Risky Biz News: Hacker exposes 986 Bitcoin addresses operated by Russian intelligence agencies
In other news: Chinese hackers outnumber FBI cyber staff 50 to one; DOJ detected SolarWinds hack six months before everyone else; major cPanel vulnerability needs patching.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
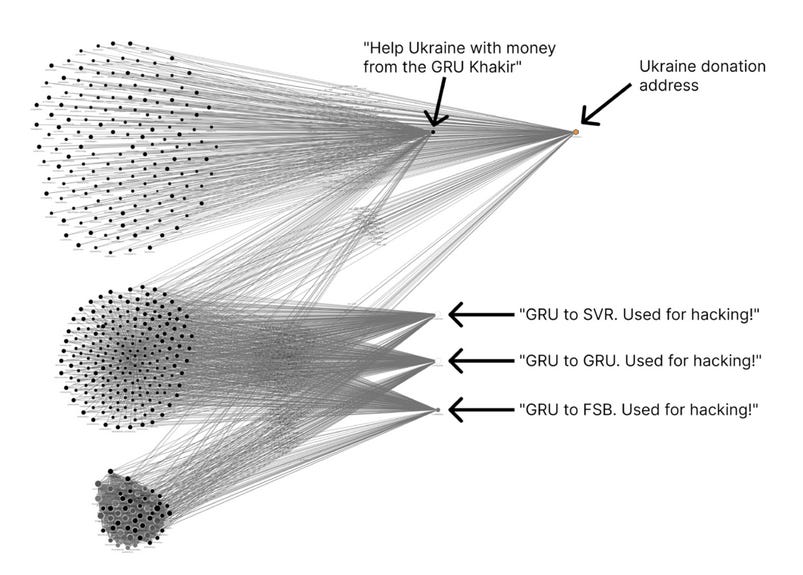
A suspected hacker has exposed 986 Bitcoin addresses allegedly operated by Russia's three main intelligence services—the Foreign Military Intelligence Agency (GRU), Foreign Intelligence Service (SVR), and Federal Security Service (FSB).
The hack and subsequent leak were discovered by blockchain analysis company Chainalysis. The company believes the hacker gained access to the private keys of several GRU wallets.
Between February 12 and March 14 last year, the hacker then proceeded to send transactions to other wallets. Each transaction contained a note in the OP_RETURN field identifying the recipients as a GRU, SVR, or FSB account.
Calling themselves the "GRU Khakir," the hacker claims the agencies use the Bitcoin addresses for hacking operations.
Once Russia invaded Ukraine, the hacker stopped exposing GRU, SVR, and FSB blockchain addresses and began sending funds to wallets raising donations for Ukraine's war effort.
Speaking at CoinDesk's Consensus conference last week, Chainalysis CEO Michael Gronager says he believes the hack-and-leak are real because the hacker didn't send small transactions that would have gone unnoticed but burned more than $300,000 of Bitcoin in the process.
"Our hypothesis is that the OP_RETURN sender did this to make the discovery of the transactions, and the accusations associated with them, more likely," the company also wrote in a report.
Three of the 986 Bitcoin addresses that received funds were previously known to have been used by Russian intelligence in past operations, such as for the SolarWinds hack and to lease servers for the DCLeaks website.
Breaches and hacks
DOJ SolarWinds hack: Kim Zetter reports for Wired that the US Department of Justice detected the breach related to the SolarWinds supply chain attack in May of 2020, six months before the incident became widely known in December of that year. Despite the early discovery, the DOJ's security team and experts from Mandiant and Microsoft could not determine the significance of the DOJ breach and the larger attack. The SolarWinds hacks became widely known after hackers also breached Mandiant and Microsoft's own networks, leading the two companies to focus more investigative efforts on the intrusions.
0VIX crypto-heist: A hacker has stolen roughly $2 million worth of cryptocurrency using a flash-loan attack on the 0VIX platform. The incident caused users to panic and withdraw more than 75% of the platform's funds, according to CoinDesk.
Casenet leak: The state of Missouri's judicial records website left exposed documents containing the Social Security numbers and personal information of thousands of Missourians, the Saint Louis Post-Dispatch discovered. Missouri Supreme Court officials acknowledged the leak and fixed the Casenet website.
Americold breach: Cold storage company Americold has been hacked, and several of its IT systems have been down for almost a week, according to an email the company sent customers. The company says it suffered a network breach on the night between Tuesday and Wednesday last week and is still investigating the incident. It expects IT systems to be down throughout the week. [Additional coverage in BleepingComputer]
General tech and privacy
Firefox Private Network EoL: Mozilla will discontinue its Firefox Private Network browser extension on June 15 this year. Launched in 2019, FPN is a browser extension that funnels the user's web traffic through Mozilla's servers, acting as a proxy system. The extension was only available to US users, never made it out of beta stage development, and was eventually replaced with Mozilla's VPN desktop app, a superior product that could protect a user's entire traffic and not just their web activity.
GnuPG's ADSK: The GnuPG project has added a new feature named Additional Decryption SubKey (ADSK) that acts like its name implies—as a second decryption key. GnuPG says it developed this feature to allow companies to decrypt the email communications of employees who are absent from their jobs, have left the company, or to decrypt emails for archival purposes.
"Another use case for ADSKs is to split keys between several devices (e.g. desktop and mobile). For example the secret part of the key for the mobile device could be on a token for additional security but on the desktop the key is on-disk because the desktop is less likely lost or stolen. The ADSK of a lost device could then be revoked and a new one generated for a new device."
Bing better at censorship than Chinese search engines: Researchers with CitizenLab analyzed the search results of eight search engines that serve the Chinese market (Baidu, Baidu Zhidao, Bilibili, Microsoft Bing, Douyin, Jingdong, Sogou, and Weibo). Surprisingly, while Baidu had the most censorship rules, CitizenLab says Microsoft's Bing ran broader political censorship rules that "affected more search results than Baidu."
Chrome 113: Google started rolling out early versions of its Chrome v113 browser update to users last week. The rest of Chrome users will receive the update this week. Upcoming changes are detailed here.
Government, politics, and policy
Chinese cyber staff outnumbers FBI staff: FBI Director Christopher Wray says China has a bigger cyber program than all the major nations combined. Wray says Chinese hackers outnumber the FBI's cyber personnel by at least 50 to one. At a Congress budget hearing, Wray requested an additional $63 million for the agency's annual budget so the agency could beef up its cyber staff with 192 new positions. [Additional coverage in CNBC]
Secure Software Self-Attestation public comment: CISA and the OMB are requesting public comments on the Secure Software Self-Attestation Form [PDF], a set of guidelines for providing secure-by-design software for use in US federal government networks. The public comments period ends on June 26. "This requirement will not only affect direct suppliers (i.e., those who provide software directly to federal agencies), but also their suppliers, and so on. In other words, a significant share of software providers that are part of the global software supply chain are impacted by all the policies following President Biden's executive orders," Henrik Plate, lead security researcher at Endor Labs, told this newsletter.
Fake Russian hacktivists: Head of the Department of Cyber Information Security in the Security Service of Ukraine, Illia Vitiuk, says that most of the pro-Kremlin hacktivists groups active today are either fronts or are coerced into launching attacks by various Russian government agencies. Vitiuk says that currently, 90% of cyberattacks targeting Ukraine are either conducted by special services or by state-sponsored groups. "I do believe that there is no so-called 'hacktivism' in Russia at all," the official told CyberScoop.
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
BreachForums forum password strength: According to this analysis on Reddit, users on the now-defunct BreachForums had the strongest passwords among hacking forum users. In addition, BreachForums users also had stronger passwords than "the average password strength in the banking industry and the United States as a whole."
Chinese dark web markets: CyberInt has a report comparing the two largest Chinese-speaking dark web marketplaces—Deepmix and Chang'an. The two platforms have a history, with Deepmix accusing Chang'an of being "a fake trading website" and stealing some of its users' passwords.
PaperCut attacks: Sophos has a report on the exploitation attacks targeting PaperCut print management servers. Payloads observed on hacked servers included Truebot (downloader, often linked to Cl0p ransomware), Buhti (ransomware), MoneroOcean (coinminer), and Mirai (botnet).
Cisco SNMP exposure: IoT search engine Censys says that it discovered more than 39,000 Cisco routers exposing their SNMP ports over the internet. The company notes that these devices are potentially vulnerable to attacks with CVE-2017-6742, a vulnerability that was recently at the center of a joint US-UK security alert. Cybersecurity agencies from both countries said that in 2021, a Russian cyber-espionage group named APT28 used an exploit for the vulnerability to compromise devices across the world.
Magecart campaign: Malwarebytes says it spotted a Magecart campaign that hijacks an online store's own resources to create realistic-looking modal popups to hijack checkout processes and steal a buyer's financial details. The campaign has been seen hitting various PrestaShop-based European stores.
New npm malware: Ten new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
BakerHostetler IR report: American law firm BakerHostetler has published its 9th annual security incident response report, based on data from over 1,160 security incidents from the prior year. One of the report's more interesting findings was that ransomware-related incidents were scarce throughout the start of the year before ransomware gangs ramped up attacks toward the end.
"In 2022, we saw increases in average ransom demands, average ransom payments, and average recovery times in most industries. The lull in ransomware that marked the start of the year is over. Ransomware groups have resumed attacks, and organizations must redouble their efforts to defend themselves against increasing attacks."
NBIP DDoS report: NBIP (the Dutch National Internet Providers Management Organisation) says DDoS attacks in the first quarter of 2023 were at their highest number since late 2021, with Dutch organizations getting hit by 676 attacks, 26 of which lasted more than 4 hours.
BGP incidents report: Russian networking security company Qrator Labs says it detected more than 9 million BPG route leaks and more than 3 million BGP hijacking events throughout Q1 2023. While the numbers look huge, Qrator says the figures are almost the same as they were in Q4 2022.
Package repository report: DevSecOps company Phylum says that in the first quarter of 2023, it found more than 800,000 spammy packages published across the package repositories such as npm, PyPI, RubyGems, Nuget, Golang, Cargo, and Maven. The company says it also spotted more than 6,000 packages that referenced malicious URLs, more than 1,600 packages that requested and executed remote code, and thousands of others that engaged in typosquatting, obfuscated their code, or were registered with throwaway email addresses.
Zscaler phishing report: Cybersecurity firm Zscaler says phishing attacks saw a 47% increase last year. The company notes the "growing use of phishing kits and AI tools to launch highly effective campaigns that bypass traditional security models, including MFA." Last year's most targeted brands included Microsoft's OneDrive and Sharepoint, followed by crypto-exchange Binance and illegal streaming services.
Ransomware report: Coveware says that ransomware gangs are back at attacking large corporations like in the old days after attacks and average ransom demands took a dive throughout 2021 and 2022 following a series of high-profile attacks that triggered several law enforcement actions. Coveware reports that the average ransom payment they saw in Q1 2023 was ~$327,000, while the median was ~$158,000. In addition, 45% of ransomware attacks this year had an initial ransom demand of over $1 million. While the ransom was either ignored or negotiated down, the trend shows ransomware gangs are getting desperate and looking for a huge payday more often than not. All in all, Coveware says that in Q1 2023, they believe that 45% of the companies that got ransomed eventually paid their attackers, a number that went up from the 37% recorded in Q4 2022.
Sophos yearly report: Cybersecurity firm Sophos says the median dwell time an attacker spent inside a compromised network before being detected went down to 10 days in 2022, down from 15 days in the previous year. The smaller dwell time number is similar to what other security firms have also documented. Mandiant reported a dwell time of 16 days, while Secureworks reported a dwell time of 11 days, showing a clear trend across the industry. Compiled with data from Sophos incident response engagements, the report also showed ransomware's clear dominance of the IR space, with almost 70% of Sophos IR engagements being ransomware-related.
Malware technical reports
Sliver: ImmersiveLabs have a report on how defenders could detect Sliver C&C traffic inside their networks.
Rapture ransomware: Trend Micro has published a report on the new Rapture ransomware. The company says Rapture is "cleverly designed" and has many similarities to the older Paradise ransomware strain.
Sponsor Section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
APT37: Chinese security researchers have published a report on APT37 (Group123, InkySquid, Reaper, Red Eyes, ScarCruft, or Venus 121) and a recent campaign targeting South Korean organizations with the RokRat malware.
BouldSpy: Mobile security firm Lookout has discovered a new Android spyware strain named BouldSpy. The company says the malware is typically installed on the smartphones of people arrested by FARAJA, one of Iran's law enforcement agencies. Lookout says it found evidence of the malware's use since March 2020, but traffic to the malware's command-and-control servers spiked during the height of the Mahsa Amini protests in late 2022, suggesting police might have installed it on the devices of detained protesters. Lookout says that based on data they "exfiltrated" from BouldSpy's C&C servers, the spyware appears to have been used on more than 300 people, ranging from minority groups to suspected criminal group members. This marks the second incident where an Iranian government agency installed malware on the personal devices of Mahsa Amini protesters. In October of last year, Trail of Bits security researcher Hamid Kashfi also found that the Islamic Revolutionary Guard Corps, a branch of the Iranian military, was manually installing malware on the devices of detained anti-government protesters.
APT28: Ukraine's CERT team says Russian cyber-espionage group APT28 is behind a series of "Windows update" emails sent to Ukrainian government employees during the month of April 2023. CERT-UA says the emails asked employees to run a PowerShell script in order to update their Windows installation and "protect against hacker attacks." CERT-UA says the script would collect data on the infected system and send it to Mocky API server.
Vulnerabilities and bug bounty
Satellite hacking: Cybersecurity firm Thales has successfully hacked a test satellite operated by the European Space Agency (ESA). Thales says they identified vulnerabilities that could enable malicious actors to disrupt the ESA satellite's operations. The hacking took place at a test workbench set up by ESA at the CYSAT conference last week.
"The results of the ethical satellite hacking exercise, the first of its kind in the world, will be used to tighten security for the satellite and its onboard applications, helping to improve the cyber resilience of space systems, protect sensitive data and support the long-term success of space programmes."
CVE-2023-29489 (cPanel): AssetNote researchers have discovered an XSS vulnerability (CVE-2023-29489) that impacts the cPanel web hosting platform. AssetNote says the vulnerability is a severe one, as it allows an attacker to execute arbitrary JavaScript code on almost every port of a cPanel-hosted server. This is a pre-authentication attack, and the only condition is that cPanel runs in its default setup. An attacker could abuse this bug to act on behalf of the cPanel platform and install web shells on customer servers. A patch was released at the end of February, but it's unclear how many of the 1.4 million cPanel installations currently available online have been patched. Proof of concept code has also been released.
Salesforce Aura leak: Security researcher Doug Merrett says that many Salesforce Community sites are leaking the private information of their owners and registered users. Infosec researcher Brian Krebs has identified leaks on websites operated by the state of Vermont, the District of Columbia, TCF Bank, and Huntington Bank. The leaks have been linked to a misconfiguration in Salesforce Community that allows an unauthenticated user to access URLs and content that should only be available to registered and authorized users.
Infosec industry
FACCT: Group-IB Russia, which split from its international division, is now known as FACCT.
ATT&CK v13: MITRE has released v13 of the ATT&CK framework. This new update comes with new techniques, new malware, and new groups.