Risky Biz News: Barracuda discloses ESG zero-day on Xmas Eve
In other news: Lapsus$ member sentenced to indefinite mental hospital stay; Russian Wikipedia shuts down; and more than 26k vulnerabilities were reported in 2023.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The RiskyBiz crew behind our newsletters and podcasts is on hiatus between December 8 and January 8 for the winter holidays, but we put out this weekly edition with some of the past week's biggest infosec stories.
Happy holidays!
Breaches, hacks, and security incidents
Rosvodokanal hack: A Ukrainian hacker group named BlackJack has breached and destroyed the IT infrastructure of Rosvodokanal, a major Russian water-supply company. The group says it carried out the attack in response to Russia's cyberattack on Ukraine's Kyivstar mobile telco. BlackJack told reporters they had assistance from Ukraine's SSU intelligence service. The agency didn't confirm. [Additional coverage in RBC-Ukraine]
Bitrix24 attack: Ukraine's IT Army took credit for DDoS attacks that took down Bitrix24, Russia's largest CRM provider. [Additional coverage in The Record]
VF Corp incident: VF Corp, the company behind retail brands such as Vans, Dickies, and Timberland, says it suffered a cybersecurity incident. VF Corp declined to comment on whether the incident was a ransomware attack. [Additional coverage in RetailDive]
National Amusements incident: National Amusements, the company behind CBS and Paramount, disclosed a cybersecurity incident. The breach took place in December 2022 but was only recently discovered. More than 82,000 people had their data stolen in the incident. [Additional coverage in TechCrunch]
First American incident: First American, the second largest title insurance company in the US, shut down its IT systems in the aftermath of a cyberattack. The incident took place after the AlphV gang hit Fidelity National, the largest title insurer in the US, at the end of November.
Mint Mobile breach: Mint Mobile has disclosed a new data breach.
Bedroom footage sold online: Private camera footage from bedrooms, changing rooms, toilets, and massage parlors in Vietnam has been hacked and put on sale online. [Additional coverage in VNExpress]
All the apes are safe: Yuga Labs co-founder Greg Solano has paid a hacker a bounty of 120 ETH ($275,000) to return 36 Bored Ape Yacht Club (BAYC) and 18 Mutant Ape Yacht Club (MAYC) NFTs that were stolen during a hack of the NFT Trader platform in early December. NFTs worth nearly $3 million were stolen in the hack, but the apes are now safe! [Additional coverage in Cointelegraph]
GTA V code leaks online: Hackers have leaked the source code of GTA V. The code was stolen in September 2022 by Arion Kurtaj, a member of the Lapsus$ hacking crew. The code was released following Kurtaj's sentencing. [Additional coverage in RockstarIntel]
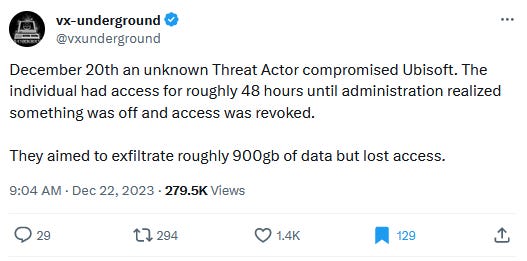
Ubisoft probes hack: A threat actor claims to have hacked and stolen more than 900GB of data from gaming studio Ubisoft. The company said it's investigating the claims and has not confirmed a breach. [Additional coverage in Xfire]
General tech and privacy
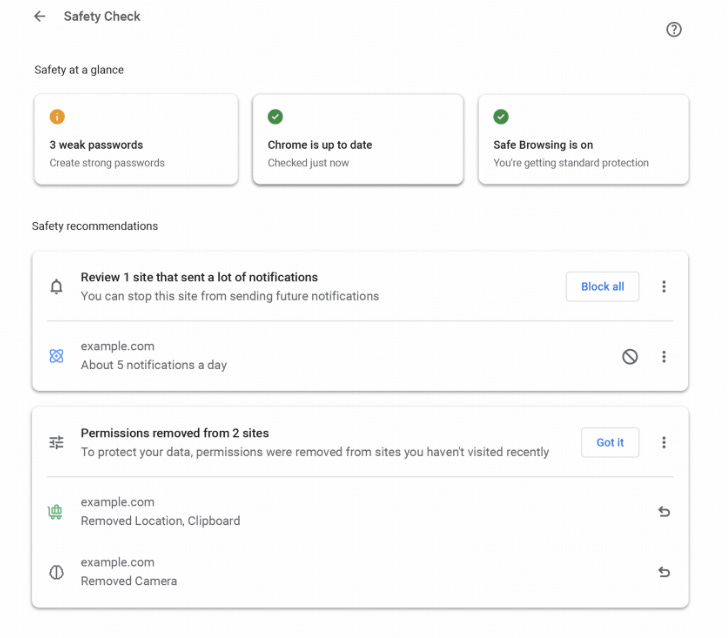
Chrome Safety Check: Google has announced that Safety Check, the feature that scans for compromised user passwords, will now continuously run in the background at all times.
"We're also extending Safety Check to revoke sites' permissions — like access to your location or microphone — if you haven't visited them in a long time. And Safety Check will now flag if you’re getting a lot of notifications from sites you don’t engage with that much, so you can easily disable them."
Wikipedia Russia shuts down: Wikipedia's Russian edition has shut down after authorities designated its lead editor as a "foreign agent."
Substack Against Nazis: More than 100 Substack editors named "Substack Against Nazis" have signed an open letter asking Substack to remove white supremacy and nazi newsletters hosted on the platform, threatening to leave if the company fails to act.
Government, politics, and policy
FTC COPPA update: The US FTC has put forward a series of updates meant to strengthen the Children's Online Privacy Protection Act (COPPA) and put new restrictions on the collection and use of children's data.
"The proposal aims to shift the burden from parents to providers to ensure that digital services are safe and secure for children. [...] The rule also limits the personal data that websites and other online services can collect from children, limits how long they can retain such data, and requires them to secure the data."
GAO report on medical device cybersecurity: The US Government Accountability Office has published a report on the cybersecurity of medical devices. The agency recommended that CISA and the FDA update their collaboration agreement, which is now five years old and outdated in the face of the current threat landscape.
EU CSA: EU officials have agreed on a form of the EU Cyber Solidarity Act, new regulation that will provide a quick way for EU member states to share information on large-scale cyberattacks.
Tallinn Mechanism: Ukraine's partners have activated the Tallinn Mechanism, a new system to provide cyber and military aid to the besieged country.
Israel-Hamas war: Israel's National Cyber Directorate says that 15 hacking groups associated with Iran, Hezbollah, or Hamas have launched attacks against Israel since the October 7 incident. [Additional coverage in Calcalist]
IDF censorship: The Israeli military has prohibited Israeli media from reporting on cyberattacks targeting the government and on cyber operations carried out by officials as part of its war on Hamas. [Additional coverage in The Intercept]
Risky Business Podcasts
In this podcast, Patrick Grey and Tom Uren talk about whether election interference will take place in the Taiwanese, US, and Russian elections that are all taking place in 2024. They also look at a ChatGPT-powered online harassment campaign.
Cybercrime and threat intel
Lapsus$ member handed indefinite hospital order: A UK judge has sentenced a member of the Lapsus$ hacking crew to an indefinite hospital order. Arion Kurtaj from Oxford, 18, was diagnosed with severe autism and was deemed unfit to stand trial. Kurtaj was directly involved in Lapsus$ breaches at Nvidia and BT/EE. He also hacked Rockstar Games and leaked images of the upcoming GTA6 game while on bail. [Additional coverage in the BBC]
FruitFly malware author case: On the same note, a US court found Phillip Durachinsky, the creator of the FruitFly macOS spyware, incompetent to stand trial because of his autism spectrum disorder. [Additional coverage in Cleveland.com]
FACCT exec to be extradited to Russia: Kazakh officials have agreed to extradite an exec of Russian cybersecurity firm FACCT—the former Russian branch of Group-IB—to Russia. Nikita Kislitsin was initially detained following an international arrest warrant issued in the US. Russia filed its own hoax indictment days later and requested his extradition as well. [Additional coverage in TASS/ English coverage in The Record]
Operation HAECHI IV: Interpol detained more than 3,500 suspects and seized nearly $300 million as part of a crackdown against cybercrime groups the agency calls Operation Haechi IV. Officials said the suspects were involved in cyber-enabled scams, such as voice phishing, romance scams, online sextortion, BEC, and investment fraud.
Digital skimming campaign disrupted: Europol and Group-IB have identified and notified the owners of 443 merchants that had digital skimmers installed on their online stores.
Kingdom Market takedown: German officials have seized Kingdom Market, a dark web marketplace selling drugs, hacking tools, and fake IDs. The portal launched in March 2021 and was accessible via both Tor and I2P. The site's admin, a Slovakian man, was also charged in the US.
Crypto-drainer attacks: A threat actor has used Google and Twitter ads to lure victims on specialized phishing sites (called crypto drainers) that collect crypto-wallet credentials and empty accounts. The group is believed to have stolen $58.98 million from over 63,210 victims over the past nine months.
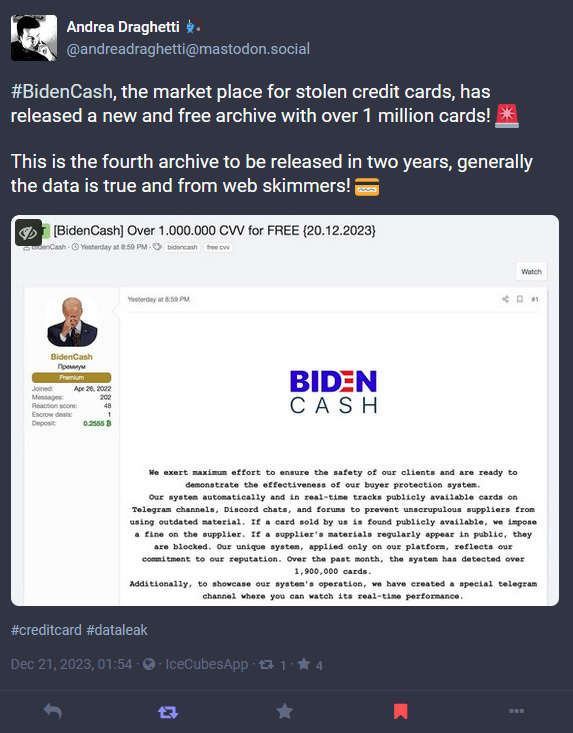
Carding scene stats: More than 71.4 million card details were posted for sale on underground carding shops, and more than 48 million card details were posted online for free throughout 2023, according to Recorded Future's Payment Fraud Year in Review report.
PyPI malware: ReversingLabs has identified five malicious Python libraries uploaded on the official PyPI portal. This batch abused GitHub Gists, issuing commands through Git commit messages.
Malicious Chrome and Edge extensions: ReasonLabs have found three Chrome and Edge browser extensions disguised as VPN tools that hijacked users' browsers to install other extensions, steal user data, and more.
Lumma usage explodes: ESET has published its threat report for H2 2023, and among the report's main findings is the sudden rise in Lumma Stealer detections.
Carbanak returns: Old malware from the Carbanak banking heists gang has been spotted in attacks throughout November 2023, used in intrusions that ended in ransomware attacks, according to the NCC Group.
Intellexa and Cytrox: Cisco Talos has published a history of Intellexa and Cytrox, two major spyware vendors.
Talos' analysis revealed that rebooting an iOS or Android device may not always remove the Predator spyware produced by Intellexa. Persistence is an add-on feature provided by Intellexa for their implants and primarily depends on the licensing options chosen by a customer.
Intellexa knows if their customers intend to perform surveillance operations on foreign soil.
Two years after its first public exposure, Intellexa’s Predator/Nova spyware solution continues to be undetected by anti-virus solutions.
KEV update: CISA has updated its KEV database with two vulnerabilities that are being exploited in the wild. The two are CVE-2023-49897 and CVE-2023-47565, two command injection flaws in FXC routers and QNAP VioStor NVRs, exploited by a Mirai botnet and the InfectedSlurs botnet, respectively.
Atlassian exploitation: Internet scanning service GreyNoise warns of a rise in attacks targeting Atlassian systems.
Old Excel bug campaign: A threat actor is leveraging a 2017 Excel RCE to infect users with the Agent Tesla infostealer. More from Zscaler.
Nim campaign: Netskope looks at a phishing campaign spreading a Nim-based backdoor using emails claiming to come from the Nepali government.
BattleRoyal: Proofpoint has published a report detailing BattleRoyal, a threat actor behind a wave of phishing campaigns that are redirecting users to websites hosting fake browser update schemes that infect victims with the DarkGate and NetSupport malware.
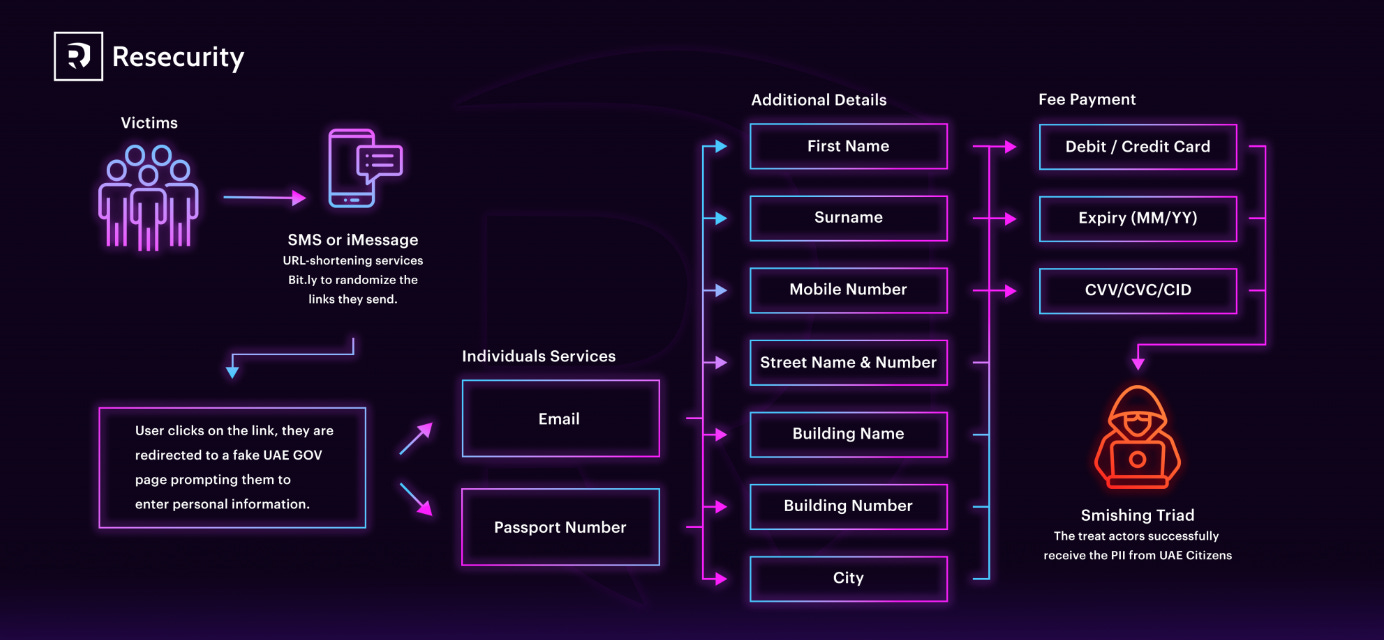
Smishing Triad: Resecurity reports on new smishing campaigns carried out by the Smishing Triad group. See previous reports from August and September.
Malware technical reports
JaskaGO: AT&T's Alien Labs security team looks at JaskaGO, a new malware strain targeting macOS and Windows systems. As the name alludes, the malware is written in Go.
Bandook: Fortinet has analyzed the C&C mechanism of Bandook, a remote access trojan that's been used in attacks since way back in 2007.
Akira: Sophos researchers have published a report on the recent tactics and IOCs employed by the Akira ransomware group.
Chameleon: A new version of the Chameleon Android banking trojan now disables fingerprint and facial scanning features as a way to bypass biometric authentication and take over devices.
Xamalicious: McAfee has published a report on Xamalicious, a new Android backdoor coded using Xamarin, an open-source framework that allows building Android and iOS apps with .NET and C#.
Operation HamsaUpdate: Intezer looks at a phishing campaign that targeted Israeli companies with emails claiming to be from networking equipment vendor F5.
"The campaign leverages a convincingly written email in Hebrew and utilizes sophisticated social engineering techniques, pressuring victims to execute the harmful code residing on their servers. The final attack delivers a complex, multi-stage loader or a destructive wiper, each variant customized for either Linux or Windows environments. [...] We’ve dubbed the Windows variant Hatef and the Linux variant Hamsa. During our analysis, we unearthed a second-stage loader coded in Delphi—which spearheads the execution of an AutoIt injector. This injector has been given the name Handala."
Sponsor Section
In this product demo, GreyNoise founder and CEO Andrew Norris demonstrates how people use the GreyNoise sensor network.
APTs, cyber-espionage, and info-ops
Peach Sandstorm: Iranian hacking group Peach Sandstorm (APT33, Holmium) is targeting defense companies across the world in attacks aiming to deploy a new backdoor named FalseFont. The backdoor was first spotted at the end of November, and the group is known for its broad use of password-spraying attacks.
OilRig's Menorah: SecurityScorecard's Vlad Pasca has a technical breakdown of Menorah, a backdoor used by the OilRig (APT34) Iranian espionage group.
Kimsuky's AppleSeed: AhnLab researchers have published an analysis of AppleSeed, a macOS malware strain used by North Korean hacking group Kimsuky.
UAC-0050: Ukraine's CERT team is seeing new UAC-0050 spear-phishing targeting Ukrainian organizations.
UAC-0099: DeepInstinct researchers look at a UAC-0099 spear-phishing campaign targeting Ukrainian officials with CVE-2023-38831, a former zero-day in the WinRAR app.
Cloud Atlas: Russian security firm FACCT has published a report on attacks against Russian companies by Cloud Atlas, an APT group that has been active since 2014.
Vulnerabilities, security research, and bug bounty
New Barracuda zero-day: On Christmas Eve, Barracuda disclosed the existence of a zero-day in its ESG appliance (CVE-2023-7102). Barracuda says it deployed a security update to all active ESG appliances on December 21 that was applied automatically and then deployed a second patch the following day to ESG appliances that exhibited indicators of compromise for new variants of the SEASPY and SALTWATER malware. The company attributed the attacks to UNC4841, the same Chinese group that exploited its appliances last year.
Chrome zero-day: Google has pushed a security update for Chrome browsers to fix an actively exploited zero-day (CVE-2023-7024).
CLFS exploits: Kaspersky shares a list of five exploits in the Windows Common Log File System (CLFS) driver that have been used over the past year by ransomware gangs as part of their intrusions.
Buffalo VPN router bugs: NSLabs researchers have found three vulnerabilities in Buffalo VR-S1000 VPN routers.
Ivanti Avalanche vulnerabilities: Ivanti has released patches for 20 vulnerabilities in its Avalanche MDM product.
Roundcube 2FA bypass: Security researcher Chand Singh has published details on CVE-2023–43837, a 2FA bypass in Roundcube's webmail plugin.
2023 vulnerability threat landscape: More than 26,000 vulnerabilities were reported this year, but only less than 1% were routinely exploited in the wild, according to the Qualys 2023 Threat Landscape report.
Infosec industry
New tool—Troll-A: Security firm Crissy Field has released Troll-A, a tool to extract passwords, API keys, and tokens from WARC (Web ARChive) files.
New tool—AuthLogParser: Eilay Yosfan from Security Joes has published AuthLogParser, a powerful DFIR tool designed specifically for analyzing Linux authentication logs, commonly known as auth.log.
New tool—SysReptor: Something we missed from May
New tool—Shadow-Pulse: Security researcher StrangerealIntel has published a spreadsheet with basic details on every major ransomware operation.
New tool—SigmaToARM: Redcentric's Ollie Legg has released SigmaToARM, a tool to convert Sigma rules to Azure ARM templates.
New tool—Ghidriff: A security researcher from ClearSecLabs has open-sourced a tool named Ghidriff, a binary-diffing engine for Ghidra.
Tool update—Ghidra: The NSA has released v11 of its Ghidra reverse engineering toolkit. The biggest update is initial support for Rust binaries.
Acquisition news: Cisco has acquired multi-cloud security startup Isovalent, known for its open-source products Tetragon, eBPF, and Cilium.
WaPo retires Cybersecurity 202: The Washington Post has retired its Cybersecurity 202 newsletter as part of recent layoffs.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about recent hints that the Ukrainian government has figured out how to make use of the IT Army.