Risky Biz News: SEC expands crypto cyber fraud team
In other news: North Carolina passes law prohibiting ransomware payments; Israel wants a Cyber Dome; and more ransomware gets linked to North Korean state hackers.
This newsletter is brought to you by Airlock Digital, Rumble Network Discovery, Proofpoint, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
The US Securities and Exchange Commission announced on Tuesday that it is expanding its cyber unit with 20 new positions. The unit will also be renamed from the SEC Cyber Unit to the SEC Crypto Assets and Cyber Unit. While its new name implies a new focus on crypto-market fraud, the unit has already been tackling criminal crypto-activity since 2017.
SEC Chair Gary Gensler said the 20 new positions will allow the unit to continue to look at "wrongdoing in the crypto markets" while still being able to investigate cybersecurity cases, as it was initially set up to do.
Per the SEC, the new unit will investigate securities law violations related to stablecoins, DeFi platforms, NFTs, new crypto-asset offerings, cryptocurrency exchanges, and crypto lending and staking products, some of which have been rampant with exit scams and false promises, leading to huge losses among investors.
According to numbers released by the blockchain cybersecurity industry, cryptocurrency platforms and users have lost or been scammed of more than $1.78 billion this year alone.
Breaches and hacks
US DOD BEC scammer convicted: A US man was found guilty of scamming the US Department of Defense out of $23.5 million as part of a BEC scam. According to the US Department of Justice, the suspect phished a government contractor and hijacked DOD payments meant to pay for jet fuel to troops operating in southeast Asia. The man, named Sercan Oyuntur, will be sentenced in June and faces tens of years in prison.
Romanian DDoS arrests: UK officials have detained a Romanian citizen living in the UK for his alleged involvement in a series of DDoS attacks against Romanian government websites over the past weekend. Romanian officials said the suspect provided translation services to Killnet, the pro-Russian hacker group that took responsibility for the attacks. In response to the arrest, Killnet threatened to attack and take down ventilators in hospitals across Romania, Moldova, and the UK.
myNurse shuts down: Healthcare startup myNurse announced it would shut down at the end of the month. The company announced the news in a data breach letter filed with the state of California. While the company said the decision to cease operations was not related to the security incident, the company also didn't deny the impact it had on its business after an intruder managed to steal both personal and healthcare data for its patients.
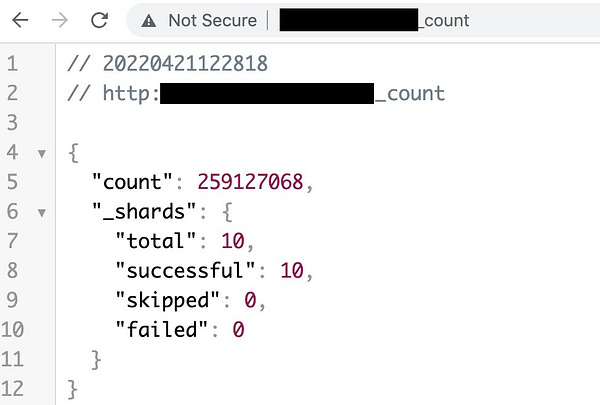
eHospital breach: The Indian government fixed a misconfigured Elasticsearch server that exposed the details of millions of Indians who signed up on its eHospital portal, according to Gadgets360. Security researcher Bob Diachenko discovered the leak and said the exposed database contained 259 million patient records going as far back as 2015.


Crippling cyberattacks: Cyber-attacks have crippled the activities of Onleihe, a popular German online book library service, Sixt, a German car sharing and car rental service, and Massy Stores, Trinidad's largest supermarket chain. The library's catalog has been offline for days; Sixt had to take car reservations using pen and paper on Friday; while several of Massy's stores are still closed following an incident last week. In addition, a ransomware attack has also forced the Kellogg Community College in Michigan to close its university campus and cancel classes on Monday and Tuesday this week.
Gaming cheaters go brr: Gaming cheat maker Aimware was hacked in 2019, and this data has now leaked into the public domain. It was added to Have I Been Pwned this week and will most likely be used to track down cheaters in games like Counter-Strike, Call of Duty, and PUBG.
General tech and privacy
K8s goes to the Sigstore: Kubernetes v1.24 was released this week; the first version of the Kubernetes system that supports Sigstore, a system for cryptographically signing software releases against supply chain attacks.
Better late than never: Heroku said it would begin user password reset operations almost a month after the GitHub OAuth token theft incident.
Government, politics, and policy
NC bans ransom payments: North Carolina has passed a law that has made it illegal for local government entities to pay ransom demands following a ransomware attack. North Carolina becomes the first US state to outlaw ransom payments, with similar bills also in work with officials in Pennsylvania and New York.


FISA stats: The US government said in a report on Friday that the FBI conducted more than 3.4 million warrantless searches of US citizens' data. The searches were allowed under the Foreign Intelligence Surveillance Act (FISA) section 702 and were performed against data collected by the NSA. Sen. Ron Wyden, D-Ore., called the report "meaningless statistics" as the FBI failed to explain the circumstances of these searches and why they jumped to 3.4 million last year from only 1.3 million the year before.
More Pegasus drama in Spain: Spanish officials said on Monday that the cellphones of the country's prime minister and defense minister were infected last year with Pegasus spyware. Prime Minister Pedro Sánchez's mobile phone was breached twice in May 2021, and Defense Minister Margarita Robles' device was targeted once the following month, per the AP. Spanish officials didn't speculate on who was behind the attacks. The revelation comes after a Citizen Lab report accused the Spanish government itself last month of using the Pegasus spyware against Catalonian politicians and activists.
Cyber Dome: The Israeli government is working on new regulations for telecommunication providers in order to improve their resilience against cyber-attacks that may bring down crucial services. Reuters reports the government started working on a so-called Cyber Dome after registering an increase in cyberattacks targeting Israeli companies and government agencies in recent years. It is unclear how this new effort will turn out, if it will be just a series of guidelines or standards, or if the government will get involved in running unified defenses itself.
Cybercrime and threat intel
Sliver usage going up: Team Cymru has published a report on offensive tools developed by the security community that have also been adopted and are being used by threat actors as well. While Cobalt Strike is the leader in this category, Team Cymru noted a spike in the malicious use of Sliver, an adversary emulation framework developed by BishopFox, and another tool similar to Cobalt Strike. Per the researchers, Sliver has often been used in the early stages of attacks and has even been utilized in ransomware delivery mechanisms.
Gmail SMTP relay spam: Email security firm Avanan said that it had seen a spike in April 2022 of threat actors using Gmail's SMTP relay service for their campaigns. The technique has been used often over the past years to send malicious emails from custom domains by routing the emails through a legitimate Gmail SMTP relay, giving the email a reputation boost to pass email security filtering.
DarkFeed drama explained: CyberScoop has more insights into how a threat actor used a Twitter Emergency Data Request (EDR) to discover the real identity of the security researcher behind the DarkFeed ransomware monitoring service. Following initial threats, the researcher shuttered DarkFeed operations and went offline.
North Korean ransomware: Cybersecurity firm Trellix has formally linked four ransomware strains spotted in the wild over the past two years to North Korea's cyber-unit responsible for making money for the regime through cybercrime — namely, Unit 180 of Bureau 121, the country's cyberwarfare agency. The four ransomware strains are named BEAF, PXJ, ChiChi, and ZZZZ. Previous reporting also linked the VHD and Tflower ransomware strains to North Korean state hackers.
Everest going up in the world: Everest, a hack-and-leak group that has been around since late 2020, posted a message on their leak site this week announcing that they are now ready to collaborate with someone skilled in deploying ransomware on the networks they compromise.


Malware technical reports
AvosLocker loves Avast: Trend Micro said that it spotted one of the gangs using the AvosLocker ransomware download and install a version of the Avast Anti-Rootkit driver on systems they have attacked. According to the security firm, the threat actor used this legitimate Avast tool to disable security solutions running on the networks they've compromised. The technique has been previously documented in a report by AON in February 2022. In addition, the same group has been scanning the local networks for systems that, while not publicly exposed, might still be unpatched for the Log4Shell vulnerability as a way to escalate internal access.
Ransomware bugs: Over the past few days, security researcher John Page has published details about vulnerabilities in several ransomware strains such as Conti, REvil, LockBit, AvosLocker, Black Basta, and LokiLocker. Page claims that some of these issues could be used inside ransomware vaccines to stop the ransomware from executing.
IsaacWiper and RansomEx: Cluster25 said it identified a series of code similarities between the RansomEx ransomware and the IsaacWiper used to attack targets in Ukraine during Russia's invasion.
APTs and cyber-espionage
Moshen Dragon: SentinelOne has published a report on a Chinese-aligned threat actor the company is tracking as Moshen Dragon. The company said the threat actor has been active in Central Asia, and every time its attacks were blocked, it abused security software from the likes of Symantec, TrendMicro, BitDefender, McAfee, and Kaspersky to side-load their malware on targeted hosts. In their report, SentinelOne's Joey Chen said that the issue exploited by Moshen Dragon is "an age-old design flaw in the Windows Operating System that allows DLL search order hijacking" and not the fault of the security software makers.
UNC3524: Mandiant has published a report on UNC3524, a newly discovered cyber-espionage group that has been targeting the emails of employees that focus on corporate development, mergers and acquisitions, and large corporate transactions. Mandiant noted that this new threat actor has extremely long dwell times inside breached networks, entered networks via IoT and networking devices, pivoted to email servers, and often re-compromised targets once it was detected and lost access to networks. Despite its corporate targeting, Mandiant said it suspects the group might be espionage-focused and not necessarily financially motivated.
Nobelium: A Recorded Future report published on Tuesday found that the Russian cyber-espionage group Nobelium has carried out a broad spear-phishing campaign in which they used domains mimicking a variety of news and media providers. The technique used in this campaign is known as typosquatting and Recorded Future analysts said Nobelium used domains with misspelled versions of news outlets.
Ukraine is everyone's favorite lure: Google TAG said in a report on Tuesday that government-backed actors from China, Iran, North Korea, and Russia, as well as various unattributed groups, are now using the Ukrainian war as the theme for their phishing operations. A similar trend was also spotted among financially-motivated actors as well.
Vulnerabilities and bug bounty
AWS package backfill attack: Security firm WhiteSource said it detected a "package backfill" attack against official AWS open-source libraries at the end of April. WhiteSource says the threat actor registered two npm JavaScript packages that were loaded inside AWS libraries, but that had since been abandoned and unpublished by their original authors. In two separate incidents, on April 28 and April 30, the threat actor registered packages with the same names and published new versions for the defunct libraries. According to WhiteSource, the two packages contained malicious code that harvested environment details from the developers' machines, most likely in preparation for future attacks.
IoT DNS poisoning: Nozomi Networks have disclosed details about a vulnerability in uClibc, a popular C library used in IoT products from major vendors such as Linksys, Netgear, and Axis. The vulnerability allows DNS poisoning attacks, also impacts the uClibc-ng variation used with OpenWRT. The bug did not receive a patch, despite months of private disclosure.
TLStorm 2.0: IoT security firm Armis has published a report on TLStorm 2.0, a vulnerability in the TLS implementation of the NanoSSL library inside Aruba and Avaya network switches. The vulnerability can be used to break network segmentation, exfiltrate data from internal networks, and escape captive portals. TLStorm 2.0 is a follow-up to the original TLStorm vulnerability, disclosed in March, which impacted the NanoSSL implementation in APC smart UPS devices.



