Risky Biz News: Microsoft and Fortra go after cracked Cobalt Strike versions
In other news: EU prosecutors to investigate Predatorgate scandal; Samsung employees upload proprietary code to ChatGPT; new car hacking technique exploited in the wild.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
NOTE: There will be no Risky Business newsletters and podcasts next week. We're all taking some time off.
Microsoft's legal team has obtained a court order that will allow it to have web and internet service providers take down infrastructure hosting pirated (cracked) versions of the Cobalt Strike framework.
Microsoft has worked together with the US Health Information Sharing and Analysis Center (Health-ISAC) and Fortra, the company that owns Cobalt Strike.
Developed in 2012, Cobalt Strike has become one of today's most popular security tools. It is widely used by red teams as a post-exploitation and adversary emulation toolkit, allowing them to orchestrate intrusions into corporate networks during pre-approved penetration tests.
The tool's advanced stealth and post-exploitation features also caught the eye of threat actors. For more than half a decade, threat actors have cracked Cobalt Strike's licensing protection and have been using so-called "cracked" versions of the software, typically to host command and control servers for their malware.
Today, cracked versions of the Cobalt Strike framework have been linked to APT cyber-espionage operations, ransomware attacks, and run-of-the-mill malware alike.
Microsoft told RiskyBizNews that its Defender security platform has detected around 1.5 million infected computers communicating with cracked Cobalt Strike servers over the past two years.
A 2020 Recorded Future report found that more than 1,400 malware C&C servers were using Cobalt Strike as their backend at the time. A Censys search currently returns ~540 Cobalt Strike servers hosted in the wild.
Microsoft, together with Fortra and Health-ISAC, say they now plan to use the recently-obtained court order to "notify relevant internet service providers (ISPs) and computer emergency readiness teams (CERTs)" and have them assist in taking cracked Cobalt Strike servers offline.
They hope this will sever connections between criminal operations and infected computers.
The court documents center around racketeering (RICO) and DMCA as the legal ground to have servers taken down.
Microsoft says its operation is still in progress and can't provide exact figures for Cobalt Strike servers that have been taken down so far.
Breaches and hacks
ACRO goes down: After two and a half months of denials, the UK's Criminal Records Office (ACRO) has finally confirmed it suffered a cyberattack that crippled its internal systems. The incident took place earlier this year, on January 17. The agency has not revealed any details, but security researchers say the agency has been hit and is trying to hide a ransomware attack. The incident has impacted UK citizens trying to gain access to their criminal records and those looking to travel or work abroad. [Additional coverage in The Evening Standard]
Samsung ChatGPT leaks: Samsung has warned employees against using ChatGPT in their daily work. The warning comes after Samsung's semiconductor division found three instances where employees uploaded sensitive information to the ChatGPT service while trying to fix errors in Samsung's proprietary source code. Data uploaded to ChatGPT includes internal documents and code meant to identify defective chips. Samsung now limits the length of questions submitted to ChatGPT to 1024 bytes while the company develops its own internal ChatGPT-like AI service for internal use. [South Korean/English coverage]
Sentiment crypto-heist: The Sentiment DeFi service was hacked for $1 million after a hacker launched a flash-loan attack against the platform. Sentiment says it fixed the vulnerability exploited in the attack and covered any of its users' losses.
General tech and privacy
Firefox Monitor update: Mozilla has rolled out a new version of its Firefox Monitor data breach monitoring and alerting service. The service now also has a dedicated website.
Metamask update: The Metamask cryptocurrency wallet has rolled out a new feature that uses OpenSea and Blockaid's lists of known scammers to show alerts to users before sending or signing a transaction to a known malicious entity.
Some Samsung phones reach security EoL: Samsung's line of 2019 smartphones has formally reached end-of-life, and devices have been cut off from security updates. March 2023 was the last security patch level for devices such as the Galaxy S10, Galaxy S10+, and Galaxy S10e. [Additional coverage in 9to5Google]
Google restricts loan apps data access: Google has restricted the amount of personal data loan apps can gather from Android users. The new policy entered into effect on April 1 last week. According to the new rules, loan apps can no longer access photos and user contacts. The move comes after reports that some loan app makers engaged in predatory behavior, such as harassing borrowers and threatening to expose their private communications and photos unless they paid their loans or agreed to higher interest rates.
Android apps to let you delete your account: Google announced that all Android apps that allow users to create accounts will also have to allow users to delete their accounts and any associated data. App makers must honor requests to delete accounts either through the app or through a web dashboard—in case users don't want to reinstall an app. The new requirement will enter into effect in early 2024.
Free Meta opt-out tool: Consumer protection group noyb has released a free tool to let users opt out of Meta's online tracking. noyb explains here how Meta has been moving from one unlawful data collection practice to the next.
Another ChatGPT investigation: Canada's privacy watchdog has launched an official investigation into OpenAI's ChatGPT service. Officials say they launched the investigation after a complaint the service was non-consensually collecting personal data. The move comes after the Italian Data Protection Authority also issued a temporary ban on ChatGPT earlier this week as the agency investigates a possible breach of GDPR legislation.
Government, politics, and policy
Mandatory RPKI in the Netherlands: The Dutch government has mandated that all government servers must use the RPKI standard by the end of 2024. Standing for "Resource Public Key Infrastructure," the RPKI standard is a public key infrastructure framework meant to cryptographically sign BPG routes and help prevent BGP leaks. Previously, the Dutch government has also enforced other internet security protocols across its IT networks, such as IPv6 (2021), STARTTLS and DANE (2019), HTTPS and HSTS (2018), and TLS (2017).
Greenland cyber threats: The Danish Centre for Cyber Security (CFCS) has published a cyber threat assessment for its Greenland territory. Officials rate the threat of cybercrime and cyber-espionage as VERY HIGH, while cyber activism and destructive attacks as LOW.
Predatorgate investigation: The EU's Public Prosecutor's Office has started a formal investigation into the Greek's government supposed use of the Predator spyware to wiretap the communications of political rivals, journalists, and members of its judiciary branch. According to Euractiv, the EEPO appears to have started an investigation after receiving a complaint from a Greek member of the European Parliament and after receiving "specific information" from Greek reporters investigating the scandal, dubbed Predatorgate in Athens. In addition to the wiretapping allegations, the EEPO also appears to be looking into the "enormous tax evasion" committed by the companies involved in Predatorgate.
IRS ECM review: The US Treasury Inspector General says that the IRS Enterprise Case Management (ECM) does not meet all cloud security requirements. Issues found by a security audit include:
79% of user accounts were not timely deactivated or disabled, as required.
The IRS did not timely remediate 24 high- and two medium-risk vulnerabilities for the ECM system.
ECM cloud servers lacked required malicious code protection.
The IRS also fixed half of the security issues it found during a previous 2021 security audit.
DOE cloud security review: A similar audit conducted by the Office of the Inspector General of cloud systems used by the US Department of Energy found its own set of issues:
Two locations utilized cloud-based systems without appropriate approval. Additionally, three locations had not conducted complete system authorizations for cloud systems, to include identifying, implementing, and assessing security controls for which the Department was responsible.
Three locations had not conducted required continuous security monitoring of cloud services that were authorized through the Federal Risk and Authorization Management Program.
Significant amounts of information were stored in unapproved cloud storage accounts.
The Department did not maintain an accurate inventory of cloud-based systems used across the enterprise, and programs and sites generally used more systems than were reported to the Office of the Chief Information Officer.
First Cyber Academy class: The inaugural class of New York City's Cyber Academy graduated this week. The academy was established last year by the New York City Cyber Command and featured coursework provided by Google's Mandiant division. The 21 graduates in the first class each represented a different city agency, where they will serve as cybersecurity liaisons going forward. [Additional coverage in StateScoop]
IRS wants netflow data: The US Internal Revenue Service wants to purchase internet netflow from Team Cymru, a known contractor for the FBI and the US military. [Additional coverage in Motherboard]
Risky Business Demo
In this Risky Business demo, Tines CEO and co-founder Eoin Hinchy shows off the Tines no-code automation platform to host Patrick Gray.
Cybercrime and threat intel
Genesis arrests: One-hundred-nineteen suspects have been detained by law enforcement agencies across 17 countries for their involvement in an underground market specialized in the sale of login credentials and authentication cookies. Named Genesis, the market was taken down earlier this week. According to the US DOJ, Europol, the UK NCA, and Dutch Police, the detained suspects were users who sold or bought data on the site. Genesis administrators are still at large and promised to set up a new website. Besides taking down the portal, authorities also carried out 208 property searchers and 97 knock-and-talk measures. Dutch Police has launched a website to let users see if their data was traded on Genesis over the past five years. The same data is also available via the Have I Been Pwned service, courtesy of the FBI. Authorities say that since 2018, Genesis offered for sale more than 80 million account access credentials stolen from 1.5 million computers from across the world.
Estonian national charged: US authorities have charged an Estonian national for evading sanctions and trying to acquire US-made electronics on behalf of the Russian government and military. In addition, the suspect, identified as Andrey Shevlyakov, also attempted to acquire computer hacking tools. US officials say Shevlyakov used one of his front companies in May 2020 in a failed attempt to acquire a license for Metasploit Pro, a tool commonly typically used in offensive and red-team operations.
Cyber insurance and the ransom ecosystem: UK non-profit RUSI has published a report on how the cyber insurance industry could play a role in slowing down the current ransomware and data extortion ecosystem.
"The cyber insurance market must prioritize discovering and disseminating best practice standards for preventing, containing and resolving cybercrime that serve both the market and the public interest, and creating institutions to enforce these broadly (perhaps with the aid of governments)."
Hacked website report: More than half of the hacked websites investigated by GoDaddy's Sucuri team last year were running outdated CMS applications at the time of their infection. Sucuri says it removed almost 1.2 million backdoors from infected websites last year. WordPress was the most hacked CMS last year, but this was because WordPress dominates the CMS market. Sucuri says it found malicious admin accounts in a third of the WordPress sites it investigated.
Joker DPR: Recorded Future says that pro-Russian hacktivist group named Joker DPR is amplifying Russian information operations in Ukraine, "possibly with the coordination of the Russian state." The group has been active since 2019 and is one of the few pro-Kremlin hacktivist groups that have been active since before Russia's invasion of Ukraine. Its main activity has been to discredit the Ukrainian government and military. To date, Joker's DPR's only claim to fame is its alleged hack of DELTA, a battlefield management platform developed by the Ukrainian Armed Forces.
Killnet: The US Department of Health and Human Services has published a report [PDF] on the Killnet pro-Kremlin hacktivist group.
DDoS attacks on Israeli targets: Anonymous Sudan has conducted a series of DDoS attacks this week against Israeli targets, such as government sites, universities, news portals, and private companies. The attacks are most likely the first wave of the yearly OpIsrael (April 7) operations. Radware has a list of hacking groups participating in this year's operation and says some defacements have already taken place.
Telegram phishing market: Kaspersky has an analysis of Telegram's increasing role in the phishing market, with the instant messaging service acting as a host for many "shops" but also phishing panel backends.
Dark web marketplace ecosystem: Threat intel outfit published a report with the current main dark web marketplaces, one year after law enforcement took down Hydra. The big five are now Mega, Blacksprut, Solaris, Kraken, and OMG!OMG! Market.
STYX Marketplace: Resecurity researchers have spotted a new dark web marketplace named STYX. Launched in January this year, the marketplace provides an assortment of illicit services ranging from data dumps to cash-out services and from DDoS attacks to stolen credentials. Despite launching only three months ago, STYX has already gained a large following, primarily because of its wide range of services available on its market.
Malware technical reports
Genesis Market malware analysis: Dutch security firm Sector7, which assisted the Dutch police investigation, has put out a report on the various malware strains through which credentials were collected and then put up for sale on Genesis. Observed malware botnets selling data on Genesis included AZORult, GoodKit, Arkei, and DanaBot, among others. The analysis also covers the Chrome extension through which buyers could use their Genesis-bought credentials and cookies. A similar report is also available from Trellix.
AresLoader: OALabs has published IOCs for the new AresLoader malware, a new malware downloader that has been advertised on some underground forums earlier this year[1, 2].
Emotet: Trustwave has a report on Emotet's recent OneNote campaigns.
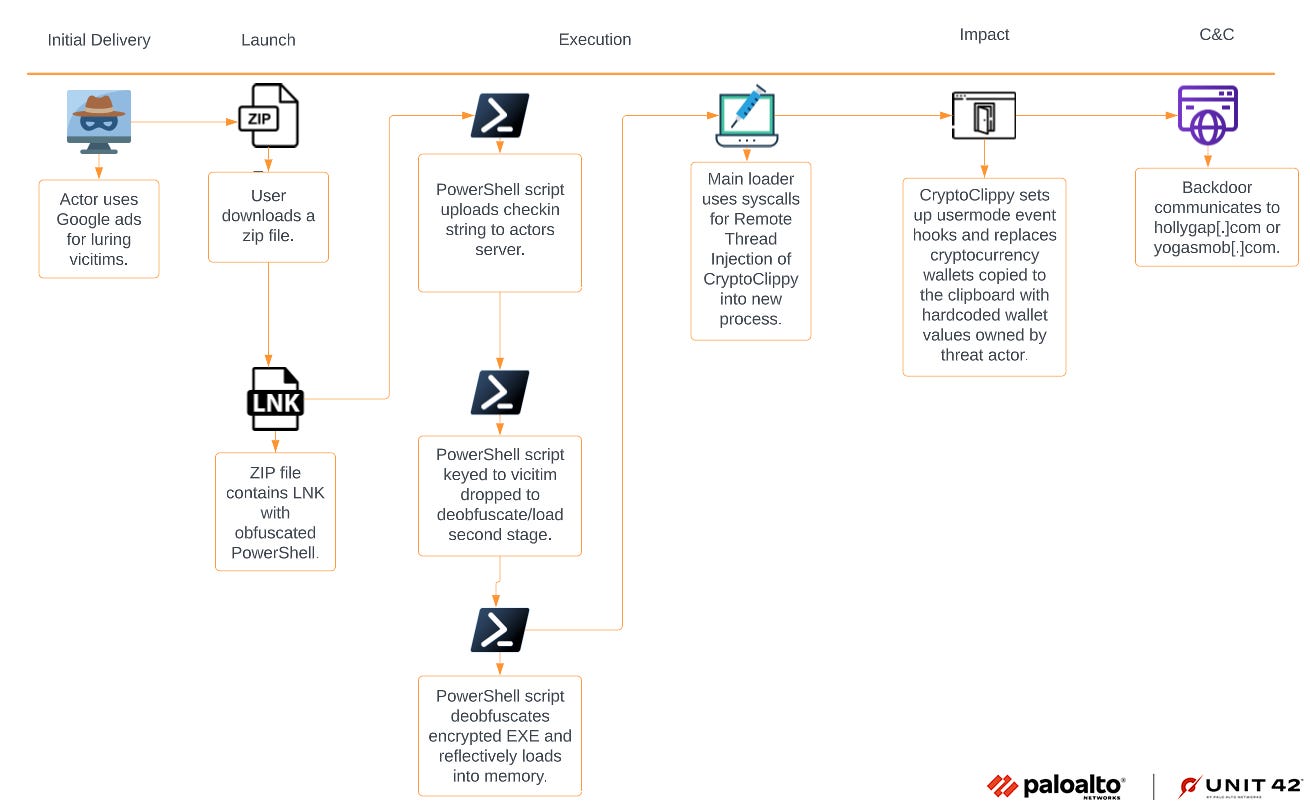
CryptoClippy: PAN's Unit42 division has discovered a malware campaign targeting Portuguese speakers. The payload in this operation is a new malware strain named CryptoClippy. Researchers say the malware operates as a clipboard hijacker that monitors the victim's clipboard for signs that a cryptocurrency wallet address is being copied, which it then replaces with one owned by attackers.
Sponsor Section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
VulkanFiles: Some of the official documents behind the VulkanFiles leak are now public.
ARCHIPELAGO (APT43): Google's TAG security team has published a report on a North Korean threat actor named ARCHIPELAGO. Google says the ARCHIPELAGO group is a subset of APT43, a group its Mandiant division covered in a report last week. Active since 2012, Google says ARCHIPELAGO is primarily targets individuals with expertise in North Korean policy issues such as sanctions, human rights, and non-proliferation issues. Its preferred mode of operation is highly advanced social engineering attacks where operators establish connections with their victims before luring them to phishing sites and stealing their credentials. In many cases, ARCHIPELAGO poses as journalists when approaching their targets.
Vulnerabilities and bug bounty
HP firmware downgrade: In somewhat of a rare ocurrence, HP has told customers to downgrade the firmware of some laser printers to earlier versions to prevent threat actors from exploiting a vulnerability it did not yet get to patch. The vulnerability—tracked as CVE-2023-1707—is an information disclosure when IPsec is enabled. The bug is rated 9.1/10, and HP says it expects to release a patch in the coming 90 days.
ThingsBoard bugs: IBM X-Force's team has discovered a vulnerability (CVE-2023-26462) in ThingsBoard, a data management and aggregation platform used by IoT device makers. The vulnerability can allow a remote attacker to gain elevated privileges because hard-coded service credentials are stored in an insecure format.
CyberGhostVPN vulnerabilities: A security researcher known as mmmds has published a report on several vulnerabilities in the CyberGhostVPN Linux client. The vulnerabilities allow MITM, RCE, and LPE attacks.
Pixel 6 vulnerability: GitHub's security team has published a write-up on a patching issue that left Google Pixel 6 smartphones vulnerable to a vulnerability that was patched five months before.
Tesla bug report: Security researcher Evan Connelly has a report on how he was able to take over internal Tesla accounts.
Cisco security updates: Cisco has released 13 security updates for some of its products. Keep an eye on CVE-2023-20102.
New car hacking technique exploited in the wild: Security researchers have discovered that car thieves are using a new technique to hack vehicles, bypass the keyless entry system, then open doors and start their engines. Named "CAN Injection," this technique appears to have been used in the wild for at least a year. It relies on thieves pulling apart headlights to reach internal cables and connect a special device that hacks the car's ECU. Short for Electronic Control Unit, this is a car's internal component that typically runs the smart keyless system. The attack works by sending specially crafted CAN messages that tell the ECU an attacker's access key is valid. Researchers say they've tracked down underground sites selling access to these kinds of hacking devices for up to €5,000. Sellers claim their devices can hack cars from Jeep, Maserati, Honda, Renault, Jaguar, Fiat, Peugeot, Nissan, Ford, BMW, Volkswagen, Chrysler, Cadillac, GMC, and Toyota. A CCTV recording showing one of these hack-and-steal incidents is below:
Infosec industry
New tool—LOLDrivers: A team of security researchers have released a new project named LOLDrivers (Living Off The Land Drivers), a curated list of Windows drivers used by adversaries to bypass security controls and carry out attacks.
New tool—debugHunter: Security researcher Daniel Púa has released a Chrome extension named debugHunter that can discover hidden debugging parameters and uncover web application secrets.