Risky Biz News: New Bluetooth relay attack bypasses current defenses
In other news: South Korea indicts four North Korean hackers; US indicts Venezuelan cardiologist behind Thanos ransomware.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Sultan Qasim Khan, a senior security researcher for NCC Group, delivered some spectacular research on Monday when he published details about a new relay attack that works at a much deeper level of the Bluetooth Low Energy (BLE) protocol than previously known relay attack techniques and which can bypass all existing defenses.
Khan said his new attack could be used to bypass security systems that rely on users presenting a BLE device as an "authentication by proximity" mechanism. This includes devices such smart car key fobs, residential smart locks, building access control systems, and security solutions that rely on using a smartphone or a laptop's BLE sensor as an entry/authorization key.
These systems are vulnerable to "relay attacks" where a threat actor intercepts BLE signals from the legitimate device and passes them using relay equipment to the actual system, even if the original BLE device is nowhere near, effectively creating a clone.
This type of attack has been known for decades, and recent anti-relay protections have been developed to challenge BLE devices in a request-response communications model and then detect any extra latency added to BLE traffic when the attacker relays these challenges. If the latency is high, the BLE device is denied access, being classified as a potential threat.
Khan said that he developed a tool that works at the BLE link layer and which introduces a much smaller delay to existing communications, and that even works even if link encryption is enabled.
The NCC Group researcher said he verified his tool by launching successful BLE relay attacks against Tesla's Phone-as-a-Key system and Kevo smart locks, but that many other devices are almost certainly vulnerable as well.
Since last year, Khan has worked to notify affected vendors and the Bluetooth SIG team of his research and about possible ways to mitigate his new relay technique. He said the Bluetooth SIG team took note of his work and said that "more accurate ranging mechanisms are under development."


Breaches and hacks
Crypto-hack #1: Users of the SpiritSwap and QuickSwap cryptocurrency platforms were redirected to phishing sites over the weekend when trying to access the platforms' legitimate domains. Both companies confirmed that the incidents took place after threat actors socially-engineered GoDaddy employees into transferring ownership of the domains. The hijacks lasted for a few hours before both companies managed to regain control over their official websites. While the platforms tried to warn users via social media and other channels, several users had their accounts hacked and emptied by the attackers.

Crypto-hack #2: However, this wasn't the only incident that took place over the weekend. About the same time as the SpiritSwap and QuickSwap incidents, a threat actor also deployed a malicious ad via the CoinZilla advertising platform. The script appeared on sites like CoinGecko, DEXTools, and Etherscan and prompted users to grant the attacker access to their Metamask wallets. CoinZilla confirmed the incident shortly after and said that the malicious ad was only live for "less than an hour" before they took it down.


General tech and privacy
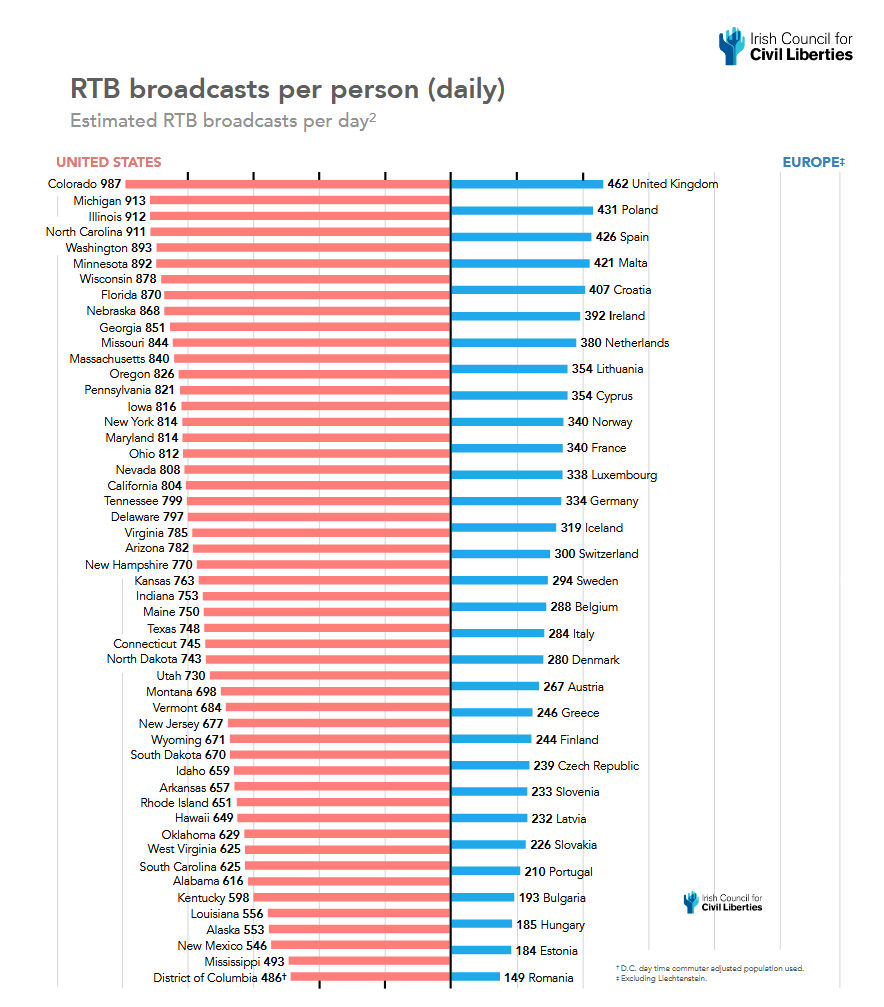
Report on Real-Time Bidding: The Irish Council for Civil Liberties has published a report on Real-Time Bidding (RTB), the process at the heart of the modern online advertising industry. The report called RTB "the biggest data breach ever recorded" because it tracks and shares what people view online and their real-world location. The report discovered that a regular US citizen has their data and location tracked 747 times per day, on average, while in the EU, where there are stricter privacy regulations, users get their data tracked only 376 times per day. Some good coverage from Natasha Lomas in TechCrunch.
New Google Cloud security features: At its yearly Security Summit conference, the Google Cloud team announced new security features and services coming to its service. Among the new features, the most interesting one is the option to give customers the ability to use the same open-source libraries that Google itself uses—as a way for customers to harden their cloud infrastructure against supply chain attacks. This new feature is called the Google Cloud Assured Open Source Software service. Some good coverage from Lucian Constantin in CSO Online.
Government, politics, and policy
New GDPR fine calculator: The EU has published new guidelines for calculating GDPR fines as part of an effort to align fine levels for infringing companies across member states. The new rules put more focus on the size of a company when determining the final fine size—instead of the offense type—and will also play a more important role in allowing supervisors from member states to monitor investigations in other countries.
North Korea IT workers warning: The FBI, the State Department, and the US Treasury have published a joint advisory [PDF] this week warning that the North Korean government is using agents disguised as IT freelancers that apply for jobs at large corporations, as a way to get a foothold inside corporate networks and high-value assets. The three agencies warn that these agents may help North Korean state hackers penetrate networks and steal intellectual property, classified information, or carry out financially-motivated attacks.
Initial access report: Cybersecurity agencies from across Five Eyes countries have published a joint report on the most common methods and techniques used by threat actors to gain an initial foothold into corporate and government networks. According to the report, some of the most common weaknesses that allow attackers to penetrate networks include not enforcing multifactor authentication, incorrectly aplied privileges or permissions, the use of default/factory logins, and not keeping software up to date.
FBI alert on web skimmers: The FBI has a flash alert [PDF] out, warning US companies about the danger of having their online stores backdoored by web skimmer gangs.
Cybercrime and threat intel
Thanos ransomware author charged: The US charged on Monday a French-Venezuelan citizen for allegedly creating the Jigsaw and Thanos ransomware strains. According to the complaint, the suspect—named Moises Luis Zagala Gonzalez—is a 55-year-old cardiologist from Venezuela. DOJ officials said Zagala created and advertised his ransomware on underground cybercrime forums and that one of his customers was the Iranian espionage crew MuddyWater. The FBI said it linked illicit money transfers from Thanos attacks to Zagala's accounts and confirmed his identity and current location following an interview with a US-based family member, whose PayPal account was also used to launder some of the suspect's ransomware profits.
Conti all along: In a report published on Tuesday, security firm AdvIntel said that the ransomware attack that hit the San Francisco 49ers NFL team earlier this year was actually carried out by the Conti gang, which used the BlackByte persona as "a shell group to process the breach." AdvIntel described the BlackByte gang as a "data-stealing venture," and not as a classic ransomware group, operating similar to Karakurt, another Conti sub-group that extorts companies with stolen files, typically after the main Conti gang failed to encrypt systems.
Attacks on SQL servers: In a Twitter thread on Tuesday, Microsoft published details about a brute-force campaign currently targeting MSSQL servers.

Ukraine arrests hacker: Ukraine's Cyber Police agency has detained a 28-year-old for hacking into social media accounts and then requesting money loans from the victim's friends into his own account. The suspect is believed to have hacked the accounts of at least 50 individuals and made more than $6,500 from his scheme.
Malware technical reports
UpdateAgent: Jamf published a report on Monday on recent changes to UpdateAgent, a malware dropper designed to target Mac systems. TL;DR: The malware has been re-written in the Swift programming language.
Facestealer: Trend Micro has published a report on Facestealer, a malware strain that was recently found in more than 200 Android apps uploaded on the official Play Store. The company said the malware is capable of stealing user passwords and other sensitive information, including private keys.
Destructive version of Chaos ransomware: Fortinet said that it recently spotted a new ransomware strain built using the Chaos ransomware builder that after it infects victims, it shows messages of support for the Russian government in its conflict with Ukraine. This version encrypts files with no way to decrypt them and adds a ".fuckazov" extension to all affected files.
Cry-what now: In a blog post on Tuesday, Microsoft's security team re-branded every infostealer malware strain that can steal cryptocurrency wallet data as "cryware." Please never use this term. Just trust me on this!
APTs and cyber-espionage
Nonghyup Bank hack: On Tuesday, South Korean officials indicted five suspects for a cyber-attack on Nonghyup Bank in 2011. Officials charged four North Korean hackers and a South Korean who allegedly traveled to China and shared information about the bank's network, including data like IP addresses. The alleged meeting took place in July 2011, two months after Nonghyup Bank detected an initial intrusion that began in 2010. Officials said the second attack that used data shared by the South Korean insider failed, although Nonghyup admitted to other intrusions in the following years.
HUI Loader: JP-CERT has published a technical analysis of HUI Loader, a malware strain used by multiple APT groups, such as APT10, A41APT, and Blue Termite.
Chinese operations: Presenting at Black Hat Asia over the weekend, analysts from Team T5 said that threat intel analysts could predict future targets of Chinese cyber-espionage groups by keeping an eye on new Chinese government policies. The company gave an example of how Beijing's recent crackdown on gaming companies during the COVID-19 pandemic was also accompanied by a wave of cyber-attacks carried out by Chinese cyber-espionage groups that targeted the local online gaming, gambling, and casinos sector.
Lazarus: ESET said it discovered traces of Lazarus malware that hid inside the folder of a known Windows crack activation tool. The victim of this attack was the same Philippines company that was infected via a trojanized KeePass app last month, and ESET said it used this technique because the Windows crack tool's instructions told users to exclude its folder from antivirus scanning.

Vulnerabilities and bug bounty
Tatsu Builder attacks: Web security firm Wordfence reported on Tuesday seeing a massive uptick in attacks targeting WordPress sites running the free and commercial versions of the Tatsu Builder plugin. The attacks peaked on May 14, when the company said it detected 5.9 million attacks against 1.4 million websites. The attackers used a recently disclosed vulnerability tracked as CVE-2021-25094.
Apple backports zero-day fixes: After releasing initial fixes for iOS and macOS zero-days at the end of March, Apple released on Monday additional backported fixes for macOS BigSur users as well.
Infosec industry
Tetragon: Security firm Isovalent has open-sourced Tetragon, an eBPF-based security observability and runtime enforcement platform.