Risky Biz News: First Kazakhstan-based APT discovered, tries to disguise itself as Azerbaijan
In other news: New side-channel attack impacts Apple devices; US states sue Meta; and two crypto-mining botnets infect 1.25 million PCs.
This newsletter is brought to you by Resourcely, the company that can help you manage Terraform securely. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
In a blog post this week, researchers with Cisco Talos have formally linked a cyber-espionage group named YoroTrooper to Kazakhstan, making it the first official APT group operating out of the country.
First spotted in the wild in June 2022, the group has followed the pattern of most nascent cyber espionage programs, starting with run-of-the-mill commodity malware and slowly moving to custom capabilities in recent attacks.
Throughout the past year, the group has primarily targeted former Soviet states in what appears to be a classic intelligence collection operation meant to support Kazakhstan's state objectives.
Talos says the group has successfully compromised state-owned websites and accounts belonging to government officials in several CIS states. Past operations also targeted embassies and energy organizations in the same countries and even some EU agencies as well.
The group's attacks have been hard to pinpoint in Kazakhstan. Talos says YoroTrooper has purchased VPN accounts and configured exit nodes to make their attacks appear as coming out of Azerbaijan, a country known to have a similar cyber espionage program.
Researchers say that other clues also played a role in their attribution, such as the fact that the group rarely targets Kazakh entities—with the exception of an operation against the country's Anti-Corruption Agency.
Furthermore, the group appears to have what Talso calls a "defensive interest" in the country's state-owned email service—Mail.kz. Cisco researchers say the group often conducts security scans of the service but has never bothered attacking it or registering look-a-like domains.
In addition, Talos has also spotted the group heavily using the Kazakh language and converting from Bitcoin to Kazakh currency. When it needs to use other languages—such as Azerbaijani—the group uses public tools like Google Translate to translate the text to Russian, Kazakhstan's second language, and for which there is better support on Google Translate.
Unlike some Belarussian cyber-espionage groups that appear to work together with Russian APTs, this also does not seem to be the case for YoroTrooper. Both Cisco reports on the group suggest it has repeatedly targeted entities in Russia, so this might not be the case of a second Ghostwriter APT.
Breaches, hacks, and security incidents
Cuban mercenaries: Pro-Ukrainian hacking group Cyber Resistance has "intercepted" new evidence of Cuban mercenaries joining the Russian Army to fight in Ukraine. The group hacked a Russian military officer earlier this year to reveal how Cubans were being recruited and transported to Russia to fight in Ukraine.
TransForm attack: The IT networks of five hospitals across Ontario are down following a cyberattack on a joint IT provider. TransForm says the incident has taken down appointment systems and some provisioning systems.
Meta locks pro-Palestine accounts: Social media company Meta has locked several Facebook and Instagram accounts that were posting pro-Palestine content. The company told NBC News they locked the accounts after they spotted a possible security breach. Meta says it is working to contact the original account owner and restore access.
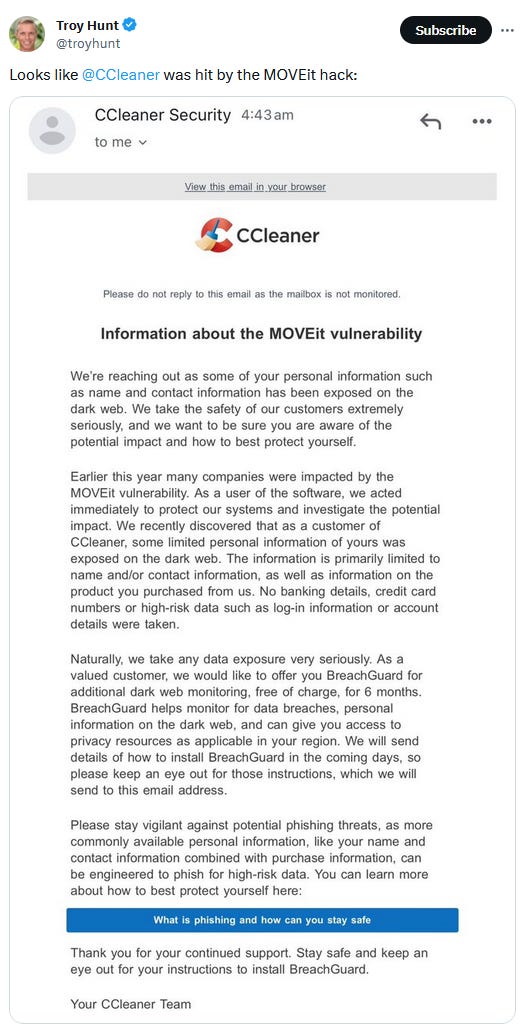
CCleaner joins MOVEit list: Avast's CCleaner app has joined the list of entities impacted by this year's MOVEit hacks.
General tech and privacy
Win11 SMB encryption: Current insider preview versions of Windows 11 now support SMB encryption for outbound connections.
Government, politics, and policy
US OAGs sue Meta: State attorneys general in 41 states and the District of Columbia have filed a collective lawsuit against social media giant Meta. Officials say the company knowingly designed algorithms and features to addict children and teens to its Instagram and Facebook platforms. Officials point the finger at features like infinite scrolling, near-constant notifications, and autoplay videos that create a sense of FOMO and cause mental health issues for young teens. The lawsuit is the result of a multi-state probe the coalition began in 2021 that started in a handful of states and expanded nationwide.
ICE's GOST: 404 Media has a profile on Giant Oak Search Technology (GOST), a database system used by the ICE to find "derogatory" social media posts by people seeking entry into the US.
Online Safety Bill becomes law: The UK's Online Safety Bill has passed through the Parliament and has become an official UK law. Now known as the Online Safety Act, its provisions force tech companies to take responsibility for the content they host on their platforms. The Act gives the UK government the power to force internet companies to remove child sexual abuse material, online scams, anonymous trolls, deepfakes, and other content the government will deem illegal. Companies that fail to act on the UK government's requests face fines of up to £18 million ($22 million), or 10% of their global annual turnover. Tech executives could also face prison time under certain circumstances.
Poland to finally investigate Pegasus abuse: Poland's new ruling coalition plans to create a parliamentary commission to investigate the use of Pegasus spyware by the previous government. The commission will look at how the former ruling party PiS used Pegasus to spy on opposition members, journalists, and prosecutors. The European Union has called out Poland for its use of the spyware, but the former government has never taken any action in response. [Additional coverage in Reuters]
Moldova blocks 22 Russian sites: Moldova's intelligence service has blocked access to 22 Russian news sites for engaging in an "informational war." The biggest names on the list are sites linked to RT (formerly RussiaToday), Mir TV, and Vesti FM. ISPs have been ordered to block access to the sites. The country previously suspended six Russian-language TV stations in 2022 for promoting pro-Kremlin misinformation about Russia's invasion of Ukraine.
RuNet censorship: Russia's communications watchdog Roskomnadzor says it is now blocking access to 167 VPN services and more than 200 foreign email providers. According to a rare statement from the agency, the Roskomnadzor is also blocking access to more than 590,000 web pages but says that most are malicious, such as phishing and malware distribution sites. Besides a blocklist, the agency also runs a whitelist, which allegedly contains more than 17,000 IP addresses to which the agency's filtering rules are not applied. [Additional coverage in Interfax]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Resourcely CEO Travis McPeak about the modern DevOps ecosystem, how giving developers tools with security baked in keeps everyone safe and happy, and how that's easier than expecting your software engineers to become cybersecurity experts overnight.
Cybercrime and threat intel
Arrests in Nigeria: Nigerian police's cybercrime unit has detained six suspects and dismantled a cybercrime recruitment and training hub active in the country's capital, Abuja. Officials say the group was involved in romance scams, BEC, and fraudulent investment schemes. Members also dabbled in hacking and trading social media accounts. Along with the arrests, Nigerian police urged landlords and building owners to report any similar hubs operating on their properties.
Fake PoC targets security researchers: Chinese security firm Shanshi has discovered a fake PoC for a GeoServer vulnerability (CVE-2023-25157) that was infected with the VenomRAT and used to lure and target security researchers.
Twitter malvertising: Sponsored ads from verified Twitter users are pushing online scams targeting the cryptocurrency community. Also known as another day ending with "y" on Twitter.
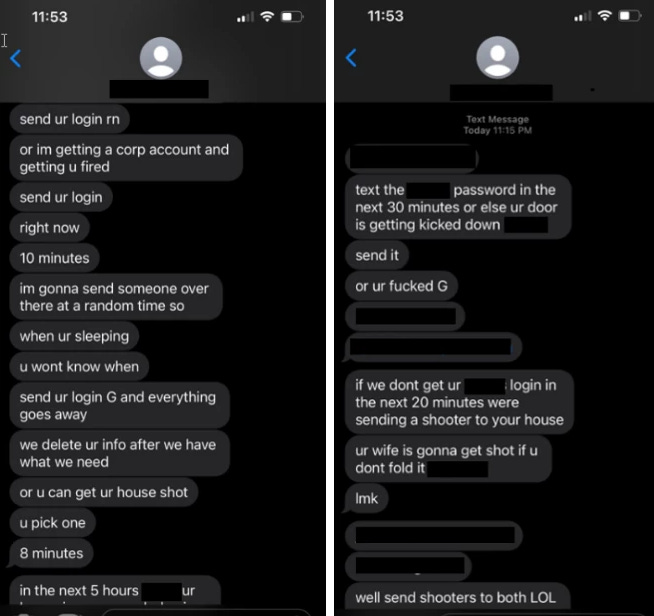
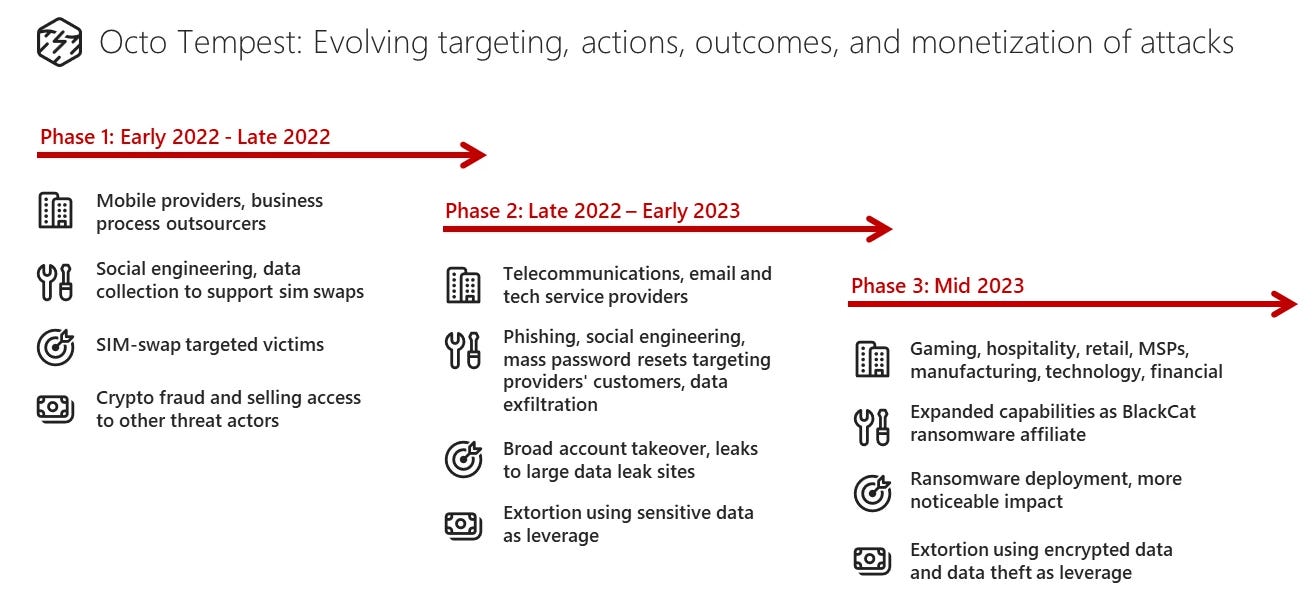
Octo Tempest: The hacking group behind recent breaches at Caesars and MGM casinos has used threats of physical violence and gun shootings to coerce some of their victims into handing over enterprise credentials. According to a recent Microsoft report, the threats are typically made against a company's tech support and help desk personnel. The Microsoft report is the first to officially confirm—screenshots included—that the group uses physical threats to gain initial access to victim networks. A Cyberscoop report has linked the group's members to an underground community named The Com, where members allegedly learned to SIM swap, arrange house swatting incidents, and commission real-life violence. The report also warns that the group has now expanded from simple extortion schemes to ransomware, having an active partnership with the AlphV operation. Microsoft tracks the group as Octo Tempest, but they are also known as 0ktapus, Scattered Spider, and UNC3944.
Malware technical reports
MOUSEHOLE: Dragos has published part two of a technical analysis of MOUSEHOLE, one of the five modules of PIPEDREAM, an ICS malware framework developed by the Chernovite group. See part one here.
StripedFly: A malware botnet named StripedFly is suspected to have infected more than one million Windows and Linux PCs since it first began operating in early 2017. The botnet uses the leaked NSA exploit EternalBlue to spread and comes with modules for performing network reconnaissance, harvesting credentials, and mining cryptocurrency. Security firm Kaspersky says the botnet uses a custom version of the EternalBlue exploit that was compiled before the original exploit was leaked online in April 2017. Researchers have not attributed the botnet to any particular threat actor, but infosec reporter Kim Zetter points out that a Chinese espionage group named BuckEye had been seen using the EternalBlue exploit a year before it was leaked.
Huge crypto-mining botnet: Russian security firm Positive Technologies has discovered a crypto-mining operation that has infected more than 250,000 Windows PCs. Most of the infected systems are located in Russia and other Soviet states. The reason for the large number of infected users in the region is because the botnet's operators used Russian torrent sites to spread apps infected with their malware.
ScamClub landing pages: Confiant researchers have published an analysis of landing pages used by the ScamClub group. The company worked with industry partners last month to take down some of the group's infrastructure.
BlackDream ransomware: Security researchers have spotted a new ransomware family named BlackDream being used in attacks across Southeast Asia.
Rhysida ransomware: Avast researchers have published an analysis of the Rhysida ransomware, first spotted in the wild earlier this year in May.
BbyStealer returns: Symantec is seeing new campaigns leveraging the BbyStealer malware.
"The threat actors behind it have been leveraging multiple phishing websites advertising free download of Windows installers for various Virtual Private Network (VPN) applications."
DuckTail: Cluster25 looks at the DuckTail malware and its most recent campaign targeting Italian-speaking users via LinkedIn.
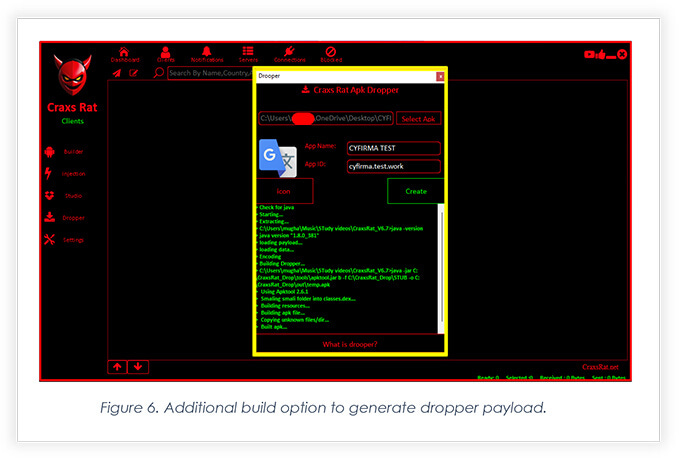
Craxs RAT: CyFirma has published a report on Craxs, a RAT developed by a developer based out of Syria. The latest RAT update adds a dropper component to make it easier to deploy additional payloads/malware strains.
Sponsor Demo
Listen to Resourcely CEO Travis McPeak talk with Risky Business Snake Oilers host Patrick Gray about the company's automagic Terraform cloud-provisioning technology.
APTs and cyber-espionage
Russian spying: Russian security firm Kaspersky says it discovered a Go-based backdoor that was used over the past few months to steal sensitive data from Russian government and industrial organizations. The company has not attributed the campaign to any APT group, but the operation seems to have been focused on intelligence collection.
APT28: France's cybersecurity agency, the ANSSI, has published a report reviewing APT28's latest operation techniques, dating back to 2021. The report is only available in French. An English version is likely to be published in the next weeks.
Winter Vivern: The Winter Vivern APT group has used a zero-day vulnerability to breach Roundcube webmail servers belonging to European government entities. The attacks were discovered by security firm ESET in early October, and a patch was released last week. The zero-day (CVE-2023-5631) is a stored XSS that allows the group to steal an account's emails. Prior to developing its own zero-day, ESET says the same group used older bugs to hack Roundcube and Zimbra email servers earlier this year in a different campaign. The exact same bugs were also exploited by a Russian cyber-espionage group named APT28, but ESET says Winter Vivern is a different group that may have possible ties to Belarus.
Operation Triangulation, part III: Kaspersky has published part three of its Operation Triangulation report. Parts one and two are here. They cover the TriangleDB malware and its modules. Part three covers the iOS exploit used to deliver the malware on targeted devices.
AridViper: Sekoia researchers have looked at the activities and internal structure of AridViper, the Hamas-linked APT group operating out of Palestine. Sekoia says the group was still active.
"AridViper seems to be organised in two subgroups, one conducting cyber espionage activities towards Israel and any entities in the Middle-East region susceptible to be involved in Palestine affairs, the second focusing on surveillance activitiestowards Palestinian Hamas opposition including the Fatah rival movement or individuals linked to the Palestinian Authority."
Yellow Liderc's IMAPLoader: PwC's security team looks at IMAPLoader, a new .NET malware strain employed by the Yellow Liderc Iranian APT group. The malware is named IMAPLoader because it is controlled via email messages and used to deploy additional payloads. PwC says IMAPLoader is deployed with the help of malicious JavaScript installed on watering hole sites where victims are selected based on their interests in the maritime, shipping, and logistics sectors.
Vulnerabilities, security research, and bug bounty
Google VRP expands to AI: Google has expanded its vulnerability research program to cover generative AI technologies. Named VRP for AI, the program will cover scenarios like prompt attacks, training data extraction, model manipulation, adversarial perturbations, and data model extractions. Microsoft also expanded its bug bounty program to cover AI earlier this month.
Tor Browser security audit: The Tor Project has published the results of a recent security audit of the Tor Browser and several other adjacent systems.
CISA KEV ransomware section: Nucleus Security's Patrick Garrity looks at how the new "ransomware" section in CISA KEV will impact vulnerability management and patching operations.
"Small" Windows zero-day: ACROS Security has discovered a zero-day vulnerability in Windows that can allow threat actors to prevent the OS from applying the Mark-of-the-Web on malicious documents. ACROS says that despite their finding, they "haven't found a realistic attack scenario" where the zero-day could be exploited in practice.
F5 BIG-IP RCE: Praetorian researchers have discovered a pre-auth RCE vulnerability (CVE-2023-46747) in the F5 BIG-IP load balancer. F5 has published security updates and a mitigation script, to be applied as needed. The bug has a severity rating of 9.8/10.
Grammarly vulnerability: Researchers at Salt Security have discovered a vulnerability in the OAuth implementations of Grammarly, Vidio, and Bukalapak that can be leveraged to hijack user accounts.
JS crypto vulnerabilities: Security researcher Zemnmez has found weak hashing algorithms being used in two JavaScript cryptography libraries.
Cisco IOS XE PoC: Security firm Horizon3 has published what it describes as a theoretical PoC exploit for two recent Cisco IOS XE zero-days (CVE-2023-20198 and CVE-2023-2073).
Apple security updates: Apple has released security updates for iOS. No zero-days this time. Phew!!!
iLeakage attack: A team of academics has developed a side-channel attack named iLeakage that targets Apple devices. The attack can be used to lure users to malicious web pages and then recover data from their Safari browser, such as passwords and the content of other tabs. Researchers say the attack is practical in the real world and works against Apple devices with A and M-series CPUs. The team notified Apple of the iLeakage attack in September 2022, but the company has not released any fixes.
Infosec industry
Market news: Defense company RTX is selling its cybersecurity division to private equity firm Blackstone for $1.3 billion. [Additional coverage in DefenseNews]
SOC burnout: According to a Tines survey of 900 security professionals, roughly 63% say they are experiencing some level of burnout after most saw workloads increase over the past year. Most blamed burnout problems on their SOC teams being understaffed. Even if 99% are satisfied with their job, more than half are considering switching jobs in the next 12 months for either better pay or lighter workloads.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq discuss "spooky effects," aka when agencies play silly buggers with target computers.