Risky Biz News: EU cybersecurity agencies warn of Chinese APT spying
In other news: Israeli company behind global election meddling campaigns; Atlassian confirms data leak; Belgium launches national vulnerability disclosure framework.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
ENISA, the EU's Cybersecurity Agency, and CERT-EU, the CERT team for EU official bodies and institutions, have published a joint advisory warning EU countries of the increasing threat of Chinese cyber-espionage operations.
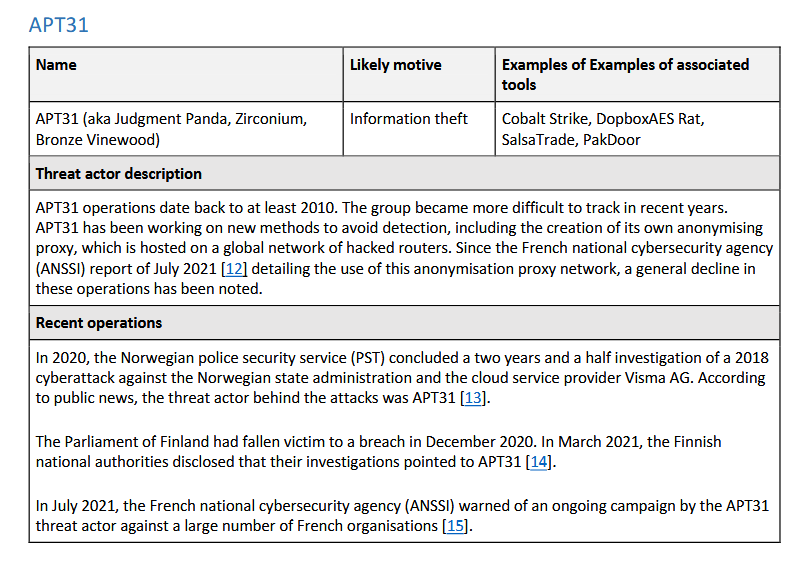
The alert particularly warns about the activities of six Chinese groups (or APTs, advanced persistent threats)—namely APT27, APT30, APT31, Ke3chang, GALLIUM, and Mustang Panda.
ENISA and CERT-EU say operations conducted by these groups "pose a significant and ongoing threat to the European Union."
Officials say these groups breach their targets by establishing persistent footholds within the network infrastructure of targeted organizations.
Both public and private sector organizations are targeted, and attacks are primarily focused on information theft.
The joint advisory is the first major document published by the EU in relation to Chinese APT activity since July 2021, when the EU Council asked the Chinese government to "take action against malicious cyber activities undertaken from its territory."
The ENISA and CERT-EU joint advisory is accompanied by a PDF with details about each APT and various defensive recommendations.
"It is kind of a weird joint publication given that it talks about 'recently conducted malicious cyber activities' but then goes on to mention examples as far back as July 2021," Stefan Soesanto, a Senior Cyber Defence Researcher at the Center for Security Studies at the Swiss Federal Institute of Technology (ETH) in Zurich, tells RiskyBizNews.
"On the one hand, this read to me as a stern reminder but also fairly desperate attempt by CERT-EU and ENISA to appeal to European public and private sector organizations.
"On the other hand, it was great to see all these past incidents being re-highlighted and Chinese threat actors being mentioned in the context of 'sustained activity'," Soesanto adds.
"I also think it's fantastic that the Belgian attribution was mentioned on the first page. In my opinion, the EU Council and the individual member states had forgotten that they left Belgium standing in the rain in mid-2022 when the Belgian MFA called out APT 27, 31, and Gallium—and almost none of the member states supported them publicly," Soesanto says.
"Overall, I think this joint publication shows that the EU and member states still have a very fragmented common threat perception. It's a Belgian problem, a French problem, a German problem, and only when enough member states come together then it becomes a European problem.
"That's just not good enough in this day and age."
Breaches and hacks
Tonga ransomware attack: TCC, Tonga's state-owned telecommunications company, was hit by ransomware. The company disclosed the incident in a Facebook post. While TCC says the attack did not impact its voice and internet services, the company says the incident will slow down the delivery of bills, customer support, and connecting new customers. The Medusa ransomware gang took credit for the attack.
SAS cyberattack: Scandinavian Airlines says it suffered a mysterious cyberattack during which its app and website went down and customer data leaked online. The airline says it's still investigating the incident, but it already confirmed that passengers who were using the app and website at the time of the attack had contact details, flight history, and the last four digits of their payment card number exposed.
Atlassian hack: Australian software company Atlassian has confirmed that hackers gained access to a contractor's systems and stole data on some of its employees. The stolen data contained the personal details of more than 13,000 employees, along with floor plans for two of Atlassian's offices. A hacking group named SiegedSec published the data online earlier this week, prompting an investigation. Atlassian told CyberScoop the data was stolen from Envoy, a third-party app that Atlassian uses to coordinate in-office resources.
Government, politics, and policy
Team Jorge: An undercover joint investigation by the OCCRP, Forbidden Stories, Le Monde, Der Spiegel, Der Standard, Haaretz, The Guardian, and 25 other news outlets have shed light on a shadowy Israeli company that provides disinformation services. During undercover interviews with reporters, the company claimed to have influenced 33 election campaigns across Africa, Europe, the US, and South and Central America. The company, referred to as Team Jorge, operates by hacking political rivals and their campaigns, planting forged information, leaking both forged and authentic files, and social media bot farms to sway public opinion in the direction of its paying customers. Most of this is done through a system called Advanced Impact Media Solutions, or Aims, a platform for managing fake accounts on a multitude of online services, like Twitter, Facebook, YouTube, Gmail, and many others. Reporters have identified "Jorge" as an Israeli businessman named Tal Hanan, who served in the Israeli special forces as an explosives expert. Team Jorge told reporters they only had three rules: (1) Nothing in Israel; (2) No American politics; and (3) "Nothing against Mr. Putin." According to Haaretz, the company had worked very closely with the infamous Cambridge Analytica.
[UPDATE: The item above was updated to correct a link to the Forbidden Stories article and to remove a mention that Team Jorge’s corporate entity was a company named Percepto International. That’s another, totally separate company that’s also in the business of selling influence operations. We just looked at the wrong Forbidden Stories article, as the publication is running a series on dis/misinformation sellers and had stories on both Team Jorge and Percepto out at the same time.]
Belgium's new vulnerability disclosure framework: The Belgian government has passed a new legal framework that protects security researchers from any legal backlash when disclosing security vulnerabilities. The framework formally entered into effect earlier this week, on February 15. It covers any vulnerabilities reported "in networks and information systems located in Belgium." One of the framework's downsides is that its protections are granted as long as the security researcher reports the vulnerabilities to the network owner but also the Centre for Cybersecurity Belgium (CCB), with the CCB acting as a gatekeeper and needing to grant its explicit approval before a vulnerability is publicly disclosed.
Sponsor section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
Cybercrime and threat intel
Klyushin trial ends: A US jury found Vladislav Klyushin, a 42-year-old Russian national from Moscow, guilty of hacking into companies and using stolen documents to trade shares using non-public information. Officials say that Klyushin, along with four other co-conspirators, earned more than $90 million from their scheme. Klyushin was arrested in March 2021 in Sion, Switzerland, and extradited to the US in December of the same year. His four accomplices are still at large. One of them is Ivan Ermakov, a former officer in Russia's GRU military intelligence agency. Ermakov is on the FBI's "Cyber most wanted" list and is also charged in the US with offenses related to interference in the 2016 US Presidential Election.
Emsisoft alert: Antivirus maker Emsisoft has put out a PSA that threat actors are using fake Emsisoft code-signing certificates to sign their malware and make it look like the attack came from one of their products.
KEV update: CISA has updated its KEV database with four new vulnerabilities that are currently being actively exploited. These are the zero-days patched during Patch Tuesday earlier this week—three from Microsoft and one from Apple.
Paradise ransomware campaign: South Korean security firm AhnLab says it detected a campaign that exploited a vulnerability in the AweRay's AweSun remote control program to deploy a version of the Paradise ransomware.
PYbot: The same company has also spotted a campaign using a fake Discord Nitro code generator to infect users with a version of the PYbot DDoS malware.
PyPI malware: Phylum discovered a malicious Python library distributed via the PyPI portal that came with a Go-based malware strain named Spark.
ESXiArgs update: Censys says that despite the attention the ESXiArgs ransomware outbreak got from news media and cybersecurity agencies, its IoT search engine has found that more than 500 new VMWare ESXi servers have been infected over the last few days. Most of the infected systems are located in France, Germany, the Netherlands, and the UK, and the successful attacks show that organizations still don't know how to protect their systems. Furthermore, Censys says that while ESXiArgs attacks began at scale at the start of February this year, they also found clues to suggest the threat actor behind this ransomware was encrypting ESXi servers as far back as October of last year.
Malware technical reports
PolyVice: INTRINSEC researchers have a report on PolyVice, the custom ransomware employed by the Vice Society ransomware gang, previously also analyzed by SentinelOne.
Hydra banking trojan: NCC's Fox-IT has a report out on Hydra, a banking trojan that targets Android devices, also known as BianLian (not to be confused with the similarly-named ransomware gang). Fox-IT says Hydra was one of the most active malware families of 2022, alongisde SharkBot and FluBot.
FatalRAT: ESET has identified a campaign using trojanized app installers to deliver the FatalRAT malware. The campaign used Google ads to promote malicious sites hosting the installers at the top of search results. ESET says the campaign, which ran between August 2022 and January 2023, targeted Chinese-speaking people in Southeast and East Asia.
"None of the malware or network infrastructure used in this campaign has been matched to known activities of any named groups, so for now we have not attributed this activity to any known group."
Brute Ratel: Yoroi has a technical report on the Brute Ratel adversary emulation toolkit, often used by APT and cybercrime groups in their operations.
Havoc: On the same note, Zscaler has a technical report on the Havoc open-source post-exploitation framework, recently abused in malware campaigns targeting government networks.
IcedID traffic: Netresec has a report on how to spot IcedID's network traffic. Defenders, assemble!
ProxyShellMiner: Morphisec reports new attacks delivering the ProxyShellMiner crypto-miner to Exchange servers via the ProxyShell vulnerabilities (CVE-2021-34473 and CVE-2021-34523).
GuLoader: AT&T's AlienVault division has published a report on the GuLoader malware downloader. Similar reports are also available from Crowdstrike, Trellix, and OALABS. AlienVault's report focuses on GuLoader's evasion tactics.
V3G4 botnet: Palo Alto Networks says a new variation of the old Mirai malware is currently infecting servers and IoT devices in order to build a DDoS botnet. Palo Alto Networks says this Mirai variation goes by the name of V3G4 and was spotted in the wild for the first time in July of last year. As of now, it has been seen targeting IP security cameras, webcams, telephony servers, Atlassian Confluence servers, and various other web-based server management panels.
Frebniis: Broadcom's Symantec division has discovered a new malware named Frebniis that is currently being by an unknown threat actor to target entities in Taiwan. The malware is typically installed on Microsoft IIS servers. Symantec was unable to find out how the malware is planted on these servers, but once installed, the malware acts as a backdoor for the attackers, executing commands it receives via special HTTP requests. One of these commands is to instruct IIS servers to act as proxies, which Symantec believes the threat actor is using to access resources on a company's internal network.
Mylobot-BHProxies connection: Security researchers at BitSight believe the operators of the BHProxies residential proxy service may be secretly operating the Mylobot malware botnet. The Mylobot malware was first spotted in 2017, and it works by infecting Windows systems and using them as proxies to relay network traffic. The Mylobot botnet peaked in early 2020 when it was counting around 250,000 unique daily infected devices. Subsequent versions of the malware made it more difficult to see the total number of infected hosts, but BitSight believes the botnet is still averaging at least 50,000 infected systems per day.
"At this point, we cannot prove that BHProxies is linked to Mylobot, but we have a strong suspicion, since Mylobot and BHProxies used the exact same IP 46.166.173.180 on an interval of 24 hours."
APTs and cyber-espionage
War in Ukraine and the pew-pews: Google TAG and Mandiant have released a joint report [summary, PDF] on how cyber operations evolved during the war in Ukraine last year. Among the report's conclusions was that while cyber operations and attacks with destructive malware peaked during the first four months of 2022, they slowed and appeared less coordinated throughout the rest of the year. Other portions of the report also cover Russia's influence operations and how the war caused a rift in the Eastern European cybercrime underground. Google and Mandiant also predict that Russian destructive cyber attacks will also expand as developments on the battlefield shift towards Ukraine and will likely also target NATO allies in the future.
Earth Yako: Trend Micro has discovered a new cyber-espionage campaign carried out by a threat actor it tracks as Earth Yako that targeted academia and research think tanks in Japan. The campaign has been taking place since January 2022. The attacks did not go unnoticed. In November 2022, the National Police Agency and the National Center of Incident Readiness and Strategy for Cybersecurity (NISC) issued a warning [PDF] about these hacking attempts. In addition, researchers say they've also seen a small number of Earth Yako operations also target organizations located in Taiwan.
Operation Silent Watch: Check Point says that a threat actor believed to work on behalf of the Azerbaijani government has launched a new campaign at the end of 2022 that targeted organizations in Armenia and Azerbaijani activists and dissidents. The campaign took place amid the second Nagorno-Karabakh war between Armenia and Azerbaijan. The attacks involved a new version of a malware strain named OxtaRAT, which was upgraded with better data theft and desktop surveillance capabilities.
Andariel's INNORIX attacks: A North Korean APT group known as Andariel is exploiting an old vulnerability in the INNORIX file transfer desktop agent to install one of their backdoors on victims' devices. The vulnerability was patched in October 2022. AhnLab didn't specify how the vulnerability was exploited (phishing, local, web-based, etc.).
WIP26: A new cyber-espionage group named WIP26 is targeting telecommunication providers in the Middle East. Discovered by security firm SentinelOne, WIP26 uses two backdoors named CMD365 and CMDEmber to steal data from compromised networks. These backdoors abuse Microsoft 365 Mail and Google Firebase for their command-and-control infrastructure and Microsoft Azure and Dropbox for data exfiltration and malware hosting. SentinelOne did not make a formal attribution for WIP26.
SideWinder APT: Group-IB has published a report with details on SideWinder APT attacks that took place between June and November 2021. SideWinder APT, also known as Rattlesnake, Hardcore Nationalist (HN2), and T-APT4, is one of the oldest nation-state threat actors that is believed to originate from India.
"The attackers attempted to target 61 government, military, law enforcement, and other organizations in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka."
Vulnerabilities and bug bounty
Jenkins update: The Jenkins project has security updates out for some plugins, including one that handles Azure credentials.
Patch Tuesday aftermath: Other security updates released during this month's Patch Tuesday cycle also include patches from Citrix, Cisco, Fortinet, SolarWinds, GitLab, Intel, and Mozilla.
CVE-2022-47966 (Zoho): VulnCheck researchers have a write-up on the CVE-2022-47966 vulnerability in Zoho's ManageEngine. The bug was patched last year. Proof-of-concept for this bug was released earlier this year, and it immediately came under active exploitation. VulnCheck's Jacob Baines looks at the PoC variations that have sprouted since then and how security solutions fail to detect them.
OT lateral movement: Forescout researchers have disclosed two new vulnerabilities that can be used to move laterally at the PLC level inside OT networks. The vulnerabilities—CVE-2022-45788 and CVE-2022-45789—impact Schneider Electric Modicon PLCs.
Infosec industry
Zscaler acquires Canonic Security: US cybersecurity behemoth Zscaler has acquired Israeli cloud security startup Canonic Security.
ChatGPT sucks: Malware sandboxing service ANY.RUN says it tested the ChatGPT service, and while the service has been proven to be good at helping cybercriminals write malware, the service sucks when it comes to reverse engineering and analyzing malware samples.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.