Risky Biz News: Malware found on Rust's Crates repository
In other news: Kroll gets SIM-swapped in attack targeting crypto platforms; MOVEit hack victim count reaches 1,000; and another spyware maker gets hacked.
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Seven malicious packages have been found and removed from Crates, the official package repository for the Rust programming language, marking the second time malware has been found on the portal. [This is the first-known incident, if anyone's curious.]
The packages were discovered by DevSecOps company Phylum, which described them as showing "the hallmarks of early preparations for a broader campaign."
All seven packages were initially published with no content and then received incremental updates over a few days with suspicious code.
This code was secretly gathering information on infected platforms and sending the data to a remote Telegram channel.
Phylum says it has seen similar patterns in campaigns that hit other package repositories and was expecting the attacker to ship future updates with more malicious content as it identified and separated test machines from systems worthy of infection.
All seven packages used typosquatting—names that were similar to more popular libraries—as a way to draw attention to themselves and trick developers into accidentally using them for their projects.
Phylum didn't provide any details on the attacker, but package repositories have usually been the hunting ground of four types of entities:
Crypto-mining operators;
Low-level threat actors targeting to collect and steam passwords and infrastructure credentials to resell online;
The teen hacker groups interested in collecting Discord and Steam-related credentials;
North Korean APT groups targeting to compromise developers and use their machines for intrusions at larger companies or for supply chain attacks.
The last category is the one everyone is particularly worried about since its activities have recently ramped up.
Just at the end of July, GitHub published a security alert warning that North Korean hackers were posing as software engineers and asking developers at established companies to work on joint projects. Many of these projects contained malware or imported malicious npm (JavaScript) packages.
With Rust seeing increased adoption among software companies primarily due to its top-of-the-line memory safety features, it should not be a surprise if threat actors turn their gaze on its ecosystem as well.
With Crates featuring the same super-lax package submission practices seen on npm and PyPI, Rust's ecosystem is just as ripe for exploitation.
Breaches, hacks, and security incidents
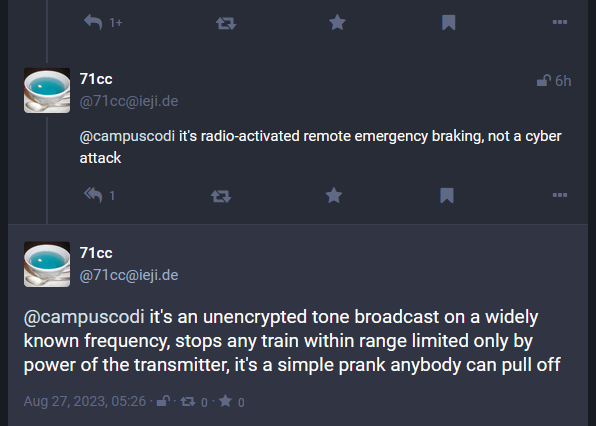
Incident disrupts Polish railway: Suspected Russian saboteurs have disrupted the services of Poland's national railway system. Officials say the attackers broadcast an emergency stop signal on a frequency used by the country's train system. The signal caused around 20 trains to come to an emergency stop for a few hours near Szczecin, a port city near the German border. Officials say the emergency signal was mixed with Russia's national anthem and a speech by President Vladimir Putin. [Additional coverage in the BBC]
WebDetetive hack: Hackers claim to have breached and deleted victim data from the servers of Brazilian spyware maker WebDetetive. The hackers say the company's Android spyware was installed on more than 76,000 devices from where it was collecting geolocation data, call logs, photos, and social media activity. The group says it breached WebDetetive after exploiting vulnerabilities in its web dashboard, which allowed it to download the database and delete victim data. [Additional coverage in TechCrunch]
Breach at France's unemployment agency: French unemployment agency Pôle Emploi says that hackers stole the personal details of more than 10 million French citizens. The breach occurred at one of the agency's service providers. Affected users include French citizens who registered on its website prior to February 2022. Stolen information only includes full names and social security numbers.
Kroll SIM swapping incident: Risk management provider Kroll says that an attacker SIM-swapped one of its employees and gained access to the data of three cryptocurrency platforms. The company says the hacker stole bankruptcy claims filed by the users of BlockFi, Genesis, and FTX. All three companies are currently undergoing Chapter 11 bankruptcy procedures in the US. The incident took place on August 19 and targeted the T-Mobile number of one of Kroll's US employees. [Additional coverage in KrebsOnSecurity]
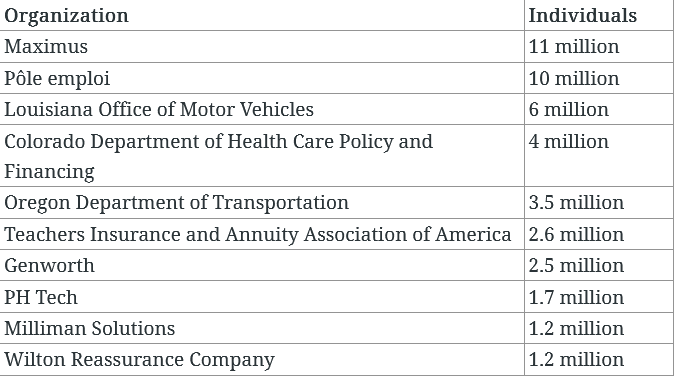
MOVEit victim count reaches 1K: The number of companies impacted by Clop's MOVEit hacking spree has formally reached 1,000, according to security firm Emsisoft. So far, the Clop gang is believed to have gained access to the personal data of more than 60 million people. US government contractor Maximus disclosed the largest breach, with 11 million users impacted.
General tech and privacy
Open-source manifesto: The Open Source Security Foundation has published an open-source consumption manifesto. The new document is basically a commitment from some software makers to improve the security of their supply chains.
Apple-v-Corellium update: A judge has denied Apple's request to re-hear its copyright case against Corellium, a company that makes an iOS simulator. [Additional coverage in Law360]
7-Zip: People on Reddit seem to think the 7-Zip website was hacked. To be investigated.
Chrome extensions on Firefox: Firefox users can now import and run Chrome extensions in their browser. This is not possible because both browsers now run on the same WebExtensions API system. There's some trickery involved. [Additional coverage in GHacks]
"Mozilla decided to create a list of extension pairs for extensions that are available on the Chrome Web Store and the Mozilla Add-ons Store. Instead of importing the Chrome extension directly, Firefox is installing the Firefox version of the extension from Mozilla's own extension store."
Dropbox caps unlimited storage plan: File sharing and synchronization service Dropbox has capped its unlimited business storage plan. The company made the decision after dealing with several cases of major abuse. Dropbox says it detected customers using its servers for cryptomining and even reselling storage. The company says the abusive customers were using "thousands of times more storage" than legitimate customers, which was risking Dropbox's business performance and sustainability. Dropbox has now capped all unlimited business plans to 15TB of storage.
Bot master extraordinaire: An investigation by web developer Travis Brown has found that around 70% of Elon Musk's Twitter followers are likely bot accounts there to just inflate his follower numbers. This explains why Musk recently claimed Twitter's userbase jumped to 540 million users after it's been plateauing at around 300 million for years. [Additional coverage in Mashable]
Mastodon gets search feature: Mastodon has added support for full-text search, one of its most requested features. Users who want their posts to be searchable will have to change a setting in their profile—see link. Search modifiers/filters are also available.
Government, politics, and policy
Hunt forward mission: US CyberCom says it successfully conducted another hunt forward mission at the request of the Lithuanian government. The mission lasted three months and involved hunting for malware on Lithuanian national defense systems and Ministry of Foreign Affairs' networks.
Creative Diplomacy: The NYT has a profile on Creative Diplomacy, an FSB-controlled Russian NGO that recruits and trains Western social media influencers and academics to spew Russian propaganda in their countries. [Additional coverage in the NYT/non-paywall]
Cobwebs Technologies: Media NGO Unicorn Riot has a profile on Cobwebs, the Israeli tech firm that helped the DHS spy on George Floyd protesters in 2020.
Predatorgate: Something we missed last month was that Greece's data protection authority said that 92 individuals have been targeted with the Predator spyware in the Predatorgate spying scandal.
CERT-RU's juice-jacking warning: Russia's CERT team has published an animated video warning against charging smartphones via public USB ports, a threat known as juice-jacking. I guess the overblown juice-jacking craze has now spread from the US to Russia.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Chris St. Myers, Threat Intelligence Lead at Stairwell, on how the company Inception platform can be used for finding old or new threats that sometimes may go unnoticed.
Cybercrime and threat intel
Indian scam center disrupted: Indian authorities have dismantled a call center in the city of Noida that conducted Social Security scams targeting American citizens. Police detained 84 employees, including the call center's two administrators. Officials say the call center used leaked data to contact victims posing as the US Social Security Administration in order to demand money. The call center contacted more than 400,000 Americans and succeeded in scamming 600. [Additional coverage in the Indian Times]
New npm malware: Thirty-nine malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details. Phylum has a write-up on one of them that deployed pen-testing tools on infected systems and contained some clever dual HTTP-DNS data exfiltration mechanism.
Proxyware hits MS-SQL servers: South Korean security firm AhnLab says it is seeing an increase in proxyware malware being installed on MS-SQL database servers. Most of the compromised servers use weak and easy-to-guess passwords. In some instances, the attackers also deployed a cryptominer alongside the proxyware script.
Lockbit clones: Kaspersky looks at how the Lockbit builder leaked code has been used in the wild by other ransomware gangs. The company says it has identified 396 different samples based on the code so far.
Malware loader stats: Security firm ReliaQuest says that roughly 80% of malware incidents can be traced back to three loader families—QBot, SocGolish, and Raspberry Robin.
BEC campaign breakdown: Cluster25 has an analysis of a recent BEC campaign they've been tracking.
BEC sees spike in 2023: Security firm Trustwave says it saw a noticeable increase in BEC activity at the start of 2023. The company says that half of the BEC lures it saw in the first half of the year were payroll diversion attacks, a tactic where attackers pretend to be employees of the targeted company and try to redirect the payroll to their own bank account. Trustwave says this tactic is extremely efficient because it's not uncommon for workers to change their bank account information for legitimate reasons.
Malware technical reports
ADHUBLLKA ransomware: Netenrich researchers look at new versions of ADHUBLLKA, a ransomware strain used to target individuals and small businesses with small ransom demands ranging from $800 to $1,600. The ransomware is also known as BIT, LOLKEK, OBZ, U2K, and TZW, and has been active since 2019.
Antibot tool: InQuest researchers look at the history of Antibot, an open-source tool that started as a GitHub project but is now one of the go-to solutions used to filter bot and authentic traffic on phishing sites and other malware control panels. The company believes the service is being operated by an Indonesian man named Eka Syahwan.
BLISTER: Elastic's security team analyzes the latest version of the BLISTER loader.
"New BLISTER update includes keying feature that allows for precise targeting of victim networks and lowers exposure within VM/sandbox environments.
BLISTER now integrates techniques to remove any process instrumentation hook and has modified its configuration with multiple revisions, now encompassing additional fields and flags."
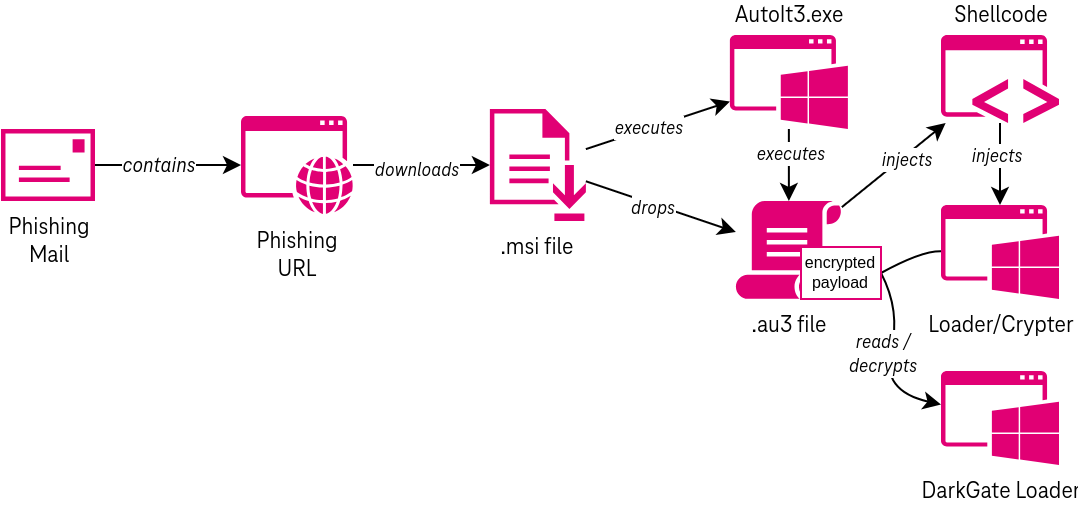
DarkGate: Malwarebytes and Deutsche Telekom researchers have a report on DarkGate (aka MehCrypt), a MaaS service that relaunched in June this year. Based on the two reports, the malware appears to be very popular already, being used in malspam, phishing, malvertising, and with SEO poisoning campaigns.
Sponsor Section
Stairwell's Mike Wiacek demonstrates Stairwell's file analysis and threat detection platform to Risky Business host Patrick Gray. Stairwell helps you monitor and analyze every executable file in your organization, automatically collecting crucial intelligence and providing your security team with in-depth visibility and detections.
APTs and cyber-espionage
APT37: Chinese security firm KnownSec has a report on North Korean hacking group APT37, also known as ScarCruft and Reaper. The report also covers the group's newest RAT known as FakeCheck.
Flax Typhoon: A Chinese state-sponsored hacking group named Flax Typhoon has been launching attacks against Taiwanese organizations since mid-2021. The group prioritizes stealthy and long-term intrusions, and its arsenal is primarily focused on open-source and LOLBins-based tools. Microsoft says that besides the bulk of its targets in Taiwan, the group has also been linked to some intrusions in Europe and Latin America.
Vulnerabilities, security research, and bug bounty
Ivanti Avalanche PoC: Proof-of-concept code has been published for an Ivanti Avalanche stack overflow vulnerability (CVE-2023-32560).
Juniper SRX and EX PoC: Security researchers from watchTowr have published a technical analysis and proof-of-concept code for CVE-2023-36844, an RCE in Juniper SRX and EX devices.
WinRAR PoC: A PoC was also published for CVE-2023-38831, the WinRAR zero-day that was used to hack stock and crypto traders.
Power Platform vulnerability: Secureworks has a write-up on a Microsoft Azure AD Power Platform privilege escalation vulnerability they found back in April.
Moodle vulnerability: SonarSource has a deep dive into CVE-2023-30943, a vulnerability they discovered in the Moodle LMS.
US govt VDP: CISA says 40 US government agencies are currently running a vulnerability disclosure program through which they receive bug reports from security researchers. The programs received more than 1,300 bug reports last year, with more than 1,100 bugs receiving fixes.
"Had a single one of the 1,119 remediated vulnerabilities been exploited, resulting in a full data breach, the federal government may have spent an estimated $4.35 million in response and recovery, with each vulnerability adding additional spending on response activities."
Infosec industry
x33fcon videos: Talks from the x33fcon Europe 2023 security conference, which took place at the end of May, are now available on YouTube.
Wiz considering SentinelOne acquisition: Israel-based cloud security firm Wiz is considering buying SentinelOne. [Additional coverage in Bloomberg/non-paywall]
New tool—Keybleed: Cryptocurrency recovery service Unciphered has launched Keybleed, a web service that lets users submit a public key and know if their crypto-wallet private key is vulnerable to known exploits or weak RNG. The company described the service as Have I Been Pwned for crypto-wallets.
New tool—MKAT: Datadog's security team has open-sourced MKAT (Managed Kubernetes Auditing Toolkit), a tool for auditing Kubernetes environments.
"It is focused on Amazon EKS at the moment, and will be extended to other managed Kubernetes environments in the future."
New tool—HVCI-loldrivers-check: Security firm Trail of Bits has released HVCI-loldrivers-check, a tool to check which drivers from LOLDrivers.io website are not blocked by a PC's local HVCI blocklist.
DEFCON health alert: Security researchers who attended the Black Hat and DEFCON security conferences in Las Vegas at the start of the month and stayed at the Caesars Palace Hotel and Casino should be aware that cases of Legionnaires' disease had been reported among hotel guests. (h/t James McMurry)
Risky Business Podcasts
In this joint Risky Business and Geopolitics Decanted feature interview, Patrick Gray and Dmitri Alperovitch talk to Illia Vitiuk, the Head of the Department of Cyber and Information Security of the Security Service of Ukraine (SBU), about the cyber dimension of Russia's invasion of Ukraine.