Risky Biz News: US and Canada warn of new Truebot malware variant
In other news: Ransomware cripples Japan's largest cargo port; OPERA1ER member arrested in the Ivory Coast; and new StackRot vulnerability fixed in the Linux kernel.
This newsletter is brought to you by asset inventory and network visibility company runZero. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
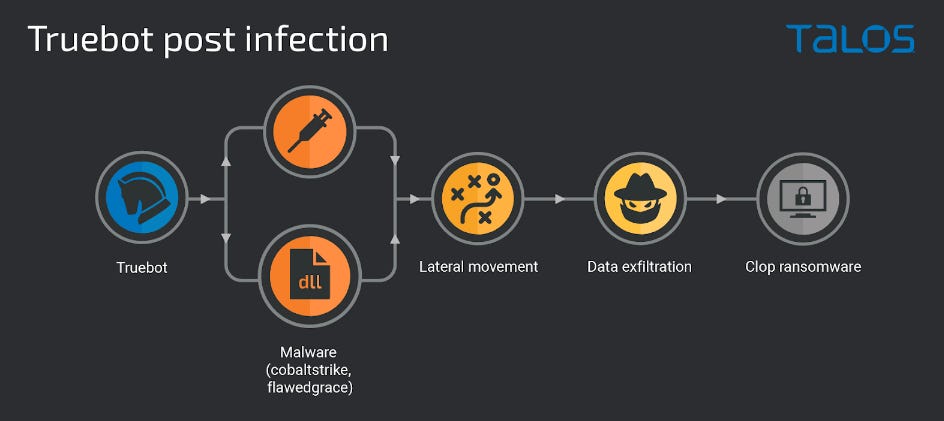
Cybersecurity agencies from the US and Canada have issued a joint security alert and are warning about malicious campaigns spreading new versions of the Truebot malware.
First spotted way back in 2017, Truebot is a malware downloader that was created and is operated by Silence, a financially motivated cybercrime crew. It is typically used as an initial infection point through which second-stage payloads are delivered on compromised hosts.
According to US and Canadian officials, new versions of the Truebot malware are currently being distributed through phishing campaigns containing malicious redirect hyperlinks.
In addition, the Silence gang is installing Truebot on systems they previously compromised by exploiting an RCE in the Netwrix Auditor software (CVE-2022-31199).
Officials say the vast majority of this activity has targeted organizations in North America. They have now released IOCs and detection rules so companies can protect themselves against the new activity.
The joint alert was issued by the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS).
It should not be taken lightly. Throughout 2022, the Clop cybercrime cartel has used the Silence gang's network of Truebot-compromised systems to gain access to corporate and government networks, steal enterprise data, and deploy its eponymous Clop ransomware. Yes—the gang behind the recent MOVEit and GoAnywhere exploitation waves. That gang!
Breaches, hacks, and security incidents
Nagoya port ransomware attack: A ransomware attack has crippled the operations of Japan's largest cargo port for two days this week. The incident brought down the terminal management system at the port of Nagayo. Cargo loading and unloading stopped all day on July 4 and 5 before systems were restored. Toyota, which is the port's primary customer, says the incident did not impact its production and supply chain. The attack was claimed by the LockBit ransomware gang. [Additional coverage in Japan Times and Piyolog]
RZD incident: The IT Army of Ukraine has taken credit for a series of DDoS attacks that have brought down the apps and website of Russian state-owned railway company RZD. The apps and websites were down for only six hours, during which time passengers couldn't make reservations or buy tickets online. [Additional coverage in RBC; English coverage in The Record]
JumpCloud incident: Cloud hosting provider JumpCloud has invalidated all API keys and has asked customers to generate new ones. The company cited an "ongoing incident."
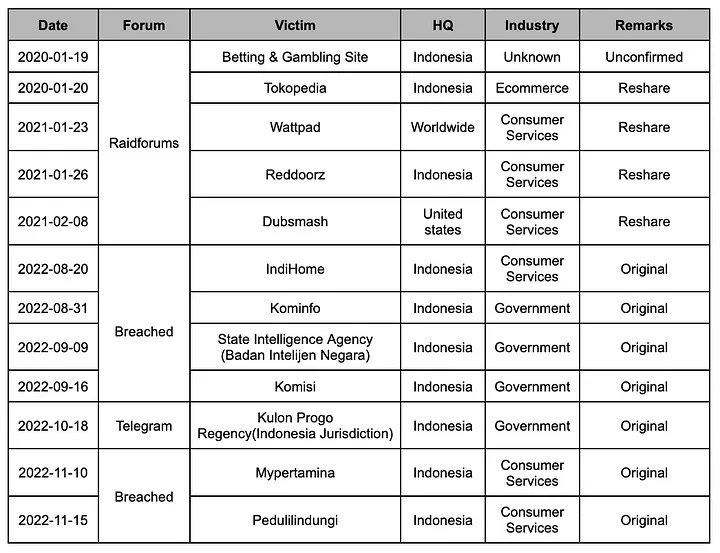
Indonesian passports leak: A threat actor named Bjorka is selling the passport details of 34 million Indonesians. Information from one million passports was published online as proof, while the rest is being sold for $10,000. Indonesian officials have yet to confirm the breach, but the leak was confirmed to be authentic by multiple Indonesian security researchers. The same hacker is also selling the personal details of 35 million of myIndieHome ISP customers. The threat actor behind the hack has a long history of hacking and leaking data from Indonesian organizations. Past victims include Indonesian gambling sites, the Indonesian State Intelligence Agency (BIN), and Tokopedia, Indonesia's largest e-commerce company.
General tech and privacy
Can't delete Threads account: Meta has confirmed that users who sign up for its new Twitter-alternative project named Instagram Threads will not be able to delete their account once they signed-up. Users will only be able to disable their Threads account. The only way to delete a threads account is to delete the associated Instagram account, something that new users might not be willing to do. [Additional coverage in TechCrunch]
Secret Firefox blocklist: The recently launched Firefox v115 contains a secret feature that allows Mozilla developers to disable any extension on any website inside their users' browsers. Developers say this is for "security concerns." Let's just say that this vague explanation is not sitting well with many of Firefox's users.
Government, politics, and policy
National Cyber Director: A GAO report has advised the White House to fill the role of National Cyber Director, which it views as a key figure in implementing the administration's recent National Cybersecurity Strategy.
RuNet test: Russian authorities disconnected the country from the global internet on the night between July 4 and 5. Authorities say the disconnection was an exercise meant to test the stability of the RuNet, the country's portion of the internet. A Roskomnadzor representative said the disconnect was mandated by law, with the agency and ISPs needing to test the RuNet's ability to function without connection to the external internet once per year. Despite this, there's reporting that the disconnect might have never happened. [Additional coverage in RBC]
Sponsor section
This week's sponsor is RunZero. In this Risky Business News sponsor interview, Tom Uren talks to RunZero's CEO Chris Kirsch about how the company has evolved from offering an active scanning product to one that can now discover assets on OT and cloud environments using both active and passive scanning approaches:
Cybercrime and threat intel
OPERA1ER member detained: Authorities in the Ivory Coast have arrested a man suspected of being a member of a large cybercrime cartel known as OPERA1ER. The man is the first suspect to be detained in connection to the gang, one of the few cybercrime groups to repeatedly target African countries. Also known as the DESKTOP Group and Common Raven, the group has been active since 2019 and is believed to have stolen between $11 million and $30 million in more than 30 attacks. Most of the victims are African banks and financial services. The suspect was detained following a joint investigation between Interpol and security firm Group-IB, which has been tracking the group for two years.
Russian sentenced to prison for pro-Ukraine DDoS: A Russian court has sentenced [cached] IT specialist Bayandin I.M. to two years in prison for carrying out DDoS attacks against the websites of Russian banks, telcos, and energy companies. The court says Bayandin carried out the attacks as a way to show his disapproval of Russia's military operation in Ukraine. Bayandin becomes the second IT expert sentenced to prison for DDoSing Russian websites following the country's invasion of Ukraine. An IT expert named Yevgeny Kotikov was sentenced to three years in prison last month for participating in DDoS attacks against Russian sites organized by pro-Ukraine hacktivists. [h/t Oleg Shakirov]
Nigerian hackers detained: Nigerian police have detained two individuals suspected of hacking and stealing money from more than 1,000 bank accounts. The two suspects, aged 40 and 50, were detained following a complaint from the United Bank for Africa. [Additional coverage in PMNews]
FBI's Hive hack: Politico's John Sakellariadis has a long read on how the FBI hacked the Hive ransomware's control panel.
SiegedSec: Chinese security firm OTS Security has a profile on the SiegedSec hacktivist group.
Honeypot experiment: A six-month experiment carried out by Trustwave's SpiderLabs has found that 19% of traffic that hit a test honeypot network was malicious in nature. Of all the malicious traffic, 95% came from IoT botnets trying to exploit new devices.
Operation Brainleeches: ReversingLabs has discovered more than a dozen malicious npm packages that contain malicious code to harvest credentials from apps where their code was included. Researchers believe the libraries might have also been used to phish Microsoft accounts because they also contained files to show phony Microsoft.com login forms. The packages have now been removed from the npm portal, but they were live for almost a month and downloaded more than 1,000 times in total.
Spyware on the Play Store: Pradeo has identified two malicious Android apps on the official Google Play Store that contain spyware behavior. The two apps were published by the same developer, both pose as file managers, and were downloaded more than 1.5 million times. Pradeo says the apps start without any user interaction and collect and exfiltrate local data to servers located in China. Stolen information includes contact lists, real-time user location, multimedia files, and local network and OS details. Both apps are still available on the Play Store.
Malware technical reports
TeamTNT Silentbob: Aqua Security has a report out on a suspected TeamTNT operation named Silentbob where the gang is deploying an aggressive worm against cloud infrastructure. Aqua says the worm targets JupyterLab and Docker APIs in order to deploy a version of the Tsunami backdoor malware, scripts to hijack cloud account credentials, and the gang's usual cryptominer.
AgentTesla: SonicWall researchers have a report on a recent NativeLoader-AgentTesla campaign.
WhiteSnake Stealer: eSentire researcher RussianPanda has published an analysis of the WhiteSnake Stealer, an infostealer advertised on underground forums since February 2022. Nothing special about it. Just your regular modern infostealer.
WISE REMOTE Stealer: CyFirma has discovered a new infostealer named WISE REMOTE that is currently advertised in underground hacking forums. WISE is your typical infostealer, with features to allow it to collect and exfil a bunch of data from infected hosts. All the data is sent to a remote control panel, ready to be re-packaged and sold on underground credential markets by attackers.
BlackByte ransomware: Microsoft has published a report from a recent BlackByte ransomware IR/intrusion. Enjoy the IOCs!
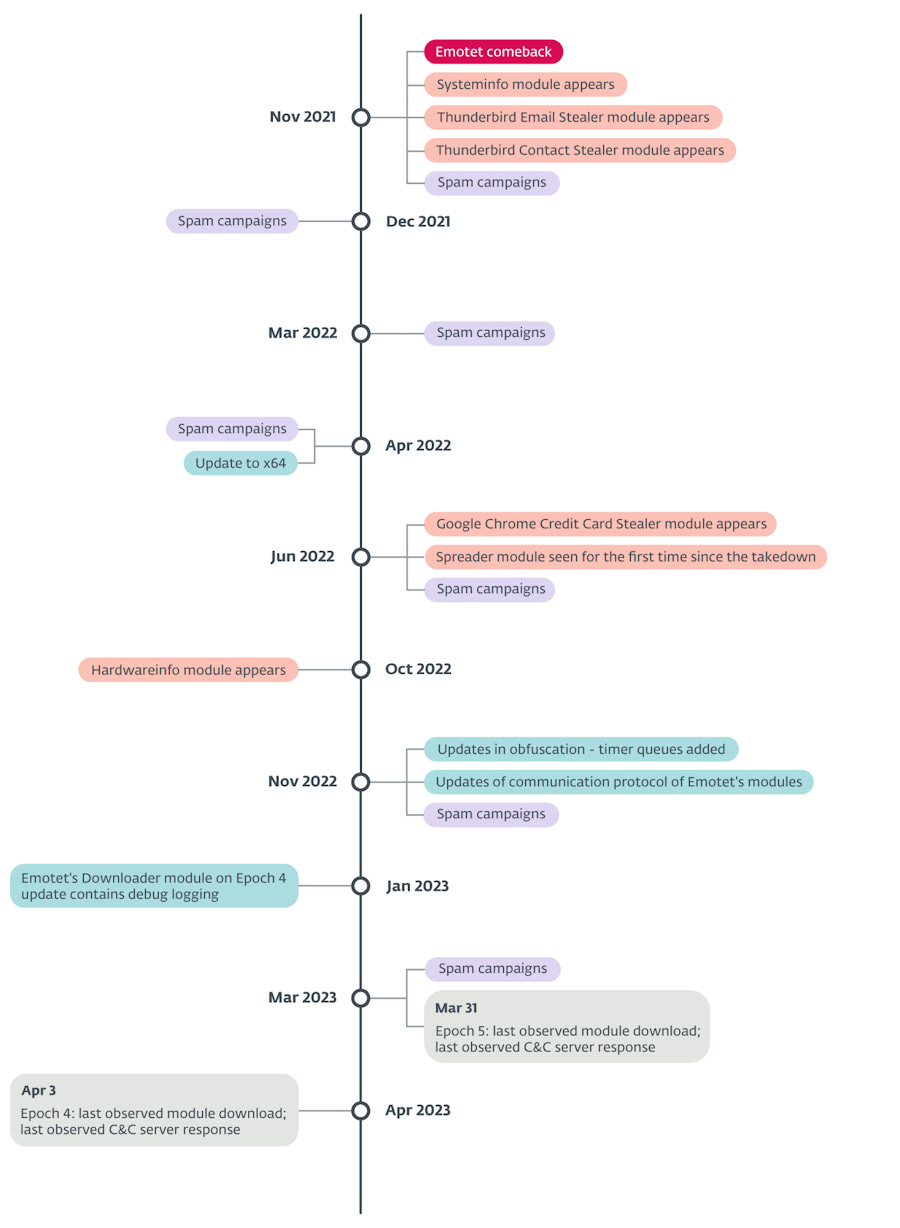
Emotet: Cybersecurity firm ESET says the Emotet botnet appears to have entered another dormancy period, with no activity being detected from its servers since April this year. The company's researchers believe the botnet is down "most probably due to failing to find an effective, new attack vector." They also suspect the botnet might have been sold to a new operator in January this year, although this is an unconfirmed rumor.
Sponsor Demo
RunZero is one of this newsletter's main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network, including OT devices in critical environments. To learn more, please check out this runZero product demo below:
APTs and cyber-espionage
TA453 (Charming Kitten): Proofpoint has a report on TA453's recent campaigns using LNK infection chains instead of Microsoft Word documents with macros. The report also covers the group's recent macOS malware arsenal. Proofpoint says it worked with Dropbox to take down some of the group's infrastructure. The campaign appears to be targeting nuclear security experts.
Vulnerabilities, security research, and bug bounty
SolarView attacks: Hundreds of SolarView solar panel management installations are exposed on the internet and unpatched to an actively exploited vulnerability. The software is typically used by energy companies and solar farms to manage solar panels in remote areas. Since March, SolarView web panels have been targeted by a Mirai IoT botnet, which has used the compromised panels to launch DDoS attacks. Security firm VulnCheck says that of the 600 SolarView systems currently exposed on the internet, around 400 are versions vulnerable to attacks.
StackRot: Chinese security researcher Ruihan Li has discovered a privilege escalation vulnerability in the Linux kernel. Named StackRot (CVE-2023-3269), the vulnerability originates in the kernel's virtual memory management subsystem and allows attackers to run code as root. Li says the process of addressing the StackRot bug was led by Linus Torvalds himself and took two weeks due to the patch's complexity. The vulnerability is the first-of-its-kind—an use-after-free via RCU calls.
Smart lightbulb collects your GPS: A security researcher known as HaxRob has discovered that the mobile app used by Arlec's smart lightbulbs secretly collects their users' GPS coordinates. The app has been installed more than 500,000 times.
Android Security Bulletin: AndroidOS security updates for July 2023 are out. Google says that three of the vulnerabilities patched this month were actively exploited in the wild. The CVEs are CVE-2021-29256, CVE-2023-2136, and CVE-2023-26083.
Cisco security updates: Cisco has released four security updates. One of them—CVE-2023-20185—is pretty bad as it allows "unauthenticated, remote attacker to read or modify intersite encrypted traffic." Cisco has declined to patch it as it impacts its old line of Nexus 9000 series of data center switches, and is asking customers to disable the module impacted by this vulnerability and use another alternative.
Infosec industry
New tool—Flutter Restrictions Bypass: CyberCX researchers have published a tool that bypasses root and jailbreak security checks performed inside Flutter-based apps. These security checks allow Flutter apps to detect potentially compromised devices and protect user data. The tool allows security researchers to bypass these detections for the purpose of security audits on Flutter-based apps.
New tool—Cyber Crisis Management: France's ANSSI cybersecurity agency has released "Cyber Crisis Management," a collection of guides and questionnaires to allow companies to self-assess their cybersecurity posture and preparedness.
"This tool offers a series of 57 questions, spread over 5 themes: governance and interactions between mobilized teams, processes and tools, crisis communication and external relations, incident detection and response, business continuity and reconstruction. For each question, a series of progressive answers allow a positioning between a novice level (0) and at the state of the art (3). It can be used as part of a quick assessment or as part of a more comprehensive audit, depending on individual needs."
Sleuthcon 2023 videos: Talks from the Sleuthcon 2023 security conference, which took place back in May, are now available on YouTube.
BlackHat keynote: Maria "Azeria" Markstedter will keynote this year's Black Hat USA security conference.
Romanian infosec journalists: Cynthia Brumfield over at Metacurity has a long read on why there are so many Romanian infosec journalists around right now (yours truly included).
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at the EU's proposed media freedom act and how one of its goals is to protect journalists from spyware.