Risky Biz News: China does a funny and tries to pose as IntrusionTruth
In other news: Guacamaya leak exposes police operations; new ATM MitM/relay attack spotted in the wild; ProtonMail finally adds support for security keys.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Something weird and very cringe-worthy happened at the start of the week when over the course of two days, on Monday and Tuesday, a few hundred (obviously very botty-bot) Twitter accounts started pushing a dumb rumor that the APT41 cyber-espionage group was actually the US National Security Agency.
In addition, some accounts tried to reinforce this ridiculously braindead disinformation attempt by floating a rumor that US cybersecurity firm Mandiant also linked APT41 to the NSA, which is obviously not true.
Some accounts posted in Chinese, others posted in English, while others even went as far as to try and pose as IntrusionTruth—a mysterious entity that has been doxing Chinese APTs for half a decade now—in an attempt to give legitimacy to their wacky theory.
In fact, after exposing some of their internal structure in a blog post back in July, IntrusionTruth seems to believe that it was APT41 itself who orchestrated this entire Twitter lameness.




We call it lameness because anyone with a basic understanding and foothold in the cybersecurity industry saw through this in the first five seconds.
Obviously, this disinformation campaign wasn't meant for the big-brains in the infosec industry, but because it was caught on early on and ridiculed into the ground, it was also almost immediately yeeted into the sun by the time of this newsletter, with the vast majority of the participating accounts being wiped clean (see list of accounts here, compiled by Stairwell security researcher Silas Cutler).
All of this fits in some bizarre trend that we've observed this year from the Chinese government, which has been obsessed with painting the US government, and the NSA in particular, as some sort of Dick Dastardly of the cyber-espionage world, responsible for all sorts of bad things, like... spying. Because that's obviously not what an intelligence agency does.
But trying to attribute your own operations to your adversary, despite quite obvious targeting and tooling differences, is some sort of brazen GigaChad move... that's just on another level of stupid and incompetence.
For disinformation like this to work, there needs to be at least some sort of doubt about the information you're trying to counter, and nobody believes that the NSA spent years spying on US government agencies and running a ransomware op as a side hustle.
Anyway, to whoever had this idea, thanks for the chuckles! T'was a boring week in infosec.
Breaches and hacks
Guacamaya leak exposes Australian police ops: A large collection of classified documents taken from the Colombian government and leaked online by the Guacamaya hacktivist group has inadvertently exposed details about criminal investigations into Colombian drug cartels and the personal details of police agents from several countries, the Sydney Morning Herald reported.
"The leak contains details of 35 Australian Federal Police operations, some ongoing, as well as surveillance reports from undercover agents, phone taps and payroll records for Colombian law enforcement officers. Many overseas police agencies are also affected."
SHEIN fined for 2018 breach: The New York Attorney General's Office has fined retailer SHINE $1.9 million for its 2018 data breach, during which hackers stole details on 6.42 million customers.
QANplatform hack: The QANplatform cryptocurrency bridge said it lost an estimated $2 million worth of cryptocurrency after an attacker manipulated one of its smart contracts.

General tech and privacy
New W3C security standard: The W3C has published the first draft of a new specification that will standardize password reset URLs to a default format:
https://example.com/.well-known/change-password
The standard was proposed by two Apple engineers, Ricky Mondello and Theresa O'Connor, and the idea behind it is to make password reset URLs across all modern websites discoverable for automated tools, which could then help users change passwords across multiple services at once.
Passkey support: Google has added support for passkeys in Chrome Desktop and Chrome Android, along with the Google Password Manager.
ProtonMail adds support for security keys: Proton, the company behind ProtonMail, one of the largest secure email service providers outside the Gmail-Outlook-Yahoo trifecta, added support this week for securing accounts with a hardware-based security key.
Signal removes SMS/MMS support: Signal said it plans to stop supporting the ability to send and receive SMS and MMS messages via its Android app as a way to improve user privacy and security. The feature was only supported in its Android app and was a leftover from the Signal service's early days when it was known under the name of TextSecure.
Firefox Relay can now protect phone numbers: Mozilla has added a phone number masking feature to Firefox Relay, an anonymization service it launched in 2020 to help users hide their real email addresses from snoopy online services. Phone number masking will be a paid feature.
OpenSSL withdraws faulty versions: The OpenSSL project has withdrawn v3.0.6 and v1.1.1r, two versions of the OpenSSL library it released a day earlier, after it received reports of serious performance regressions.
RSS feed for MSFT security updates: After years of pleadings from its customers, Microsoft has finally made available an RSS feed for its security updates portal. Pop the champagne bottles!
Domain join hardening: Also, as a result of its recent Patch Tuesday security updates, Microsoft said it hardened the domain join process as a result of a patch for CVE-2022-38042.
Government, politics, and policy
Greek spyware inquiry: The Greek national parliament has finished its investigation into the use of spyware by security services against the country's opposition parties, and snoopy journalists and officials unsurprisingly found that they did nothing wrong. [eyeroll]
Midterm election InfoOps: Recorded Future has a report on the possible sources of malign influence operations that are likely to take place during the upcoming US Midterm Elections. The usual suspects include Russia, China, Iran, and even from within, from the many right-wing extremist groups that have recently popped up inside the US in recent years.
The real reason to ban TikTok: In an op-ed for Cyberscoop, Dakota Cary of the Krebs Stamos Group argues that the real reason for the US to ban TikTok is because of the risk of manipulation of public sentiment in favor of the Chinese government and not because of its data security practices.
Russia looks to create its own GitHub: The Russian Ministry of Digital Development is looking to create a "national open source repository" to host public open source projects that could be safely used inside the country. Work will begin on this new project on November 1, 2022, and the ministry hopes to have the service running by April 30, 2024. Russia will become the second country after China (Gitee) to create its own GitHub-like clone.
Sponsor section
Thinkst is one of this newsletter's four main supporters and this week's featured sponsor. Last week, the company launched a new product called Sensitive Command Canarytoken, a simple canary token that sends an alert every time any command you choose as "sensitive" or "malicious" is executed on your host.
Cybercrime and threat intel
Large DDoS attack: In its quarterly threat report for Q3 2022, Cloudflare said it mitigated a large-scale DDoS attack that reached a massive 2.5 Tbps, launched by a Mirai botnet variant and aimed at the Wynncraft Minecraft service.
Web attacks in Q3 2022: Similarly to Cloudflare, GoDaddy's Sucuri team has also published its quarterly web malware threat report for Q3 2022. The report includes data from 260,101 website infections and is summarized in the video below:
Project DDOSIA: A pro-Russian hacktivist group named NoName057(16) launched a program this month called DDOSIA, through which the group claims to pay contributors who download their tool and launch DDoS attacks against western targets. [Additional coverage in BleepingComputer]
New type of ATM MitM/relay attack detected: The European Association of Secure Transactions (EAST), an industry group of banks and ATM vendors, said it's aware of at least 501 cases of ATM thefts where attackers used a new type of ATM MitM/relay attack to intercept and steal customer funds. "Our Expert Group on All Terminal Fraud (EGAF) is monitoring and analysing these attacks, with close cooperation between industry partners and law enforcement in the affected countries," EAST Executive Director Lachlan Gunn said in the organization's half-year H1 2022 report [PDF].
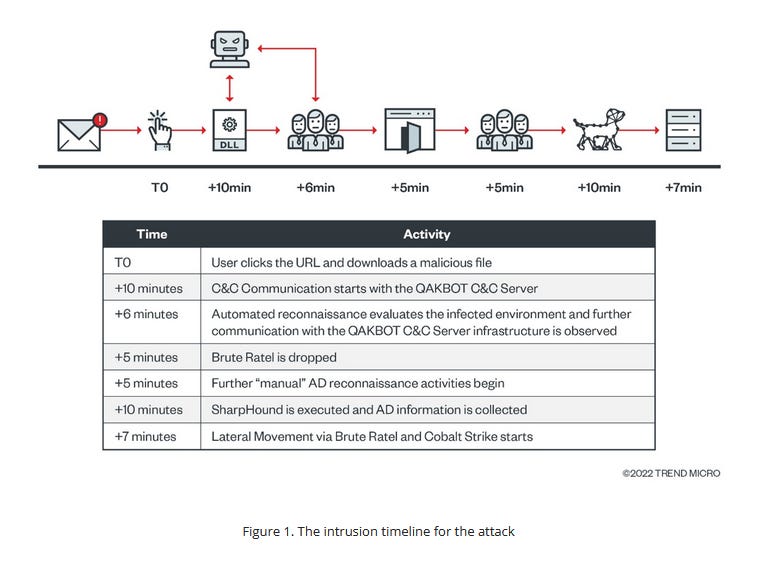
BlackBasta via QAKBOT: A Trend Micro report describes how recent infections with the QAKBOT malware deploy Brute Ratel or Cobalt Strike payloads within minutes of entering a system. Trend Micro linked these attacks to the threat actor behind the Black Basta ransomware.
Agent Tesla via WSHRAT: Similarly, Uptycs also published a report on a email malspam campaign where a threat actor deployed the Agent Tesla infostealer via the WSHRAT remote access trojan
UA military-themed phishing: Fortinet researchers published a report on a recent spear-phishing campaign using Ukrainian military-themed Excel documents to infect targets with Cobalt Strike backdoors.
Phishing targets election workers: US cybersecurity firm Trellix said it detected a malicious email campaign that has targeted county workers managing US local election infrastructure. Election workers in Arizona and Pennsylvania were targeted months before their states' primary elections cycles. The malicious emails tried to lure workers on phishing sites and steal their credentials.
TOAD attacks: Researchers from mobile security company ThreatFabric said they've seen telephone-oriented attack delivery (TOAD) tactics, where cybercriminals call and coach victims into installing Android banking malware on their devices. ThreatFabric said this particular campaign targeted users of Italian banks, and the final payload was the Copybara Android banking trojan.
Malware technical reports
Alchimist & Insekt: Cisco Talos researchers published a report this week on Alchimist and Insekt, a new C&C framework and RAT, respectively, both of which have been spotted being deployed in attacks in the wild. Talos researchers said both tools are written in the Go programming language, Alchimist has a Chinese web interface, and Insekt has cross-platform capabilities, being able to infect Windows, Linux, and Mac machines alike.
Ducktail: Zscaler said it detected a campaign using cracked versions of popular games and software applications to distribute the Ducktail infostealer.
"Ducktail has been around since 2021, and is attributed to a Vietnamese threat group. Campaigns to-date have focused on taking over Facebook Business accounts, both to manipulate pages and to access financial information."
Icarus Stealer: OALabs published an analysis of the Icarus infostealer.
LockBit 3.0 builder: On the same note, NTT Security has a report on the leaked LockBit 3.0 builder.
Magniber: HP security researchers have a breakdown of Magniber, a ransomware strain that has been active for more than half a decade and has exclusively targeted South Korean users.
IcedID's BackConnect protocol: Security firm Netresec has published a report on BackConnect, a proprietary command-and-control (C2) protocol used by the IcedID botnet.
APTs and cyber-espionage
Budworm: Broadcom's Symantec Threat Hunter Team said it spotted new attacks from the Budworm APT (also known as APT27 and Lucky Mouse), including attacks on US entities, which Symantec said the group hasn't targeted in years.
"The Budworm espionage group has mounted attacks over the past six months against a number of strategically significant targets, including the government of a Middle Eastern country, a multinational electronics manufacturer, and a US state legislature. The latter attack is the first time in a number of years Symantec has seen Budworm targeting a U.S-based entity. Along with the above high-value targets, the group also conducted an attack against a hospital in South East Asia."
WIP19: SentinelOne said it's been tracking a new Chinese-speaking threat group (WIP19) that has been targeting telecommunications and IT service providers in the Middle East and Asia. SentinelOne says WIP19 uses legitimate, stolen certificates to sign novel malware, including a new credentials dumper, ScreenCap, and new SQLMaggie malware.
Review of Chinese APTs: BoozAllenHamiltorn has published a report reviewing recent Chinese offensive cyber-espionage operations, a report that also includes a comprehensive catalog of threat actors and their tactics.
Vulnerabilities and bug bounty
Timing attack on npm API: AquaSec researchers discovered a security flaw in the npm API that can be used to expose if an organization has private packages and then run a timing attack and go through a list of names to verify which ones are assigned to the organization. GitHub refused to fix the issue.
Public PoC for Fortinet zero-day: There is now a publicly-accessible proof-of-concept exploit for the recently disclosed Fortinet zero-day tracked as CVE-2022-40684. Shortly after…

Infosec industry
Hulio founds new infosec firm: Former NSO Group CEO Shalev Hulio and former Austrian chancellor Sebastian Kurz have founded a new company called Dream Security. According to Israeli news outlet Globes, the new company will focus on providing defensive security services to the EU industrial sector and has already raised more than $20 million in funding.
Unofficial extended security updates: Acros Security said it plans to continue to offer security updates for Windows 7 and Windows Server 2008 R2 systems through its 0patch micro-patching service. Microsoft officially ended support for both operating systems in 2021 and has continued to offer paid security updates to enterprise customers through its Extended Security Updates (ESU) program. Support for both OSes in ESU will end in January 2023, but Acros said it plans to support both for two extra years, until 2025, through its 0patch service.