Risky Biz News: Python and PHP libraries hijacked to steal AWS keys
In other news: GM and Zola get hit by cred-stuffing attacks; Clearview AI fined in the UK; mysterious APT hacks RT email accounts.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Developers had a very bad day on Tuesday after news broke that two very popular Python and PHP libraries got compromised after a threat actor gained access to their respective developers' accounts and pushed new versions containing malicious code.
The incidents impacted the CTX Python library on PyPI and hautelook/PHPass PHP library on the Packagist portal. Both are very popular libraries with tens of thousands of weekly downloads, according to DevOps security firm Sonatype.
The code added to new versions of both libraries would collect environment details from a developer's computer, such as AWS and other server passwords, and upload the data to a remote Heroku app, hosted at:
https://anti-theft-web.herokuapp[.]com/hacked/
Because the exfiltration URL pointed to the same Heroku app, investigators believe both attacks were carried out by the same threat actor, who was most likely looking to collect AWS keys so they could hijack cloud resources and mine cryptocurrency.
Even if the security of supply chains for open source projects is nowhere near as good as some experts would want, the attack was detected rather quickly, mainly because both libraries were abandoned and did not receive any new versions in years, sparking concern for some of their more attentive users, some of which reported the rather unusual updates via Reddit.
The attack seems to have impacted Python developers more than PHP coders, as the hautelook/PHPass library had been abandoned and its releases deleted last September, so most devs had already moved to other libraries in the meantime.
Nevertheless, the incident did have a major impact in the Python community, where it was downloaded more than 27,000 times between May 14 and May 24, according to an IR report published by the Python security team on late Tuesday night.
The same report also concluded (and confirmed an ISC SANS report from earlier in the day) that the attacker gained access to the CTX developer account by identifying their email address and re-registering the email server domain after it had previously expired. This rather new account hijacking technique allowed the threat actor to reset the developer's PyPI account password and then push the malicious versions two weeks ago.
Breaches and hacks
GM cred-stuffing: General Motors said that the data of some of its customers was exposed following a credential stuffing attack that took place last month, according to a data breach notification letter the company filed with California's Office of the Attorney General. In addition, the company also said that it "identified recent redemption of customer reward points for gift cards that may have been performed without the customers' authorizations."
Zola cred-stuffing: Wedding planning startup Zola said that hackers breached user accounts following credential stuffing attacks. The company disclosed the incident over the weekend after several users complained that hackers had depleted accounts, incurred huge charges on their cards, and even locked them out of their accounts days ahead of their weddings. According to a TechCrunch report, some of these accounts are being listed on underground Telegram channels. Zola said that only 0.1% of its users were impacted and that it will refund all users who lost funds in the incident.
General tech and privacy
Clearview AI fined in the UK: The UK Information Commissioner's Office (ICO) has fined facial recognition company Clearview AI more than £7.5 million ($9.4 million) for breaching the UK GDPR and collecting users' photos without permission. The ICO has also ordered Clearview AI to stop collecting and indexing the personal information of UK citizens and to delete existing UK-related databases.
Some Russian companies fire Ukrainian IT experts: Russian news outlet RBC is reporting that Russian companies have begun to fire or demote IT experts of Ukrainian nationality or descent. In addition, sources from Russian cybersecurity firms have also told the publication that they have been instructed to closely monitor employees of Ukrainian descent or those who have relatives in Ukraine. Moves to fire or demote IT workers with access to critical systems have been observed in companies with government contracts, and sources have described it as an "unspoken requirement" for continuing to work with government agencies.
Google geo-location data collection: A coalition of Democratic lawmakers have asked Google on Tuesday to stop the collection and retention of personal user data and geo-location information via its Android operating system pertaining to online inquiries about abortion access. Forty-one Democratic lawmakers signed the document, according to a NextGov report.
Government, politics, and policy
US Senate report: A report published on Tuesday by the US Senate Homeland Security and Governmental Affairs Committee has found that US law enforcement lacks comprehensive data and visibility into ransomware attacks due to poor reporting, which is fragmented across multiple federal agencies such as CISA, the FBI, the Treasury's FinCEN, and others.
EU wants a "cyber posture": The Council of the European Union agreed on a set of unified core principles meant to create a unified cyber posture for EU member states. This include:
strengthen resilience and capacities to protect;
enhance solidarity and comprehensive crisis management;
promote the EU's vision of cyberspace;
enhance cooperation with partner countries and international organisations;
prevent, defend against and respond to cyber-attacks.
The Council called on EU agencies and member states to integrate these principles into upcoming directives and guidelines.
France: In March, ANSSI, France's cybersecurity agency, published a report with an overview of threats against French companies throughout 2021. That report is now available in English.
Hack exposes Chinese Uyghur camps: Documents leaked by anonymous hackers show the full extent of China's Uyghur internment camps across its Xinjiang province. Fourteen different news organizations have analyzed the leaked documents and confirmed their authenticity. Here's a spectacular visual report from the BBC.
Cybercrime and threat intel
Conti's last breaths: After reports that it was shutting down, the Conti gang published eight new victims on its leak site over the weekend, in what security researchers are describing as its last breaths.

RansomHouse: Threat intelligence company CyberInt has published a report on a new data extortion group that was first seen earlier this year and calling itself RansomHouse. The group has one of the longest and more detailed terms of service of any extortion group that was seen operating over the past few years.





DeFi hacks: Threat intel firm BishopFox has a report out reviewing all the DeFi blockchain platform hacks from last year and the main methods used to breach their networks and exfiltrate funds.
jQuery scans: A threat actor is scanning the internet for websites that use the jQuery File Upload plugin, per ISC SANS. The organization believes the threat actor is attempting to fingerprint vulnerable systems in order to exploit security flaws in the plugin and upload malicious files (such as web shells) on web apps still using older versions of the plugin.
200 malicious npm packages: DevOps security firm Snyk found more than 200 malicious npm packages uploaded on the npm portal, including some that would install a Cobalt Strike-based backdoor on infected systems. All the packages had names similar to legitimate packages, in what security researchers call a dependency confusion attack, aimed at tricking developers into using and importing the malicious package into their projects instead of the legitimate one.
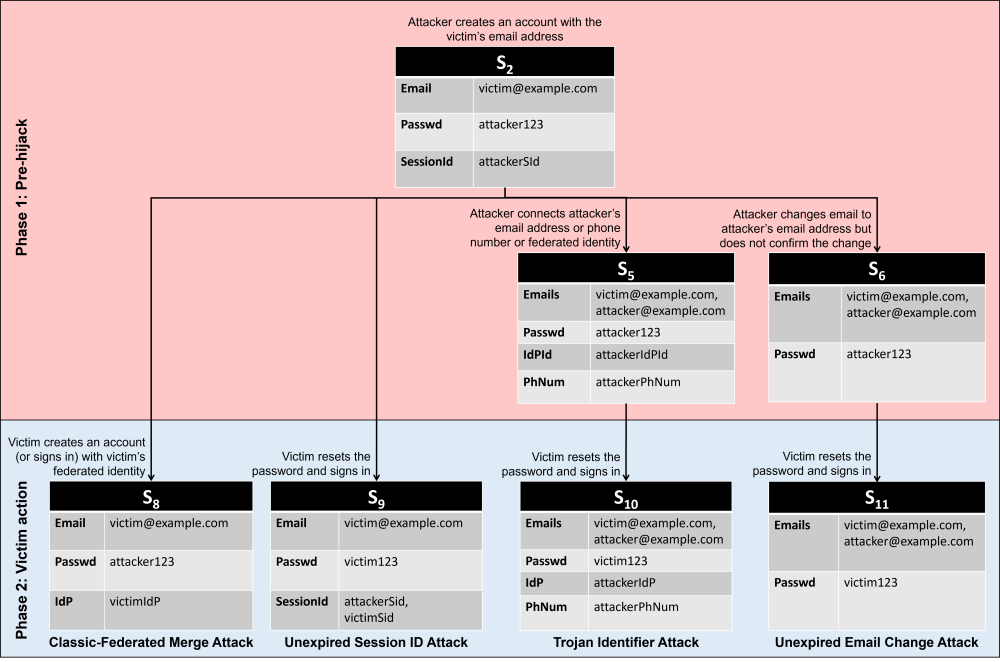
Account pre-hijacking: A duo consisting of an independent researcher and a Microsoft engineer have published a research paper this week on a new account hijacking technique that they called account pre-hijacking. The technique consists of a threat actor registering accounts on websites before the victim, using the victim's email address. The attacker then connects their own email address, phone number, or federated identity to the victim's account but never officially confirms the changes. When a victim tries to register an account, they are asked to reset their password. If the service fails to invalidate all previous sessions or purge older account details, the attacker still maintains access to the account they initially created. More in the research paper.
Malware technical reports
Web skimming attacks: Microsoft has a good review on web skimming attacks and the latest techniques these groups are using these days.
Yashma ransomware: The BlackBerry team published a report on the new Yashma ransomware. Just like SentinelOne in a recent report, BlackBerry researchers concluded that Yashma is based on the older Chaos ransomware.
Vulcan ransomware: According to SentinelOne, the operators of the Vulcan ransomware group are actively recruiting affiliates to help them breach networks and carry out intrusions.
Nokoyawa ransomware: Fortinet has published a report on the new Nokoyawa ransomware, which the company said borrows code from strains like Babuk, Karma, and Nemty.
GoodWill ransomware: CloudSek researchers said that a new ransomware strain named GoodWill—instead of requesting ransom payments—instructs victims to donate money to perform three acts of goodwill in order to receive a decryption key for their files. The three acts include:
Donating new clothes to the homeless, recording the action, and posting it on social media.
Taking five less fortunate children to Dominos, Pizza Hut, or KFC for a treat, taking pictures and videos, and posting them on social media.
Providing financial assistance to anyone who needs urgent medical attention but cannot afford it, recording audio, and sharing it with the operators.
For now, this appears to be only a proof-of-concept ransomware, and no known victims have been identified. CloudSEK researchers said that based on current evidence, they believe the ransomware's creator is located in India.
APTs and cyber-espionage
Turla: Cybersecurity firm Sekoia published a blog post on Monday detailing a recent reconnaissance and espionage campaign executed by the Turla APT group. Targets included the Baltic Defense College and the Austrian Economic Chamber.
Russia Today campaign: Malwarebytes said on Wednesday that after Russia's invasion of Ukraine, an APT group began targeting employees of Russia Today with a malicious spear-phishing campaign. The company reports that the attacks infected RT employees with a remote access trojan and that the threat actor "had access to almost 100 RT TV employees' email address." The attacks also appear to have targeted the Rostec defense conglomerate as well.
Vulnerabilities and bug bounty
Matryoshka Trap: A team of four Chinese academics has published a report called Matryoshka Trap [PDF], which describes how to use memory-mapped I/O (MMIO) calls to escape virtual machines. The vulnerabilities impact QEMU/KVM, a hypervisor widely used in cloud computing environments, and are tracked as CVE-2021-3929 and CVE-2021-3947. The paper was presented at the CanSecWest security conference last week, and proof-of-concept code was also made available on GitHub.
$10 million bounty: Cryptocurrency platform Wormhole paid one of the largest bug bounties ever recorded, awarding $10 million to a security researcher named satya0x for a bug that could have allowed a threat actor to steal funds from its inter-blockchain bridge implementation. Wormhole's huge payout comes after the company was hacked and lost more than $322 million in an incident earlier this year, in February.


GitHub bug bounty program: GitHub said it awarded more than $800,000 in bug bounty rewards in 2021, bringing its total to more than $2.3 million awarded to security researchers since the creation of its bug bounty program in 2016.
Screencastify vulnerability: Security researcher Wladimir Palant has published a report about a vulnerability in Screencastify, a Chrome browser extension that could be used to record and share videos using a browser's webcam API. Palant said attackers could abuse the bug to secretly record videos via a victim's webcam. The researcher said that after notifying the extension's developer earlier this year, in February, not only did they not fix the issue but also added a second vendor's domain through which it could be exploited.
No patches: Netgear said that "due to technical limitations outside of [their] control," they are unable to patch multiple security vulnerabilities in the BR200 and BR500 router models. The vulnerabilities can allow threat actors to execute malicious code against a victim's router management panel when users visit a malicious site. Netgear has recommended that all users log off from the router control panel to prevent automated attacks.
Trend Micro zero-day: Trend Micro said it patched a vulnerability exploited by the Moshen Dragon APT in attacks reported earlier this month by SentinelOne.
Zoom fixes: Zoom has fixed four vulnerabilities reported by the Google Project Zero team that could have allowed threat actors to hijack user systems just by sending malicious instant messages to Zoom users. The root cause of the issue was identified as the Zoom clients and server software using different XML parsing libraries to handle XML data via the XMPP protocol, opening the door to hijacking conversations and connecting Zoom users to malicious servers.
ISaPWN: Kaspersky's industrial security research team has published a report on ISaPWN, a set of vulnerabilities in ISaGRAF, a programming tool and execution environment used to create and run programs for programmable logic controllers (PLCs). The company said that since March 2020, it has worked with various vendors, such as Rockwell Automation, Schneider Electric, Xylem, GE, and Moxa, to test and release patches for various PLC and SCADA tools that make use of ISaGRAF. The vulnerabilities are considered critical as some can allow unauthenticated, remote attacks against industrial equipment, while others allow password brute-force attacks or device persistence.


Infosec industry
Security funding news: One good newsletter to subscribe to is Security Funded, a weekly newsletter with news on recent funding rounds and market moves from cybersecurity companies. The newsletter is curated by Mike Privette. Sample newsletter here.
Verizon DBIR: The Verizon 2022 Data Breach Investigations Report (DBIR) is out. The report has built a well-deserved reputation for providing the most comprehensive view of the cybersecurity landscape across the world. Among this year's main DBIR conclusions was that supply chain attacks were responsible for roughly 62% of the security incidents that took place last year and were analyzed for the report.