Risky Biz News: Lazarus steals $54 million from CoinEx crypto-exchange
In other news: US wants countries to commit to not paying ransoms; Caesars paid $15 million ransom; and Meduza head infected with Pegasus spyware.
This newsletter is brought to you by Red Canary, your Managed Detection and Response ally. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
North Korean hackers known as the Lazarus Group have stolen $54 million from the CoinEx cryptocurrency exchange.
The hack took place on Tuesday, September 12. In a statement, CoinEx said the hackers identified a leak of some of its private keys and used them to steal Ether, Tron, and Matic assets from some of the company's hot wallets.
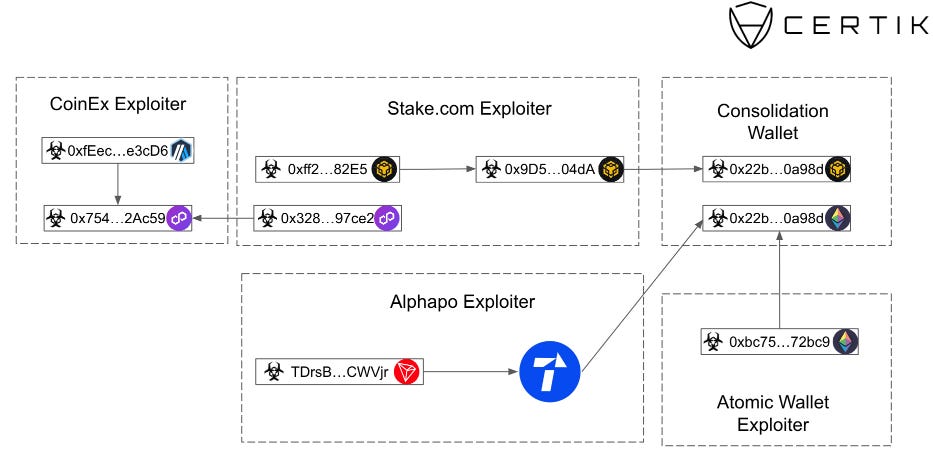
The company didn't formally link the hack to North Korea, but a blockchain investigator named ZachXBT found that some of CoinEx's stolen funds were sent to the same address that is storing funds stolen from the recent hack of the Stake.com crypto-gambling site.
The FBI linked the Stake.com hack to Lazarus, a North Korean hacking group also known as APT38 and TraderTraitor.
The same group is believed to have stolen $300 million worth of crypto assets throughout 2023. This includes more than $60 million worth of assets from Alphapo, $37 million from CoinsPaid, $100 million from Atomic Wallet users, $41 million from Stake.com, and the recent $54 million from CoinEx.
A CertiK report also confirmed ZachBXT's findings, sharing additional connections between the CoinEx attack and the group's other hacks.
In a report published last year by South Korea's intelligence service, NIS says North Korean hackers have stolen more than $1.2 billion worth of cryptocurrency and other virtual assets in the past five years. Half of that sum was stolen in 2022 alone.
Breaches, hacks, and security incidents
Caesars hack and ransom payment: The Caesars hotel and casino chain has paid a $15 million ransom to a hacking group known as Scattered Spider. The hack took place earlier this month after the group social-engineered an employee at one of Caesars' IT providers and then moved to Caesers' network. In SEC documents, Caesars says it paid the ransom after the hackers threatened to leak sensitive customer data. According to multiple sources, the Scattered Spider group is believed to have also hacked MGM Resorts this week in a similar fashion. The MGM incident is still ongoing and has caused a prolonged IT outage at the company's US properties. In the MGM incident, the Scattered Spider group is believed to have either deployed the AlphV ransomware themselves or sold access to MGM's network to the AlphV gang. [Additional coverage in Bloomberg/non-paywall in Yahoo News]
Retool hack: DevOps company Retool says hackers gained access to 27 accounts for customers from the cryptocurrency industry. The hack took place in August after the attackers used a deepfake voice for one of its employees to trick its IT desk into resetting the MFA protections on the company's Okta admin account. Retool says the attacker then used the account to hijack its internal network and pivot to customer environments. Okta warned its customers at the end of August that hackers were targeting IT help desks with requests to reset MFA protections for the super admin account. Retool is the first company to come forward and disclose a hack related to the wave of Okta hacks.
Rollbar data breach: A security incident also took place at another DevOps company named Rollbar, which is currently notifying customers of a data breach that took place last month. The company has reset all customer tokens after a threat actor gained access to its internal network. Rollbar says the attacker initially tried to run a crypto-mining operation with its resources, and when that failed, started poking around for other data.
MalindoAir data leak: The data of more than 4.3 million MalindoAir (now owned by Batik Air) customers has been leaked online and indexed by the Have I Been Pwned service. The company was allegedly hacked in 2021, according to reports. It marks the company's third major after suffering similar breaches in 2019 and 2013.
Airbus leak: A threat actor named USDoD has dumped the data of 3,200 Airbus vendors and employees on an underground hacking forum. According to threat intel company Hudson Rock, the hacker used the account of a Turkish Airlines employee who had access to Airbus IT portals. As infosec reporter Brian Krebs notes, this is the same threat actor who compromised the FBI's InfraGuard system in late 2022.
General tech and privacy
SMB NTLM blocking: Microsoft has announced an upcoming feature in Windows 11 that will block sending NTLM hashes via outbound SMB connections. The feature is meant to block incidents where attackers trick an SMB client into sending an NTLM authentication hash to a remote system the attacker controls. The feature is currently under testing in Windows 11 Insider builds. There's also a new feature in the works that will let admins control which SMB version dialect is allowed to run.
Twitter in trouble with the FTC: The US FTC says Elon Musk made decisions that impacted Twitter's data security and privacy practices in violation of a 2022 order. The order, which predates Musk's acquisition, required that Twitter implement data access safeguards and privacy audits, which the FTC says Twitter is not following anymore. [Additional coverage in Axios]
Twitter not removing hate speech: A study by the Center for Countering Digital Hate has found that Twitter is failing its moderation duties and not removing hate speech from its platform. I don't think you need a study to tell us this one.
WordPress ActivityPub plugin: WordPress now has an official ActivityPub plugin for Fediverse cross-posting.
Switzerland joins Mastodon: After the Netherlands, Germany, the EU, and others, the Swiss government is now on Mastodon too.
Government, politics, and policy
DOD Cyber Strategy: The US Department of Defense has published an unclassified version of its 2023 Cyber Strategy four months after presenting a classified version to Congress. The Pentagon says the new Cyber Strategy is grounded in the DoD's real-world experiences and draws on lessons learned from the recent conflict in Ukraine. Principles outlined in the strategy include improving cyber partnerships with US allies, defending forward, and a focus on building a resilient cyber force. The document outlines China and Russia as the US' top adversaries in cyberspace.
US National Cybersecurity Alert System: CISA is trying to pitch the idea of a national cybersecurity alerting system that would warn companies and citizens about major cybersecurity incidents. [Additional coverage in The Record]
US Army to focus on OSINT: The US Army's intelligence leaders plan to prioritize data collection from publicly available sources and commercial data. Officials are increasing training and plan to make Army OSINT courses more widely available across the intelligence community. The Army's new approach was detailed in a private OSINT strategy document published this summer. The Army's deputy chief of staff for intelligence says OSINT sources have proven invaluable to military operations in both the Afghanistan war and Russia's invasion of Ukraine. [Additional coverage in Federal News Network]
White House and no more ransoms: The White House has asked countries part of the Counter Ransomware Initiative to publicly commit not to pay ransoms to cybercriminals. The White House wants member states to issue a joint statement at this year's CRI annual summit, to be held at the end of October. It is unclear if all members will commit. The Counter Ransomware Initiative launched in 2021 and currently includes 47 members. [Additional coverage in The Record]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Red Canary Principal Readiness Engineer Gerry Johansen about the need to prepare and drill IR plans in advance and why that's just as important as the IR playbook itself.
Cybercrime and threat intel
French prosecutors appeal PyLocky case: French prosecutors have appealed a judge's decision to dismiss the case against the author of the PyLocky ransomware due to clerical errors in one of the court documents. The case against Hamza Bendelladj was dismissed at the end of August. French prosecutors had accused 34-year-old Hamza Bendelladj of orchestrating attacks with the PyLocky ransomware against French companies from his prison cell in the US but Bendelladj's legal team argued that court documents included wrong citations that referenced the JobCrypter ransomware and not PyLocky. [Additional coverage in ZDNet France]
Pegasus hits Meduza head: Security researchers have found traces of the Pegasus spyware on the iPhone of Galina Timchenko, the head of Russian independent news agency Meduza. The phone was infected around February 10 this year via the PWNYOURHOME exploit, according to a joint report from AccessNow and CitizenLab. The infection took place a day before Timchenko was supposed to attend a private meeting with other exiled heads of Russian independent media to discuss topics related to the Putin regime. Neither AccessNow nor CitizenLab attributed the infection to any threat actor or government.
Spyware firms weaponize online ads: A Haaretz investigation has discovered that several Israeli cyber companies have developed technologies capable of using online ads to deploy spyware on targeted devices. The report identifies NSO Group, Insanet, and Rayzone as companies that have developed products that can weaponize online ads. Of the three, Hareetz says only Insanet and Rayzone received permission from the Israeli government to sell its technology overseas. [Additional coverage in Haaretz/non-paywall]
Phishing campaign hits hotels: Perception Point researchers have identified a complex phishing campaign targeting hotels around the world with infostealers such as Vidar, Lumma, or StealC. This seems to be related to a campaign Trend Micro spotted earlier this year.
Ransomware campaign: The same Trend Micro says it is now seeing infostealers like Vidar and RedLine being used as entry points for ransomware attacks.
PTI-257 group: Prodaft researchers have published IOCs from PTI-257, a former Wizard Spider (Ryuk/Trickbot/Conti) member who is currently working as a Lockbit RaaS affiliate.
Joint statement on deep fakes: CISA, the FBI, and the NSA have published a joint advisory on the exponential increase of deep fakes online. The US agencies say there are "limited indications of significant use of synthetic media techniques by malicious state-sponsored actors," but the technique has been seen used by "less capable malicious cyber actors." Officials expect deep fakes to grow in sophistication and increase in use as AI/ML technologies advance.
Europol cyber report: According to a Europol report published this week, malware-based cyber-attacks remain the most prominent form of intrusion into companies across the world.
VISA Biannual Threats Report: VISA's security team has published its biannual report [PDF] containing information on the most notable threats to the payments ecosystem.
Malware technical reports
MetaStealer: SentinelOne has discovered a new infostealer targeting macOS systems named MetaStealer. It is unclear if this is related to a similar infostealer targeting Windows systems, discovered last year by NCC Group.
Lydia spyware: Dr.Web has spotted new versions of the Lydia Android spyware. The malware has been used in the past to target Iranian citizens. The latest version was spotted masquerading as an Iranian online trading platform.
DBatLoader: IBM's X-Force team has a breakdown of recent DBatLoader (ModiLoader) phishing campaigns and infections. Researchers noted a general improvement of the group's phishing techniques and malware code.
3AM ransomware: Broadcom's Symantec division has discovered a new Rust-based ransomware strain named 3AM. Symantec saw the ransomware used in one attack so far, where a known ransomware affiliate deployed it on a victim's network after Lockbit was detected and blocked. The 3AM ransomware comes with a Tor-based support and payment portal but does not appear to operate a dark web leak site (yet).
AlphV Sphynx goes after Azure: In a Mastodon thread, security firm Sophos says it has discovered a version of the AlphV ransomware that contains new features designed to encrypt Azure Storage accounts. Named Sphynx, this AlphV variant was first spotted this year in March, and the new Azure encryption capabilities seem to have been added over the summer. Sophos says Sphynx attacks involve the use of a legitimate Azure customer key that allows the threat actor to disable Tamper Protection for the victim's account before proceeding with data encryption.
Sponsor Section
Timing and response plans could mean the difference between an attempted attack or a full-blown compromise. Red Canary's Incident Response & Readiness Guide arms security teams with the blueprint for a modern and effective incident response plan.
APTs and cyber-espionage
Operation Rusty Flag: Deep Instinct researchers have spotted a threat actor targeting Azerbaijani targets using lures related to the Nagorno-Karabakh military conflict in order to infect their systems with novel Rust-based malware.
APT36: Zscaler looks at the APT36 Pakistani espionage group and its updated arsenal involving a new Windows backdoor named ElizaRAT.
Lazarus' EarlyRAT: Qihoo360 researchers have published an analysis of EarlyRAT, a new malware strain developed and used by the Lazarus APT.
Konni on WinRAR: Chinese security firm Knownsec 404 says the Konni North Korean cyber-espionage group has now adopted the recent CVE-2023-38831 WinRAR zero-day for its phishing operations.
DPRK activity: According to the same Knownsec 404, APT37 (Reaper) has been one of the most active North Korean espionage groups this year.
Qihoo360 blames NSA: Chinese security firm Qihoo360 claims the US National Security Agency breached the network of the Xi'an Northwestern Polytechnical University in June of last year. Qihoo claims NSA operators used 41 different hacking tools in their intrusion. While the company made a similar attribution last year, this marks the first time Qihoo has published IOCs from the alleged intrusion. The IOCs are for a malware strain named SecondDate, first exposed by the ShadowBrokers group in 2016. Qihoo researchers say they've also worked with "industry partners from multiple countries" and have now identified 13 NSA staffers who conducted the intrusion. [English coverage in China Daily]
Peach Sandstorm: An Iranian cyber-espionage group known as Peach Sandstorm (Holmium, APT33) has conducted password-spraying attacks against thousands of organizations across the globe. The campaign began in early 2023 and targeted organizations in the satellite, defense, and pharmaceutical sectors. Microsoft says that some of the attacks were successful, and the campaign is still ongoing. In cases of a successful compromise, the group was seen pivoting to internal networks in order to facilitate intelligence collection in support of Iranian state interests. Microsoft says that while the password-spraying attacks were high-volume and noisy, the post-compromise activity was stealthy and much more sophisticated than the group's previous operations.
Vulnerabilities, security research, and bug bounty
Cisco security updates: Cisco has released six security updates.
Azure HDInsight vulnerabilities: Orca researchers have uncovered eight XSS vulnerabilities in Azure HDInsight, an Azure analytics service.
ThemeBleed vulnerability: Gabe Kirkpatrick has a write-up on ThemeBleed (CVE-2023-38146), a remote code execution vulnerability he found in the Windows Themes framework that was patched earlier this week. A PoC is included.
GitHub repojacking vulnerability: Checkmarx researchers have identified a vulnerability in GitHub's service that can be exploited to hijack other users' repositories. The vulnerability exists because of a race condition in how GitHub handles repository creation and username renaming operations. Checkmarx says it identified more than 4,000 GitHub repositories that are vulnerable to the new attack.
GitHub Actions worm: Palo Alto Networks has shown that threat actors can create worms that spread and compromise projects via GitHub Actions.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine how AI can help cyber criminals and scammers.