Risky Biz News: EU sanctions Russian disinformation network
In other news: Kenyan government systems see major disruption following cyberattack; Google rolls out Unknown Tracker Alerts; CoinsPaid blames North Korea for recent hack.
This newsletter is brought to you by GreyNoise. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Spotify:
The European Union has sanctioned the operators of a Russian disinformation network known as "RRN" (Recent Reliable News) for spreading fake news and propaganda about Russia's invasion of Ukraine.
The EU says Russian government bodies participated in creating, running, and disseminating RNN's fakes on social media.
Five organizations and seven individuals managing them, including GRU agents, were added to the EU's sanctions list.
InfoRos, a GRU-run news agency that manages more than 270 fake news sites (previously sanctioned by the US as well).
Institute of the Russian Diaspora, a fake "institute" founded by InfoRos' leadership to disseminate their content.
ANO Dialog, a Russian non-profit organization created by the Moscow Department of Information and Technology that posts propaganda via the "War on Fakes" Telegram channel and adjacent website.
Social Design Agency and Structural National Technologies, two Russian IT firms supporting the RNN network.
The sanctions come in the aftermath of a report published by the French government in June, exposing the network.
French authorities say the network operated its own websites, where they posted disinformation, but also used typosquatting to create websites that posed as EU government portals and local media outlets.
Articles published on these sites pushed narratives that the Ukrainian government and army were associated with neo-Nazi groups, that Ukrainian refugees were responsible for crimes across Europe, and that sanctions against Russia were damaging European countries.
Articles also claimed that EU countries were guilty of war crimes because they supplied arms to Ukraine, that EU weapons were sold on the black market, that Ukrainian government officials were stealing from EU donations, and that radioactive clouds were heading toward EU cities from the discharge of UK weapons that contained depleted uranium.
In France, the RNN network created a website posing as the French Ministry of Foreign Affairs and published an article claiming the country had introduced a "security tax," whose proceeds would go to Ukraine. In another case, RNN created a fake site posing as the French Ministry of Interior that claimed French citizens would be forced to house Ukrainian refugees.
The network published content targeting EU countries but also the Middle East and the Americas.
The French government says RNN disinformation was amplified using bots on social media networks like Facebook, Twitter, and Telegram.
Stories and narratives were also often boosted by the official accounts of Russian embassies and cultural centers across the world.
"France condemns these acts, which are not worthy of a permanent member of the United Nations Security Council. No manipulation attempt will dissuade France from supporting Ukraine in the face of Russia's war of aggression."
RNN is also the same disinformation network that was unmasked in September 2022 by Meta, Qurium, DFRLab, and the EU Disinfo Lab. In a series of joint reports, the four called the network "the largest of its kind" but said that its content was low quality, low effort, and received little interaction.
Breaches, hacks, and security incidents
Pentagon leak (another one): The FBI and the Pentagon are investigating a potential compromise of the Air Force's communications system after an engineer took home sensitive government radio equipment. The incident took place at the Arnold Air Force Base in Tennessee, where the engineer was employed. According to court documents, he was reported by government contractors who noticed erratic behavior consistent with insider threats. The FBI says the engineer stole equipment worth more than $90,000, and the breach impacted 17 Air Force facilities and possibly even the FBI's own communications systems. [Additional coverage in Forbes/non-paywall]
eCitizen disruption: A cyberattack has disrupted Kenya's eCitizen online platform and has brought down access to more than 5,000 government services. The incident impacted passport applications, the issuing of e-visas for foreign travelers, the release of ID cards and driver's licenses, as well as electricity payments. A pro-Kremlin group calling itself Anonymous Sudan has claimed responsibility for the disruption, claiming Kenya meddled in the affairs of the Sudanese government by offering to mediate a peace deal in the country's civil war. However, the attack suspiciously took place shortly after Kenyan officials criticized Russian President Vladimir Putin for not renewing a crucial deal that would have allowed Ukrainian grain to flow to African countries. [Additional coverage in the BBC]
DepositFiles leak: DepositFiles, one of the largest and oldest file-hosting and file-sharing services, exposed a configuration file that could have granted attackers access to its infrastructure. Exposed information included the credentials for the site's database, abuse and support emails, payment systems, and social media accounts. [Additional coverage in Cybernews]
CoinsPaid blames hack on North Korea: Estonian cryptocurrency platform CoinsPaid says it was hacked for $37.3 million after abruptly suspending withdrawals last week. The company has not revealed any details about how the incident took place but blamed the attack on North Korea's Lazarus hacking group. CoinsPaid has asked crypto platforms that received some of its stolen assets to aid in recovering the funds.
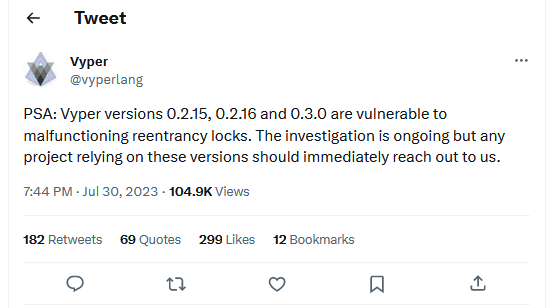
Vyper crypto-heists: A threat actor has exploited a zero-day vulnerability in Vyper, a programming language for creating blockchain smart contracts. At least five cryptocurrency platforms have lost more than $25 million worth of crypto-assets so far. The list includes AlchemixFi ($13 million), JPEG'd ($11 million), MetronomeDAO ($1.6 million), Ellipsis Finance ($68,600), and Debridge Finance ($24,600). According to cryptocurrency experts, the vulnerability allows attackers to bypass security protections and carry out reentrancy attacks.
General tech and privacy
New Azure AD security feature: Microsoft has launched a new Azure AD security feature to continuisly enforce access policies for users. The feature will scan if a user's token is being used IP addresses inside a preset geo-location range and invalidates tokens used from the outside. The feature was developed to block replay attacks using stolen authentication tokens. The feature is in public preview and available for testing with apps such as Exchange Online, SharePoint, Teams, and Microsoft Graph.
Apple cracks down on device fingerprinting: Apple has updated its developer program to crack down on developers abusing some of its API features to collect data on user devices in order to track them online. Apple says that even if a user has given an app permission to track their activity, fingerprinting the underlying device is still not allowed. The company says that with the release of iOS 17 and macOS Sonoma this fall, developers who want to access certain API features will have to provide a valid reason to do so. Apps that don't provide a good reason won't be accepted on the App Store starting next spring.
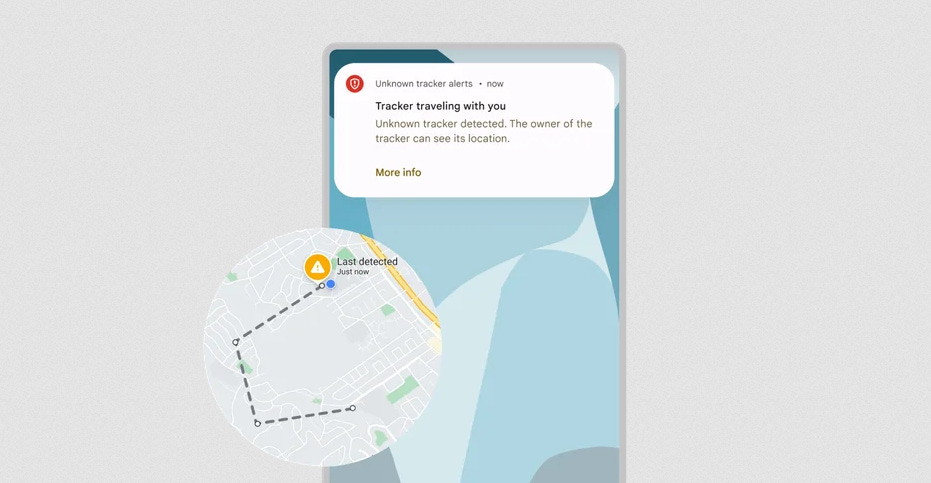
Google rolls out Unknown Tracker Alerts: Google is rolling out a new feature to its Android devices to show popup alerts whenever an unknown Bluetooth device is traveling with the user. Officially known as "Unknown Tracker Alerts," the feature is based on a technical specification Google developed together with Apple. The new spec is meant to prevent threat actors from using AirTag-like devices to track users or their property without authorization.
Government, politics, and policy
US Cyber Force update: The US government has moved closer to establishing a new separate branch of the Armed Forces dedicated solely to cyber operations. The US government has directed the National Academy of Public Administration to conduct an assessment on the feasibility of establishing a seventh branch of the US military, named the US Cyber Force. The provision was included in the National Defense Authorization Act that passed the US Senate last week. [Additional coverage in The Record]
New Army and Air Force cyber teams: Both the US Army and the US Air Force have created new specialized cyber teams to support their kinetic teams with cyber tasks related to intelligence gathering, electronic warfare, and sensors.
Senator demands Microsoft investigation: Oregon Senator Ron Wyden has asked the US government to investigate Microsoft for its security lapses that enabled the SolarWinds and Storm-0558 hacks. The two incidents allowed Russian and Chinese hackers access to sensitive government systems. Sen. Wyden says Microsoft never took responsibility for its failures in both incidents and listed all the ways the company failed to protect its systems in both cases. He demanded investigations from the Justice Department, the Federal Trade Commission, and the Cybersecurity and Cyber Safety Review Board.
DETOUR Act: A group of US senators has introduced a bill to prohibit large online platforms from using deceptive user interfaces to trick consumers into handing over their personal data. It also bans using users for behavioral experiments without their consent. The new bill goes by the Deceptive Experiences To Online Users Reduction (DETOUR) Act and focuses on stopping tech giants from using practices known as "dark patterns." In addition, social media companies will also be prohibited from using designs intended to create addictive and compulsive usage patterns among children under the age of 17.
The Hunt for Volt Typhoon: The US government is hunting for malware planted inside military and critical infrastructure networks by Chinese hackers. The hunting effort is related to the activity of a Chinese APT group named Volt Typhoon, exposed in a report by Microsoft this May. Officials say the group's activity predates the Microsoft report for at least a year and stretches far beyond military and telecommunications targets. The White House believes China may use the malware to disrupt military operations in the event of a conflict. Confirming an NYT report, John Hultquist says Mandiant has spotted the group in "land, air, and sea transportation targets which could be leveraged for a serious disruption to logistics." [Additional coverage in the New York Times/non-paywall]
"There is a debate inside the administration over whether the goal of the operation is primarily aimed at disrupting the military, or at civilian life more broadly in the event of a conflict. But officials say that the initial searches for the code have focused first on areas with a high concentration of American military bases."
Jordan passes new cybercrime law: The Jordanian Parliament passed a cybercrime law last week that limits what people can say and do on the internet and criminalizes any criticism of the government. The law introduces jail terms of at least three months and fines of $7,000 or higher for spreading "false news" that undermines "national unity." Citizens who specifically attack other persons online can be sent to jail and fined at least $35,000. The law has been widely criticized by privacy groups and Western governments for limiting free speech or any valid criticism of the government. [Additional coverage in The New Arab]
Russian law impacts FOSS participation: The Russian Parliament has passed three bills banning Russian citizens from participating in the activities of foreign non-profit organizations that have not registered with the Russian government. Russian IT experts say the laws have an unintended side effect and may prevent software developers from contributing to some open-source projects. Because the laws have been intentionally drafted with vague language, they can be used to prosecute programmers just for filing a bug report or submitting a code commit. Open-source projects managed through non-profits and foundations that fall under the new laws include the Linux kernel, the Firefox browser, and most major database systems and programming languages.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with GreyNoise founder and CEO Andrew Morris about the company's vast network of honeypots and how they're preparing to take it to the next phase.
Cybercrime and threat intel
SSNDOB admin pleads guilty: Ukrainian national Vitalii Chychasov has pleaded guilty to fraud and hacking charges related to the running of SSNDOB, a cybercrime platform that sold the personal information of more than 24 million Americans. Chychasov was arrested in March 2022 while attempting to enter Hungary and was extradited to the US in July 2022 when the FBI also seized all the SSNDOB portals. Chychasov faces a maximum penalty of 15 years in federal prison. Officials say Chychasov made at least $19 million from running SSNDOB. As part of the plea deal, he agreed to forfeit $5 million.
TA2541 update: An incident responder known as y0sh1mitsu has published an update on the tactics used by TA2541, a cybercrime group known to sling RATs at companies from the aviation and transportation verticals.
Akira-Conti connection: Security firm ArctivWolf assessed with high confidence that some former Conti-affiliated threat actors may be connected to the new Akira ransomware operation. Other security firms like K7 and Antiy previously said the same thing.
New npm malware: Sixteen malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
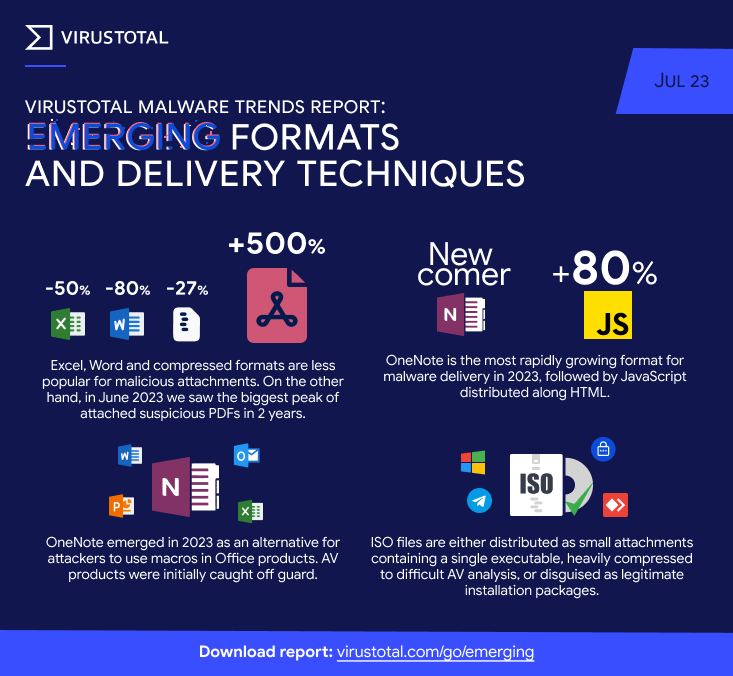
VT malware trends: Email attachments have remained the most popular method of delivering malware in the first half of the year, according to trends observed by Google's VirusTotal division. Traditional file formats such as Excel, Word, and compressed archives saw a decline this year. In their place, threat actors are adopting OneNote documents and JavaScript payloads. Following last year's crackdown on macro-based malware from Microsoft, Google says OneNote, in particular, emerged this year as everyone's favorite macro replacement.
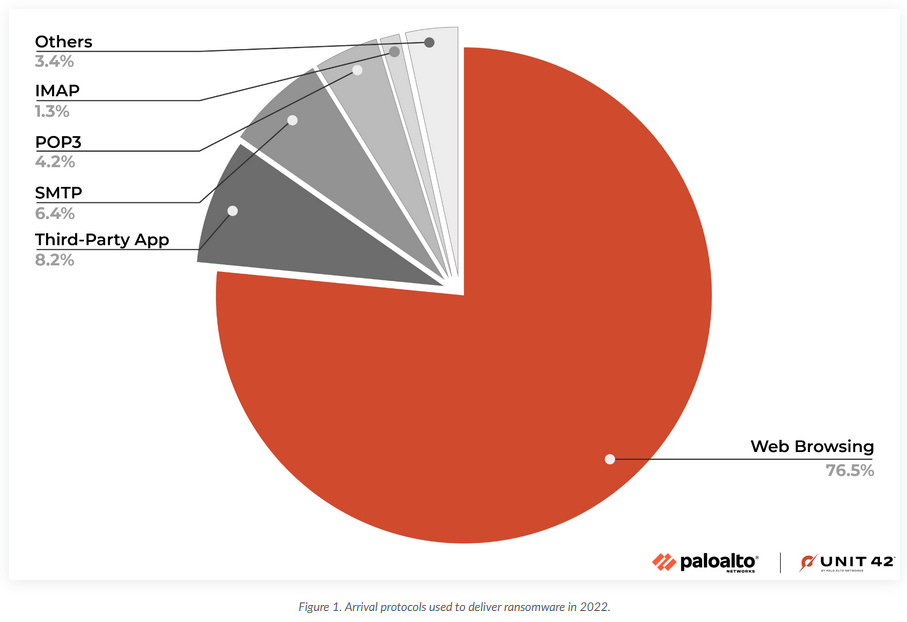
Ransomware delivery methods in 2022: The vast majority of ransomware payloads spotted in 2022 were delivered to users via the browser rather than phishing links or other protocols. According to data compiled by Palo Alto Networks, browser delivery account for 76% of all ransomware events the company detected last year. The vast majority of these payloads were ransomware strains targeting end users rather than large enterprises. Most payloads were hosted on social media and file-sharing services.
Malware technical reports
CherryBlos: Trend Micro has discovered a new Android malware strain named CherryBlos that targets cryptocurrency users. The malware was designed to steal cryptocurrency wallet credentials and replace addresses when users attempt to make transactions, redirecting funds to the malware's creators. CherryBlos also contains a hidden feature that uses OCR to scan local images and read any embedded text in the hopes of discovering wallet mnemonic phrases that may have been saved on the victim's device. Trend Micro says the malware has been active since April and has been distributed using Telegram channels and YouTube and TikTok clips.
Submarine: CISA has released three malware reports with IOCs and descriptions for three different backdoors found on Barracuda email servers. These backdoors have been deployed after an unidentified attacker used a zero-day (CVE-2023-2868) in the Barracuda server. The reports cover a generic reverse shell, SEASPY (a backdoor that disguises as a legitimate Barracuda service), and SUBMARINE (a never-before-seen backdoor that lives inside the server's SQL database).
Sponsor Webinar
In this webinar, GreyNoise's Abigail Whidden explores the powerful combination of Splunk and the GreyNoise platform and how customers can leverage GreyNoise's vast intelligence on internet-wide scans and attack activity to enhance security operations.
APTs and cyber-espionage
Bahamut: CyFirma looks at some of the Android malware used by the Bahamut APT in campaigns targeting Southeast Asia.
APT37's STARK#MULE: Securonix published a report last week on STARK#MULE, a spear-phishing campaign carried out by North Korean group APT37 targeting Korean-speaking individuals. The emails used a US Army and military recruitment lure.
Mustang Panda: Sophos has a Mastodon thread on a recent PlugX malware sample they believe is linked to a Mustang Panda campaign.
Vulnerabilities, security research, and bug bounty
LLM Attacks: A team of academics has developed a method that constructs adversarial attacks on LLM systems, allowing users to bypass security protections and run malicious queries. Similar attacks have been developed in the past, but they require a substantial amount of manual effort to analyze the LLM and design the malicious queries. Researchers say their attack is different because it can generate malicious queries in an automated fashion with little work needed from the attacker.
IDOR alert: CISA, the NSA, and Australia's ACSC agencies have released a joint security advisory to warn software developers and vendors about the dangers of leaving IDOR vulnerabilities unaddressed in their applications and APIs. Standing for Insecure Direct Object Reference, IDOR vulnerabilities happen when apps or APIs allow an attacker to access sensitive data without authentication or because of broken access controls. This marks the first time that the three agencies issued a joint alert about a vulnerability type. The alert comes after an IDOR vulnerability was exploited in the MobileIron MDM to breach 12 Norwegian government agencies. IDOR vulnerabilities are also ranked #1 in the OWASP API Security Risks Top 10 list.
GNOME vulnerability: Security research Zac Sims has discovered a vulnerability in librsvg, the library responsible for rendering SVG images on Linux GNOME desktops. The vulnerability (CVE-2023-38633) can allow local or remote attackers to disclose files from the user's OS.
Vulnerabilities exploited in the wild: Apache Shiro (CVE-2023-34478) and OpenSSH (CVE-2023-38408) vulnerabilities are being exploited in the wild, according to SOS Intelligence.
FallingSkies PoC: Datack researchers have published a PoC exploit for a CloudPanel authentication issue tracked as CVE-2023-35885 and known as FallingSkies. CloudPanel is a free hosting software that can run static sites, PHP, Node.js and, Python applications.
Ivanti (MobileIron) PoC: Proof-of-concept code has been published on GitHub for the Ivanti EPMM (MobileIron Core) zero-day (CVE-2023-35078) that was exploited in the wild earlier this month to hack into the network of several Norwegian government agencies. Expect widespread exploitation from ransomware gangs.
Another Ivanti RCE: In the meantime, Ivanti released a security update on Friday to patch another RCE in the same product—with a CVE identifier of CVE-2023-35081. The vulnerability was discovered and reported by security firm Mnemonic.
Infosec industry
New tool—BadZure: Splunk's Mauricio Velazco has released a tool named BadZure that populates Azure AD with misconfigured tenants for security testing purposes.
New tool—WSPCoerce: Canadian security researcher Simon Lemire has released a tool named WSPCoerce to coerce authentication from Windows hosts using MS-WSP.
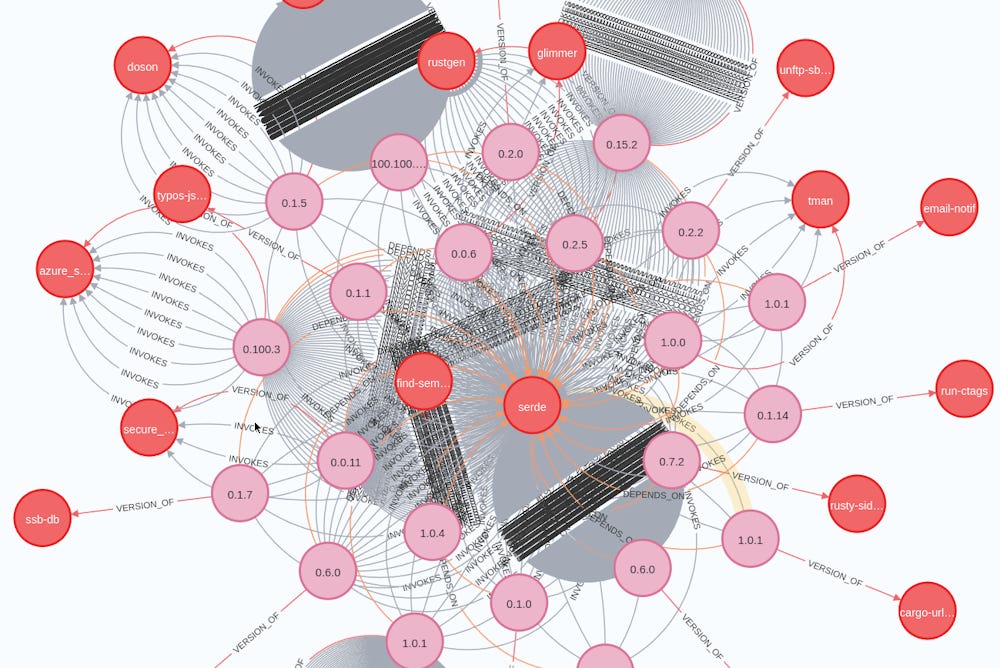
New tool—Painter: The Rust Foundation has open-sourced a tool named Painter to help secure the supply chain of Rust projects. The tool creates a call graph for the entire Rust Crates ecosystem and maps out all dependencies of all versions in all history, allowing investigations into a project's historical dependencies.
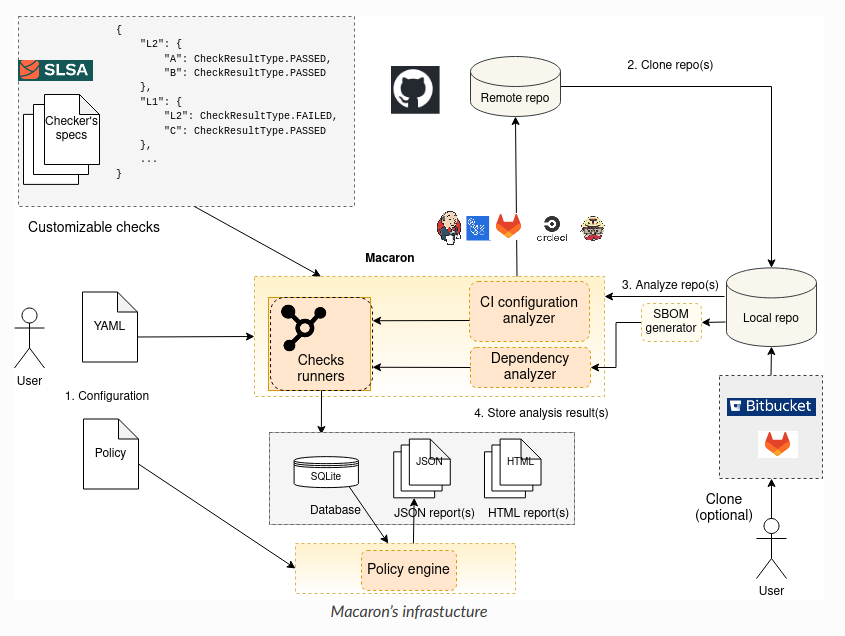
New tool—Macaron: Oracle has open-sourced a supply chain security analysis tool named Macaron.
"Macaron is an analysis tool which focuses on the build process for an artifact and its dependencies. As the SLSA requirements are at a high-level, Macaron first defines these requirements as specific concrete rules that can be checked automatically. Macaron has a customizable checker platform that makes it easy to define checks that depend on each other."
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at when it makes sense for governments to invest in building their own secure phones.