Risky Biz News: Authorities seize iSpoof in major blow to fraudsters and cybercrime groups
In other news: Guadeloupe government hit by ransomware; Android driver patch gap; Mars Stealer servers get hacked back.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Europol and law enforcement agencies from several countries have seized the servers and websites of iSpoof, a service that allowed users to make calls and send SMS messages using spoofed identities.
The service launched in December 2020 and advertised itself as a way for users to protect their phone numbers and identities online, but Europol said that iSpoof was widely abused for fraud as it allowed cybercrime gangs to pose as banks and other financial organizations.
An investigation into iSpoof began in 2021 after Dutch Police identified the service during one of its fraud investigations. Dutch Police said they linked the service to a web host in Almere, where they deployed a wiretap that allowed them to map the site's reach and learn the identities of its registered users and administrators.
Officials said iSpoof had more than 59,000 registered users before it was taken down this month.
One hundred forty-two suspects were detained throughout the month of November, with more than 100 individuals detained in the UK alone, including iSpoof's administrators, the UK Met Police said.
Europol said iSpoof was being used to place more than one million spoofed calls each month, that administrators made more than €3.7 million, and that the service has been linked to fraud and losses of over €115 million worldwide.
UK police said they plan to notify all UK users who received spoofed calls made through iSpoof.
Breaches and hacks
EU Parliament DDoS attack: The EU Parliament said its servers were subject to a DDoS attack hours after they proclaimed the Russian government as a sponsor of terrorism. A pro-Kremlin hacktivist group took credit for the attack, according to Roberta Metsola, President of the EU Parliament. The agency's website resumed operations after two hours.
Guadeloupe cyberattack: In a message posted on its official website, the government of the Caribbean island Guadeloupe, a French overseas region, said it was hit by "a large-scale computer attack." Officials said they shut down all affected systems to protect data and diagnose the problem. The incident took place on Monday, and systems have yet to be restored. Security experts believe this is a ransomware attack, although the perpetrators have not yet been identified.
Ransomware on Indian hospital: A suspected ransomware attack has disrupted the IT network of the All India Institute of Medical Sciences (AIIMS), one of India's largest medical schools and hospitals. The Hindustan Times said this would mark the first instance of a major Indian hospital being affected by ransomware. Healthcare organizations, and especially hospitals, have been constantly targeted by ransomware gangs all over the US and Europe for the past five years, but as these organizations are getting better at protecting their networks, ransomware attacks are now hitting other countries as well.
Westmount ransomware attack: The local government of Westmount, part of the Montreal urban area, said it's dealing with a ransomware attack that crippled its IT network. Local press said the attackers have already demanded a ransom payment, but officials do not intend to pay.
Continental ransomware attack: German authorities have called in the FBI to help with their investigation into the ransomware attack that hit Continental, a major supplier for the international automotive industry. According to a Handelsblatt report, the LockBit ransomware gang breached Continental in July and spent a month exfiltrating data from its network before attempting to extort the company for $50 million. In August, Continental gleefully said that it had averted a cyberattack before admitting that it got hacked earlier this month after the LockBit gang leaked some of its data.
Government, politics, and policy
Don't cyberattack here, plz: Retired US General Ben Hodges told Reuters that a cyber attack on the German ports of Bremerhaven or Hamburg would severely impede NATO efforts to send military reinforcements to its allies. That's one way to say, "don't cyberattack here." I wonder how many threat actors have had their interests piqued by this article.
Voting machine bug: Former Brazilian President Jair Bolsonaro filed a lawsuit claiming that more than 280,000 voting machines used in the recently-concluded presidential election contain a software bug. Bolsonaro's camp said that the voting machines, all dating before 2020, lacked individual identification numbers in internal logs and asked a judge that votes from these systems be ignored. According to Bolsonaro's lawyer, this would be enough to grant the former President the election victory.
DOD zero trust framework: The US Department of Defense has released a framework [PDF] to guide agencies into implementing zero trust architectures on their networks.
Cybersecurity Apprenticeship Sprint: The US government said that it hired 7,000 apprentices in official cybersecurity roles following an apprenticeship sprint held over the summer. Around 1,000 of the new hires came from the private sector. The sprint was launched in July by the White House and the Department of Labor as a way to boost the government's cybersecurity workforce.
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Operation HAECHI III: Interpol said it detained 975 suspects and seized nearly $130 million as part of a crackdown against cybercrime groups the agency calls Operation Haechi III. Officials said the suspects were involved in phishing, romance scams, sextortion, investment fraud, and money laundering criminal operations.
Hacking back: Security firm Buguard said it identified a vulnerability in the command and control (C&C) servers of the Mars Stealer malware. Buguard said the vulnerability can be used to tamper with Mars servers to delete data collected from infected users, terminate connections to infected systems, and even lock Mars operators out of their own servers by scrambling their admin passwords. The company told TechCrunch it neutralized five Mars Stealer servers so far and that the same vulnerability is also present in servers for the Erbium malware.
Bjorka profile: S2W Talon has looked at Bjorka, a threat actor who has been hacking and leaking documents from Indonesian government agencies and private companies for the past two years. Some of these leaks included details related to sensitive cases, like the murder of human rights activists by government officials. The threat actor was previously active on RaidForums, but also on its newer iteration on Breached. The threat actor claims on their Telegram channel to be a girl from Poland, but this has not yet been verified to be true. Past Bjorka profiles are also available from The Diplomat and DarkOwl.
PyPI malware: DataDog's security team has an analysis of fastapi-toolkit, a Python library created earlier this year in March and which, all of a sudden, shipped a malicious update earlier this week. The malicious update allowed a remote attacker to execute arbitrary python code and SQL queries in the context of the web application.
Malicious Chrome extensions: Google has removed two Roblox-themed Chrome extensions [1, 2] from the official Web Store after it discovered that recent updates deployed malicious code inside users' browsers that stole their Roblox account credentials. The incident appears to be linked to several reports from Roblox users who had some of their game inventory got stolen over the past few days. More than 200,000 users installed the extensions. [Read more in BleepingComputer]
Infostealer market: A comprehensive report of the infostealer market from security firm Group-IB has found that the RedLine Stealer is today's most popular infostealer, being used by 23 out of 34 gangs the company tracks. The company said that in the first seven months of 2022, these gangs collectively infected over 890,000 devices and stole more than 50 million passwords. Most of the infected devices were located in the US.
Birdsite security issues: Some threat intel companies are telling their customers that they can no longer guarantee takedowns of malicious or reputation-damaging content from Twitter as there is nobody in Twitter's abuse team to respond to requests anymore.
Hey, Google: Do your job!


Malware technical reports
Life ransomware: Trend Micro said that it detected a new version of the WannaRen ransomware in attacks that targeted Indian users over the month of October. The original WannaRen ransomware was active for only a few days in August 2020, when it infected thousands of Chinese internet users who downloaded copies of a malicious Notepad++ app hosted on local download sites. The ransomware went silent days after the attack, after several Chinese security firms released free decrypters to help users recover their encrypted data. Trend Micro named this new WannaRen variant as Life ransomware, but the company didn't say if it was still decryptable.
Cryptonite ransomware: Fortinet has taken a look at Cryptonite, an open-source ransomware building kit. Not to be confused with the Chaos ransomware variant, also named Cryptonite.
Black Basta + Qakbot: Cybereason researchers are reporting on malware infection killchains where victims were initially infected with the Qakbot trojan before they got ransomed by the Black Basta ransomware crew.
"To make the recovery more difficult, the threat actor also locked the victim out of the network by disabling DNS services. We observed this tactic used on more than one victim."
SocGolish waves: Sucuri has been keeping an eye on the tactics used by the SocGolish gang to deploy malicious code on hacked WordPress sites. The gang uses this malicious code to redirect users to other websites hosting apps laced with the SocGolish malware. They later use their malware to deploy malware for other gangs, such as infostealers, RATs, and even ransomware.
APTs and cyber-espionage
Bahamut APT: Cyber-mercenary group Bahamut has been spotted using boobytrapped Android VPN apps to infect users with spyware. Spotted by ESET, the company said this campaign has been taking place since January, and the group has used a website posing as the SecureVPN service to distribute their spyware—made to look like the SoftVPN or OpenVPN applications. ESET said the campaign is still ongoing.
ZINC/Lazarus: Avertium has a detailed rundown of all the TTPs employed by ZINC, a North Korean APT, also known as the Lazarus Group.
Vulnerabilities and bug bounty
Android patch gap: Google's Project Zero team warns that there is a patch gap in the Android ecosystem where patches for vulnerabilities in various drivers often linger for months before they are shipped to consumers. Google gives the example of several vulnerabilities in the Arm Mali GPU drivers for which fixes have yet to reach many end-user devices, despite receiving official patches from Arm this summer. Devices from Google, Samsung, Xiaomi, Oppo, and other phone makers are still vulnerable.
ConnectWise vulnerability: Guardio Labs researchers said they found a cross-site scripting (XSS) vulnerability in the ConnectWise remote access platform that the security firm said has "great potential" for misuse by scammers. Guardio said the vulnerability could be used to hijack accounts and their remote access capabilities and that ConnectWise quickly patched the issue after receiving its report.
CVE-2022-40300: ZDI has a report out on CVE-2022-40300, a Zoho ManageEngine SQLi vulnerability that could be used to hijack servers via its built-in password manager capability.
Argent vulnerability: Cryptocurrency platform Argent fixed a vulnerability last week that could have allowed a threat actor to empty customer wallets without any user interaction.
"The vulnerability is exploited by sending a transaction in a certain way that bypasses Argent Contract signature verification logic. This would allow an attacker to send any transaction with an empty or false signature that would get executed and accepted on-chain."
Infosec industry
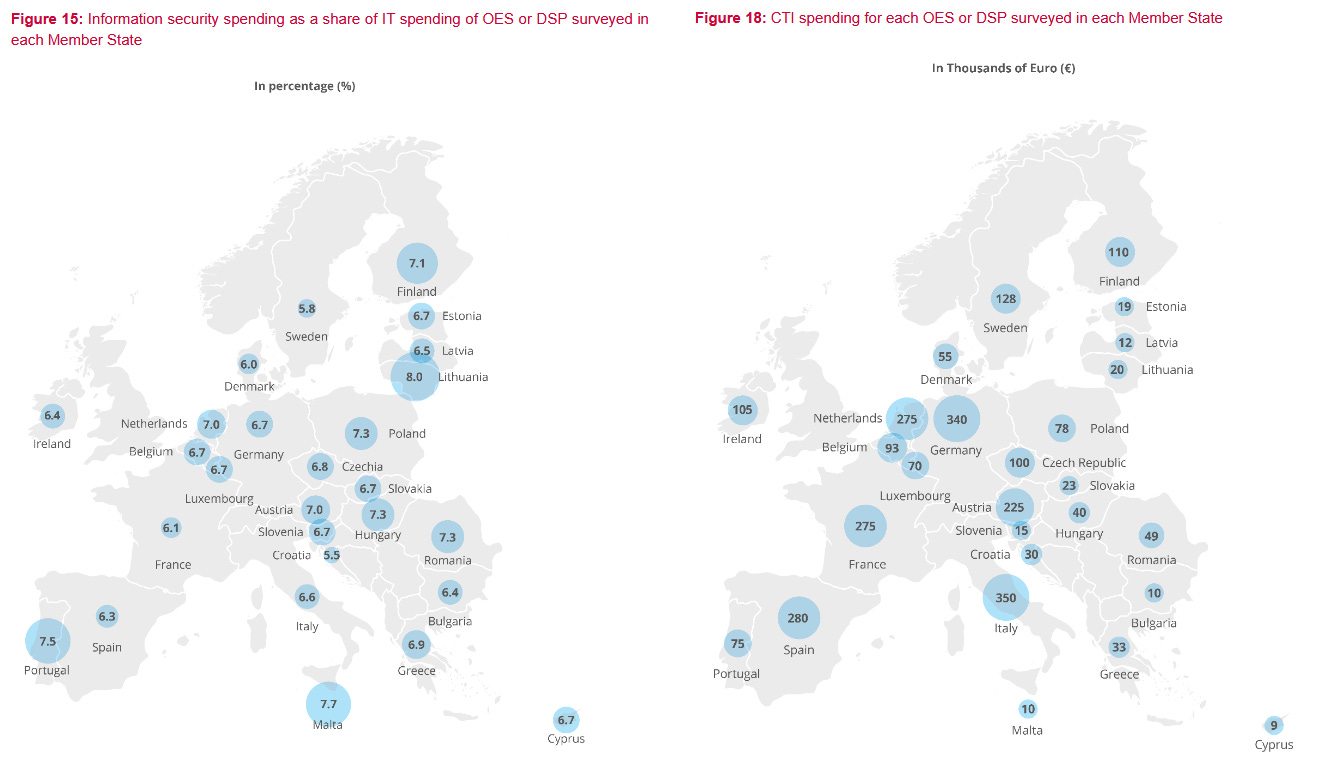
ENISA investments report: The EU's cybersecurity agency analyzed investments in the IT and cybersecurity field and found that information security budgets were "significantly lower compared to last year." In a report on Wednesday, ENISA said the median percentage of IT budgets spent on information security in 2022 was 6.7%, 1% point lower compared to last year's numbers. In addition, ENISA found that the estimated direct cost of a major security incident this year was around €200,000, twice as large as in 2021, indicating an increase in the cost of incidents.