Risky Biz News: SugarCRM zero-day used to compromise roughly 10% of all internet-accessible servers
In other news: Windows 7 reaches end-of-support; smart ship management platform taken down after hack; Raspberry Robin botnet loses 30% of C2 servers in partial takedown.
This newsletter is brought to you by Airlock Digital, Proofpoint, runZero, and Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed.
Almost 10% of all internet-accessible SugarCRM servers (representing 291 of 3,066 servers, based on Censys data) were hacked and compromised using a zero-day exploit published online in late December.
SugarCRM describes the zero-day as an authentication bypass that allows threat actors to upload encoded images containing malicious PHP code on SugarCRM platforms.
Censys researchers say the final payload in many attacks appears to be a simple web shell that could be used to control compromised systems. According to an open-source report, the zero-day appears to have been used to drop crypto-mining malware as well.
SugarCRM released an official patch a week after public disclosure. The company said that all users who run on-premise servers of its SugarCRM Sell, Serve, Enterprise, Professional, and Ultimate services should apply the update to avoid future attacks.
The company says it has hired a forensics firm to investigate the one-week time window during which its cloud platform was exposed to possible attacks.
No CVE has been assigned to this issue yet.
Breaches and hacks
SF BART ransomware: The San Francisco Bay Area Rapid Transit (BART) is investigating an intrusion of its IT network after the Vice Society ransomware gang claimed to have compromised the agency via a blog post on their dark web leak site. The agency's spokesperson told The Record that "no BART services or internal business systems have been impacted," but they are still looking into claims that data was stolen.
OxShag leak: A dating website named OxShag, which was created by Oxford University students for their fellows, has caused an accidental data leak by exposing everyone's names and university email addresses. According to The Times, OxShag appears to have listed the university's entire email directory for both students and administrators alike. The website was shut down following student complaints.
DNV ShipManager attack: Norweigian company DNV says it had to shut down its ShipManager smart ship management platform in the aftermath of a cyberattack that took place last Saturday. DNV said ShipManager would work in offline mode while they investigate the incident together with the Norwegian police. The ShipManager platform, which allows maritime companies to manage ship fleets, their crew, maintenance, procurement, cargo, and other analytics, is currently used by more than 300 maritime companies and installed on more than 7,000 vessels.
General tech and privacy
Cryptome suspension: Twitter has permanently suspended the account of Cryptome.org, a leak site known for publishing leaks of sensitive documents from across the world. The last files published on the site before the suspension are documents claiming to contain Donald and Melania Trump's tax returns.
Windows 7 end of extended support: As of January 10, 2023, the Microsoft Windows 7 and Windows 8.1 operating systems have formally reached their end of extended support. Both operating systems previously reached their end of life for home users in January 2020, after which point only selected corporate customers were eligible for additional security updates under a commercial plan. These updates will stop this week. Other Microsoft products that also reached their end of support this Tuesday also include Visual Studio 2012 and the Windows RT and Windows Server 2008 operating systems, among many others.
Government, politics, and policy
DDoS attacks on Serbian govt: The Serbian government says it mitigated a two-day-long DDOS attack that hit several of its official websites and IT infrastructure. No group has yet to claim the attacks.
Malta drops Huawei CCTV project: The Maltese government will abandon its joint project with Huawei to implement a facial recognition-based CCTV system across some of its urban areas. Named Safe City Malta, the project was announced in 2018 and was initially deployed in 2019 in two cities—Paceville and Marsa. After years of criticism from privacy advocates, earlier this week, the Maltese government chose not to extend Huawei's contract and let the project lapse.
DNS4EU: Czech cybersecurity company Whalebone has been selected to build DNS4EU, a public DNS service for the European Union, its agencies, and citizens. Whalebone will lead a consortium of 13 companies based across 10 EU countries. Members include universities, national CERT teams, and other private companies. The project was first announced in January last year. A recording of the press conference and the consortium's plans is embedded below.
US Supreme Court denies NSO Group: The US Supreme Court has declined to hear a petition brought by infamous Israeli spyware vendor NSO Group related to its WhatsApp lawsuit. Meta sued NSO Group in 2019 after the company created and sold an exploit that was used to hack the smartphones of tens of WhatsApp users across the globe. Meta asked a US court for an injunction banning NSO Group from developing future exploits. As part of its legal defense, NSO argued that it was entitled to "sovereign immunity" because the exploit was bought and used by foreign governments that had the authority to use such tools. Lower US courts declined NSO's petition and request for "sovereign immunity," and with the Supreme Court ruling the same, the case is now free to move forward. According to the Knight Institute at Columbia University, the decision clears the path for lawsuits by journalists and activists.
DOI password audit: The Inspector General at the Office of the Interior carried out a security audit of the password management policies used inside the US Department of the Interior. In a report [PDF] published last week, officials said they were able to crack more than 18,000 of the department's AD accounts, representing 21% of the department's entire userbase. Officials said the DOI failed to enforce password complexity requirements, failed to protect 89% of high-value accounts with a form of multi-factor authentication, failed to enforce password age limits, failed to enforce password reuse policies, and also failed to deactivate inactive accounts.
Sponsor section
RunZero is one of this newsletter's four main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network. To learn more, please check out this runZero product demo below:
Cybercrime and threat intel
Auction site scammer sentenced: A Romanian national was sentenced to 89 months in prison for his role in a large cybercrime gang that defrauded Americans. The group operated by using stolen identities to create accounts on popular online auction sites, such as eBay, where they posted ads for non-existing goods, and then laundered their ill-gotten funds through cryptocurrency. The man is the fifth member of the gang to plead guilty and receive a long prison sentence. Four other Romanian nationals also previously received prison sentences between 61 and 70 months last year, according to the DOJ.
New npm malware: Fourty-seven new malicious npm packages spotted. Check out GitHub's security advisory portal for details.
Dark web drug markets: Threat intel company Resecurity says that at least seven dark web marketplaces dedicated to the drug trade have recently released Android apps as a new way for their customers to place orders on their sites. Marketplaces that now run Android apps include the likes of Yakudza, TomFord24, 24Deluxe, PNTS32, Flakka24, 24Cana, and Maps TGK.
ScrubCrypt: Perception Point researchers say they discovered a new crypter service named ScrubCrypt. The service is currently being advertised on underground hacking forums and has already been used in the wild to mask the Xworm RAT in recent phishing campaigns.
Godfather in Germany: BaFin, Germany's financial sector regulator, published a public service announcement on Monday warning of attacks carried out with a new strain of malware known as Godfather. First described in a report from Group-IB last year, Godfather is a banking trojan that targets Android devices and which contains functionality to target more than 400 mobile banking and cryptocurrency applications.
Lorenz ransomware update: Security firm S-RM says it is seeing the Lorenz ransomware gang access backdoors planted on Mitel VoIP servers months before in order to launch attacks on companies that failed to detect the initial intrusions. All systems appear to have been compromised via a Mitel zero-day (CVE-2022-29499) that was disclosed last April and which the Lorenz gang is known to have abused in previous months, per reports from Arctic Wolf and Crowdstrike.
Kinsing attacks: Microsoft has published a report that takes a deep look at the techniques used by the Kinsing cryptomining botnet to breach Kubernetes clusters. According to Microsoft, Kinsing operators preferred two methods. The first targets outdated server images that come pre-packaged with vulnerable applications. The second method targeted Kubernetes clusters that ran misconfigured PostgreSQL databases.
Malware technical reports
URSNIF: The fantastic team at the DFIR Report has published a new report that goes into the finer details of a URSNIF attack. The intrusion started with an ISO file and ended six days later after the attackers extracted access credentials from the company's network. According to the DFIR Report team, "the threat actor was able to RDP to a backup server using the admin credentials they acquired."
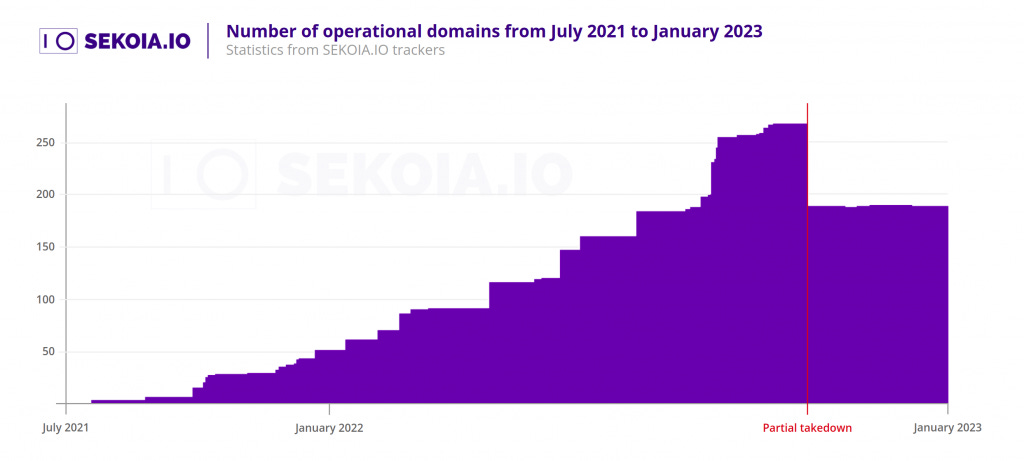
Raspberry Robin partial takedown: Cybersecurity firm Sekoia says the Raspberry Robin lost 80 (30%) of its command and control (C&C) servers in October last year as part of a partial takedown operation. The company's report takes a look at how the botnet's operators reacted after losing a large chunk of their servers.
"These domains had their DNS zone deleted and the tags clientHold, clientTransferProhibited were added to their status codes, leading to a total loss by the botnet operators."
APTs and cyber-espionage
PlugX analysis: Malware researcher Tìm Kiếm has published a technical analysis of a recently discovered PlugX malware sample. The malware is typically used by Chinese APTs, but Kiếm makes no formal attribution.
Hive's XDR33 variant: Netlab, the network security division of Chinese security firm Qihoo 360, says it discovered a new malware strain named XDR33 that appears to be a new variation of Hive, a malware control framework supposedly developed by the CIA. Hive is one of the tools that had its documentation leaked by WikiLeaks in 2017 as part of the Vault7 collection. Netlab researchers said they discovered the XDR33 variant last year in October being deployed on F5 devices, where the malware would act as a backdoor. Netlab says this is the first time they found a variant of the CIA Hive malware kit in the wild. Netlab didn't attribute XDR33 and the recent attacks to the CIA, at least, not yet. The report comes after China's CERT agency issued an alert in April last year about attacks carried out with the CIA's Hive malware—attacks which they directly attributed to the CIA.
StrongPity APT: ESET researchers have uncovered a new operation carried out by the StrongPity APT where the group created a website that impersonated Shagle, a video chat service that lets users have encrypted video chats with random strangers. ESET says StrongPity's goal was to get users to download and install an Android app that was a modified version of the open-source Telegram app, repackaged with one of the group's backdoors.
Vulnerabilities and bug bounty
Threema vulnerabilities: A team of academics from the ETH Zurich University has published a technical paper on a series of vulnerabilities in Threema, a secure end-to-end encrypted messaging service that bills itself as a Signal and WhatsApp alternative. The seven vulnerabilities can allow a threat actor to impersonate a user, gain access to Threema servers, and gain access to Threema data on an unlocked device. Responding to the research, Threema said the vulnerabilities impact an older version of its protocol "that is no longer in use." The company's response turned out to be both dismissive and misleading and the research team said their work is what forced the company to update to its curent and a newer protocol.
$1 million bounty: A security researcher was awarded a $1 million bug bounty reward after discovering and reporting a vulnerability that impacted three parachains running on the Polkadot blockchain, namely the Moonbeam, Astar Network, and Acala projects. According to cryptocurrency news outlet The Block, the researcher said that if the vulnerability had been exploited in the wild, an attacker could have stolen as much as $200 million worth of crypto-assets from the three projects.
Experian website bug: Credit reporting agency Experian has patched a bug in its website that allowed identity thieves to view credit reports and the personal details of any of the company's customers. The bug was super simple to exploit and consisted of replacing a part of the Experian website URL in the security questions page (/acr/oow/ with /acr/report/). According to KrebsOnSecurity, the issue was discovered last year by a Ukrainian security researcher who saw it mentioned on Telegram channels dedicated to online fraud.
Taking over a dead IoT company: Security researcher Kevin Chung has taken over an old domain used by NYCTrainSign, a now-defunct company that sold displays that show the time until a certain NYC train would hit a certain train station. Chung also wrote an exploit that allowed him to get full control of any signs still in the field.
CVE-2022-23529: Palo Alto Networks researchers have discovered a vulnerability in the JsonWebToken open-source project that can be used to achieve remote code execution (RCE) on a server verifying a maliciously crafted JSON web token (JWT) request.
CVE-2022-43974: Deutsche Telekom security researcher Alissar Ibrahim has published details [PDF] about a critical buffer overflow vulnerability in the MatrixSSL library. Ibrahim says the issue can allow an attacker to overwrite a large part of a server's RAM and lead to remote code execution. The issue was fixed with the release of MatrixSSL 4.6.0 last month.
Asus router vulnerabilities: Asus has patched a set of three vulnerabilities that can be used to bypass authentication in some of its newer router models and take over devices. Details are available via Cisco Talos.
Siemens PLC vulnerabilities: Red Balloon researchers have discovered a series of vulnerabilities in the firmware of Siemens SIMATIC and SIPLUS S7-1500 Series PLC devices, commonly deployed in industrial networks. Researchers say the vulnerabilities can allow attackers to bypass all protected boot features, resulting in persistent arbitrary modification of operating code and data on vulnerable PLCs. Red Balloon described the issues as "architectural vulnerabilities," meaning they can't be patched at a software level. Siemens has published recommendations for its users regarding workarounds and mitigations [PDF].
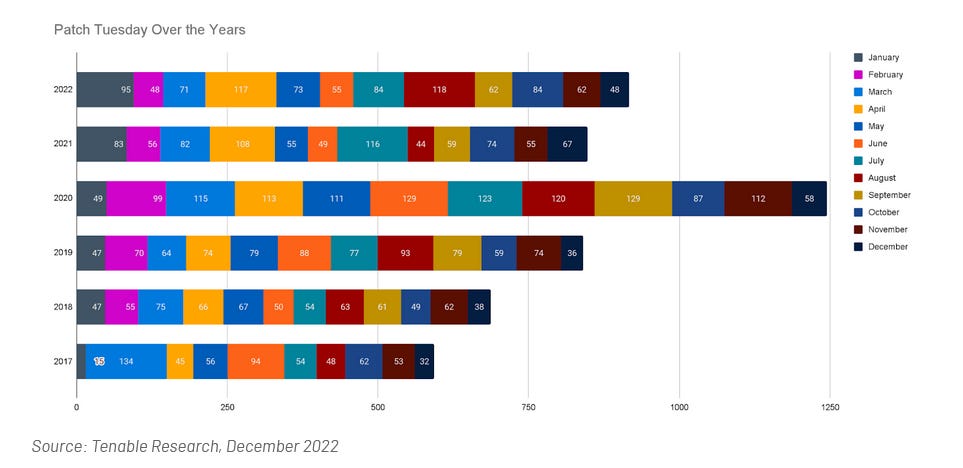
Patch Tuesday: Yesterday was also this year's first Patch Tuesday. We had security updates being released by Adobe, Microsoft, and SAP. Zoom, Lenovo, and the Android project released security updates last week as well. This month, Microsoft patched 98 vulnerabilities, including an actively exploited zero-day (CVE-2023-21674). On the same topic, vulnerability management company Tenable also published a blog post delving into the history and evolution of Microsoft Patch Tuesday security updates over the past few years.
Infosec industry
New tool—ImageMagick Security Policy Scanner: DoyenSec has open-sourced the code of a new web-based tool named ImageMagick Security Policy Scanner, which, as it name implies, can scan and detect misconfigurations in ImageMagick library configs.
New tool—cobalt-strike-stager-parser: Security firm Stairwell has open-sourced this week a new tool that can decode Cobalt Strike staging shellcode.
Red Hat Insights: Red Hat has formally launched Red Hat Insights, a malware detection service for RHEL systems.
Risky Business podcast host Patrick Gray recorded this video with Okta, which shows users how to enable phishing-resistant authentication. It also goes into how enabling phishing-resistant auth for some users can benefit the whole org, even if it's not turned on everywhere.