of Veterans Affairs and will be exclusively available to veterans.
State Department reward: The US State Department is offering a $10 million reward for information on new methods and technologies used by North Korean hackers to launder their funds. The reward was put up a day after the US seized and sanctioned Sinbad, a cryptocurrency mixing service used by DPRK hackers to launder hacked crypto funds.
House hearing on supply chain security: The House Subcommittee on Cybersecurity, Information Technology, and Government Innovation held a hearing on the state of software supply chain security last week.
Risky Business Podcasts
In this podcast, Patrick Grey and Tom Uren talk about how threat actors abusing legitimate tools (aka living off the land or LOLbins) is the new normal. Everyone is doing it, from activists to cybercriminals to nation-states. It's a worry because the defender's standard practices really aren’t set up to detect and deal with that kind of behavior.
Cybercrime and threat intel
Platypus hackers freed in France: A French court has set free two suspects accused of stealing $9.5 million worth of crypto assets from DeFi platform Platypus Finance in February this year. Aged 20 and 18, Mohammed M. and Benamar M. were arrested a week after the hack in the Paris suburb of Aubervilliers. The two brothers claimed in court they acted in good faith and were just conducting white-hat ethical hacking. The duo said they found a vulnerability in the Platypus platform and moved the funds before a hacker could steal them. [Additional coverage in LeMonde/non-paywall]
Trickbot member pleads guilty: A Russian national has pleaded guilty to his role in developing and deploying the Trickbot malware. As part of the Trickbot gang, Vladimir Dunaev developed browser modifications and malicious tools that aided Trickbot in stealing credentials and deploying additional malware on infected computers. Dunaev was arrested in late 2021 after getting stuck in South Korea due to COVID-19 travel restrictions. He was extradited to the US and charged a month later. Dunaev now faces a maximum penalty of 35 years in prison.
New npm malware: Twenty-one malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
Cyber Toufan wiping campaign: A pro-Palestinian hacktivist group named Cyber Toufan is conducting data-wiping campaigns. The group claims it is attacking companies supporting Israel, but we all know they're just hitting anyone with an exposed system and re-framing it as "hacktivism" in the context of the Israel-Hamas war.
New Twisted Spider activity: A threat actor known as Twisted Spider is using the DanaBot malware to gain access to corporate networks and then deploy the Cactus ransomware via hands-on activity. Spotted by Microsoft, the initial DanaBot infections occur via malvertising campaigns. The Twitsted Spider group appears to have switched to using DanaBot for initial access after authorities took down the QakBot botnet at the end of August. Twisted Spider is a known affiliate for different ransomware services, such as REvil, Maze, and Egregor.
UAC-0006: Ukraine's CERT team has published a report on UAC-0006, a cybercrime group that has recently targeted members of the Ukrainian society to steal funds from their accounts. The group's primary tool has been SmokeLoader.
AeroBlade: A threat actor named AeroBlade is targeting organizations in the US aerospace sectors with the goal of conducting commercial cyber espionage. Discovered by BlackBerry's security team, the group appears to have set up infrastructure in September 2022 and began attacks in July this year. AeroBlade's s modus operandi includes phishing operations and the deployment of reverse shells for future reconnaissance.
M-13 profile: Security firm StrikeSource looks at M-13, a Russian company that provides software to the Russian government. Its offerings include the likes of Katyusha, Arena, Arsenal, and Strike. All are tools to mine and monitor news platforms and social media. Its owner, Vladislav Klyushin, was sentenced to nine years in prison in the US for hacking companies and making $93 million on the stock market using the stolen files.
"M-13's offerings are lackluster, to say the least, and far less than what would be hoped for from an organization with ties to the GRU. In comparison to what was seen with NTC Vulkan, M-13's capabilities make it seem as though the software side of its business was merely a front for its hacking and fraud operations which behind the scenes were used to enrich Klyushin and his co-defendants to the tune of tens of millions."
Amadey interview: A security researcher named G0njxa has interviewed InCrease, the author of the Amadey loader.
Internet bot traffic: An Arkose Labs report [PDF] has found that automated bots accounted for roughly 73% of the internet traffic the company monitored throughout the third quarter of 2023. Not all bots were malicious, and some were used for automation and other tasks. According to the company, the top web threats they tracked in Q3 were fake account creation, account takeovers, and web scraping.
Lumma campaign: The Perception Point team looks at a recent phishing campaign delivering the Lumma Stealer.
Booking campaign: Secureworks analyzes a phishing campaign targeting Booking.com users with the Vidar infostealer.
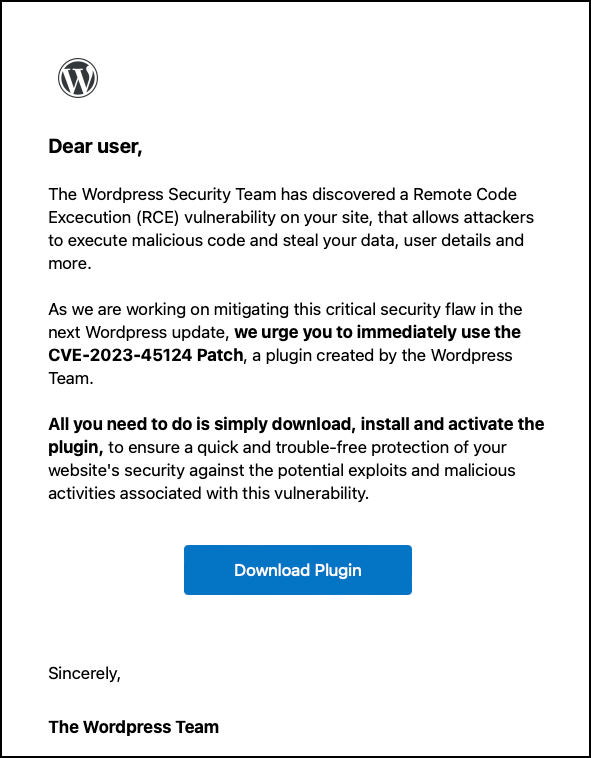
WP phishing campaign: A threat actor is posing as the WordPress security team in a phishing campaign targeting owners of WordPress sites. The campaign is advertising a patch for a non-existent CVE (CVE-2023-45124) and lures site admins into installing a backdoored plugin.
Malware technical reports
Stealc: MSSP Lab has published a two-part series on Stealc, a new infostealer that has been advertised on the cybercrime underground since the start of the year. Additional information via Sekoia, too.
DanaBot: CyFirma researchers look at DanaBot, a versatile malware strain that has been going around since 2018.
Turtle ransomware: Researchers have found a new ransomware strain named Turtle that can encrypt files on Windows, Linux, and macOS systems.
Akira ransomware: French security firm Intrinsec has published a technical report on the typical operations of an Akira ransomware intrusion.
Sponsor Section
In this product demo, Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray.
APTs, cyber-espionage, and info-ops
US Treasury sanctions Kimsuky: The US Treasury Department has sanctioned North Korean hacking group Kimsuky for its intelligence collection operations. The group has been active since 2012 and operates under the Reconnaissance General Bureau (RGB), North Korea's primary foreign intelligence service. It is also known in infosec nomenclature as APT43, Emerald Sleet, Velvet Chollima, TA406, and Black Banshee. Kimsuky joins the likes of Lazarus, Andariel, and Bluenoroff, three other North Korean hacking groups sanctioned in September 2019.
APT-C-28 (ScarCruft): Chinese security firm Qihoo 360 has published a report on North Korean hacking group APT-C-28 (ScarCruft, Reaper, APT37) and its recent campaigns delivering the Chinotto backdoor.
CL-STA-0002: PAN Unit42 researchers have identified a new APT group that has recently carried out operations against organizations in the Middle East, Africa, and the US. Tracked as CL-STA-0002, evidence suggests the group has been active since 2020. Unit42 says the group used custom malware (Agent Racoon, Ntospy, Mimilite) and is most likely a state-sponsored group.
Weekly dose of dumb Russian propaganda: A network of pro-Kremlin online accounts tried to blame a recent storm in Crimea on the US using "climate weapons" in Ukraine. I guess the "bio labs" shtick got old and boring with the troll farm employees.
Vulnerabilities, security research, and bug bounty
French govt bug bounty program: The French government will pay up to €20,000 to bug hunters to find vulnerabilities in its FranceConnect and AgentConnect online platforms. The two are authentication systems used by regular citizens and government employees to log into official government sites. This is the second bug bounty program the French government has set up this year after launching a similar effort for the maProcuration attorney-finding platform in May. [Additional coverage in Le Parisien]
CISA KEV update: CISA has removed a D-Link router vulnerability tracked as CVE-2022-28958 from the KEV database of actively exploited vulnerabilities. CISA says it removed the KEV entry after the vulnerability's CVE identifier was revoked. MITRE withdrew the identifier after VulnCheck researcher Jacob Baines discovered that the vulnerability never existed and filed a dispute to have it removed from the National Vulnerabilities Database.
EPPS intro: Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, has published a 14-minute introduction to the Exploit Prediction Scoring System (EPSS). Managed by FIRST, the system is currently supported alongside CVSS by more than 50 security products.
Connected zero-days: A Chrome zero-day and two Safari zero-days that were patched last week are connected, according to Google TAG researcher Maddie Stone.
VMware security update: VMware has finally released a software patch for a security flaw it first announced two weeks ago in the Cloud Director Appliance, tracked as CVE-2023-34060.
Zoom vulnerability: AppOmni researchers have identified a vulnerability in the Zoom web conferencing service that could have allowed threat actors to hijack Zoom Rooms.
Vulnerabilities in court case systems: Security researcher Jason Parker has discovered multiple vulnerabilities in the web-based case and document management systems used by multiple US courts. The vulnerabilities could have allowed threat actors to access sensitive court records related to civil and criminal cases. Although the majority did, not all of the affected courts have rolled out patches. [Additional coverage in TechCrunch]
O-RAN vulnerabilities: Trend Micro researchers have identified vulnerabilities in the Open Radio Access Network (O-RAN) mobile specification that can be used to crash or spoof information inside a crucial component of 5G network architectures.
Infosec industry
Nullcon 2023 videos: Talks from the Nullcon 2023 security conference, which took place in September, are available on the conference's official website.
New tool—Tricard: Unicorn Security has open-sourced a tool named Tricard that can fingerprint and detect malware sandboxes.
New tool—ASRGEN: Splunk's Michael Haag has released a tool named ASRGEN that can test configurations that can reduce a system's attack surface. The code is on GitHub as well.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the latest Russian cyber attacks on the Ukrainian energy grid.