Risky Biz News: BEC loses top spot in FBI Internet Crime report
In other news: NetWire RAT author arrested in Croatia; STALKER 2 game dev extorted by Russian "fan," DOD to embrace remote cyber workforce.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
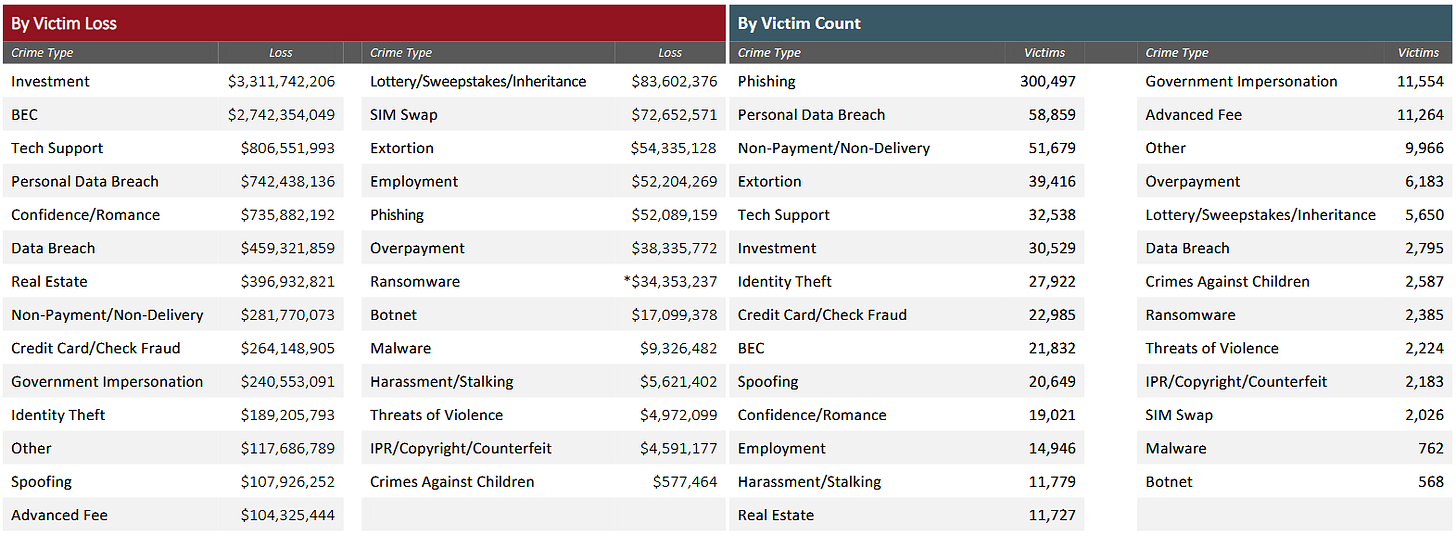
The Federal Bureau of Investigation has released its yearly internet crime report [PDF], and after seven years of dominance, business email compromise has lost the top spot to a "rising star"—namely, investment fraud.
Together with Verizon's Data Breach Investigations Report (DBIR), the FBI's Internet Crime Report is one of the most seminal reports in the cybersecurity community.
It is compiled by the FBI each year by aggregating complaints filed through the FBI's Internet Crime Complaint Center (IC3), a website where Americans can report an internet crime to the FBI.
Since its first edition, the IC3 report, as it's most commonly known, has been reporting losses at an increasing rate each year, and 2022 continued that trend. The FBI says that last year, users reported losing more than $10.3 billion to various forms of cybercrime, a 50% increase from 2021's $6.9 billion figure.
But things get interesting when we break down the numbers per category. While BEC ($2.7 billion) lost the top spot to investment fraud ($3.3 billion), both crime types combined accounted for more than half of the losses reported last year.
Furthermore, both BEC and investment fraud were also the only crime types that had losses in the realm of "billions," while everything else was in the millions mark.
For industry analysts, the shake-up at the top of the FBI IC3 report was surprising but not a total shock.
The signs were there for anyone paying attention. For example, in November of last year, Interpol detained nearly 1,000 suspects engaged in BEC and investment fraud and seized nearly $130 million as part of Operation HAECHI III. Europol also cracked down on call centers in Europe that used social media to lure users to scammy crypto-investment platforms. Spanish police, too, as part of an operation against a gang that stole nearly €12 million.
Security firm Group-IB and Resecurity published reports on two cybercrime groups known as CryptosLab and Digital Smoke that ran massive investment scam networks. These groups abused the brands and impersonated the investment portals of many high-profile brands, attracted investors with too-good-to-be-true opportunities, and then disappeared with the money.
In June of last year, the FBI put out a public statement warning that investment scams were rampant on LinkedIn.
It put out another alert in October of last year, warning about a tactic known as pig-butchering.
Here is also where the confusion about "investment fraud" lies. In pig-butchering, threat actors approach victims via dating sites, move conversations to other more private platforms, build a rapport, and once they have the victim's trust, they propose they go into a joint investment. In most cases, the investments are made in cryptocurrency, mainly because the scammer can hide their identity better and because there's no way to recover cryptocurrency once it's been transferred out.
But investment fraud takes place in many other ways. For example, WithSecure (formerly F-Secure) has a report here where scammers used Youtube videos advertising various cryptocurrency investment platforms to trick users into depositing funds at a platform they operated.
Scammers also use social media spam on sites like LinkedIn, Twitter, and Facebook to achieve the same results. Instant messengers are also abused, with known cases where threat actors have used Discord, WhatsApp, and Telegram to lure users onto their platforms.
Although the FBI says that crypto investments saw "unprecedented increases in the number of victims and the dollar losses," investment scams aren't always limited to cryptocurrency fans alone.
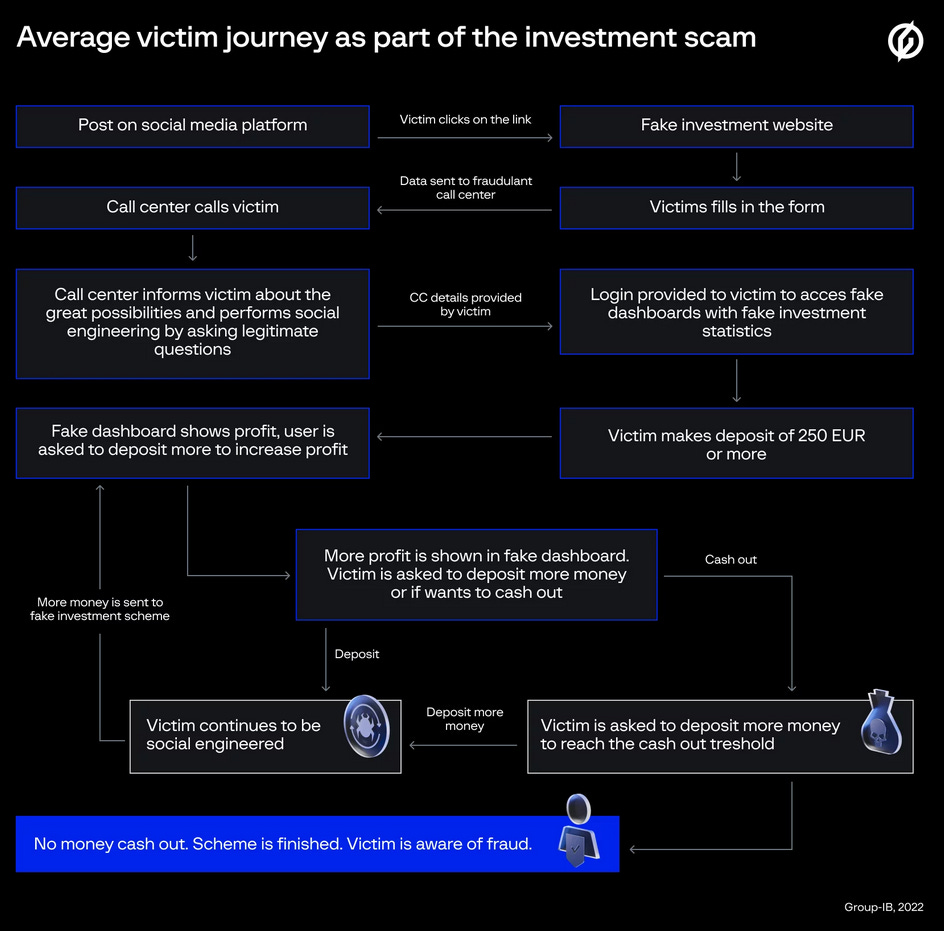
For example, Group-IB documented an operation that targeted stock market players as well. This group takes the cake for sophistication, with them building fake investment portals, complete with a dashboard that shows fake profits and urging users to deposit more via phone calls.
In addition, the FBI IC3 report also details other forms of investment scams that the FBI has received reports about and which they believe users should be aware of:
Liquidity Mining: victims are enticed to link their cryptocurrency wallet to a fraudulent liquidity mining application. Scammers then wipe out the victims' funds without notification or permission from the victim.
Hacked Social Media: scammers used hacked social media accounts to perpetrate a fraudulent investment opportunity using cryptocurrency, targeting existing friends of the hacked user.
Celebrity Impersonation: impersonating a well-known celebrity or social figure, the scammers feign a friendship with the targeted victim, who is eventually enticed to learn how to invest in cryptocurrency or is given the opportunity to invest by the scammer.
Real Estate Professionals: the scammer contacts a real estate agent, usually offering to buy a very expensive property for cash or cryptocurrency. Once engaged, the fraudster will expose their control of fictitious accounts with a purported value of millions of dollars to entice them to engage in their investment scheme.
Employment: victims apply for fake positions online at an investment firm or company supposedly affiliated with investing. Instead of a job, the victims are instead offered advice investment advice. The investment is fraudulent and designed to retrieve as much money from the target as possible.
The FBI also says the most targeted age group reporting investment fraud scams are ages 30-to-49—which is incredibly ironic for this newsletter's author. This is the age group that went through the early phases of the internet and most likely saw many similar investment scams before. The "Hello, I'm a Nigerian Prince and I need help returning from orbit" generation appears to have collective amnesia when it comes to crypto investments and social media replies—apparently!
But the tragedy of it all is that because many of these schemes are carried out using cryptocurrencies, there is little law enforcement can do, at least in the immediate future. As a result, many victims will most likely never see their funds again, and why the FBI reports that "many victims have assumed massive debt to cover losses."
Breaches and hacks
STALKER 2 extortion: A Russian individual going by the name of Nick Frost is extorting Ukrainian gaming company GSC Game World, threatening to release content from the studio's upcoming STALKER 2 game. The suspect wants the company to re-add its Russian language localization to the game, which GSC removed after Russia's invasion of Ukraine. In addition, Frost, who describes themselves as a "fan," also wants the company to unban their account from their official Discord. The individual has given GSC until March 15 to respond; otherwise, they plan to leak the game's story, cut scenes, concept art, maps, and more. Frost shared some images of the content they have in a VK post.
Blackbaud pays to settle SEC ransomware lawsuit: Blackbaud, a company that provides software and cloud hosting solutions for K12 schools, has agreed to pay $3 million to settle charges in relation to a 2020 ransomware attack. The SEC sued Blackbaud after the company filed documents with the agency and put out public statements for its customers stating that attackers did not gain access to bank account information or social security numbers. In its lawsuit, the SEC says the company's employees discovered that such data was stolen, but due to a lack of internal procedures, the information never made it to its senior management.
FONASA attack: The BlackCat ransomware gang has formally taken credit for the attack on FONASA, Chile's National Health Fund, in mid-February.
General tech and privacy
Brazil seizes Flipper Zero devices: Anantel, the Brazilian National Telecommunications Agency, is seizing and stopping shipments of Flipper Zero devices coming into the country. The device, released at the end of last year, is typically used in wireless penetration tests to hack various types of electronic devices. Despite being released for months, Flipper Zero devices have not been certified for use inside Brazil. Brazilians who tried to buy the product overseas have reported that their shipments have been redirected to Anantel, which has returned them to their senders. In the rare statements it provided on the topic, Anatel says it received reports that Flipper Zero devices have been used to commit crimes in Brazil, and it's why it cannot approve their import. In a recent blog post, the EFF pointed out Anantel's hypocrisy as the agency has homologated similar devices from other vendors.
OneNote security updates: Microsoft plans to improve the security of its OneNote application after several threat actors have started abusing OneNote documents in malware campaigns. In most cases, threat actors distribute OneNote files that contain additional embedded files. When users open the OneNote document and allow that file to download and execute, the attacker will run malicious code on their system. Going forward, Microsoft says it intends to show a notification before the embedded file runs as a way to warn users and give them the possibility to block the malicious file or allow it to execute if they trust the document.
IBM donates to CycloneDX: IBM has donated two open-source projects—SBOM Utility and License Scanner—to CycloneDX, an SBOM standard developed under the guidance of the OWASP Project. The two projects offer validation, content analysis, and accuracy of software license information included within BOMs.
Government, politics, and policy
Belgium bans TikTok on govt devices: The Belgian and Flemish governments have formally banned the use of the TikTok app on government devices, citing "security risks posed by the use of the app."
ECB to test European banks: The European Central Bank plans to run what it describes as a "thematic stress test on cyber resilience" of the EU's largest banks. Officials say they need to understand how banks react to major cyberattacks and scenarios like banks losing access to IT services due to things like sanctions.
"It's a new exercise, and we will devote quite a significant amount of time and resources to it, to have a better understanding of where the banks' strengths and weaknesses are. We plan to have the results by around the middle of next year."
Joint US-ROK working group on DPRK cyber threats: In a meeting of their joint working group, the governments of the United States and the Republic of Korea have announced plans to increase their efforts in tackling North Korea's malicious cyber activities.
Cloud security regulations: Politico reports that the Biden administration is exploring a plan to regulate the security practices at US cloud providers. US officials believe cloud providers aren't providing the level of security they should and that a successful cyberattack could lead to widespread outages at private businesses and government agencies that rely on their services. Politico also reports that some US officials appear to be frustrated by the fact that some cloud providers charge customers to add security protections, something they feel should be available by default.
AI regulation: The US Chamber of Commerce has called on lawmakers to regulate AI technologies in a report published last week. Officials call it a disruptive technology that could displace jobs, promote bias, and adversely affect privacy and personal liberties.
DOD embraces remote work: The US Department of Defense has released its Cyber Workforce Strategy for the next five years as part of the department's attempt to address its cybersecurity workforce shortage. The strategy, here in full [PDF], sets out four main goals (see image below), with the highlights being on allowing for remote work, improving the incentives program to compete with the private sector, and tapping into "under-represented sources of talent" such as minorities, people of color, and women, all of which are not well represented in the private sector. [Press coverage in the Federal News Network]
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy demonstrates the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
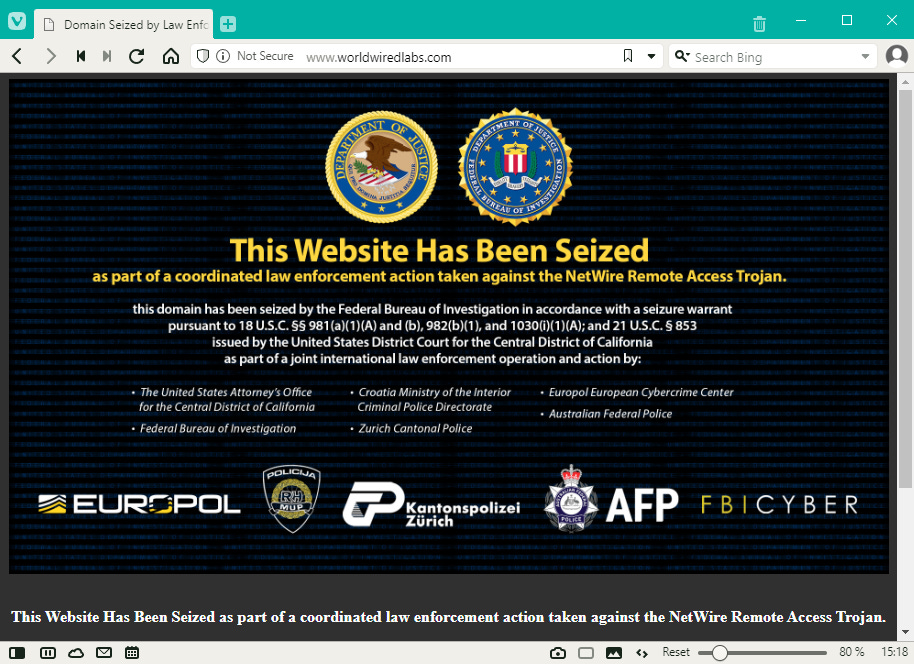
NetWire author detained: US and Croatian authorities announced they arrested a Croatian national who operated a website that sold access to the NetWire remote access trojan. The NetWire RAT has been available for sale on underground forums and through its official website since 2012. Today, it is both one of the cheapest and one of the most widely used remote access trojans, marketed for as low as $80. While officials have not disclosed the suspect's name, infosec reporter Brian Krebs says the suspect took few steps to hide their real identity, which Krebs identified as a man named Mario Zanko. Beside's the suspect's arrest, US authorities have also seized the RAT's official website, located at worldwiredlabs[.]com.
Santos linked to credit card skimming op: US Rep. George Santos (R-NY) has been accused of orchestrating a credit card skimming operation by one of his former roommates. [More on this saga in The Hill]
Interesting overlaps: Starting from a recent CISA alert on the Royal ransomware gang, Walmart's security team has found some interesting infrastructure overlaps between the Royal ransomware gang, Conti, and the FRwL (Z-Team, UAC-0118) group that has targeted Ukrainian organizations with the Somnia ransomware.
KEV update: CISA has updated its KEV database with four new vulnerabilities that are currently being actively exploited. The first is CVE-2020-5741, the Plex media server RCE used to hack LastPass last year. The second is CVE-2021-39144, a vulnerability in the XStream Java library, which is used all over the place.
MSSQL attacks: AhnLab published a report on the various LOLbins used in attacks against MSSQL servers.
Emotet's return: DeepInstinct has its own take on Emotet's recent return.
Ducktail returns: The same DeepInstinct crew also has a report on the recent malware deployed in attacks by Ducktail. This is a threat actor first spotted last year by WithSecure that focuses on compromising Facebook accounts with access to ads and business-related features.
Trend Micro yearly report: Security firm Trend Micro has published its yearly threat report. Some of the more interesting findings are below.
Ransomware attacks targeting macOS went down in 2022, while attacks against Linux systems grew more than eight times.
While three Exchange bugs were the most targeted vulnerabilities in 2021, 2022 saw a shift towards non-Microsoft-related bugs, with a focus on Log4j-related exploitation.
Malware technical reports
BlackMamba: Cybersecurity firm HYAS has used AI tools to create BlackMamba, a proof-of-concept polymorphic keylogger.
Xenomorph v3: ThreatFabric researchers have put out a report on Xenomorph v3, the third major version of Xenomorph, an Android banking trojan developed by a threat actor known as the Hadoken Security Group. Hadoken is the largest player in the mobile malware underground community, where they also manage the GymDrop and BugDrop droppers and the MaqSpy RAT.
GoBruteforcer: Researchers with Palo Alto Networks have discovered a new Go-based malware strain. Named GoBruteforcer, the malware has been used to launch brute-force attacks against web servers running phpMyAdmin, MySQL, FTP, and Postgres services. Infected systems are added to the GoBruteforcer botnet and used to compromise new hosts and help the botnet grow in size.
Sponsor Section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
UNC2970: Mandiant has a two-part report on UNC2970, a North Korean cyber-espionage group that uses job recruitment emails and LinkedIn messages to lure users on phishing sites or to infect them with malware. Mandiant says they linked UNC2970 activity to what is also known as UNC577, or Temp.Hermit, or the group behind Operation Dream Job [see reports from Google TAG, Proofpoint, and ClearSky]. Mandiant's latest reports cover the APT's latest attacks, which also targeted security researchers, but also two new malware strains tracked as LIGHTSHIFT (in-memory only dropper) and LIGHTSHOW (fileless backdoor).
SSSCIP report: The State Service of Special Communications and Information Protection of Ukraine, or SSSCIP, has published a report summarizing Russia's cyber efforts in Ukraine. The report is interesting because we finally have a map for Ukraine's UAC-xxxx threat actor naming scheme. For example, UAC-0107 is the CyberArmyofRussia hacktivist group, and so on.
KamiKakaBot: EclecticIQ researchers have put out a report on KamiKakaBot, a malware loader used in operations by Dark Pink, a suspected Chinese APT they say is targeting ASEAN countries. KamiKakaBot is one of the four main/custom tools used by this group, as detailed in Group-IB's initial report. The others are TelePowerBot, and the Cucky and Ctealer information stealers.
Vulnerabilities and bug bounty
OpenSea XSS: Imperva researchers have found a cross-site search vulnerability in the OpenSea NFT marketplace that can be used to deanonymize a user's account.
Veeam security updates: Backup service Veeam released security updates for its products last week.
ClipChamp vulnerability: AgileHunt researchers have found a misconfiguration in the cloud infrastructure of the ClipChamp video editor.
New IRIS technique: Security expert Andrew "bunnie" Huang has developed a new technique called IRIS (infrared in-situ) that allows researchers and companies to check the insides of microchips without destroying the chip with acid, lasers, or other methods. The technique works by "shining infrared light through the back side of the package and detecting reflections from the lowest layers of metal using a digital camera." Pretty interesting work if you have to vet hardware before deploying it in highly-secure environments.
CASPER attack: Academics from the School of Cyber Security at the Korea University in Seoul have published details on CASPER, a new covert data exfiltration channel. The technique uses malicious code planted on the air-gapped system to instruct its built-in speakers to send out inaudible high-frequency audio that contains encoded stolen data.
Infosec industry
USENIX Enigma suspended: USENIX has suspended its Enigma privacy and security conference. USENIX says it has "no immediate plans for its return" but hopes Enigma will eventually come back. The organization blamed the combination of the recent pandemic and spending reductions in the technology sector.
New framework: The Cyber Threat Alliance has published a global edition of its Cyber Incident Reporting Framework, initially released last year for US companies.
New tool—RansomLock: A new website launched last week named RansomLock. The website lists victims that ransomware groups are "claiming" to have compromised. The data is aggregated from ransomware leak sites.
Tool update—Donut: Donut, a shellcode payload generation tool, has reached v1.0.