Risky Biz News: Apple and Google release new spec to combat the use of Bluetooth devices for unwanted tracking
In other news: Japan to boost cyber force by 20K; India bans 14 secure messaging apps; Israel power outages were the result of technical issues, not cyberattacks.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Apple and Google have put forward a new technical specification that aims to combat the misuse of Bluetooth devices (such as AirTags) for unwanted tracking.
The new spec introduces a universal interface that can detect when a Bluetooth device keeps following a smartphone or tablet and show an alert warning the owner of potentially unwanted tracking.
The new spec will allow Bluetooth device makers to trigger alerts on both platforms with the same code instead of having to worry about different iOS and Android standards.
The specification's first draft has been submitted for public comment and approval at the Internet Engineering Task Force (IETF), and Apple and Google say that a production-ready version of the specification is expected to be ready by the end of the year, after which, it will make its way in future versions of both Android and iOS.
Several vendors have already agreed to support the specification in future products, such as Samsung, Tile, Chipolo, eufy Security, and Pebblebee.
The news comes after several reports that devices like Apple AirTags have been abused over the past year for stalking and for criminal schemes.
Beyond your typical cases of jealous individuals tracking the movements of their partners, AirTags have become the darlings of car thieves. In most of the reported cases, thieves placed AirTags on expensive cars parked in public spaces, followed them to their owner's home, and stole them from private residences, where the chances of getting detected are much smaller.
But AirTags and similar tracking devices are not inherently bad. As Apple VP Ron Huang explains, AirTags were created to give users "peace of mind knowing where to find their most important items."
The perfect example for this came this week when the New York Police Department asked car owners to place an AirTag in their cars to help officers easily track and recover cars in case they ever get stolen.
Google plans to share more on the specification at its upcoming I/O 2023 developer conference, to be held next week.
Breaches and hacks
US Marshals Service ransomware attack: The US Marshals Service is still grappling with the aftermath of a ransomware attack that hit its computer systems in mid-February this year. The Washington Post reports that ten weeks after the attack, a computer system used to hunt fugitives is still down and inoperable. Operated by the Marshals Service Technical Operations Group (TOG), the system is used to track criminal suspects by collecting and aggregating data from their cell phones, emails, or internet use. The system was shut down after the ransomware attack and has not yet been restored.
Israeli power outages, not a cyberattack: The Israel Electric Corporation says the massive power outages that hit Israel last week, on April 27, were the result of excessive consumption and a malfunction at one of its Haifa power stations and not because of a cyberattack. The IEC put out the statement after a pro-Kremlin hacktivist group named Anonymous Sudan took credit for causing the outages. The group never provided evidence beyond a Telegram post after the outages were broadly reported in Israeli media. They then immediately made threats of impending cyberattacks targeting the US. The cringe is real. [Additional coverage in ynetnews]
T-Mobile's second 2023 breach: US wireless carrier T-Mobile says a threat actor gained access to the account data of its customers, including their account PIN codes. In a letter filed with the Maine Attorney General's Office, T-Mobile says the breach took place between February 24 and March 30 this year. The incident marks T-Mobile's second security incident this year and its ninth since 2018.
Bitmarck cyberattack: German IT provider Bitmarck has shut down all customer and internal IT systems following a cyberattack. The incident took place on April 30 and is suspected to have been a ransomware attack. The company claims it found no evidence of data exfiltration (at least, yet). Bitmarck's primary customer base is healthcare organizations in German-speaking countries.
Level Finance crypto-heist: DeFi platform Level Finance has lost $1 million worth of crypto assets after a threat actor exploited a vulnerability in one of its smart contracts. The company says that more than 214,000 of its own LVL tokens were stolen and converted into 3,345 BNB (Binance coins). Level Finance says it deployed a fix within 12 hours of the hack and plans to release a post-mortem report in the coming days.
General tech and privacy
Chrome to drop HTTPS lock icon: Google has announced plans to remove the HTTPS lock icon from the Chrome web browser address bar with Chrome version 117, set for release in early September 2023. Google will replace the infamous lock with a new tune icon that will provide users with the typical website certificate information that would be normally shown when pressing the old lock. Google cited the ubiquitous use of HTTPS, which is used for most web traffic. Going forward, instead of showing the lock icon, Chrome will show alerts when users navigate to a website over unencrypted HTTP.
Rapid Security Response: Apple has used a new security feature called "Rapid Security Response" for the first time this week to deliver security updates for iOS and macOS. Announced last year at WWDC, Rapid Security Response is a new update mechanism that was added in iOS 16 and macOS 13 and which allows Apple to deploy security updates to its devices as separate standalone patches without needing to update the entire operating system. Current evidence suggests that Apple patched a Safari bug. This marks the first time Apple has used the new feature on its stable operating systems. Previously Apple provided some Rapid Security Response updates to its beta testers to make sure the feature was working. Despite this, some users reported on social media that the RSR update failed to install on their devices. [Additional coverage in BleepingComputer]
WordPress drops Twitter: Automattic has announced it plans to remove the ability to automatically share new WordPress content on Twitter through its Jetpack Social plugin. The company cited Twitter's latest API changes and expensive API costs. Instead, the company plans to add auto-sharing for Instagram and Mastodon. The change affects all WordPress.com-hosted sites and individual sites where the Jetpack is installed.
Mastodon to get support for quote posts: Mastodon has announced a slew of new changes driven by the huge influx the platform has been getting. New features include quote posts, improved content and profile search, and support for groups. In addition, all new Mastodon users will be onboarded on mastodon.social, instead of having them pick their instance—a process many users found confusing and overwhelming.
AI-generated news sites: NewsGuard has identified 49 news and information sites that appear to be almost entirely written by artificial intelligence software. The sites span seven languages (Chinese, Czech, English, French, Portuguese, Tagalog, and Thai), produce content on a variety of topics, and publish hundreds of articles a day. None disclose their ownership or that they publish AI-generated content, lending researchers to believe that "a new generation of content farms is on the way."
Mozilla acquires Fakespot: Mozilla has acquired Fakespot, a service for detecting fake shopping reviews. Mozilla plans to integrate the service in future versions of Firefox.
Government, politics, and policy
ACSC calls for passphrases: The Australian Cyber Security Centre is recommending that users and companies move away from passwords and start using passphrases. Typically made up of 4 or more random words, passphrases are much harder to brute-force by attackers due to their length but are easier to remember compared to passwords. The ACSC says that users should aim for passphrases that contain at least four words and are at least 14 characters long.
India blocks 14 secure messaging apps: The Indian government has banned 14 secure instant messaging applications. Officials say the apps are being used by terrorists to spread propaganda and incite riots in India's Jammu and Kashmir provinces. The list of banned apps includes Crypviser, Enigma, Safeswiss, WickrMe, Mediafire, Briar, BChat, Nandbox, Conion, IMO, Element, SecondLine, Zangi, and Threema. [Additional coverage in AbpLive]
CSE scolded by watchdog: A Canadian government intelligence watchdog (NSIRA) has scolded the country's foreign signals intelligence agency (CSE) for failing to properly take into account international law during cyberspace operations that took place in 2019. The report was compiled in 2020 and was made public last week. Other subsequent NSIRA reports covering CSE's operations were also put together but have not yet been made public.
Japan to boost cyber force: Japan's Ministry of Defense plans to increase the ranks of its cyber force by more than 20,000 over the next five years. The new cyber personnel will be integrated into Japan's Self-Defense Forces, which currently includes just 540 cyber specialists. The hiring spree will take place in several steps. The ministry plans to increase the SDF cyber defense personnel to 2,200 by 2023 and to 4,000 by the end of 2027. [Additional coverage in Nippon.com]
Russia working on TCP/IP replacement: Russian technology experts are apparently working on new networking protocols to replace "the use of the American TCP/IP network protocol stack."
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Nine money laundering sites seized: US and Ukrainian authorities have seized nine cryptocurrency exchanges. Officials said the websites were advertised on private hacker forums and had been used to launder the profits of online scams and cybercrime operations. Officials say they seized servers in the US, Ukraine, and across Europe that helped host the portals. The nine exchanges are 24xbtc.com, 100btc.pro, pridechange.com, 101crypta.com, uxbtc.com, trust-exchange.org, bitcoin24.exchange, paybtc.pro, and owl.gold.
Operation SpecTor: Europol has confirmed that the sudden shutdown of the Monopoly dark web marketplace in December 2021 was the result of a law enforcement takedown orchestrated by German police. Almost 16 months after the initial takedown, Europol says intelligence gathered by German authorities allowed law enforcement agencies across nine countries to detain 288 of the market's vendors and seize more than €50 million in cash and virtual currencies, more than 850 kg of drugs, and 117 firearms. Europol says the arrests are part of Operation SpecTor, the agency's most successful operation against dark web markets to date.
"In terms of arrests, the operation was even more successful than previous operations codenamed DisrupTor (2020) with 179 and Dark HunTor (2021) with 150 arrests."
KEV update: CISA has updated its KEV database with three new vulnerabilities that are currently being actively exploited. The first is a vulnerability in TP-Link routers (CVE-2023-1389) that was discovered at last year's Pwn2Own hacking content and is now exploited by a Mirai botnet. The second is a variation (CVE-2021-45046) of the Log4Shell vulnerability in the Apache Log4j2 component. And the last is a security flaw (CVE-2023-21839) in Oracle WebLogic servers that was patched in January and is now abused for initial access.
TBK DVR exploitation: Fortinet says it is seeing a spike in exploitation of a five-year-old vulnerability (CVE-2018-9995) that impacts DVR products from Japanese company TBK.
GoAnywhere MFT exposure: Almost three months after a zero-day was disclosed in the GoAnywhere file-transfer application, Censys says that around 180 GoAnywhere web panels are still exposed online. The number is up from the 130 panels they detected back in February. Researchers say that around 30% of these 180 systems appear to have not been patched.
BitLocker attacks: Security researcher slipstream/RoL has published a list of all publicly-known BitLocker attacks. It's just seven entries long.
Gh0st RAT campaign: Cofense has details on a malspam campaign spreading the open-source Gh0st RAT (a 15-year-old malware, nonetheless).
LNK and CRX campaigns: Mandiant has detected threat actors abusing a combination of malicious LNK and CRX files as part of malspam operations. The technique relies on tricking users to execute a LNK shortcut files that open a local browser. This technique is different because the LNK file also contains command-line arguments that force the browser to load an attacker's Chrome extension CRX file.
Killnet rebrand: The Killnet pro-Kremlin hacktivist group has officially renamed to "PMC Killnet." The rebrand comes after the group alluded to plans to incorporate into a real business and provide hacking-for-hire services.
1877 Team: SilentPush published a profile on 1877 Team, a hacktivist group made up of Iraqi Kurds that was founded in July 2021 and has taken credit for several DDoS attacks, defacements, and doxxes over the past year. The primary targets of their operations are organizations located in the Middle East, Africa, Asia, and Western countries.
Bassterlord profile: Analyst1 has a profile on Bassterlord, a Ukrainian cybercriminal who used to work as an affiliate for the LockBit ransomware gang but has since retired (allegedly).
New ransomware operation: A new double-extortion ransomware group named Akira has been spotted. Unclear if it's the same as this Akira ransomware strain spotted way back in 2017.
Malware technical reports
KONO DIO DA coinminer: AhnLab researchers have discovered a new coinminer named KONO DIO DA that is currently being installed on poorly managed Linux SSH servers.
Satacom (LegionLoader): OALABS has published details about Satacom (LegionLoader), a malware loader that has been recently associated with the NullMixer malware operation.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
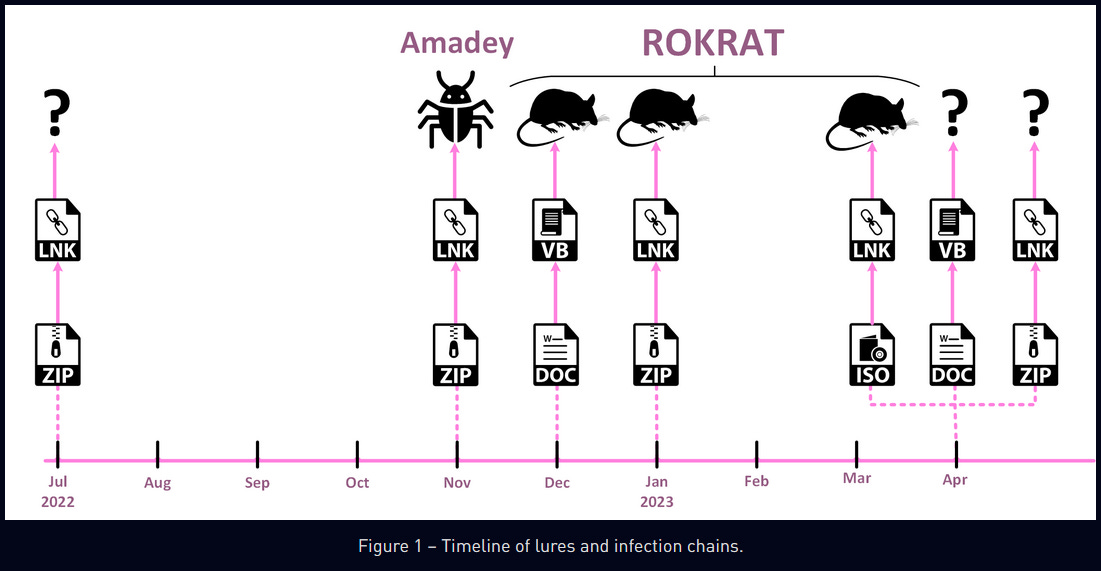
APT37: Check Point has published a report detailing the recent operations and infection chains used by the APT37 North Korean group. Final payloads included malware such as ROKRAT, Amadey, and GOLDBACKDOOR. The targets of this campaign were Korean-speaking individuals focused on South Korean foreign and domestic affairs. Similar reports were published last week by both AhnLab and Anheng.
SolarWinds incident: Wired has a long-form read on the SolarWinds supply chain attack.
Sandworm destructive attacks: Ukraine's CERT team believes that one of Russia's military cyber units, known as Sandworm (UAC-0165), has conducted another destructive cyber-attack against an unnamed government organization. CERT-UA says Sandworm used a combination of BAT and Bash scripts to destroy files on both Windows and Linux computers. On Windows, a BAT script leveraged the WinRAR application to recursively search for certain files, archive them, and then delete both the original files and the archive. On Linux, a Bash script used the built-in dd utility to rewrite files using zero-byte characters. CERT-UA says the incident is similar to another Sandworm destructive attack that hit Ukrainian state news agency Ukrinform earlier this year in January.
Earth Longzhi: Trend Micro says that Earth Longzhi, a sub-group of the APT41, has recently launched attacks on organizations in Taiwan, Thailand, the Philippines, and Fiji. Trend Micro says the new attacks come after months of dormancy (see previous report). The new campaign leveraged a technique named Bring-Your-Own-Vulnerable-Driver (BYOVD), which has gained quite the traction with North Korean cyber-espionage groups.
Iranian cyber-enabled influence operations: Microsoft says that since June 2022, the Iranian government has accelerated its cyber-enabled influence operations. The company says that of the 24 cyber influence operations it attributed to Iranian groups last year, 17 took place from June to December. The spike is obvious when compared to only seven Iranian cyber operations detected in 2021. Microsoft says that most of these operations were carried out by Emennet Pasargad (tracked as Cotton Sandstorm, aka NEPTUNIUM), a contractor for the Iranian government best known for its attempt to meddle in the 2020 US Presidential Elections.
"Iranian cyber actors have been at the forefront of cyber-enabled IO, in which they combine offensive cyber operations with multi-pronged influence operations to fuel geopolitical change in alignment with the regime's objectives. The goals of its cyber-enabled IO have included seeking to bolster Palestinian resistance, fomenting unrest in Bahrain, and countering the ongoing normalization of Arab-Israeli ties, with a particular focus on sowing panic and fear among Israeli citizens. [...]
Most of these operations have a predictable playbook, in which Iran uses a cyber persona to publicize and exaggerate a low-sophistication cyberattack before seemingly unassociated inauthentic online personas amplify and often further hype the impact of the attacks, using the language of the target audience. New Iranian influence techniques include their use of SMS messaging and victim impersonation to enhance the effectiveness of their amplification."
Vulnerabilities and bug bounty
Oracle Opera RCE: Assetnote researchers have discovered a pre-auth RCE vulnerability in Oracle Opera, a hotel property management solution widely used across the hospitality industry. Researchers say that Oracle has played down the severity of the vulnerability by claiming the vulnerability requires an attacker to be authenticated, which they show in a blog post to be false. Assetnote also says the vulnerability, tracked as CVE-2023-21932, should have also received a severity score of 10/10 instead of 7.2/10.
"There are a tonne of other vulnerabilities in Oracle Opera, some which are still not resolved. Please do not expose this to the internet, ever."
According to a Shodan search, there are almost 1,000 Oracle Opera servers currently reachable via the internet.
CVE-2023-20869 (UHCI): Nguyễn Hoàng Thạch of STAR Labs has discovered a local privilege escalation (CVE-2023-20869) in VMware Workstation. The bug resides in the UHCI component and can allow attackers from inside a host to execute arbitrary code in the context of the hypervisor.
CVE-2023-28929 (Trend Micro OfficeScan): NTT has published details on CVE-2023-28929, a vulnerability they found in TrendMicro's OfficeScan antivirus engine, a product that was the subject of a few zero-days in the previous years.
CVE-2023-28231 (Windows DHCP): Trend Micro's ZDI has a write-up for CVE-2023-28231, an RCE in the Windows DHCP server that Microsoft patched earlier this month.
Databricks vulnerability: SEC Consult has published details about a Databricks privilege escalation issue that could allow an authenticated, low-privileged user of a cluster to elevate privileges and gain admin-level access to other clusters within the boundary of the same workspace and organization. The vulnerability can be exploited via legacy global init scripts. As a result of SEC Consult's findings, Databricks is notifying customers to "immediately" disable legacy global init scripts on their could infrastructure (AWS | Azure) if they are not being used, or migrate to its new global init scripts framework. The company also plans to remove support for global init scripts from its software later this year, on September 1.
FireOS vulnerabilities: Bitdefender researchers have identified vulnerabilities in streaming devices running Amazon's FireOS operating system. Affected devices include products from Fire TV and Insignia TV. The vulnerabilities include unauthorized authentication through local network PIN brute-forcing and arbitrary Javascript code execution.
FRRouting vulnerabilities: Forescout researchers have discovered three vulnerabilities in FRRouting, a routing protocol for the Linux and BSD operating systems. More specifically, the vulnerabilities reside in the protocol's BGP message parsing process. Forescout says it discovered the bugs while analyzing seven popular BGP protocol handling implementations (FRRouting, BIRD, OpenBGPd, Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS).
Infosec industry
Tool update—ClamAV: Cisco Talos has released v1.1 of the ClamAV open-source antivirus engine.
NIST CSF 2.0 draft: The US NIST has released a first draft for its upcoming 2.0 release of the agency's Cybersecurity Framework (CSF) [PDF]. [Additional coverage in Decipher]
Cybersecurity newswire: Cyberpress, a newswire service for the distribution of cybersecurity press releases, launched this week. The newswire service is here.
Industry movements: CyberCX has hired Ciaran Martin, the former head of the UK's GCHQ, as the chairman of its UK branch. Martin has served as an advisor for the company since 2021.
UniCon 2023 videos: Talks from the UniCon 2023 security conference, which took place last month, are now available on YouTube.
New book: Microsoft security researcher Thomas Roccia has announced plans for "Visual Threat Intelligence," a visual guidebook for new cyber threat intelligence analysts.