Risky Biz News: SEC adopts new cybersecurity rules; adopts 4-day disclosures
In other news: Former Group-IB CEO gets 14 years in prison in treason case; 41 zero-days exploited in the wild last year; and new DDoS attack types spotted.
This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The US Securities and Exchange Commission has passed a new set of cybersecurity rules for publicly traded companies.
The new rules would require companies to disclose any cybersecurity incident to the SEC within four days after a company has deemed the incident grave to be "material." In the context of the SEC, material refers to events that impact a company's operations, finances, or may sway shareholder voting decisions—so it's likely to cover quite a lot of incidents.
The new rule is not without its fair share of controversy. The rules passed in a close 3-2 partisan vote following more than a year of negotiations and rulemaking. Both Republican-appointed members voted against it.
The new disclosure timeline also controversially doesn't start at the time of the breach itself but when a company's lawyers decide to categorize the incident as "material"—which, as WaPo reporter Joseph Menn points out, leaves somewhat of a loophole in prolonging breach disclosures for some incidents.
The rules also allow for some incidents to be delayed if a breach is considered to have an impact on public safety or national security—but these delayed disclosures will need express written approval from the US Attorney General, which suggests they might not be granted except for extreme and very large cybersecurity incidents.
Publicly traded companies previously had to disclose security breaches to the SEC, per 2011 and 2018 guidance, so this doesn't change much, but no strict timeline was previously enforced.
The four-day disclosure is also double the 48 hours the SEC initially proposed in a draft of the regulation it put out for public comment back in March, suggesting it received some serious pushback from companies and industry groups on the short deadline it initially proposed. This was more than obvious when the SEC delayed announcing the new rules last month, citing more work needed on the language.
In addition to the disclosure rules, companies will also be required to disclose to the SEC in a yearly filing how they manage cybersecurity risks and what cybersecurity expertise their boards and managers have.
An IANS study published in June found 90% of public companies lacked even one qualified cyber expert on their board.
The new rules will enter into effect for US companies 30 days after they're published in the official Federal Register. Foreign companies get 90 days, while smaller reporting companies get 180 days.
Pro-tip: If you're an SEC EDGAR lurker like me, the new breaches will have to be filed via 8-K forms. If you want to keep an eye on new disclosures, set a CapEdge email alert for a query like this in your account.
Breaches, hacks, and security incidents
NATO investigates breach: NATO is investigating a possible security breach after a hacktivist group named SiegedSec posted a batch of NATO documents on its official Telegram channel this week. The files appear to have been obtained through the NATO Community of Interest Cooperation Portal, a web portal for exchanging unclassified information. SiegedSec claimed the leak had nothing to do with the war in Russia and Ukraine. [Additional coverage in CyberScoop]
AlphaPo hack: Blockchain sleuth ZachXBT has linked the AlphaPo $60 million cyber heist to North Korea's Lazarus Group.
CardioComm incident: Healthcare IT service provider CardioComm says that a cyberattack has taken down some of its services, including some servers that support the company's handheld electrocardiogram monitoring devices. Since the attack, the company says users can't access cloud-stored readings but that devices are working as intended.
Ortivus cyberattack: A cyberattack on Swedish IT provider Ortivus has left at least two UK ambulance services without access to MobiMed ePR, the company's electronic patient records platform. The two ambulance services serve more than 12 million people across South England. Ambulances are still servicing patients, but staff doesn't have access to patient records in real-time in cases of emergency. [Additional coverage in the BBC]
CISA report: CISA says that half (54%) of the security incidents that impacted government agencies and critical infrastructure organizations in 2022 have been traced back to attackers using valid credentials to access the victim's network. This includes credentials for admin accounts, VPN servers, and other crucial systems. Spear-phishing links were successful only 33% of the time, according to CISA's yearly risk and vulnerability assessment report.
General tech and privacy
Meta's fined in Australia: Australia's Federal Court has ordered Meta to pay a fine of AUD$20 million (USD$13.5 million). The fine is in connection to a civil lawsuit filed by the Australian Competition and Consumer Commission (ACCC) against Meta for collecting the personal data of its Onavo VPN users without their knowledge or consent. Besides the fine, Meta is also on the hook for AUD$400,000 (USD$270,000) in legal fees to the ACCC. [Additional coverage in iTnews]
ESRB face scanning proposal: The US Entertainment Software Rating Board (ESRB) is seeking the FTC's approval to roll out a facial scanning program for online gamers. The ESRB says the new technology would allow gaming companies to determine the age of a user based on a face scan and prevent kids from registering accounts for games outside their age rating or protected by parental controls. [Additional coverage in Gizmodo]
Vivaldi critical of Google's WEI: The Vivaldi browser team has published a scathing criticism of a new standard proposed by four Google engineers. Named the Web Environment Integrity, the standard has been likened to a Web DRM, allowing several tech giants to lock access to the free internet, prevent new browsers from launching, and neuter ad-blocker extensions.
Mastodon instance seized: We have the first known case of a Mastodon server getting seized—Kolektiva[.]social.
Android KitKat: Google has announced that it will stop distributing Play Services updates for Android 4.4, also known as KitKat, one of the most popular and widely used versions of the Android OS ever released. Ten years later, KitKat is finally dead, both officially and unofficially, as only 0.5% of Android devices today are still running it.
e-Tugra removed from Firefox: Turkish certificate authority e-Tugra has been removed from Mozilla's list of trusted certificate issuers. Websites that use the company's certificates will now show an error message when accessed with Firefox. The removal comes after security researcher Ian Carrol identified flaws in e-Tugra's systems that allowed attackers to issue their own certificates or steal customer data. Google removed trust in e-Tugra certificates at the end of June, while Apple never trusted the company's certificates.
Semiconductor breakthrough: A lab in South Korea says it created the world's first superconductor that can work at room pressure and temperature. "Huge if true" moment, but their work has yet to be peer-reviewed or independently confirmed.
Government, politics, and policy
Russian spyware company CEO found dead: Russian businessman Anton Cherepennikov was found dead in his office last week, having allegedly overdosed on "medical gas." Cherepennikov was the CEO of ICS Holding, one of the Russian tech companies that helped the Kremlin implement its SORM national surveillance system. His company developed Yarovaya, a SORM system used to spy on Russian internet traffic. Cherepennikov and one of his companies were sanctioned by the US Treasury in February of this year. [Additional coverage in RBC & Svoboda/English coverage in The Times]
Russia's VKontakte censorship: CitizenLab has a thorough analysis of Russia's censorship of its in-house VKontakte social media platform. tl;dr: Censorship of Western news outlets went through the roof following Russia's invasion of Ukraine.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about vulnerable drivers, BYOVD attacks, and the problem with driver-based attacks.
Cybercrime and threat intel
Sachkov case: A Moscow court has sentenced former Group-IB CEO Ilya Sachkov to 14 years in prison to be served in a strict regime penal colony. Sachkov has been under arrest since September 2021, when he was detained on treason charges. Details about his case have never been made public by Russian authorities. Reporting in Russian media claims Sachkov was detained for providing data on Russian hackers to foreign intelligence services. Sachkov's sentence is four years short of the 18 years the prosecution asked in a pre-sentencing hearing earlier this month. Sachkov had always maintained his innocence and claimed in a Telegram video last month that he had been set up by FSB agents as part of a revenge plot. [Additional coverage in RBC/English coverage in KrebsOnSecurity]
Fenix group: Metabase Q researchers have identified a new threat actor named Fenix that is behind a wave of malspam targeting tax-paying individuals in Mexico and Chile.
Stormous gang returns: The Stormous cybercrime group has returned from a year of inactivity and is again extorting victims. The gang has restored its Telegram channel and has listed 35 victims on its dark web leak site. The group had been previously inactive, and its websites have been down since July of last year. Threat intelligence firm KELA believes the group went inactive after they were caught lying about several intrusions in subsequent extortion attempts. The group is believed to have Arabic-speaking members.
Anonymous Sudan interview: BBC cybersecurity reporter Joe Tidy has published an interview with the Anonymous Sudan "hacktivist" group.
NoBit ransomware: A new ransomware RaaS calling itself NoBit is advertising its services via Telegram.
AlphV launches API: Well, this is something new! The AlphV ransomware gang has launched an API that their affiliates and security researchers can query and get information about their latest victims.
Cryptojacking attacks rise: In its yearly threat report, SonicWall says it observed a 399% rise in cryptojacking attacks. The biggest spike was registered across European organizations, where cryptojacking attacks rose by 788%. The company's report comes after Microsoft's security team also warned of a rise in cryptojacking attacks this year. The SonicWall report also noted a decline in ransomware victims paying their attacks, which is what security firm Coveware also noted in a report last week as well.
Tomcat attacks: AquaSec has published a summary of the type of attacks and malware targeting Apache Tomcat web servers. It's Mirai! Mirai's everywhere!
New phishing method: Trellix researchers have spotted threat actors using a new method to abuse the "search-ms" URI protocol handler to download malicious payloads in recent phishing campaigns.
QUIC DDoS attacks: While it's been known that the QUIC protocol can be abused for DDoS reflection attacks, new research suggests attacks could reach up to 250 amplification factors, putting QUIC over the more popular DNS protocol (180 amp factor) in terms of raw power. With QUIC adoption slowly crawling toward 10% of all internet sites, the protocol is set to grow into a major problem for DDoS mitigation providers.
New DDoS type: The Dutch National Internet Providers Management Organization (NBIP) and US-based DDoS mitigation provider Radware say they are seeing large-scale DDoS attacks being carried out using a new attack method. Named HTTPS DDoS Tsunami, this new method can generate DDoS attacks with extremely high RPS (Requests Per Second) rates, sometimes reaching 880,000 or higher. The new attack method is challenging to mitigate because attackers switch the type of HTTP requests they use every few minutes. Radware says the new attack technique was developed by the hacktivist groups that emerged after Russia's invasion of Ukraine. It did not say on what side.
SocksEscort: A newly discovered IoT botnet named AVRecon appears to have been the backbone of a shady proxy service named SocksEscort. Network security company Spur spotted the connection between the two earlier this month after Lumen's security team sinkholed some of the botnet's command and control servers. Spur says Lumen's partial takedown had an immediate and severe impact on the number of proxies in SocksEscort's network, suggesting the proxy service was either using or secretly running the AVRecon botnet. In its analysis of the botnet, Lumen said AVRecon contained traffic-proxying capabilities but also other capabilities, such as ad fraud and password spraying.
Malware technical reports
CoD MW2 worm: A Steam worm is currently making the rounds using CoD MW2 servers to spread from player to player. It's unclear what the worm actually does, but it's most likely nothing good. Activision has confirmed the issue and has taken MW2 off the Steam platform to investigate. [Additional coverage in TechCrunch]
Iranian mobile malware: Sophos has published a report on a group of Android malware targeting the customers of four Iranian banks.
Akira: K7 Computing has published an analysis of the Akira ransomware's Linux encrypter.
Fruity: DrWeb researchers have discovered a new Windows malware strain named Fruity. The malware is being used as a modular downloader that delivers various other second-stage payloads on infected hosts, such as the Remcos RAT.
Jigsaw: ThreatMon has a technical deep dive into the new Jigsaw stealer. The company says the malware is an "exact replica" of the older Meow Stealer.
"The hacker behind this malware is attempting to deceive potential buyers by rebranding the same stolen software."
Nitrogen: A new malware strain named Nitrogen has been spotted in the wild by Sophos, Bitdefender, eSentire, and Trend Micro. Researchers believe the malware's goal is to backdoor corporate networks to enable hand-on-keyboard sessions and potentially drop ransomware. The malware is currently being distributed using malicious ads for certain software packages. Malicious ads have been spotted on the Google search engine, but also Bing—which is somewhat rare. Software used as a lure includes Slack, AnyDesk, WinSCP, Cisco AnyConnect, TreeSize, and other typical corporate IT programs.
Sponsor Demo
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs and cyber-espionage
Bitter's ORPCBackdoor: Knownsec's report on ORPCBackdoor, a new malware strain used in recent campaigns by the Bitter APT, is now available in English.
PatchWork's Eyeshell: The same company also published a report on EyeShell, a backdoor it's been using on Windows systems.
BlueBravo's GraphicalProton: RecordedFuture has published a report analyzing GraphicalProton, a malware strain used in recent BlueBravo (APT29) operations targeting diplomatic and foreign policy institutions in Eastern Europe, as these organizations provide valuable insight for the Russian intelligence consumers during the ongoing war in Ukraine.
APT29: Anheng also has a report out too on another APT29 campaign, this one impersonating the German embassy.
Vulnerabilities, security research, and bug bounty
Axis vulnerability: OTORIO researchers have found a vulnerability in the Axis A1001 door controller. A security advisory is here [PDF].
"This vulnerability involves the way it communicates, potentially exposing sensitive networks to unforeseen risks. Such a flaw could pose a significant threat to facilities' security and their internal IP networks. The exploit for this vulnerability requires physical access to the RS-485 twisted pair cable situated at the rear of an access control reader, typically stationed at the entry of a secured facility or perimeter. What sets this vulnerability apart is its potential for Remote Code Execution (RCE) on the internal access controller from outside of the facility. By exploiting the serial channel used for reader-controller communication, an attacker could gain unauthorized access to open doors or tamper with logs on the access controller. Even more alarmingly, this flaw could serve as a gateway to the internal IP network, irrespective of its segmentation or air-gapped status from the internet."
ASUS security updates: ASUS has released security updates for several router models to allow binding DDNS to a user's account to mitigate the risk of Man-in-the-Middle (MITM) attacks.
Jenkins security updates: Security updates are available for the Jenkins project and some of its plugins, including the GitLab authentication module.
ModSecurity vulnerability: Trustwave researchers have identified a DoS vulnerability (CVE-2023-38285) in the ModSecurity web server security plugin that can be used to disable protection.
Zimbra zero-day patched: Two weeks later, Zimbra has released a patch for a zero-day that was spotted exploited in the wild by Google TAG. The zero-day, an XSS vulnerability, is now tracked as CVE-2023-37580.
Citrix ShareFile exploitation: GreyNoise has seen the first exploitation attempts targeting a recently-patched RCE vulnerability (CVE-2023-24489) in the Citrix ShareFile file-sharing application. While this sounds bad, GreyNoise could not say if the exploitation originated from actual threat actors, researchers, or security firms.
Huawei phone vulnerability: DoyenSec has found a vulnerability in the Huawei phone theme manager that can be exploited to run malicious code on Huawei devices. DoyenSec says they disclosed the issue to Huawei in December 2019 and that despite some fixes Huawei attempted to make in 2021, the issue is still exploitable. Researchers say their exploit is reliable and that exploitation requires only the installation of a malicious theme.
Ubuntu vulnerabilities: Cloud security firm Wiz has discovered two privilege escalation vulnerabilities (CVE-2023-2640 and CVE-2023-32629) in the custom implementation of the OverlayFS filesystem used by the popular Ubuntu OS. Researchers say the vulnerabilities are both easy to exploit using a simple modified binary. Wiz estimates the two vulnerabilities impact roughly 40% of Ubuntu cloud installs.
AWS WAF Bypass: Sicuranext's Andrea Menin has published details on an AWS firewall bypass using Unicode characters inside JSON files.
STIR/SHAKEN compliance in the US: A security firm has filed a complaint with the FCC alleging that most US telcos are using non-compliant STIR/SHAKEN certificates. The FCC mandated that US telcos use the STIR/SHAKEN protocol to combat robocalls in a June 2021 decision. Martini Security says that despite rolling out STIR/SHAKEN infrastructure, most STIR/SHAKEN certificates contain errors and may be exploited to allow robocalls through.
TETRA:BURST vulnerabilities: Kim Zetter has interviewed Brian Murgatroyd, chair of the technical body at ETSI, responsible for developing the TETRA standard. Earlier this week, a team of academics disclosed they found a series of vulnerabilities in the TETRA standard.
"KZ: An intelligence agency isn't going to tell you they're exploiting it.
BM: Yeah, that's true. Although what you've said relates to the algorithm itself, the rest of the protocol is open. So it's only the algorithms themselves [that are secret]. And the vulnerabilities [the researchers found] — apart from [the backdoor in] TEA1 — were all nothing to do with the algorithms. They were all to do with the protocol within the standard…. That's why we changed the standard."
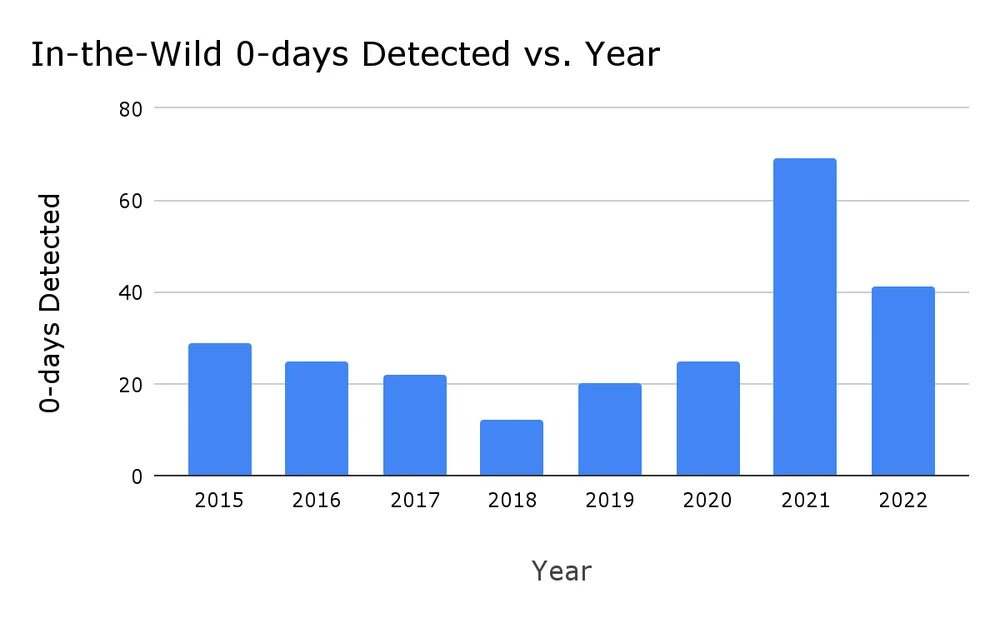
Zero-days in 2022: Google's Project Zero team has observed 41 zero-days being exploited in the wild in 2022, a number considerably below the 69 zero-days it spotted the year before. 40% of the 2022 zero-days were variants of older bugs, with attackers investing time in finding older zero-days that have not been patched properly. Project Zero says it observed several trends, including a drop in zero-days targeting browsers, with attackers moving their efforts to less secure platforms. Google says attackers didn't necessarily need to use Android zero-days last year as many n-days worked as zero-days since many vendors failed to ship security patches in time, leaving their users exposed to old Android vulnerabilities.
Infosec industry
New tool—Testing Handbook: Trail of Bits has released a new tool named the Testing Handbook, a teaching resource for developing automated testing skills.
New tool—Cartographer: NCC has open-sourced a tool named Cartographer, a code coverage mapping plugin for Ghidra.
New tool—BucketLoot: RedHunt Labs has open-sourced a tool named BucketLoot that can automatically scan S3 buckets for security issues.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at when it makes sense for governments to invest in building their own secure phones.