Risky Biz News: Meta formally links pro-Western influence operation to US military
In other news: DraftKings users hacked for $300,000; new RobinBot DDoS botnet; Karakurt starts recruiting.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Meta's security team has formally confirmed the involvement of the US military in a pro-Western influence operation the social network took down this summer.
The company said it removed 39 Facebook accounts, 16 Facebook pages, and 26 Instagram accounts that tried to pose as locals in various countries.
The accounts posted content in different languages and across several countries as part of an influence operation meant to praise the anti-terrorism efforts of the US military and criticize China, Russia, and the Taliban.
"The people behind this activity posted primarily in Arabic, Farsi and Russian about news and current events, including terrorism concerns and praise of the US military, as well as content about the COVID-19 pandemic — some of which we removed for violating our misinformation policy. This operation also shared posts criticizing Iran, China and Russia, including Russia's invasion of Ukraine, China's treatment of the Uyghur people, Iran's influence in the Middle East, and the support of the Taliban regime in Afghanistan by Russia and China."
This is the same campaign that was first described at the end of August in a joint report from Graphika and the Stanford Internet Observatory—a joint report based on Meta and Twitter datasets the companies released in advance, and the campaign that was ridiculed for gaining almost zero engagement despite its years-long effort.
At the time, the two organizations formally linked the campaign to the Trans-Regional Web Initiative, a somewhat obscure DOD project launched 15 years ago and meant to create and run regional news websites to educate and inform local audiences.
While back in the 2000s, the project looked like another Radio Liberty initiative, it appears the project turned into your run-of-the-mill covert influence operation.
While Meta didn't specifically connect their findings to the Trans-Regional Web Initiative project, they did say that their "investigation found links to individuals associated with the US military" and that these individuals actively tried to conceal their identities and coordination.
This probably didn't help with the concealment thing:
"This network posted primarily during US business hours (EST) rather than during work hours in the countries they targeted."
While the Pentagon did not formally confirm the August report, the DOD did order a sweeping audit of its "information warfare" efforts, most likely not pleased with either the abysmal results they were getting or getting publicly doxxed and shamed. All of this is particularly interesting since WaPo also reported that Meta gave the DOD a small nudge about its easy-to-spot clandestine info-op back in 2020, telling them to knock it off before cracking down on the accounts two years later.
Breaches and hacks
DraftKings account hacks: Sports betting service DraftKings confirmed that hackers stole $300,000 from customer accounts. The company blamed the incident on users who reused (compromised) passwords for their accounts. However, online, several users said they used unique passwords, which might suggest that some users might have had their computers infected with malware that stole their DraftKing credentials.
Radio Free Asia breach: US news agency Radio Free Asia has disclosed a security breach that might have exposed the personal information of more than 3,700 of its employees. RFA said that a threat actor exploited a vulnerability in a service provider's systems to gain access to "a limited number of servers." The agency said it took down impacted servers and is now moving to a new email provider and changing passwords.
General tech and privacy
5G network security breaches: According to a survey commissioned by Nokia among 5G network operators, at least a third of all 50 respondents said they experienced eight or more security breaches over the past year. More in the survey itself or in CybersecurityDive's coverage.
AWS Nitro System: Amazon has published details about the security design of its AWS Nitro System [PDF], the underlying virtualization platform on which all modern EC2 instances run.
Far-right figures reinstated on Twitter: Cyberscoop reports on how Twitter (also recently known as $8chan) is silently unbanning all the crazy right-wing figures the former management spent years removing from its platform for abhorrent abuses. Similarly, WaPo reports that the team that hunted foreign influence operations was either fired or decided to quit after Musk took over the site. Probably why advertisers are running for the hills and not even looking back.
Meta improves privacy on children's accounts: Meta announced this week that it would apply default options with increased privacy settings for children under the age of 18/16 that register new accounts on its Facebook and Instagram platforms. In addition, the company said it was also developing new tools to stop the spread of self-generated intimate images online.
More Apple privacy drama: Security researchers Tommy Mysk and Talal Haj Bakry said they found that Apple's analytics service creates an identifier named "dsId" (Directory Services Identifier) that is unique for each user and tied to their iCloud account. The duo warns that because of this, Apple can track and identify users as they navigate the web and link them to their real-world identities. As MacRumors points out, the issue here is that Apple states on its privacy and legal page that no information from a device for analytics purposes can be traced back to any specific user.
Government, politics, and policy
Italy tracks and redirects entire ISP traffic: Italian police said they tracked and redirected the internet traffic from all internet service providers in order to identify people who subscribed to a pirate IPTV service. Cool, but maybe they can use the same "capability" next time to detect Italian systems connecting to known malware C2—and be actually useful to their citizens.
Rewards for Russian hacktivists: Dmitry Gusev, a deputy in the Russian Duma, has floated the idea of awarding Russian hacktivists state awards and military ranks as a way to thank them for attacks carried out across the world.
US State Department security audit: A security audit carried out in September 2022 found vulnerabilities in eight of nine domains managed by the US State Department "despite the Department's expenditure of substantial resources on information system security." [See OIG report/PDF or coverage in FCW]
CISA IRPF update: CISA has updated its Infrastructure Resilience Planning Framework (IRPF), released last year, with more information to better help state, local, tribal, and territorial (SLTT) planners protect infrastructure. Read or download the full IRPF v1.1 here/PDF.
"[IRPF] can be used to support capital improvement plans, hazard mitigation plans, and other planning documents, as well as funding requests. Today's update adds important new resources and tools to better support partners as they face an evolving threat environment."
NSO's Supreme Court case: In an update on the NSO-vs-Facebook lawsuit and NSO's attempt to have the case heard at the US Supreme Court to overturn an initial ruling, the US Supreme Court has asked the US Department to weigh in. According to a document [PDF] filed this week, the DOJ told the Supreme Court that it sees no reason for NSO Group to receive state-level immunity for how their tools were used to hack into personal WhatsApp accounts and recommended the Supreme Court not to hear their case. (via John Scott-Railton)
"Whether or not common-law immunity for an entity acting as the agent of a foreign state might be appropriate in some circumstances, NSO plainly is not entitled to immunity here. The State Department has not filed a suggestion of immunity in this case. There is no established practice—or even a single prior instance—of the State Department suggesting an immunity for a private entity acting as an agent of a foreign state. And no foreign state has supported NSO's claim to immunity; indeed, NSO has not even identified the states for which it claims to have acted as an agent. Nor does the court of appeals' decision otherwise warrant review. It does not conflict with any decision of this Court. The question presented has not divided the courts of appeals—indeed, it has seldom arisen at all. And this unusual case would be a poor vehicle for considering that question in any event. The petition for a writ of certiorari should be denied."
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Pig-butchering crackdown: The US Department of Justice said it seized seven websites that were being used to trick victims as part of an online scam scheme known as "pig butchering." Pig butchering schemes are a combination of romance, investment, and cryptocurrency scams, where victims are approached via dating sites and then social-engineered into making various investment or cryptocurrency transactions. Pig butchering scams originated in Southeast Asia—where they have deep ties to criminal cartels—and are spreading globally. The DOJ said the seized domains impersonated the Singapore International Monetary Exchange and were used to steal more than $10 million from at least five victims.
Ten BEC scammers charged: The US DOJ has charged ten suspects across the US for stealing more than $11.1 million from state Medicaid programs and private health insurers. Officials said the group used BEC schemes where they posed as business partners to divert money from their victims' bank accounts into accounts operated by their money mules. The DOJ said that five state Medicaid programs, two Medicare Administrative Contractors, and two private health insurers fell victim and lost money to the group.
Lurk leader has sentenced reduced: A Moscow court has reduced the prison sentence of Konstantin Kozlovsky, the leader of the Lurk cybercrime group, to 13 years and four months in prison. Kozlovsky had his sentence reduced by eight months from the initial 14 years in prison he received earlier this year.
Russian cybercrime investigation: Russian law enforcement has seized two Bitcoin wallets from a law enforcement official who was investigating the Infraud cybercrime organization. According to court documents, the wallets held more than 1,000 bitcoin and are believed to have been bribes the investigator received from the gang's lawyer.
REvil investigation stalls: Kommersant reports that the criminal case against members of the REvil gang detained by Russian officials earlier this year has stalled after US investigators broke communications and cooperation with their Russian counterparts following Russia's invasion of Ukraine.
Freebie Bots: Kasada researchers said they identified a new type of automated bot attack named Freebie Bots that operates by scanning retail websites for mispriced goods and services and purchasing them at scale before the error is fixed.
"Kasada research has found more than 250 retail companies recently being targeted by Freebie Bots, with over 7 million messages being sent monthly in freebie communities. Members within one popular freebie community used Freebie Bots to purchase nearly 100,000 products in a single month, at a combined retail value of $3.4 million. Kasada's research reveals that the total cost of the goods for Freebie Bot users was only $882, helping some individuals to realize a monthly profit of over $100,000."
2FA-bypass phishing campaign: PIXM researchers said they are tracking a sophisticated phishing campaign that targets users of cryptocurrency services and wallets like Coinbase, Metamask, KuCoin, and Crypto.com. Researchers said the phishing sites where users are being lured include the ability to intercept 2FA tokens, allowing the attackers to access secure accounts. In addition, the attackers will also use an in-browser chat window to initiate a remote desktop session on the victim's device (usually via TeamViewer), approve their own device as valid to access the user's account, and then drain cryptocurrency from their wallet.
Luna Moth: Unit42 researchers have a report out on Luna Moth (aka Silent Ransom Group), a threat actor that has been engaging in callback phishing campaigns over the past months that have targeted several industry verticals. The group's operations were also previously covered by Sygnia researchers.
"Callback phishing, also referred to as telephone-oriented attack delivery (TOAD), is a social engineering attack that requires a threat actor to interact with the target to accomplish their objectives. This attack style is more resource intensive, but less complex than script-based attacks, and it tends to have a much higher success rate."
OMG!OMG! Market: Threat intel outfit DarkOwl has a profile out on OMG!OMG! Market, a Russia-based dark web market that appears to have taken one of the top spots as the go-to destination after the Hydra seizure earlier this year. The market is primarily known for its drug-trading ecosystem.
Yanluowang leak analysis: Trellix researchers have published a deep dive into the leak of internal chats from the Yanluowang ransomware gang, which we covered earlier this month. Analysis of more than 2,7k messages reveals ties between members of the Yanluowang gang and members of other ransomware operations such as Babuk, Conti, and HelloKitty.
Karakrut starts recruiting: Karakurt, a group with ties to the former Conti gang [1, 2, 3] and known for its hack-and-leak extortion operations, announced this week they are recruiting people to breach networks, malware coders, social engineers, and personnel to extort companies for payments. (via CyberKnow)
Malware technical reports
Hagga: Yoroi founder and CEO Marco Ramilli published a report on recent developments in the operations of Hagga, a threat actor known for distributing infostealer trojans. Recent changes include the adoption of Fsociety Tools, an open-source penetration testing framework.
ViperSoftX: Avast has analyzed recent changes in the operations of ViperSoftX, an infostealer that has been seen in the wild since 2019. Avast says that in recent attacks, the ViperSoftX operators have switched to using their malware to install an extension for Chromium-based browsers in order to execute a MitM attack when users visit cryptocurrency platforms to steal credentials and swap wallet addresses with one they operate.
Nighthawk C2 framework: Proofpoint has an analysis on Nighthawk, an up-and-coming red-team tool from MDSec. Proofpoint said it hadn't seen Nighthawk abused by threat actors, but it can see its appeal as a possible C&C framework for malware operations.
SocGolish: The same Proofpoint security team has linked the SocGolish malware operation to the TA569 threat actor. SocGolish is malware deployed to users via malicious JavaScript code injected on hacked websites. Initial infections with SocGolish have been previously linked to the deployment of infostealers, RATs, and even ransomware, as of recently.
RobinBot: QiAnXin researchers said they spotted a new IoT malware strain named RobinBot that has been used to carry out DDoS attacks. Researchers said the malware uses code borrowed from the Mirai and Gafgyt families, supports multiple DDoS attack methods, and can spread via both Telnet password brute-forcing and vulnerability exploitation.
Aurora: Sekoia has an analysis of Aurora, a former botnet now turned infostealer advertised on underground hacking forums for as low as $250/month.
RansomExx: IBM X-Force researchers said they discovered a new version of the RansomExx ransomware that was rewritten in the Rust programming language. They named this new version RansomExx2 but noted that most of its functionality is similar to its C++ predecessor. RansomExx now joins the ranks of BlackCat, Hive, and Zeon—other ransomware strains also written in Rust.
SharkBot: Antivirus maker Bitdefender said it identified four Android apps on the official Play Store acting as downloaders for the SharkBot banking trojan. The apps were file managers but also contained malicious code to help deploy malware on a user's device after their Play Store installation.
Raspberry Robin: The Sophos X-Ops team has a thread and IOCs on recent Raspberry Robin attacks.
Tofsee: The Tofsee spam botnet is still alive, apparently, and doing very well [PDF].
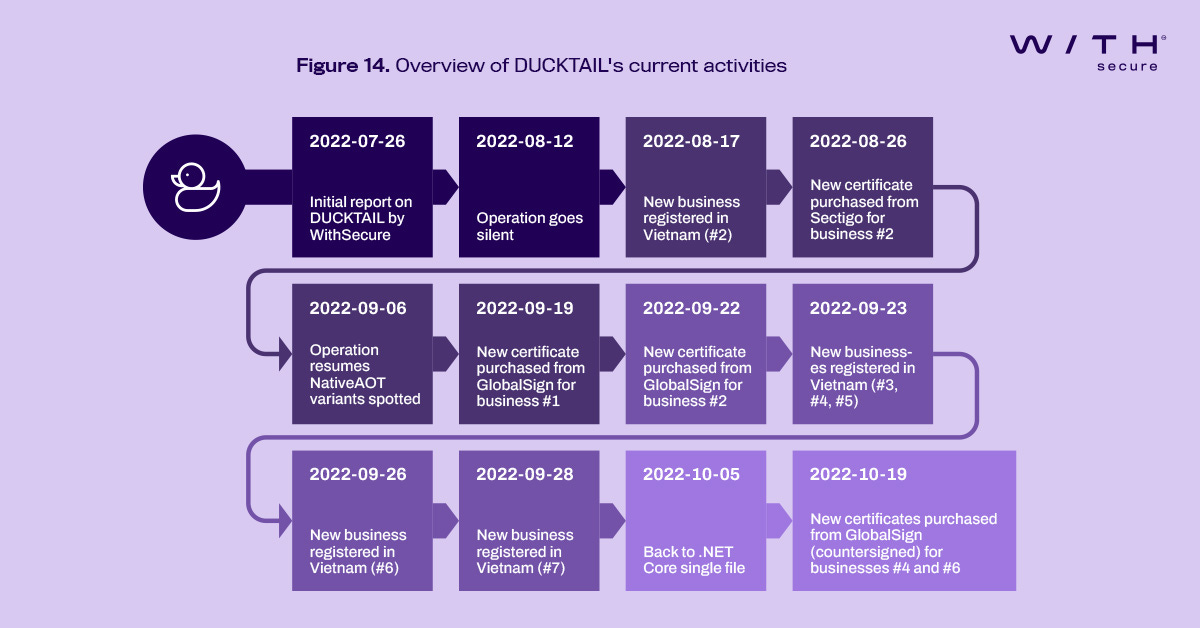
DUCKTAIL: WithSecure says the DUCKTAIL malware operation has returned with new attacks after the company exposed its operations earlier this summer in July. The malware, believed to be operated from Vietnam, is known for targeting the Facebook profiles of people from the digital marketing and advertisement space with the primary goal of hijacking their Ads and Business accounts. See WithSecure's technical report here/PDF.
APTs and cyber-espionage
Claimloader: The LAC threat analysis team has a report out on a recent spear-phishing operation carried out by the Mustang Panda APT, which deployed the Claimloader trojan on infected systems. Claimloader appears to be a variation of the malware Cisco Talos first spotted and documented back in May.
Boa server vulnerability: Earlier this year, Recorded Future said that a Chinese APT leveraged a vulnerability in an IoT device to gain access to an Indian electrical grid operator. In a report this week, Microsoft said identified the entry point for that attack as Boa, a tiny web server component discontinued in 2005 but still widely used across the IoT and ICS space.
Konni: Chinese security firm Anheng Hunting Labs has published a report on recent operations of the Konni North Korean APT, attacks that targeted entities in Eastern Europe and Northeast Asia throughout 2022.
Vulnerabilities and bug bounty
AWS vulnerability: DataDog's Nick Frichette has disclosed a vulnerability in the AWS AppSync service that could have been exploited to break tenant barriers and access other customers' resources. Amazon has rolled out a fix this week and says that no customer has been affected by this issue.
CVE-2022-41924: Emily Trau has a detailed write-up on remote code execution and DNS rebinding vulnerabilities in the Tailscale Windows VPN client. According to Trau, a threat actor can exploit the vulnerabilities by luring users to a malicious website. Vendor updates are available.
Infosec industry
Black Friday deals: Aussie security researcher Mike Monnik has compiled a list with some of the upcoming cybersecurity-themed Black Friday and Cyber Monday deals.
CISA on Mastodon: After a fake account was spotted for CISA Director Jen Easterly on Mastodon, CISA now has an official account on the platform.
LABScon 2022 videos: Talks from the LABScon 2022 security conference, which took place back in September, are available on YouTube. RiskyBizNews was told more videos will be uploaded in the coming days/weeks, so keep an eye on the playlist.
IRISSCON 2022 videos: Talks from the IRISSCON 2022 security conference, which took place earlier this month, are available on YouTube.