Risky Biz News: PyPI to enforce 2FA, reduce stored IP addresses
In other news: The Pentagon has a new Cyber Strategy; hacker backdoors Emby media servers around the world; and the NSO Group has new ownership.
This newsletter is brought to you by Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. The Apple Podcasts link is here:
The Python Software Foundation has taken several actions to improve the security and privacy of the official Python Package Index (PyPI) following a series of incidents over the past few weeks.
Plans are currently underway to enable two-factor authentication (2FA) for PyPI accounts and to reduce the instances where the PyPI portal needs to store a user's IP address.
All accounts that maintain a Python library on the PyPI portal must set a 2FA method by the end of the year or have their access to some PyPI features limited.
The Foundation says the move comes to improve the supply chain security of the Python ecosystem. The move also comes after the Foundation had to temporarily halt submissions of Python packages to PyPI last weekend after the portal was flooded with a large number of malicious packages.
While 2FA blocks account takeovers, it's also a serious barrier for automated attacks like the ones PyPI has seen over the past few months.
Currently, 2FA is supported on PyPI but has been optional. The Foundation offered free security keys for the maintainers of its Top 1% packages last year in a move it proved to PyPI devs that 2FA wouldn't be the serious disruption everyone thought it would be.
The second major move announced at the end of last week was the Foundation's effort to purge IP addresses from its server logs and replace them with hashes (of the IP address) or geographic data provided by its CDN provider Feedly.
The only systems that will handle plaintext versions of a user's IP address will be rate-limiting systems, and the Foundation says it's working on replacing those as well.
"We apply a salt (known value) to the IP address before hashing it. It's not a perfect solution, but it's a step in the right direction.
The hash is non-reversible, but since the known address space is relatively small, it's possible to brute force the hash to determine the original IP address. By applying a salt, we require someone to possess both the salt and the hashed IP addresses to brute force the value. Our salt is not stored in the database while the hashed IP addresses are, we protect against leaks revealing this information."
News of this major engineering effort came two days after the Foundation revealed it was subpoenaed by the US Department of Justice to reveal information on five PyPI accounts. The requested information included the users' IP addresses, but also the IP addresses of all users who downloaded packages from the five users.
While other package indexes have announced plans to force their users to enable 2FA, the move to purge IP addresses from logs and databases is quite a novel solution and one we expect to see other privacy-focused organizations test and implement in the near future.
Breaches and hacks
Emby server hacks: Software company Emby has remotely shut down the media servers of some customers after a hacker used a vulnerability to hijack their systems. The hacker used an old vulnerability to install a malicious plugin that stole user passwords. The company developed a firmware update to scan for the malicious plugin, shut down systems where it was present, and ask users to change passwords. More than 1,200 customer systems were affected.
Super VPN data leak: The Super VPN service has exposed more than 360 million records after its Chinese developer left the app’s database open to the internet. The database contained information on all its paid customers, including details such as emails, the customers' real IP addresses, geolocation information, and the VPN servers they connected to. The database was secured after it was discovered and reported to the developer by security researcher Jeremiah Fowler. Fowler's findings contradict the app's App Store listing, where the service claims "no logs [are] saved anywhere."
Augusta ransomware attack: The city of Augusta, Georgia, has been hit by a ransomware attack that encrypted some of its internal IT systems. The incident took place on May 21 and was claimed by the BlackByte ransomware gang. Initial media reports claimed the gang had requested a $50 million ransom demand, which city officials denied in a press release. Augusta is the second-largest city in the state of Georgia. Atlanta, the state's largest city, was also hit by ransomware in 2018.
MCNA ransomware attack: US healthcare provider Managed Care of North America says a ransomware gang has stolen the personal information of 8.9 million of its customers. The breach took place in late February when the LockBit gang gained access to the company's network and stole patient information before encrypting systems. LockBit leaked MCNA's data online at the start of April after the healthcare provider declined to pay the criminal group. According to MCNA, the leaked data includes full PII, SSNs, driver's license information, health care and insurance details.
DDoS attacks: Government websites in Italy and Senegal have seen DDoS attacks over the past few days from hacktivists.
Jimbos Protocol crypto-heist: The Jimbos Protocol cryptocurrency platform has been hacked for $7.5 million worth of Ether. According to blockchain security firm Peckshield, the hack was due to the lack of proper controls in one of the platform’s protocol that allowed the threat actor to exploit price ranges during asset conversions for a profit. The Jimbos Protocol was launched less than three weeks before. [Additional coverage in AZCoin News]
Patricia crypto-heist: Nigerian cryptocurrency exchange Patricia says that hackers breached customer trading application and stole some of its funds. The company did not reveal how many funds were stolen. It paused withdrawals and notified authorities.
SolarWinds 2020 hack lawsuit: The Delaware Supreme Court has upheld a decision from lower courts to dismiss a lawsuit filed by SolarWinds shareholders against the company. Shareholders sued SolarWinds in 2021 in regard to the company's 2020 supply chain attack that impacted thousands of organizations across the world. They argued the company breached its fiduciary duties after failing to secure its infrastructure.
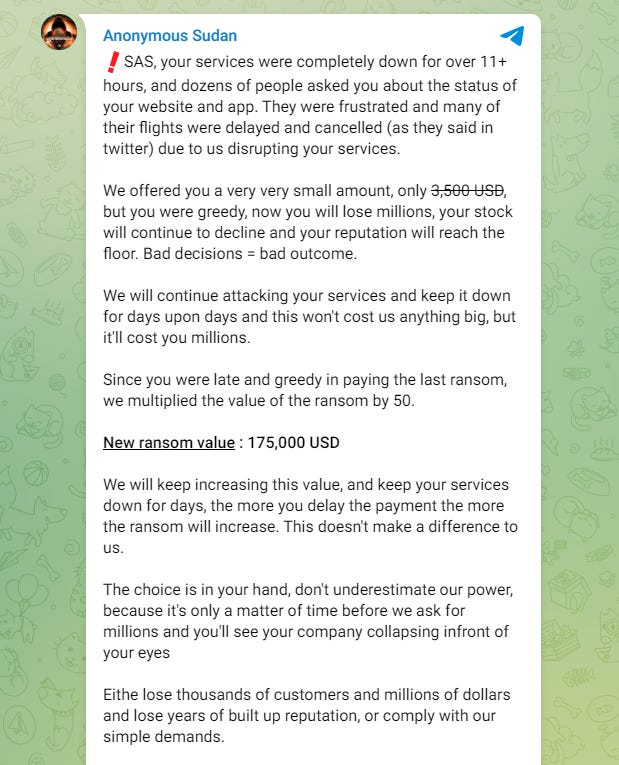
SAS extortion: Totally-not-Russian hacktivist group Anonymous Sudan is requesting $175,000 from Scandinavian Airlines to stop DDoS attacks on its websites. Guess the group got over their hacktivism phase quickly and is now into full-blown extortion.
General tech and privacy
Txti shuts down: Web hosting service Txti plans to permanently shut down all operations on July 1 this year. The company cites abuse from "bad actors" as the reason for its decision. Txti launched in 2016 and allowed users to host simple text-based web pages that could load on older phones.
Twitter pulls out of EU disinformation efforts: Crypto-spam, state propaganda, right-wing nuthouse, harassment, and the butt-of-all-jokes platform Twitter has pulled out of an EU voluntary project to combat online disinformation. Because, of course, it did.
Bitwarden goes passwordless: Password manager Bitwarden now supports passkeys.
Windows XP activation cracked: Crackers have broken the activation algorithm allowing anyone to install and verify Windows XP without a license (XP has been EoL for years).
Government, politics, and policy
ITA's surveillance past: The office of Senator Ron Wyden has requested that the International Trade Administration (ITA) of the US Department of Commerce answer questions on how it has helped American companies sell their surveillance products on foreign markets. Sen. Wyden has demanded the ITA reveal what kind of surveillance products it helped promote abroad over the past five years, what kind of assistance it provided to surveillance vendors, and to which foreign markets the products were sold. The Senator has also asked the ITA to reveal if the possibility that surveillance tools may be used for human rights abuses is taken into consideration before helping a surveillance vendor.
"As you know, the Biden Administration has recognized that surveillance technologies are frequently used by governments to invade the privacy of their citizens, enable violence and discrimination, and disproportionately harm marginalized and vulnerable communities. Given the Administration's stated interest in limiting the human rights abuses made possible by these technologies, ITA must be transparent about its past and current promotion of these technologies abroad."
Pentagon cyber strategy: The US Department of Defense has sent a classified version of the 2023 Cyber Strategy to Congress. The document notifies lawmakers on how the DoD will operate in cyberspace to protect the US and its priorities. It is the first Cyber Strategy document the DoD has published since 2018. The Pentagon says the new Cyber Strategy version is grounded in past DoD real-world experiences and also includes lessons from the recent conflict in Ukraine. Officials say the Russo-Ukrainian conflict "demonstrated how cyber capabilities may be used in large-scale conventional conflict." Principles outlined in a summary factsheet [PDF] include defending forward, cyber partnerships with US allies, and the focus on building a resilient cyber force. An unclassified version of the document will be released later this year. [Additional coverage in The Record]
China denies hacking reports: The Chinese government has put out a salty statement denying recent Microsoft and Five Eyes reports that Chinese hackers breached US critical infrastructure organizations, calling it "a patchwork with a broken chain of evidence," "a report filled with disinformation," "subterfuge," bla bla bla, and more whataboutism.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritization.
Cybercrime and threat intel
New NSO ownership: Israeli spyware vendor NSO Group is under new ownership after creditors forced a change earlier this year. The company is now under the ownership of Dufresne Holdings, a company founded by Omri Lavie, one of NSO's original co-founders. The move comes after NSO creditors Credit Suisse and the Senator Investment Group foreclosed NSO's former owner, Luxembourg-based holding company NorthPole. Yaron Shohat has also been appointed as the company's new CEO. [Additional coverage in the Wall Street Journal/non-paywall]
Paragon Solutions: The Financial Times published an interesting profile [non-paywall] on Paragon Solutions, an Israeli spyware vendor that, unlike NSO Group, has become a customer of the US government rather than its mortal enemy. The company operates the Graphite platform, which, according to reports, is used by the US Drug Enforcement and Administration Agency (DEA).
Freenom malicious domains go down: Interisle security researcher Dave Piscitello has observed "a significant decline in phishing domains" hosted on top-level domains managed by domain registrar Freenom. The company is the official domain name registry for top-level domains of the Central African Republic (.cf), Equatorial Guinea (.gq), Gabon (.ga), Mali (.ml), and Tokelau (.tk). Meta sued Freenom in March for ignoring abuse requests and allowing malicious sites to operate unimpeded. Piscitello says the lawsuit appears to have worked, and Freenom domains now account for only 15% of phishing domains worldwide after it accounted for a whopping 60% in November of last year. [Additional coverage in KrebsOnSecurity]
DeltaBoys: CyFirma has a profile on DeltaBoys, a threat actor that appeared in 2021. The group started out as database brokers and carders before evolving last year into a group that sells access to web shells they have planted on hacked websites. CyFirma notes that in recent months, the group has also carried out a few mass defacement operations as well.
Basterlord manual leaks: UK threat intel analyst Daniel Card has published a manual that contains advice on how to defend networks from the techniques included in the "Ransomware Manual," a training guide that was being sold by a threat actor named "Bassterlord" on underground forums earlier this year for $10,000.
MeshAgent campaign: AhnLab has published details on a malware campaign that uses malicious VPN clients to infect users with the SparkRAT and a version of the legitimate MeshAgent remote access utility, which attackers use to access compromised hosts.
YouTube campaign: Fortinet reports on a campaign using YouTube videos promoting cracked software that infect victims with malware strains such as the Vidar Stealer (infostealer), the Laplas Clipper (clipboard hijacker), XMRig (cryptominer).
PlutoCrypt decrypter: Cybersecurity firm Prodaft has published a free decrypter for the PlutoCrypt ransomware to allow victims to recover their files without paying the attackers.
New npm malware: Seven new malicious npm packages were spotted last week. Check out GitHub's security advisory portal for more details.
PT trends report: Russian security firm Positive Technologies has published its yearly threats report for 2022 and looks at possible trends for 2023. The 207-page report is here. One of the most interesting things we found in the report was this list of today's major bug bounty platforms.
Malware technical reports
Snake hunting: JUMPSEC researchers have published a guide on how security researchers can go hunting for Turla's Snake malware—recently left with its pants around its ankles by Five Eyes.
Bandit Stealer: Trend Micro published a report on a new Go-lang infostealer named Bandit Stealer. The infostealer contains quite a lot of anti-detection mechanisms and can collect data from 15 browsers and crypto-wallets.
r77 rootkit: Elastic's security team has a deep dive into r77, a stealthy open-source rootkit that has been used in the wild to deploy persistent Monero cryptominers.
Risky Business Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
Nothing in this edition.
Vulnerabilities and bug bounty
Mitsubishi PLC vulnerability: Cisco Talos researchers have discovered a vulnerability (CVE-2023-1424) in Mitsubishi MELSEC PLCs that can lead to denial of service and even code execution. A patch was released last month.
GitLab PoC released: Security firm OccamSec has published a proof-of-concept exploit for a critical GitLab vulnerability. GitLab released patches for the issue last week and "strongly recommended" that users patch servers "as soon as possible." The vulnerability allows unauthenticated third parties to read files on GitLab servers and may be used by attackers to steal proprietary source code. The vulnerability is considered easy to exploit and received a rare 10/10 CVSSv3 severity score.
Sonos vulnerabilities: ZDI has published a write-up on the four Sonos vulnerabilities exploited last December at its Pwn2Own hacking contest. The vulnerabilities include two info-leaks and two RCEs.
Infosec industry
WOOT papers: The papers presented at the Workshop on Offensive Technologies (WOOT) security conference, which took place last week, are available on the conference's website. The paper titled "CustomProcessingUnit: Reverse Engineering and Customization of Intel Microcode" won this year's Best Paper Award. Also, check out "Emoji shellcoding in RISC-V."
Trustwave spams Glassdoor: An investigation has discovered that security firm Trustwave appears to have spammed its own Glassdoor page to improve the company's workplace rating on the site. The investigator linked the start of the campaign to Trustwave hiring a new Chief People Officer in May 2021.
Ferrari+Bitdefender: Ferrari signed a long-term partnership with Bitdefender after the company suffered a cyber-attack and was extorted back in March. Bitdefender was already one of Ferrari's F1 sponsors, and the new deal basically extends their collaboration to the entire Ferrari business.
New book: Microsoft security researcher Thomas Roccia has released "Visual Threat Intelligence," a visual guidebook for new cyber threat intelligence analysts. Discount code available.
New tool—LOOBins: Security researcher Brendan Chamberlain has launched a new project named LOOBins, a portal that collects information on all the macOS binaries that can be abused for living-of-the-land attacks. Similar projects also exist for Windows (LOLBAS and LOLDrivers) and Linux (GTFOBins).
New tool—Code Query: NCC Group has open-sourced a new tool named Code Query, a new universal code security scanning tool.