Risky Biz News: Albania cuts diplomatic ties with Iran in first-ever cyber-related escalation
In other news: New APT42 group; former Conti members are now targeting Ukraine; and Patreon fires security team.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The Albanian government announced on Wednesday that it would be cutting all diplomatic relations with Iran in the aftermath of a major cyberattack, marking the first time when a cyberattack has escalated this severely in the political realm.
In a recorded video statement published on YouTube, Albania's Prime Minister Edi Rama said that after concluding an investigation into the incident, they found "indisputable evidence" that Iranian state-sponsored hackers were behind the cyberattack that took place earlier this year, on July 15, and which crippled multiple of the Albanian government's IT systems.
Rama gave Iranian diplomats 24 hours to close the embassy and leave the country. While the Iranian government denied being involved in the attack, NATO, the White House, and the UK government published statements in support of the Albanian government and its attribution of the attack to the Tehran regime.
The US called Iran's attack on its NATO ally a "troubling precedent" and promised to "take further action to hold Iran accountable."
But while Iranian officials might deny any involvement, the proof is in the pudding, and, in this case, the pudding is the malware used in the July 15 attack, which both Mandiant and Microsoft have linked back to multiple past instances of Iranian cyber-espionage operations and tooling.
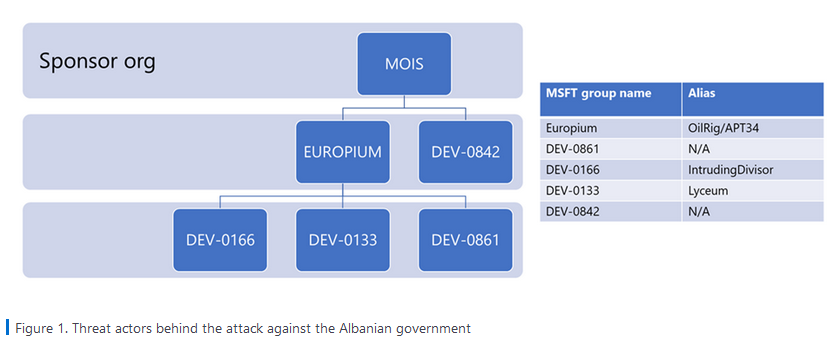
Microsoft, which was also involved in the Albanian government's response to the incident, said it was able to link the incident to four different Iranian APTs, and detailed how they worked together to breach Albanian government networks as far back as 2021, steal data, and then deploy their wiper and ransomware combo in July this year when the Iranian government decided it was time to act.
Microsoft says these four groups, listed below, appear to work under the guidance and control of the Iran Ministry of Intelligence and Security (MOIS).
DEV-0842 deployed the ransomware and wiper malware
DEV-0861 gained initial access and exfiltrated data
DEV-0166 exfiltrated data
DEV-0133 probed victim infrastructure
Both Mandiant and Microsoft say the Iranian attack is directly connected to the Albanian government harboring thousands of Iranian dissidents part of an exiled opposition party named the People's Mujahideen Organization of Iran, also known as Mujahideen-e-Khalq, or MEK.
The group found shelter in Albania in 2016, at the request of the US government, after the Iranian regime declared the group a terrorist organization and started hunting its members.
MEK members were set to hold an annual summit on July 21. The Free Iran World Summit was eventually canceled because of terrorist and bomb threats, but Microsoft says that the threats and the July 15 cyberattacks were part of a broader effort from the Iranian government to go after the group and its host country.
But while past operations typically involved coordinated social media campaigns, data leaks, and vague threats and declarations from Iranian officials, the deployment of a data wiper and ransomware appears to have crossed a line Albanian, and NATO officials wouldn't like to be crossed anymore.
While Albanian's prime minister tried to play down the aftermath of the July 15 attack and said that government systems were now restored, the attack did cripple government operations and official websites for weeks in a row. In fact, moments after Iranian officials left the embassy, Albanian police raided the building in search of any incriminatory evidence that may have survived the typical hard-drive bashing and document-burning practices of fleeing diplomats, showing that there is some very bad blood between the two countries for the time being.
The incident is still fresh, and political analysts/pundits are still probing sources for what went into this aggressive reaction from the Tirana government, but the general sentiment is that NATO partners backed and pushed Albania into its decision as a way to signal to other "cyber" aggressive countries that a line is being crossed when entire government IT networks are being wiped just because someone wants to attack a "zombie party" (taken from The Grugq excellent analysis of the incident).
In his view of the incident, my colleague Tom Uren also sees this entire incident as Iran going overboard, and Iran's attack on Albania also reminds me of a Reddit comment I once read—"using the Death Star laser to kill a fly."
Attacking government systems with wipers to stop a conference is totally disproportionate and unreasonable, so a strong response is needed to prevent these types of attacks being seen as acceptable. We'll have to wait and see if this step by the Albanians will be enough to discourage Iran from engaging in similar activities elsewhere in the future.
Breaches and hacks
Some Axie funds were recovered: In a blog post on Thursday, blockchain analysis company Chainalysis said the US government was able to recover around $30 million worth of cryptocurrency from wallets linked to the Lazarus Group, representing part of the cryptocurrency that was stolen from crypto game Axie Infinity. The funds were stolen in March 2022, when Lazarus hackers took more than $600 million from the Ronin Network, a sidechain built for the play-to-earn game Axie Infinity.
North Face credential stuffing attack: Apparel company The North Face said that hackers hijacked around 195,000 customer accounts for their official website after they executed a credential stuffing attack that lasted between July 26 and August 19 this year.
Shiba Inu leak: Cloud security firm PingSafe claim that the operators of the Shiba Inu crypto token (currently the 14th largest token by market cap) appear to have leaked their platform's AWS credentials.
General tech and privacy
Signal offered pro-bono post-quantum encryption protection: PQShield, a UK company specialized in providing post-quantum cryptography (PQC) technology, said it developed a system through which it can add PQC protection to the Signal secure IM service, a technology they are willing to provide to the organization for free. [Additional coverage in Help Net Security]
Ring expands E2EE: After adding end-to-end encryption (E2EE) support to some of its products last year, Ring announced this week plans to expand the feature to new products—and specifically to its line of battery-powered devices.
Lockdown Mode to go live next week: During a conference this week where it announced a new series of products, including its new iPhone 14 smartphone, Apple said that iOS 16 will launch next week, on September 12, which also means that Lockdown Mode will become broadly available to the company's users.
Let's Encrypt to support CRLs: Free-to-use certificate authority Let's Encrypt said it will finally add new infrastructure later this month that will allow it to support revoking certificates via Certificate Revocation Lists.
Norton privacy study: An academic study [PDF] performed by three researchers from NortonLifeLock found that eight out of ten websites that feature an on-site search functionality end up leaking user-performed search queries to advertisers running ads on their sites. The study analyzed the internet's top one million sites, found a search bar on 512,701 domains, and found that 81.3% of these leaked search queries.
Google takedown report: Google TAG published its summary of coordinated influence operation campaigns terminated on Google platforms in July this year. It includes bot networks linked to China and Russia.
Patreon fires entire security team: Well, this ain't good news for Patreon users.

Government, politics, and policy
EU to impose IoT security rules: The European Union is working on a set of new cybersecurity-related rules for IoT vendors that are expected to be unveiled next week and enter into effect by 2024. According to a leaked version of the upcoming Cyber Resilience Act, obtained by Euractiv, IoT product vendors will have to:
regularly test their own devices for vulnerabilities;
inform authorities and consumers about attacks;
must ship quick fixes and regular security updates for the product's entire life span;
ensure confidentiality of data, including using encryption, and more.
IoT vendors who don't comply with these requirements could risk fines of up €15 million or 2.5% of their annual turnover, whichever is higher. In addition, the EU will also have the power to recall and ban products that are not compliant.
State Department training: The US State Department said this week that they would be sponsoring a nine-day training program named "Unhiding Hidden Cobra," which will train six partner nations on the risks associated with North Korean malware and cyber activity. According to US officials, the partner nations are located in the Western Hemisphere, Africa, and Asia, and participants will be staff from computer security incident response teams and entities with similar roles from the countries' public and private sectors.
RfJ program bearing fruits: An FBI official said this week that the State Department's Rewards for Justice program, which offers money for tips on cybercriminals, has already yielded some fruits.
NSA encryption news: The NSA has published requirements for quantum-resistant (QR) algorithms that will need to be implemented by vendors and operators of national security systems in order to handle classified or critical information for military and intelligence activities.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
New exploited vulns added to KEV: CISA has added ten new vulnerabilities to KEV, its database of actively exploited security flaws. These include bugs in Android, Apple, Chrome, Fortinet, NETGEAR, QNAP, D-Link, MikroTik, and Oracle.
BackupBuddy WP plugin targeted: WAF provider Wordfence reports that threat actors are using a recently disclosed vulnerability in the BackupBuddy WordPress plugin to compromise WP sites. Both Wordfence and iThemes, the plugin's developer, said attacks against this plugin have been taking place since at least August 27, at least a week before a security update was released on September 2. From iThemes:
This vulnerability could allow an attacker to view the contents of any file on your server that can be read by your WordPress installation. This could include the WordPress wp-config.php file and, depending on your server setup, sensitive files like /etc/passwd.
RDP attacks: ESET has published a report [PDF] on RDP abuse, noting an explosion in RDP attacks since its last report on the topic back in 2020.
Intermittent encryption: SentinelOne researchers said that several ransomware gangs had adopted intermittent encryption, or partial encryption of victims' files, as a technique to speed up encryption operations and possibly evade detection by security tools. Among the groups who are using this technique are ransomware gangs like Qyick, Agenda, BlackCak/ALPHV, Black Basta, and PLAY.
Monti ransomware gang: Intel471 researchers said they found a new ransomware gang that goes by the name of Monti and appears to use a ransomware strain very similar to the now-defunct Conti, whose code was leaked online earlier this year.
Appalling and reprehensible abuse of an innocent target: AdvIntel CEO Vitali Kremez noted this week that the Cobal Strike command and control servers operated by several ransomware gangs have been getting DDOSed with anti-Russia and anti-war messages.
Killnet targets Japan: Pro-Russian hacktivist group announced this week plans to target Japanese companies and government agencies with DDOS attacks.


Malware technical reports
PlugX evolution: Security firm Cybereason has published a report on the evolution of the PlugX malware family over the past decade. First spotted in 2012, the malware was initially used by Chinese APT groups before spreading to a broader audience across the years. Currently, the malware can function as a loader and remote access trojan.
BlackCat ransomware: SecurityScorecard researchers have published a breakdown and TTPs typically during attacks with the BlackCat/ALPHV ransomware.
Spymax: ERNW researchers have analyzed Spymax, an Android remote access trojan launched back in 2019.
APTs and cyber-espionage
Former Conti members now target Ukraine: Google TAG said in a report on Wednesday that some of the former Conti affiliates and initial access brokers have been running operations targeting the Ukrainian government for months. CERT-UA has been tracking this group under the name of UAC-0098[1, 2, 3].
Iranian APT subgroup engaging in ransomware attacks: In a similar report published a few hours later, Microsoft's MSTIC team said it found that Nemesis Kitten (DEV-0270), a subgroup of the Phosphorus APT, has also been engaging in ransomware attacks as a form of "moonlighting for personal or company-specific revenue generation."
New Lazarus operations: Cisco Talos has covered recent attacks carried out by the Lazarus North Korean APT against private companies and energy providers in the US, Canada, and Japan. The company said the initial point of entry was VMWare Horizon servers and the final payloads were typically VSingle and YamaBot, and a new malware strain named MagicRAT.
APT42: Mandiant has published a report on the newly-named APT42, a cyber-espionage group they say operates on behalf of the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-IO).
The full published report covers APT42's recent and historical activity dating back to at least 2015, the group's tactics, techniques, and procedures, targeting patterns and elucidates historical connections to APT35. APT42 partially coincides with public reporting on TA453 (Proofpoint), Yellow Garuda (PwC), ITG18 (IBM X-Force), Phosphorus (Microsoft), and Charming Kitten (ClearSky and CERTFA).
In light of Microsoft's report on DEV-0270, Mandiant said they had not seen any overlaps between APT42 and DEV-0270, which Mandiant tracks as UNC-2448, but said that the latter "may also have ties to the IRGC-IO" based on documents leaked by the Lab Dookhtegan Telegram account.
Mandiant also addressed the topic of APT35 and APT42 and their connections to the IRGC:
Mandiant assesses with moderate confidence that both APT35 and APT42 operate on behalf of the IRGC but originate from different missions and contracts or contractors based on substantial differences in their respective targeting patterns and tactics, techniques, and procedures.

Charming Kitten: Certfa researchers have published a review of Charming Kitten APT operations, focusing on the group's social engineering tactics, and especially on their recent modus operandi that revolves around impersonating experts in Middle East topics to set up audio or video calls with their targets, hoping to lure them on malicious sites or malware downloads.
Bronze President: Secureworks researchers have published a report on attacks carried out by the Bronze President Chinese cyber-espionage group during June and July 2022. The attack targeted government officials in Myanmar and Vietnam.
Vulnerabilities and bug bounty
Vulnerability disclosure drama: Ukrainian security researcher Vladislav Iarmak says VPN software maker nthLink is pressuring GitHub to take down a page where he disclosed a vulnerability in their product.


Go launches vulnerability database: The team behind the Go programming language launched this week a new website meant to serve as a global database for security flaws in the Go language and its libraries.
Windows Credential Guard bugs: James Forshaw, a security researcher with Google Project Zero, has released details about CVE-2022-34712, a leak in the Windows Defender Credential Guard security system that could be used for Kerberos key disclosure attacks.


Infosec industry
BSides LV videos: Talks from the BSidesLV 2022 security conference, which took place in early August, are now available on YouTube.
Recap: Resmo's Mustafa Akın has a cool recap of the recent fwd:cloudsec and AWS re:Inforce 2022 cloud security conferences. (via Clint Gibler's cool tl;dr sec newsletter)
New tool—wtfis: Security engineer @pirx has open-sourced a new tool named wtfis, a command-line tool that gathers information about a domain, FQDN, or IP address using various OSINT services.
New tool—EvilGoPhish: Security researcher Dylan Evans took an idea expressed in an Outpost24 blog post and created EvilGoPhish, a mash-up of Evilginx and GoPhish, two very popular phishing toolkits.
New tool—Monkey365: NCC Group has open-sourced Monkey365, a PowerShell module that can be used to review the security posture of a Microsoft cloud environment. The tool, presented at BlackHat last month, can scan for potential misconfigurations and security issues across Azure, Azure AD, and Microsoft 365 accounts.
Some advice for newcomers: WannaCry-fame and Kryptos Logic security researcher Marcus "MalwareTech" Hutchins published an interesting video over the summer on things he wished he knew when he started out in cybersecurity, which is actually a pretty good listen.