Risky Biz News: EU prepares continent-wide IR plan, complete with private sector cybersecurity reserves
In other news: FSB raids Moscow police departments following major leaks; first Pegasus infection found in Israel; 3CX was a supply chain attack in another supply chain attack.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The European Commission has published the first draft of its EU Cyber Solidarity Act, a legislative effort to improve cybersecurity across EU member states and establish a common incident response plan.
The new regulation includes three major areas of interest.
The first goal is to establish what the EU calls a European Cybersecurity Shield. In practice, the EU plans to interconnect the national Security Operations Centres (SOCs) of member states in order to boost information sharing.
"They will use state-of-the-art technology, such as artificial intelligence (AI) and advanced data analytics, to detect and share timely warnings on cyber threats and incidents across borders."
The second part is a new Cyber Emergency Mechanism, a set of procedures meant to help improve the coordination and response to both targeted and continent-wide cybersecurity threats.
This mechanism will include both pre- and post-incident actions. For example, joint efforts to prevent attacks and strengthen critical sectors, but also the availability of financial support for mutual assistance between member states in the case of an attack.
A crucial part of the Cyber Emergency Mechanism will also be the creation of an EU Cybersecurity Reserve. EU officials describe this cybersecurity reserve force as "a selected pool of trusted private companies providing managed security services, such as incident analysis or incident response coordination."
Officials say these companies will be pre-contracted and ready to be mobilized in support of member states in the case of significant and large-scale cybersecurity incidents. The EU's cybersecurity agency, ENISA, will be in charge of selecting and mapping these providers for the Union's needs. Let's hope this process doesn't get bogged down in the EU's notorious bureaucracy.
And last, the EU Cyber Solidarity Act also comes with a Cybersecurity Incident Review Mechanism meant to allow its security teams to asses, learn, and modify procedures based on past incidents.
The European Commission says implementing the EU Cyber Solidarity Act would cost €1.1 billion, of which two-thirds will be provided from the EU's budget, while the rest will come from member states.
EU officials started work on the new regulation in March of last year, after Russia's invasion of Ukraine, when it became apparent Russia was using its cyber capabilities both inside and outside Ukraine.
The EU Cyber Solidary Act will now go to the European Parliament and the European Council for feedback and approval.
Breaches and hacks
First Israeli citizen hacked with Pegasus: Haaretz reporters have discovered and confirmed the first case of an Israeli citizen having their device infected with NSO Group's Pegasus spyware. The victim was described as "an Israeli in his 30s who has been active in political protests in recent years." Haaretz says the victim's phone was first infected in April 2021 and then again in November 2022. The first infection was confirmed by cybersecurity firm ZecOps (part of Jamf), while the second by CitizenLab. Neither ZecOps nor CitizenLab couldn't identify who deployed the spyware, and it's unclear if it was an Israeli law enforcement agency.
Hacker returns 80% of stolen SafeMoon funds: The hacker who stole $8.9 million worth of assets from cryptocurrency platform SafeMoon has agreed to return 80% of the stolen funds, estimated at $7 million. SafeMoon says it would let the hacker keep the rest of the funds, calling it a "white hat bounty reward"—which it obviously isn't.
Failed cryptocurrency exchange attack: Japan's CERT team has published a report from a failed spear-phishing attack on a cryptocurrency exchange's employees. The victim was not named.
Wallet draining attacks: Taylor Monahan, the founder of MyCrypto and a developer of the MetaMask crypto-wallet service, says that a threat actor has been silently draining funds from cryptocurrency wallets across the internet in a massive campaign that began in December of last year. Monahan says the threat actor has stolen more than 5,000 ETH so far, representing more than $9.7 million at today's market prices. Monahan says he has not discovered how the attacks are taking place, but they don't appear to be involving any phishing. The attacker has also specifically targeted wallets storing large quantities of cryptocurrency, suggesting this was a very targeted attack. [Additional coverage in Bitcoinik]
General tech and privacy
Ad traffic stats: Ad-blocker company AdGuard says that roughly 7.24% of the traffic it sees through its browser extension are network requests connected to online ad trackers.
Battle.net DDoS attack: Activision-Blizzard's Battle.net client has been getting hit with DDoS attacks this week that are kicking all of the company's users out of their games. This happened several times this week.
Mullvad VPN raided by Swedish police: VPN service provider Mullvad says Swedish police raided its Gothenburg office on April 18 and served the company a search warrant. Mullvad says officials sought to seize computers storing customer data. The company says police left without taking any servers after they were told that no such data existed and that taking the devices that did not fit the warrant statute would be illegal under Swedish law.
Proton Pass: Proton, the company behind the ProtonMail secure email service, has launched a public beta of a new password manager named Proton Pass.
npm package provenance: GitHub has added a feature to allow JavaScript developers to link their npm packages to a GitHub repository and eliminate user friction from having to go down an npm package's possible source repo.
GitHub private vulnerability reporting: GitHub has formally launched a new feature called Private Vulnerability Reporting that allows users to privately report a security flaw to a public repo without having to spill exploit details via its public Issues Tracker section.
ICANN proposal: ICANN and Verisign have put forward a proposal to change domain registry agreements to allow any government in the world to easily seize .NET domain names. According to George Kirikos, President of Leap of Faith Financial Services, the proposal doesn't include any protections for registrars or domain owners. Kirikos believes this proposal is just a test to see how the community reacts before expanding it to other top-level domains like .COM.
Government, politics, and policy
Disinformation campaign hits Poland: Poland's Ministry of National Defense says that Belarusian hackers tried to scare Polish citizens with a series of SMS and Telegram messages. The message told Polish recipients they were recruited into the army and would be sent to fight in Ukraine. Officials attributed the campaign to Ghostwriter, a Belarusian hacking group specialized in running disinformation campaigns. They said this was Ghostwriter's third attempted disinformation campaign in Poland after they also tried two other operations in January and then in March.
FSB raids Moscow police: Officers with the FSB and the MVD have raided multiple Moscow police departments on suspicion that officers sold personal information of Russian citizens to Ukrainian entities. According to reports in RBC and TASS, searches have been going on for weeks, multiple police officers were detained, and more are being questioned. According to the Baza Telegram channel, the FSB is specifically investigating the sale of personal data of Russian judges and security forces.
Dutch MIVD yearly report: The Dutch Military Intelligence and Security Service (MIVD) says that Chinese private companies facilitated several cyber-espionage campaigns by Chinese military hackers against Dutch targets last year. MIVD officials believe that such operations were set up to help Chinese hackers remain anonymous and avoid public attribution. Dutch intelligence officials also say that Chinese universities currently play an important role in China's cyber-espionage operations by training personnel and developing tooling used in PLA offensive cyber operations. The revelations were part of the MIVD's public annual report for 2022. The same report also confirmed that GRU hackers hijacked Cisco routers across the Netherlands as part of an operation first revealed this week by UK and US authorities.
Law enforcement agencies plead to Meta: The Virtual Global Taskforce, an international alliance of 15 law enforcement agencies, has sent an open letter to Meta asking the company to reconsider adding end-to-end encryption (E2EE) features to Facebook and Instagram messages. The agencies argue this would hinder their own and Meta's efforts to fight the proliferation of CSAM on the platform.
Cybersecurity guide for smart cities: Cybersecurity agencies from Five Eyes countries have published a cybersecurity best practices guide for smart city systems. The guide puts forward three main recommendations to help communities strengthen their cyber posture: secure planning and design, proactive supply chain risk management, and operational resilience.
GOP partisanship meets cybersecurity: Attorneys General from Iowa, Missouri, and Arkansas have sued the US Environmental Protection Agency (EPA) for its "new, burdensome cybersecurity rule" [see here] they claim imposes "significant costs" on public water systems. The group, all coming from GOP-controlled states, are singing the old "big government bad, deregulation good" tune that the Republican party likes to sing. [Additional coverage in Inside Cybersecurity]
NCSC warning on commercial spyware: The UK's NCSC cybersecurity agency says that the proliferation of commercial spyware and hacker-for-hire services will become a global threat to individuals and private organizations in the coming years. The agency says that more than 80 countries across the world have bought cyber intrusion software over the last decade and is seeing thousands of people targeted with commercial spyware every year. NCSC officials say they expect the demand for hacker-for-hire services to rise. Officials anticipate that "significant financial rewards" may also incentivize government employees or contractors to become hackers-for-hire.
NCSC warns of Russia's lame hacktivist groups: The UK NCSC agency has issued a warning that Russia's new wave of hacktivist groups may soon move to more disruptive and destructive attacks against Western critical infrastructure.
"Although these groups can align to Russia's perceived interests, they are often not subject to formal state control, and so their actions are less constrained and their targeting broader than traditional cyber crime actors. This makes them less predictable."
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Pompompurin suicide attempt: There's an unconfirmed report that Conor Fitzpatrick, the 19-year-old hacker known as Pompompurin, tried to take his life this week. Fitzpatrick was detained by the FBI last month for running BreachForums.
PaperCut exploitation: Print management software maker PaperCut says that threat actors are actively exploiting a vulnerability to gain access to customer print management servers. The vulnerability—tracked as CVE-2023–27350—allows an unauthenticated attacker to get Remote Code Execution (RCE) on a PaperCut Application Server. PaperCut released a fix for the vulnerability in March. The company says threat actors are going after servers that have not been updated, and they are asking customers to patch systems to avoid getting hacked.
"If you suspect that your server has been compromised, we recommend taking server backups, then wiping the Application Server, and rebuilding from a 'safe' backup point prior to when you discovered any suspicious behavior."
Eval PHP exploitation: GoDaddy's Sucuri says it is seeing threat actors abuse Eval PHP, an abandoned plugin, to take over and backdoor WordPress websites.
npm malware: Phylum researchers have a report on a recent npm library that was trojanized with a Python-based remote access toolkit. This is the same "vibrance" library also spotted by Mend and covered in our last edition.
Bumblebee SERP poisoning: Secureworks says it is seeing a wave of Google search ads pushing boobytrapped versions of legitimate software that install the Bumblebee malware.
Spain phishing campaign: BlackBerry has a report on a massive phishing campaign impersonating Spain's tax agency. Final payloads include Vidar and IcedID.
EPOS phishing campaign: Cofense published a report on a phishing campaign targeting EPOS Net customers, a large Japanese credit card company.
OneNote phishing: Antiy researchers have documented a phishing campaign using OneNote files to infect targets with the Snake keylogger.
IPFS adoption grows: Palo Alto Network joins the ranks of Cisco Talos and Trustwave to warn that threat actors are increasingly adopting the IPFS peer-to-peer protocol as part of phishing infrastructure. The move comes after the IPFS protocol has become a core technology for many blockchains and after many cloud providers have added support for it to fill a market niche created by the infrastructure needs of modern Web3 cryptocurrency platforms.
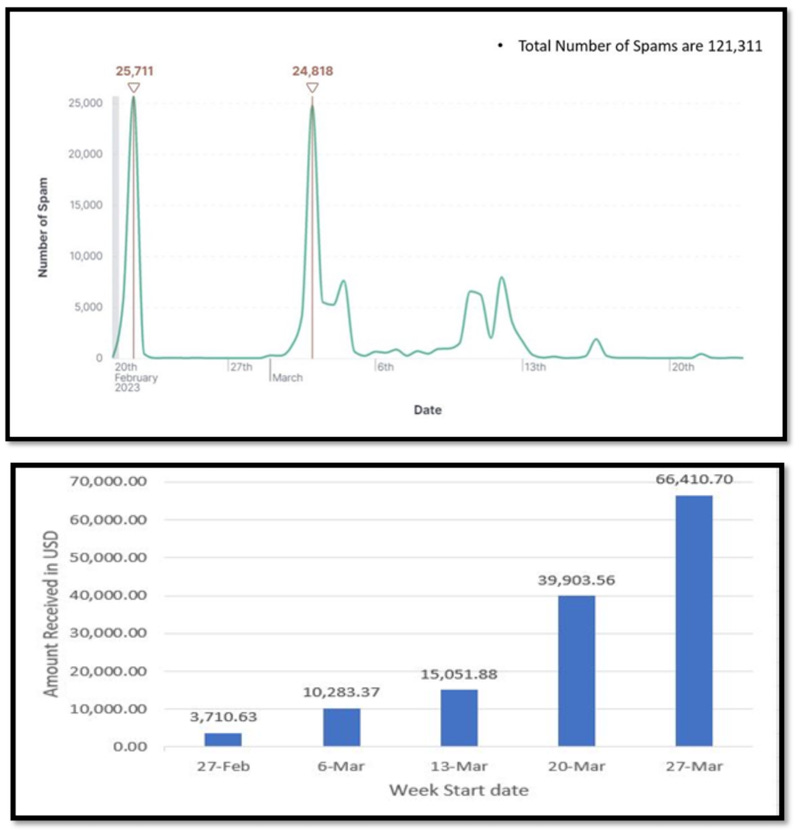
Extortion email campaigns: Security firm McAfee says it saw two major spikes of extortion email campaigns earlier this year in February and March. The emails threatened individuals to expose their web browsing history unless they paid a ransom demand of roughly $1,300. McAfee says that based on blockchain public transactions, the threat actors appear to have made roughly $130,000 worth of Bitcoin from the campaigns since the end of February alone.
LoRa used as a side-channel: Researchers with Nettitude Labs have created a proof-of-concept that uses the LoRa protocol as a side-channel command and control system inside compromised environments.
Censys State of the Internet Report: IoT search engine Censys says it found more than 8,000 internet-exposed servers that were hosting sensitive information, such as credentials, database backups, and configuration files. In addition, the company also found more than 40,000 instances of monitoring tools and API servers that were left exposed online without proper authentication. Censys researchers say these systems could be abused to conduct reconnaissance, giving detailed insight to attackers into a target's network. [More in the Censys 2023 State of the Internet Report]
Faceless proxy service: Infosec reporter Brian Krebs published a profile on Faceless, a proxy service that has helped cybercrime gangs disguise malicious traffic for the past seven years. In typical Krebs fashion, the article also comes with an exposé of the Faceless admins.
Xiaoqiying (Genesis Day, Teng Snake): Recorded Future says that a pro-Chinese hacktivist group named Xiaoqiying is planning to launch cyberattacks against organizations in Japan and Taiwan. The group first made its presence felt in late January this year when they defaced dozens of websites for South Korean research and academic institutions. Recorded Future says the group also plans to attack NATO countries as well as any country or region that becomes hostile to China.
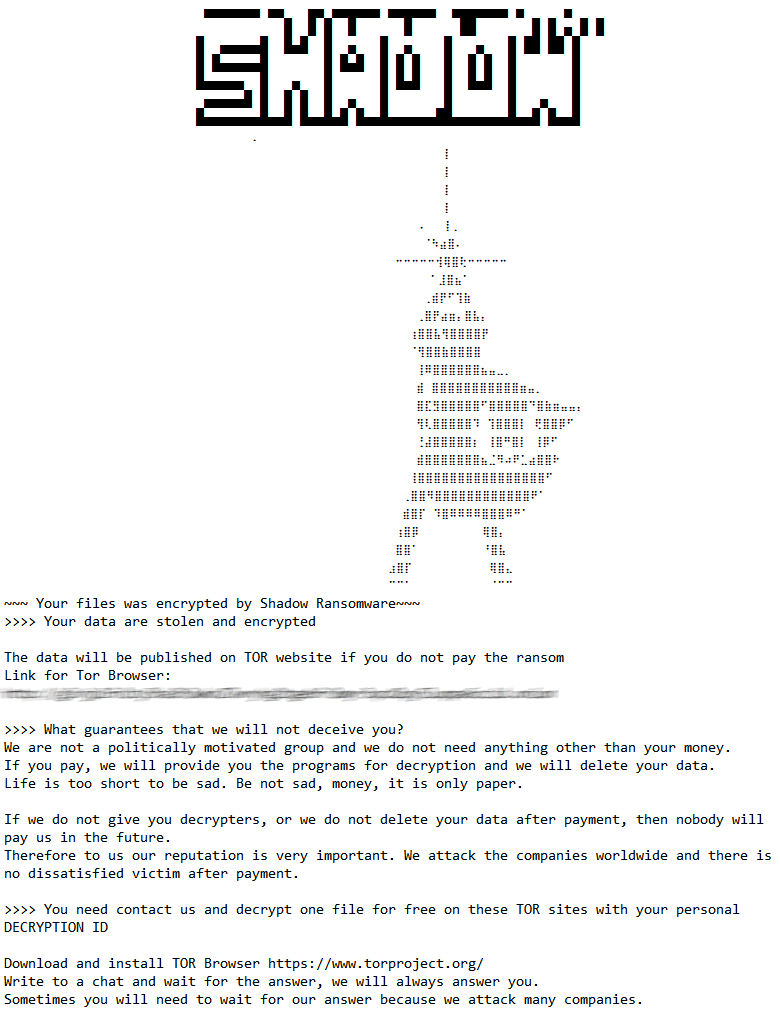
Shadow ransomware targets Russia: Group-IB researchers say that a new ransomware gang named Shadow is attacking Russian companies and demanding large ransoms of up to $2 million to decrypt their files. The group also operates a dark web leak site where they threaten to leak files in case victims don't pay. The Shadow group has been active since at least mid-March of this year and has also hit companies in Asia, the EU, and the US. Group-IB says Shadow built its ransomware on the leaked source code of the LockBit ransomware.
Malware technical reports
FlowCloud: NTT Security has published a report on FlowCloud, a backdoor used by the LookBack (TA410) APT group. While the malware has been used for quite some time now and has been deployed via phishing campaigns and vulnerability exploitation, NTT researchers say they've seen recent attacks where the malware was also dropped on Japanese networks via USB memory sticks.
AuKill: Sophos says that ransomware gangs have adopted a tool named AuKill to disable EDR security software on compromised environments before launching their file encryption operations. The tool works by abusing an outdated driver of the Microsoft Process Explorer application. So far, Sophos has seen affiliates for the Lockbit and Medusa Locker ransomware programs abuse AuKill in attacks earlier this year.
Play ransomware: Broadcom's Symantec division says it say the Play ransomware gang deploy two new tools in recent attacks. The first is Grixba, a network-scanning tool used to enumerate all users and computers in the domain. The second is Costura, a tool to copy data from the Volume Shadow Copy Service (VSS) that are normally locked by the operating system.
LockBit for macOS: SentinelOne has a technical analysis of LockBit's macOS ransomware test.
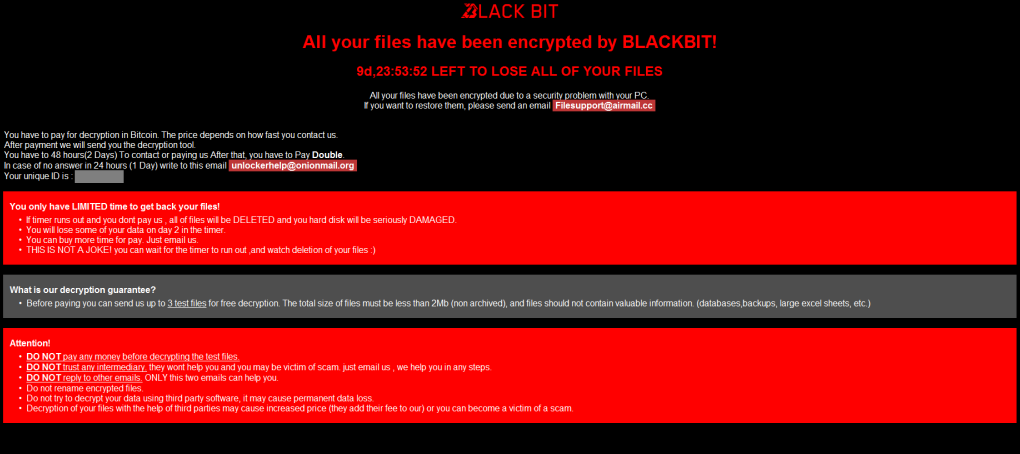
BlackBit ransomware: AhnLab has a report on the BlackBit ransomware, currently hitting South Korean organizations and actively distributed since September of last year.
Sponsor Section
Airlock Digital is one of this newsletter's four main supporters and this week's featured sponsor. Earlier this year, in May, Airlock Digital CEO David Cottingham held a product demo with Patrick Gray, the host of the main Risky Business podcast, showing how Airlock's allow-listing product works.
APTs and cyber-espionage
APT attacks on China: The Japan Cybersecurity Innovation Committee has published a report [PDF] of historical APT attacks that have targeted Chinese organizations. The report looks at APTs from Vietnam, India, Taiwan, the Korean peninsula, and the US.
Gamaredon leak: Researchers with EclecticIQ say they gained access to an SMTP email server panel operated by the Gamaredon Russian APT group. The server exposed past Gamaredon spear-phishing operations, such as campaigns targeting Ukrainian government entities like the Foreign Intelligence Service of Ukraine (SZRU) and the Security Service of Ukraine (SSU).
Google's Russian APT ops report: Google's TAG security team says that 60% of Russian cyber operations this year were aimed at Ukrainian targets. Google says it saw operations conducted by FROZENBARENTS (Sandworm) and FROZENLAKE (APT28), but also by PUSHCHA (Ghostwriter), a Belarusian threat actor supporting Russian operations.
ECCRR Russian-Ukrainian cyber war: The European Cyber Conflict Research Initiative (ECCRI) published a report [PDF] on the cyber operations that have taken place in the Russian-Ukrainian war.
SideCopy: Team Cymru has published a report uncovering new infrastructure operated by SideCopy, a Pakistan-based APT group. The report yet again confirms the group's attribution to Pakistan operators.
"There is specific evidence to demonstrate that the Action RAT infrastructure, connected to SideCopy, is managed by users accessing the Internet from Pakistan."
Daggerfly: Broadcom's Symantec division says they've seen the Daggerfly APT (aka Evasive Panda, Bronze Highland) target an African telco with new plugins of its MgBot malware framework.
APT43: The Google VirusTotal team has released a report on APT43 tooling and the visibility on its service.
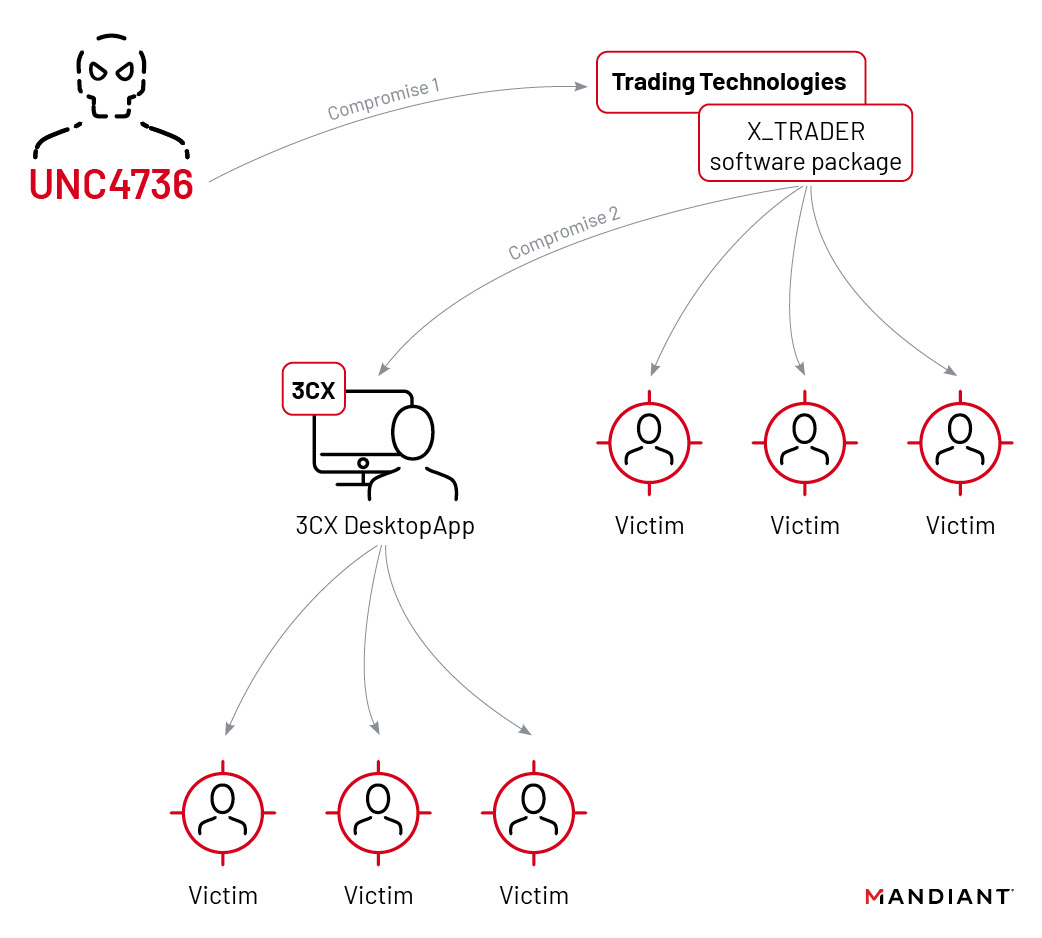
3CX supply chain inside a supply chain: Mandiant says it found the root cause of the 3CX supply chain attack, and the origin appears to be another supply chain attack. According to Mandiant, a 3CX employee got hacked after installing a backdoored official version of X_Trader, a stock market trading app created by financial software company Trading Technologies. Mandiant says the X_Trader app appears to have been backdoored before November 2021, a year after it was decommissioned by Trading Technologies and months before the 3CX employee installed the app. In a blog post, 3CX confirmed the timeline and said the employee's personal device was compromised via the X_Trader app, from where the hacker pivoted to its corporate network. The incident marks the first time that a supply chain attack was caused by a previous supply chain attack. While security firms attributed the initial 3CX hack to the Lazarus Group, a broad codename used to describe North Korea's state-sponsored hacking apparatus, Mandiant says the 3CX and Trading Technologies supply chain attacks were actually the work of a Lazarus sub-group known as UNC4736. Remaining on the topic, ESET has also published its own analysis of the 3CX supply chain attack. Its report covers some separate Lazarus Linux malware that has links to the malware used during the 3CX incident. [Additional coverage in Wired and Zero Day]
Vulnerabilities and bug bounty
OpenAI bug bounty program: OpenAI, the maker of ChatGPT, has launched a bug bounty program.
Kubernetes security audit: NCC Group has concluded and published a new security audit of the Kubernetes automation platform. Nothing major found.
New Spectre exploits: Google security researchers have found two new ways to exploit the Spectre CPU vulnerability in the Linux kernel. Both issues—tracked as CVE-2023-0458 and CVE-2023-0459—have been fixed.
TLS session ticket vulnerabilities: A team of academics discovered vulnerabilities in TLS session tickets, a mechanism that allows servers to suspend and then resume secure connections. Researchers say that many servers use guessable keys to encrypt session tickets, allowing attackers to decrypt TLS traffic or impersonate the server. Web hosting providers such as AWS and StackPath were found to be running servers that were vulnerable to attacks.
Dirty Vanity technique: Deep Instinct has published details about Dirty Vanity, a new code-injection technique that abuses forking, a lesser-known mechanism that exists in Windows operating systems.
Google Chrome zero-day: Google has released Chrome v112.0.5615.137/138 that fixes eight security flaws, including a new zero-day (CVE-2023-2136). The zero-day was discovered by Google's TAG team and came after the team patched another zero-day last week. That one was abused by a surveillance vendor.
Oracle security updates: Oracle has released its quarterly security updates. The company has patched 433 vulnerabilities across several product families.
BrokenSesame: Cloud security firm Wiz has discovered an exploit chain comprised of a container escape and accidental 'write' permissions that allowed it to execute remote code inside Alibaba Cloud databases.
Apache Druid vulnerability: Chinese security firm Chaitin says that a recently patched Apache Kafka RCE vulnerability (CVE-2023-25194) also impacts the Apache Druid analytics engine. Researchers say the Druid project is vulnerable because it comes with a feature to import data from Kafka servers.
WD My Cloud vulnerability: Trend Micro has published a technical report on CVE-2022-29844, a buffer overflow vulnerability that was used to gain access to a Western Digital My Cloud NAS device during the Pwn2Own Toronto 2022 hacking contest.
Infosec industry
New tool—Security Notes: Refactor Security has open-sourced Security Notes, a Visual Studio Code extension to aid code reviews from a security perspective.
Acquisition news: Akamai has acquired API security company Neosec. The acquisition is expected to close in the second quarter of 2023.
Group-IB exits Russia: Group-IB says it exited the Russian market, sort of. The original Group-IB company split operations in the late 2010s between a Singapore-based company and a Moscow-based entity. Now, Group-IB co-founder and CEO Dmitry Volkov says he is no longer a shareholder of the Russian company after selling his 10% stake in the Russian asset. At the same time, Group-IB co-founder Ilya Sachkov sold his stake (37.5%) in Singapore-based Group-IB Global Private Ltd. to members of the company's top management.
Cybersecurity Skills Initiative: Microsoft is expanding its Cybersecurity Skills Initiative to Argentina, Chile, Indonesia, and Spain, and delivering grants to nonprofits to help skill people for the cybersecurity workforce. With this expansion, Microsoft is now working in 28 countries around the world.