Risky Biz News: Ransomware gangs hit TeamCity and WS_FTP servers
In other news: Website leak exposes Russian military and intelligence centers; mandatory MFA for AWS root accounts; and Arm, Google, and Qualcomm patch zero-days.
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Ransomware groups are exploiting recently disclosed vulnerabilities in TeamCity and WS_FTP servers to breach corporate networks and ransom organizations.
The attacks are exploiting CVE-2023-42793 and CVE-2023-40044.
The first is an authentication bypass and RCE vulnerability that can allow threat actors to take full control of JetBrains TeamCity CI/CD servers. Once on the development pipeline, threat actors can pivot to other resources on a company's internal or cloud network, from where ransomware gangs can do extensive damage.
The second is a remote code execution in WS_FTP, a file-transfer application developed by Progress Software—the same company that also made the MOVEit file-sharing server, heavily exploited by the Clop gang earlier this year in hacks that impacted more than 2,000 organizations. This bug is particularly nasty because it can be exploited with one HTTPS POST request.
In both cases, exploitation began over the past weekend after proof-of-concept code was published online for both vulnerabilities. There are reports of attacks against TeamCity servers from Prodaft and attacks against WS_FTP servers from Huntress, Rapid7, and Kevin Beaumont.
Unlike previous vulnerabilities that impacted enterprise gear, these ones are in products that aren't so widely used—when compared to the likes of Citrix, Cisco, Fortinet, or VMWare products.
According to reports, there are roughly 1,200 TeamCity servers and from 550 to 4,300 WS_FTP servers connected to the internet.
Some security experts have said the numbers are too small to make threat actors care about the vulnerabilities since there are more abundant targets online that can be exploited; however, the recent attacks show the contrary.
The reality is that easy money is still easy money, especially for ransomware gangs after free exploits landed in their laps last week.
Breaches, hacks, and security incidents
ETSI hack: The European Telecommunications Standards Institute (ETSI) says hackers have stolen a database containing information on all users who registered on its website.
Lorenz leak: The website of the Lorenz ransomware gang has leaked every message ever sent through its contact form. Copies of all messages are available here.
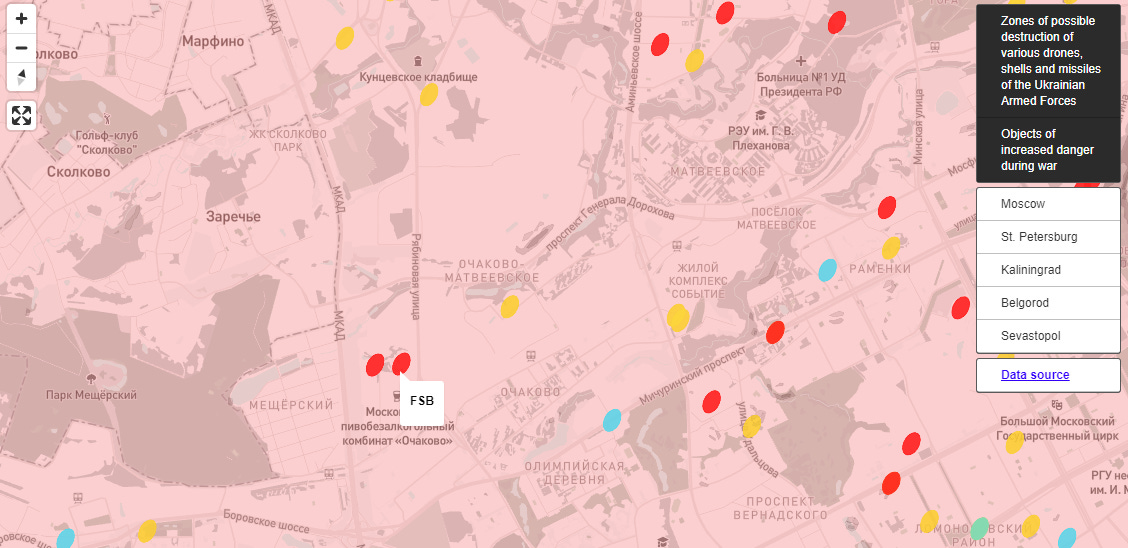
Russian intelligence leak: Moscow officials have accidentally leaked the secret locations of Russian military and intelligence facilities. The data was part of a 434-page document that was available on the website of the Moscow City Hall. The document contained a list of all "special consumers" on the Russian electricity grid—locations that should never be disconnected from the grid and where a constant flow of electricity should be made available at all times. Most of the entries in this special group included critical infrastructure objectives, such as hospitals and train stations, but the document also exposed the exact locations of facilities maintained by the Russian military and Russian intelligence agencies. The leaked data has been used to create an interactive map that reporters argue could be useful for the Ukrainian Armed Forces in selecting future targets. [Additional coverage in the Dossier Center]
General tech and privacy
Mandatory MFA on AWS root: Amazon is making multi-factor authentication mandatory for all AWS accounts with root access to an organization's management console. The change will take effect in mid-2024. Amazon plans to expand the mandatory MFA requirement to other types of accounts throughout the next year.
GCP moves security features behind paywall: Google Cloud has moved the Policy Intelligence smart access control feature from the company's free tier to its paid Security Command Center subscription plan. The Policy Intelligence feature allows Google Cloud customers to analyze IAM policies and identify cloud resources that have extensive permissions. Google's move to restrict access to crucial security features comes after Microsoft gave customers free access to 31 cloud security log types earlier this year.
Mastodon yearly report: Mastodon has published its yearly activity report for 2022. The company reported €326,000 in donations, more than 9,600 active Mastodon servers, and 5.8 million registered users (at the end of 2022).
Google announces new Gmail anti-spam features: Google has introduced new anti-spam features for companies and individuals who send more than 5,000 emails to Gmail users each day. The company says that by February 2024, all bulk senders must authenticate their email servers using modern security standards and provide an easy way for users to unsubscribe from future emails. Google says it will keep an eye on spam thresholds and mark abusive bulk senders as spam if necessary.
Google alters search results for profit: Documents from Google's anti-trust case in the US have revealed that the company is altering billions of user search queries each day in order to return search results that contain more ads. [Additional coverage in Wired/non-paywall]
"Here's how it works. Say you search for "children's clothing." Google converts it, without your knowledge, to a search for 'NIKOLAI-brand kidswear,' making a behind-the-scenes substitution of your actual query with a different query that just happens to generate more money for the company, and will generate results you weren't searching for at all. It's not possible for you to opt out of the substitution. If you don't get the results you want, and you try to refine your query, you are wasting your time. This is a twisted shopping mall you can't escape."
Google lends a hand to Twitter: After destroying its own advertising business because its CEO can't stop promoting neo-nazi ideology, Twitter has decided to rent its near-zombie ad space to Google's Ads platform. More from tech and privacy activist Lauren Weinstein.
Government, politics, and policy
Japan to switch to domestic security software: The Japanese government will switch to using domestically-developed security software during fiscal year 2025. Officials say the move is part of an effort to improve the collection and analysis of telemetry and cyberattack data. Development of the new system is scheduled to finish by the end of March next year. The new system will be compatible with Windows systems and security software from Japanese companies. [Additional coverage in Nikkei]
GAO cybersecurity report: A GAO report found that federal agencies and critical infrastructure entities need to do a better job at sharing cyber threat intel information in order to effectively tackle ever-increasing complex cyber threats.
"Long-standing challenges, such as security concerns and timeliness, make this harder. For example, representatives from a nonfederal partner said the FBI briefed them on a cyber threat about 5 months after it was identified."
European Media Freedom Act: The European Parliament has proposed an updated version of the European Media Freedom Act that includes a ban on the use of spyware against journalists. The new document does not introduce a full blanket ban. Spyware may be used against journalists as a "last resort" and on a "case-by-case basis" under judicial authority to investigate serious crimes, such as terrorism or human trafficking.
FSB wants to track geolocation data: The Russian FSB intelligence service has put forward a draft law that will require all internet service providers to store the geolocation and payment information of their users. The draft law has been filed with the Russian Parliament. If approved, the law will apply to large internet companies active in Russia. These companies are already mandated by law to store all sorts of user data, which they have to make available to law enforcement investigations. [Additional coverage in Svoboda]
Formal VPN ban incoming: Russian communications watchdog Roskomnadzor plans to formally ban mobile VPN apps starting next year. The ban is scheduled to go into effect on March 1, 2024. After that date, mobile app stores like the Google Play Store and the Apple App Store will be forbidden from listing VPN apps to Russian users. [Additional coverage in RIA Novosti]
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Selena Larson, Senior Threat Intelligence Analyst at Proofpoint, about the state of play in the cybercrime ecosystem. People and organizations are getting better at protecting themselves from scams and compromises, but criminals will use every possible avenue to reach people and scam them.
Cybercrime and threat intel
Thai crypto scammers detained: Thai authorities have arrested five members of a cybercrime group that ran investment-romance fraud operations, commonly known as "pig butchering" scams. The suspects were detained last month, and officials seized $277 million worth of crypto-assets the gang stole from victims. Thai police were aided in their investigation by Binance's security team, which also helped dismantle a second smaller criminal group involved in crypto money laundering operations.
Thunderbird ransomware warning: The Mozilla Foundation is warning customers a ransomware gang is using its Thunderbird email app as a lure to deploy ransomware and encrypt networks.
Malicious npm packages: Fortinet has a report on a set of malicious JavaScript packages spotted on the official npm repository.
Supply chain report: Threat actors have published more than 245,000 malicious packages over the past calendar year, a figure twice as large as the two previous years combined. The number shows a clear and visible increase in attacks targeting the software supply chain, according to a recent report published by DevSecOps firm Sonatype. The same report also found that software rot is also highly active in the JavaScript and Java ecosystems, where 18.6% of open-source projects maintained in 2022 had been abandoned this year.
Umbreon interview: DataBreaches.net has a three-part interview with Dutch hacker Umbreon, known for operating as DataBox and selling hacked data on the old RAID and Breached forums. See parts one, two, and three.
Malware technical reports
Mystic Stealer: OALABS has published an analysis and IOCs for the Mystic infostealer, launched earlier this year in April.
Knight ransomware: CloudSek takes a look at the Knight ransomware, a rebranded version of the old Cyclops RaaS. Knight is one of the few RaaS platforms currently active today that offers Android and macOS versions besides the classic Windows, Linux, and ESXi—although if they work, it's another matter. Knight is written in Go.
Sponsor Demo Section
This is a new demo! Ryan Kalember shows Risky Business host Patrick Gray Proofpoint's Sigma platform. Sigma is a data loss prevention and insider threat detection tool that crunches data from different sources and presents a unified view of it.
APTs and cyber-espionage
APT41's Android malware: ThreatFabric has published an in-depth analysis of two Android malware strains used by the APT41 Chinese cyber-espionage group. They're named LightSpy and AndroidControl and are the DragonEgg and WyrmSpy strains first spotted by Lookout earlier this year.
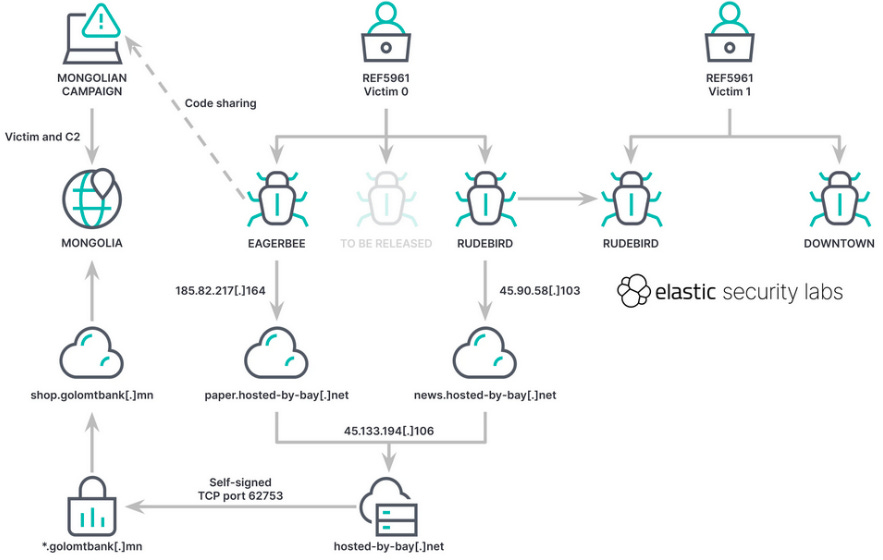
REF5961: Elastic's security team has published a report on REF5961, a cyber-espionage group they found on the network of a Foreign Affairs Ministry from a member of the Association of Southeast Asian Nations (ASEAN). Elastic says it found the group's tools next to the malware of another cyber-espionage group it tracks as REF2924. REF5961's arsenal includes malware such as EAGERBEE, RUDEBIRD, and DOWNTOWN.
"Further, the correlation of execution flows, tooling, infrastructure, and victimology of multiple campaigns we're tracking along with numerous third-party reports makes us confident this is a China-nexus actor."
Konni: ThreatMon researchers have published a report on Konni, a North Korean APT group, and its recent campaign delivering malicious ISO files.
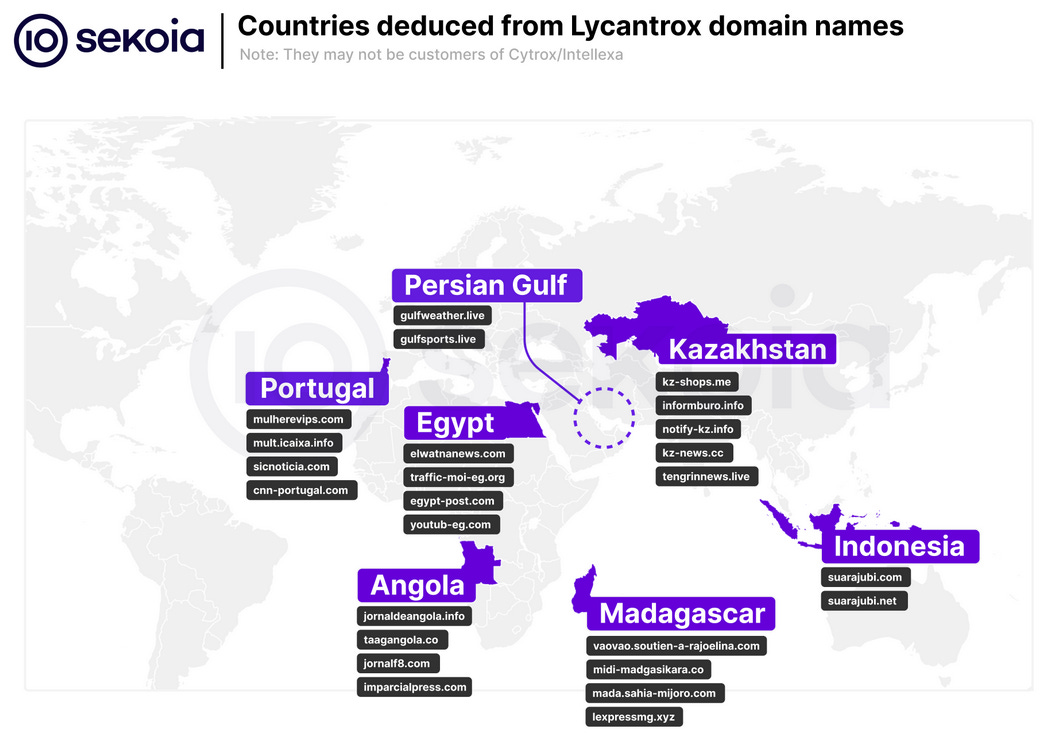
Cytrox infrastructure: French security firm Sekoia has identified domains and servers operated by spyware maker Cytrox (which they call Lycantrox). Servers appear to be located in Portugal, Angola, Kazakhstan, Indonesia, Egypt, Madagascar, and the Persian Gulf.
Vulnerabilities, security research, and bug bounty
Android patches two zero-days: The Android project has published security updates for the month of October to fix two actively exploited zero-days. The patches fix zero-days in the Libwebp library (CVE-2023-4863) and the Arm Mali GPU driver (CVE-2023-4211). The first is the same zero-day spotted by CitizenLab last month in attacks deploying the Pegasus spyware on Android and iPhone devices. Details about the second zero-day are not available, but Arm credited two Google security researchers for discovering the attacks.
Qualcomm exploitation: US chipmaker Qualcomm says threat actors are exploiting four vulnerabilities in its firmware in limited, targeted attacks. The attacks are targeting a bug patched in May 2022 (CVE-2022-22071) and three zero-days the company patched this week (CVE-2023-33106, CVE-2023-33107, and CVE-2023-33063). The attacks are targeting Adreno GPU and Compute DSP drivers. Qualcomm says it was notified of the ongoing exploitation by Google's Project Zero security team.
Recent zero-days in MSFT products: Microsoft says it reviewed its products and patched apps that are vulnerable to the recent Libwebp (CVE-2023-4863) and Libvpx (CVE-2023-5217) zero-days. Patches were made available to Edge, Teams, Skype, and various Microsoft Store extensions that support the WebP format.
Exim patches RCE bug: The Exim email server team has released patches for three of six zero-days disclosed last week by Trend Micro's ZDI project. Of the fixed zero-days, the most important vulnerability is a no-authentication remote code execution bug tracked as CVE-2023-42115. Although the vulnerability sounds bad, reports from the Exim team and watchTowr Labs say the bug is overhyped and hard to exploit.
"But in the meantime, don't panic - this one is more of a damp squib than a world-ending catastrophe."
Linux LPE: StarLabs researchers have published an analysis of CVE-2023-31248, an LPE vulnerability in the Linux kernel.
Looney Tunables: Qualys researchers have published an analysis of Looney Tunables (CVE-2023-4911), an LPE vulnerability in the GNU C Library. The bug impacts all versions released since April 2021 and primarily affects Linux distributions. Patches have been released this week.
OpenRefine vulnerability: SonarSource has discovered a ZIP slip vulnerability in OpenRefine, a Java tool for working and cleaning the format of complex and messy data.
"A Zip Slip vulnerability is caused by inadequate path validation when extracting archives, which may allow attackers to overwrite existing files or extract files to unintended locations."
ShellTorch vulnerabilities: Oligo Security has disclosed details on ShellTorch, three vulnerabilities impacting TorchServe, a server for running PyTorch machine learning processes. Of the three, the most severe is a remote code execution vulnerability (CVE-2023-43654) that allows unauthorized access to TorchServe management interfaces. Oligo says the RCE could be used to upload unauthorized data and alter ML models.
ConnectedIO router bugs: Claroty has identified several vulnerabilities in the firmware and cloud platform of ConnectedIO, a maker of 3G and 4G routers. The routers are typically used as components in IoT products to allow the devices to connect to the internet.
Infosec industry
Cybersecurity spending forecast: Research and consulting firm Gartner expects cybersecurity and risk management spending to reach $215 billion in 2024, 14.3% up from 2023. Gartner put out a positive forecast despite the recent decreases in cybersecurity investments and several rounds of layoffs across the infosec industry. The company attributes the rise in spending to the continuous adoption of cloud technologies and a large hybrid workforce.
New tool—cloudgrep: Cado Security has open-sourced cloudgrep, a tool for searching resources across S3 cloud storage servers.
"It currently supports searching log files, optionally compressed with gzip (.gz) or zip (.zip), in AWS S3."
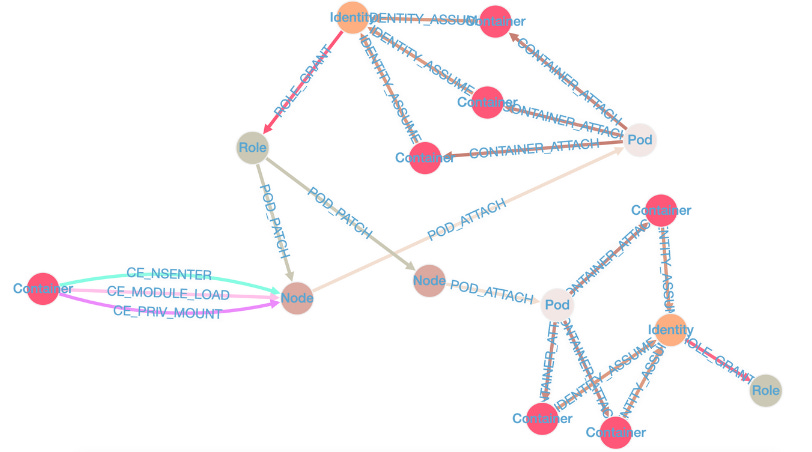
New tool—KubeHound: DataDog's security team has open-sourced a tool named KubeHound that can be used to analyze Kubernetes clusters and create graphs of possible attack paths.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine how US and UK strategies to use cyber power differ but are in some ways mirror images of each other.