Risky Biz News: Iranian state hackers breached US government agency and deployed a cryptominer, out of all things
In other news: Google wins lawsuit against Glupteba botnet operators; Popopret gets suspended sentence; France fines Discord for GDPR violations.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
In a joint security advisory this week, CISA and the FBI revealed that an Iranian APT group breached the network of a US government organization in an attack that could have turned out much worse than it did.
The breach took place earlier this year, in February, and CISA and FBI incident responders said the threat actor used an exploit for the Log4Shell vulnerability to take control over a VMWare Horizon server, moved laterally inside the victim's network, compromised the domain controller and local credentials, and deployed reverse proxies on several hosts for future access.
The report doesn't mention anything about sensitive data collection or abuse of the agency's email domain for espionage purposes but instead claims that the intruders deployed a very basic and widely known cryptocurrency mining app known as XMRig to mine the Monero cryptocurrency on the agency's servers, for their own personal gains.
This seems odd, but if you've read enough reporting on Iranian APTs, it's actually not that strange since it's widely known at this point that the Iranian government heavily relies on third-party contractors to carry out offensive cyber operations and espionage activity.
Previous reports have linked several of these groups to both classic espionage activity but also to your run-of-the-mill financially motivated cybercrime, usually carried out from the same infrastructure but for the personal gain of the operator, who would most likely know that because of their Iran citizenship, they would face almost no consequences for their actions.
For example, Iranian threat groups have been linked to internet-wide scans that compromised corporate systems, which were later put on sale on cybercrime forums. They've also been linked to different ransomware strains and subsequent payments, but also to the theft of academic papers that were later resold internally, in Iran, on dedicated web portals.
While the joint alert doesn't mention the victim, the Washington Post cites people familiar with the investigation who claim that the compromised agency was the Merit Systems Protection Board, a small government agency established to protect government workers against partisan political actions. Obviously, not the high-end US government target you'd expect, which would explain why the intruders chose mining over espionage.
WaPo also identified the Iranian hacking group as Nemesis Kitten. This group—also known as DEV-0270, Cobalt Mirage, APT42, and UNC788—has been linked in the past to attacks with the Log4Shell vulnerability, but also ransomware.
Some security experts have already suggested that deploying a cryptominer could be a cover to hide their espionage-related operations, but is it, though?
If there's one thing that's known about cryptomining is that it's noisy as hell. Once you deploy a cryptominer, your entire server slows down to a crawl, which often leads to your IT team looking into your active process lists and spotting XMRig, one of the most common signs that you've been hacked. In a government agency, that usually implies calling in the feds and DHS, so this theory doesn't particularly hold up.
It's quite possible that the intruders either didn't have the vision to see how they could abuse MSPB's position in the US government infrastructure, or they just didn't care or know what they compromised.
Breaches and hacks
Infosys leak: Cybersecurity firm Infosys has leaked a FullAdminAccess AWS keys on PyPi for over a year, according to Tom Forbes, a Python developer from the UK.
Hyundai fined: South Korea's data privacy watchdog has fined automaker Hyundai 3 million won ($2,000) after the company's engineers shipped untested code to one of its servers that exposed the personal data of six customers. According to the commission's inquiry, the server in question was responsible for an app that broadcasts real-time sales information.
Dom.ru leak: Hackers have leaked the alleged database of Dom.ru, a Sankt Petersburgh-based internet service provider. The data allegedly contains the personal details of 4 million of the company's customers, including full names, dates of birth, phone numbers, customer comments, and service-related information.
General tech and privacy
Apple satellite emergency service: Apple launched this week "Emergency SOS via Satellite," a new feature for its Health app that can allow phone owners to request emergency services via satellite whenever they are outside WiFi or cellular coverage. The service is currently available in the US and Canada and will come to France, Germany, Ireland, and the UK in December. Instructions on how to set up the service are available here.
Twitter working on encrypted DMs: While almost everything else is falling apart at Twitter, the company appears to be working on adding support for encrypted DMs. Probably not the trustworthy feature Musk envisions when there are reports of foreign intelligence agents lurking inside your company.
Fringe groups love Musk's Twitter acquisition: A joint report from social media analysis app SMAT and New Zealand NGO Tohatoha found that news of Musk's formal Twitter acquisition has been met with great joy by various fringe and extremist groups in all of the internet's darkest corners.
"From this initial research we can see that racist, conspiracy-driven, anti-democratic groups are very actively discussing and excited about the news of Musk's takeover. [...] Whether this drives them off of the fringe platforms and back into the mainstream remains to be seen, however the mainstreaming and platforming of their malicious campaigns seems to be an inevitable result. That Gab, an extremist friendly platform run by a Christian theocratic ultranationalist infamously known for a wide variety of hate based views, is most fervently discussing the takeover is itself a kind of 'canary in the coalmine' for the issues to come."
Google and Microsoft services in French edu sector: As spotted by privacy expert Alexander Hanff this week, the French government has apparently told and warned educational institutions that the use of cloud products like Microsoft 365 and Google Workspace is technically forbidden across France because of their illegal data harvesting practices, which are not compliant with the GDPR. They're still used in some schools, though.
Ad-blocker apocalypse getting closer: After AdGuard published a limited version of its ad-blocker to comply with Chrome's new Manifest V3 extension design rules, AdBlock Plus did so as well this week, and it also complained about their ad-blockers extremely limited blocking capabilities. Crazy world we live in, where ad companies can neuter all ad-blockers in their browser without a formal government inquiry into its monopolistic behavior. Weird, eh?
CNIL fines Discord: France's CNIL data protection agency has fined Discord €800,000 for multiple GDPR infractions. These included keeping data more than necessary and having a password management policy that was not sufficiently strong, such as allowing six-characters-long passwords. CNIL said the company has since corrected its password policy, which now also includes basic brute-force detection on failed login attempts.
Meta fires employees: Meta has disciplined or fired dozens of employees and contractors who improperly accessed users' accounts for various reasons, including bribery, the WSJ reported. The firings come after an internal probe.
Government, politics, and policy
Russia's cyber forces underperformed: Speaking at the Aspen Cyber Summit, Mieke Eoyang, deputy assistant secretary of defense for cyber policy at the Department of Defense, said that Russian forces "underperformed expectations" in both the cyber and military space.
"Eoyang said some of that underperformance from the Russians could be tied to their underestimation of how long it takes to prepare for cyber operations and cyberattacks prior to a war."
Shut up, Russia: The Russian government has issued a spunky statement in regards to Australia identifying the Medibank hackers as located in Russia before contacting Russian law enforcement first. For a country that rarely does anything to curb its ginormous cybercrime ecosystem, Russian government officials sure have a lot to be mouthy about.


Universal health code in China: The Chinese government is planning to digitize the health records of its citizens and assign them a "universal health code" by 2025. The move has sparked fear among Chinese activists that the digitized health records could be used to bar citizens' access to certain services, jobs, or benefits based on their medical history, genetic information, or family history.
Qatar WC app warning: Officials for the Dutch, German, French, and Norwegian governments have warned against installing Qatar's World Cup apps Ehteraz and Hayya, citing several privacy and security concerns. German officials specifically recommend that in cases where the use of any of the apps is necessary, that users install the apps on a separate phone that does not store any of their personal data and then wiping the device after use during the World Cup events.
US-China cyber report: In its yearly report to Congress, the US-China Economic and Security Review Commission has found that "China has developed formidable offensive cyber capabilities over the past decade and is now a world leader in vulnerability exploitation." The commission also found that China "enjoys an asymmetric advantage" over the US in cyberspace due to its unwillingness to follow norms for responsible state behavior. The report found that China selectively applies and promotes norms to benefit its authoritarian view of cyberspace and is "creating new organizations to supplant existing cyber governance mechanisms in line with its vision for the internet."
Sponsor section
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
Cybercrime and threat intel
Popopret pleads guilty: Daniel Kaye, known for his hacker monikers of BestBuy and PopoPret, has pleaded guilty to running The Real Deal dark web marketplace after being arraigned in a US court earlier this month. Not only that, but Kaye was also already sentenced to time served and one year of supervised release. As DataBreaches.net suggests, Kaye appears to have reached some sort of deal with US investigators. The deal might be related to a US investigation into a notorious hacking group known as TheDarkOverlord, which used to sell the data of hacked companies on Kaye's marketplace.
Chinese hacker: Chinese authorities have sentenced a hacker named Li Moumou to 10 years and six months in prison for stealing 384 Ether coins, worth $110,000 at the time of the theft in early 2018, from the wallet of a local man. Authorities said Moumou obtained the funds using a trojan planted on the victim's device and that after his arrest, they managed to return the stolen funds to the victim.
Malware dev sentenced in Russia: Russian authorities have sentenced a man named Sosin P.V. to two years in prison for developing a web-based penetration testing tool named WASP 1.0. According to a report, the tool combined software like the Apache HTTP server and the Arachni Scanner, together with SQLmap, a tool considered illegal in Russia. Sosin has filed an appeal which will be heard later this month. He has told local news outlets he is not expecting the sentence to be overturned.
Two scammers sentenced: George Ugochukwu Egwumba, 47, and Princewell Arinze Duru, 33, both from California, were sentenced this week to 132 and 81 months in federal prison for their involvement in BEC, romance, and elder fraud scam operations. According to the DOJ, the men worked as middlemen with a Nigerian cybercrime gang, helping the group launder stolen funds.
"The conspiracy involved the laundering of at least $6 million in fraudulently obtained funds and the attempted theft of at least an additional $40 million."
Google wins Glupteba lawsuit: A New York court has ruled in favor of Google in the company's lawsuit against Dmitry Starovikov and Alexander Filippov, the operators of the Glupteba adware botnet. Google sued Glupteba's creators last December, shortly after it also disrupted their botnet. According to court documents, the judge issued a default judgment in the case and ordered the two accused, along with their US lawyer, to cover Google's legal fees in the case. The judge concluded that the defendants were misleading the court and litigating in bad faith. The judge said the defense abused the court discovery rules to obtain information from Google about how the company was blocking their botnet, and also proposed a settlement where they would be paid $1 million each for additional information about their botnet, an offer that Google refused and subsequently reported the two to law enforcement for extortion. [Additional coverage in SecurityWeek]
Elastic's threat landscape report: Elastic's security team its 2022 Global Threat Report. Some of the company's main findings are below:
CobaltStrike was the most popular malicious binary or payload for Windows endpoints, with ~35% of all detections.
On macOS, almost 48% of detections were linked to the MacKeeper binary, considered by many security firms as adware.
On Linux, Meterpreter was the most common malicious payload, with almost 14% of all detections, followed closely by Gafgyt (12%) and Mirai (10%).
Amazon RDS exposure: A Mitiga report claims that there are hundreds of Amazon RDS servers exposed online each month. Amazon RDS, or the Amazon Relational Database Service, is a cloud service from Amazon that provides access to various hosted relational database engines like MySQL, PostgreSQL, MariaDB, Oracle, MSSQL, and others.
Record number of DDoS attacks: Security firm NCC Group said that the month of October saw the highest number of DDoS attacks this year, with a 14% increase from September, to 2,090 recorded attacks. Per Matt Hull, Global Head of Threat Intelligence at NCC Group, "this shift is even more notable this month as overall ransomware attacks decreased."
Twitter accounts for sale on the dark web: With Twitter slowly becoming a swamp of right-wing, porn, and cryptocurrency spam, threat intel company Cybersixgill says there's a flourishing underground market for Twitter bots, spam tools, and account hacking services that may play a big role in the platform's future development and direction.
"Now, new data acquired by Cybersixgill appears to confirm that a significant portion of inauthentic Twitter accounts may have been built with tools and services found on the deep and dark web. And the problem is getting worse."
Malware on npm: Malware has been found in three npm libraries named geocomponents, babel-preset-geocaching, and geocaching-express-account-middleware.
WatchDog: Cado Security has a report out on the WatchDog crypto-ming botnet, which has seen a resurgence over the summer. Previous reports on this botnet are also available via Trend Micro, Lacework, and AquaSec. In a 2021 report, Palo Alto Networks called WatchDog one of the oldest crypto-mining gangs in operation today.
Emotet's return: Proofpoint has a detailed write-up of the recent Emotet spam campaigns after the botnet came back from its most recent hiatus, with the botnet ceasing all activity between June and November 2022. As Proofpoint's Sherrod DeGrippo told RiskyBizNews in our latest podcast, this comeback involved lots of international lures targeting users using phishing emails in different languages, such as Greek, German, French, Italian, Japanese, Portuguese, and Spanish.
Malware technical reports
RedLine Stealer: Indian cybersecurity company CloudSEK has a technical report on RedLine Stealer, a very common Malware-as-a-Service operation available under different pricing models.
Typhon Reborn: PAN's Unit42 has analyzed Typhon Reborn, a newer version of the Typhon Stealer, currently advertised in underground Telegram channels.
"These new features include block listed usernames and countries, new message clients and a crypto-extension stealer for Google Chrome and Microsoft Edge. The author also removed a few existing features, including the keylogging ability as well as the clipboard stealing and crypto mining features."
HZ Rat: German cybersecurity company DCSO has a report out on HZ RAT, a lesser-known trojan that hosts many of its command and control servers in China.
LodaRAT: Two years after its initial analysis of the Loda remote access trojan, Cisco Talos published a new report detailing the malware's recent evolution.
"Changes in these LodaRAT variants include new functionality allowing proliferation to attached removable storage, a new string encoding algorithm and the removal of 'dead' functions."
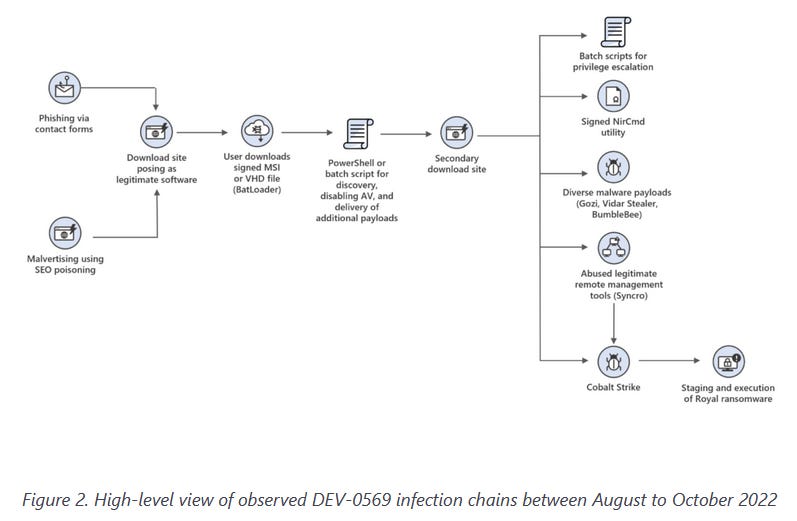
DEV-0569 and Royal ransomware: Microsoft has published a report on a threat actor it tracks as DEV-0569, which the company says it saw deploying the Royal ransomware on high-value systems it was infecting via malvertising and contact form phishing schemes.
Dagon Locker ransomware: A new ransomware strain named Dagon Locker has been spotted being distributed in the wild. According to AhnLab and Symantec researchers, Dagon features strong code similarities to the MountLocker and Quantum ransomware strains. Currently, the Dagon crew does not run a leak site to shame victims, nor does it delete volume shadow copies, which may allow some of the encrypted data to be recovered.
ARCrypter ransomware: BlackBerry's security team has a report on the new ARCrypter ransomware, the strain used in attacks on the Colombian National Food and Drug Surveillance Institute last month and against the Chilean National Consumer Service in August.
Hive ransomware: CISA, the FBI, and the HHS have issued a joint report on the Hive ransomware.
"As of November 2022, Hive ransomware actors have victimized over 1,300 companies worldwide, receiving approximately US$100 million in ransom payments, according to FBI information."
RapperBot: Fortinet researchers say that a botnet called RapperBot, which they first spotted back in August, launching brute-force attacks in an attempt to expand their numbers, has been recently repurposed to launch DDoS attacks. According to current data, these attacks appear to target gaming servers and are a continuation of a similar campaign observed earlier in the year.
Vulnerabilities and bug bounty
F5 Big-IP vulnerabilities: Rapid7's Ron Bowes published details on CVE-2022-41622 and CVE-2022-41800, two vulnerabilities in the Big-IP load balancer, patched this week by F5.
Zendesk vulnerabilities: Varonis researchers have published details on an SQL injection vulnerability in Zendesk Explore, an analytics and reporting service for the Zendesk CRM platform.
"Zendesk started working on a fix the same day it was reported. The company fixed multiple bugs in less than one workweek with zero customer action required."
Infosec industry
New tool—Orpheus: TrustedSec has open-sourced a new tool named Orpheus that can bypass current Kerberoasting protections.
Jamf acquires ZecOps: Cybersecurity firm Jamf has acquired ZecOps, a small security shop specializing in iOS security.
How to follow infosec topics and figures on Mastodon: Dragos' Lesley Carhart has a simple tip on how to follow Mastodon users via RSS.
Default format is: [server]/users/[username].rss
Example (for Lesley's feed): https://infosec.exchange/users/hacks4pancakes.rss
Another example (for my feed): https://mastodon.social/users/campuscodi.rss
2022 Aspen Cyber Summit stream: A recorded live stream of the 2022 Aspen Cyber Summit, which took place this week, is available on YouTube and embedded below. A text summary of the hours-long event is available via The Record, as well.