Risky Biz News: US charges and sanctions WazaWaka
In other news: Turkish opposition media hit by DDoS attacks on election day; DoD embraces Microsoft Defender; and a new Chinese APT backdoors TP-Link routers in Europe.
This newsletter is brought to you by Proofpoint. You can subscribe to a podcast version of this newsletter by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Click below for today’s edition on Apple Podcasts:
The US Justice Department has charged a Russian national named Mikhail Pavlovich Matveev for a series of ransomware attacks across the US, including two attacks against police departments.
Matveev is widely known in infosec circles under his hacker pseudonym of WazaWaka. He has also gone on underground forums under many other nicknames, such as Boriselcin, KAJIT, M1x, Orange, and Uhodiransomwar.
He is a known initial access broker and a former affiliate for ransomware gangs such as Babuk, Conti, Darkside, Hive, and LockBit. He is also one of the founders of RAMP, a notorious dark web cybercrime forum that launched in the spring of 2021.
US officials say that while he was part of the Babuk, Hive, and LockBit gangs, Matveev carried out numerous attacks against US organizations, including hospitals, police departments, and airlines.
But by far, Matveev's most notorious attack—and the case that most likely started an investigation into his criminal spree—was the intrusion he executed while part of the Babuk gang against the Metropolitan Police Department of the District of Columbia.
In a brazen move, Matveev asked for a $4 million ransom payment, threatening the DC Metro PD with leaking sensitive files that would expose police investigations and their informants.
The DC Metro PD intrusion received international coverage around the world and brought too much heat on the Babuk RaaS, which eventually closed shop just days later. In hindsight, the failed DC Metro PD attack was one of those milestone incidents in the history of infosec. The Babuk gang not only shut down operations but also released the source code of their ransomware, which has since been adopted and abused by several ransomware gangs—creating a string of problems for cybersecurity firms ever since (but that's another discussion).
But before today's formal indictment, Matveev's identity was not a secret.
He was doxed by infosec reporter Brian Krebs in a January 2022 article and then famously had a public breakdown a month later, confirming Krebs' reporting.
In an interview with The Record, Matveev also famously stated that there is no other part of the cybercrime ecosystem that makes as much money as ransomware.
But he won't get to enjoy most of the money he made. Besides the indictment unsealed by the DOJ today, the US Treasury Department has also added Matveev to their sanctions list, and the US State Department is now offering a $10 million reward for any information leading to his arrest. He is now also listed on the FBI's Cyber Most Wanted website.
Breaches and hacks
Polish government breach: Polish reporters say they found a working password inside an inbox dump belonging to Polish government official Michał Dworczyk. Reporters say that although the email was from 2020, the password still worked and granted access to a government system that contained national security information, such as a detailed map of the military port in Gdynia, an evacuation plan for the city of Warsaw, and maps of Poland with military overlays. The official's email inbox was leaked on a Telegram channel and initially originated from a 2021 hack that Polish officials attributed to Russian hackers. [Additional coverage in OKO]
Philadelphia Inquirer cyberattack: The Philadelphia Inquirer was unable to print the Sunday and Monday editions of its newspaper after the company fell victim to a cyberattack over the weekend. The company says it discovered the attack on Saturday when one of its employees couldn't access the organization's CMS backend. While all signs point to this being another ransomware attack, the paper has yet to confirm it. The Inquirer says the incident is the largest disruption to its operations since a major blizzard prevented it from printing its newspaper for two days back in January 1996. The disruption also comes just days before Philadelphia's mayoral primary election that took place on Tuesday.
Iron Dome "hack": The Time of Israel published an analysis of the wild claims made by the Anonymous Sudan group earlier this month that they hacked Israel's Iron Dome anti-missile defense system. Officials call the execution of the hack "comically poor" but warn against future collaborations between pro-Kremlin and Iranian hackers, with Iran appearing to abandon "red lines."
Turkish media DDoS attacks: Three Turkish media outlets associated with the country's opposition parties say they've been hit with cyberattacks on the day of the Turkish presidential election. Television channel Halk TV and newspapers Sözcü and Cumhuriyet reported DDoS attacks on their websites. The incidents came at the same time the Turkish government asked Twitter to censor accounts for several opponents right before the election, a request Twitter gladly followed through, unlike others.
China Daily News ransomware attack: Threat intel analyst Dominic Alvieri has spotted that the LockBit ransomware claimed to have breached China Daily News, an online news outlet owned by the Propaganda Department of the Chinese Communist Party.
SchoolDude breach: Brightly Software is notifying almost three million users that their personal information has been stolen in a security breach of SchoolDude, a web platform for managing educational institutions. Stolen data includes names, emails, passwords, phone number, and school district information.
General tech and privacy
WhatsApp Chat Lock: Meta has added a new feature to WhatsApp named Chat Lock that allows users to lock certain conversation threads under a device's password or biometric authentication. Meta says new messages that arrive in a locked chat will also have their notification anonymized to protect the user's privacy.
Black Sea internet cable: The EU plans to lay an internet cable through the Black Sea connecting Georgia to Bulgaria to reduce Europe's dependence on internet connections that pass through Russia. The move comes as the US, the UK, and the EU have expressed global concerns over possible Russian spying and sabotage in the case of a conflict. A joint investigation by public broadcasters in Denmark, Norway, Sweden, and Finland claimed last month that Russia is operating a fleet of vessels disguised as fishing trawlers in the North Sea that carry underwater surveillance equipment and are mapping key sites for possible sabotage. [Additional coverage in the Financial Times/non-paywall]
AppStore fraud numbers: Apple says it blocked nearly 3.9 million stolen credit cards from being used to make fraudulent purchases on App Store in 2022. The company says it blocked more than $2 billion in fraudulent transactions throughout 2022 and banned 714,000 accounts from its transactions system. In terms of abusive apps, Apple says it rejected more than 153,000 app submissions for spam, content theft, and misleading descriptions. In addition, Apple also removed more than 147 million ratings and reviews from the App Store last year that it deemed inauthentic and made through automated accounts.
Government, politics, and policy
Ransomware in Belgium: Belgium's Center for Cyber Security says that 97 local organizations reported successful or unsuccessful ransomware attacks last year. This number will most likely be beaten in 2023, with 27 attacks already reported in the first three months of the year. [Additional coverage in VRT]
Investigation into Chinese cranes: The Dutch government has announced an investigation of Chinese cranes installed in Dutch ports. The investigation comes after reports from US intelligence that China may use software installed on the cranes to collect data on the movement of goods and military equipment through Western ports.
ECCC launches: The European Cybersecurity Competence Centre formally opened its doors and began operations last week in Bucharest, Romania. The ECCC was established in 2020 as an EU agency specializing in cybersecurity research. The agency operates independently from ENISA and CERT-EU and is primarily tasked with providing financial support and technical assistance to cybersecurity start-ups and SMBs and promoting cyber-security standards. The ECCC's official headquarters are now located on the campus of the Polytechnic University of Bucharest. (h/t Ravi Nayyar)
DOD expeditionary cyberspace operations: The US Department of Defense has formally acknowledged and defined the concept of "expeditionary cyberspace operations." The term refers to deploying military and intelligence assets in the field to conduct a cyberspace operation closer to the target. Such operations have obviously taken place already, but this marks the first time the DOD updates military doctrine to account for cyber's increasing role in modern battlefields. [Additional coverage in DefenseScoop/Army.mil]
DoD embraces Microsoft Defender: The US Department of Defense will replace existing endpoint security agents with Microsoft Defender, according to a report from Newsweek. Newsweek claims the DoD has pushed the move despite opposition from senior IT leaders in its military services. Unnamed DoD IT staff quoted in the report claim the move will make the Defense Department overly reliant on a single vendor. [Additional coverage in Newsweek]
Sponsor section
Proofpoint, this week's sponsor, has recently published the 2023 edition of Voice of the CISO, a yearly report featuring insights and experiences from more than 1,600 CISOs from around the world. The report covers recent threat actor trends, insights into better defenses, and the latest dynamics in board-CISO relations.
Cybercrime and threat intel
Influencer charged with romance scams: US authorities charged a famous Ghanaian Instagram influencer for her role in a cybercrime operation. Officials say that Mona Faiz Montrage, 30, of Accra, Ghana, partook in several romance scam operations between 2013 and 2019. The scams targeted elderly individuals, and Montrage and her accomplices made and laundered more than $2 million from the scheme. Montrage was arrested in the UK in November 2022 and was extradited to the US last week to face charges. Before her arrest, Montrage also managed to rise to fame as Instagram influencer "Hajia4Reall," amassing more than 3.4 million followers on the site and becoming one of Ghana's most followed Instagram profiles.
NSO Group update: OpenSecrets says the NSO Group has recruited a considerable lobby force to get the US to remove the company from its sanctions list.
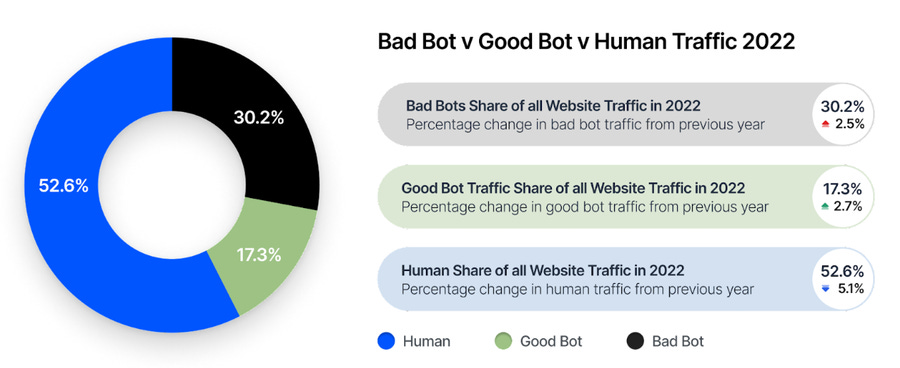
Bot traffic: Imperva says that roughly 47.4% of internet traffic it analyzed last year came from bot networks, a percentage that is up 5.1% from the previous year. Of these, Imperva says that roughly 30% was "bad bots" used for various forms of automated attacks.
Infostealer market: Both KELA and Secureworks have put out reports on the current infostealer market, the top shops, and the most active strains.
WordPress exploitation: Akamai says that two days after a Patchwork researcher discovered an XSS vulnerability in the Advanced Custom Fields WordPress plugin, threat actors were already scanning the internet for vulnerable sites. The company described the activity as "significant." According to Akamai, the first attacks started less than 24 hours after Patchwork's disclosure and used the sample exploit code from the company's technical write-up. Roughly 70% of WordPress sites using the plugin are still running an old vulnerable version, according to the plugin's stats page.
Website defacement campaign: Sucuri has discovered more than 50 websites that have been defaced with content from a Belarussian bottled water company. Yep, you read that right.
MichaelKors RaaS: Crowdstrike researchers have uncovered a new Ransomware-as-a-Service operation named MichaelKors. The operation launched in April 2023 and offers ransomware strains capable of encrypting Windows and ESXi/Linux systems.
Qilin RaaS: Group-IB published a report on Qilin, a RaaS that emerged in July 2022 and has claimed responsibility for 12 attacks so far.
RA Group: Cisco Talos has a report on a new ransomware gang named RA Group that launched last month and also engages in double-extortion attacks. The group is now the tenth ransomware operation to build their ransomware around the leaked source code of the now-defunct Babuk gang.
BianLian ransomware: The FBI, CISA, and the ACSC have published a joint technical report on the BianLian gang. The report highlights the gang's transition from a file-encrypting ransomware operation last year to a pure data exfil&extortion gang this year. This happened after Avast released a free decrypter for BianLian's ransomware.
UNC3944 attacks: Google's Mandiant has published a report on new attacks carried out by UNC3944, a group more commonly known as Scattered Spider or Roasted 0ktapus. The report covers the group's use of the Serial Console on Azure VMs to install remote-access software on cloud environments. The attacks are part of the group's operations that support its SIM-swapping capabilities.
8220 Gang: Trend Micro published a report on new techniques used by the 8220 Gang, a Chinese threat actor that is known for targeting and compromising poorly secured cloud servers with crypto-miners and IRC bots. According to the company, the group is now targeting Oracle WebLogic servers with CVE-2017-3506.
PyPI malware: Fortinet researchers have spotted eight new malicious Python libraries uploaded on the official PyPI portal.
Malicious VSCode extensions: Check Point has discovered three malicious Visual Studio Code extensions available through the official VSCode store that contained code to steal user data and enable backdoor access. The extensions were installed more than 45,000 times.
BidenCash expands to SSH access: The BidenCash carding forum has expanded its services and is now also offering access to compromised SSH servers. The new service launched last week and lets cybercrime gangs buy access to a hacked SSH server for only $2, according to threat intel company CloudSEK. BidenCash previously made a name for itself by selling dumps of stolen credit card details. As of October 2022, the site had sold access to more than 1.2 million card details.
Malware technical reports
Geacon: Cybersecurity firm SentinelOne has detected attacks against macOS systems using Geacon, a Go version of the Cobalt Strike Beacon, a popular red-team toolkit. The Geacon project and several of its variations have been widely available on GitHub for more than a year, but SentinelOne says it has seen an uptick in Geacon samples uploaded on VirusTotal over the last few months. Researchers say that while some payloads may be legitimate red team operations, some are also genuine threat actors.
Quasar RAT C&C servers: Embee researchers have identified 64 command and control servers for the Quasar RAT via Shodan and Censys.
CryptNet: Zscaler published a technical analysis on CryptNet, a new ransomware gang that engages in double extortion.
"CryptNet is a simple but effective ransomware that has taken the popular Chaos and Yashma codebase and increased the file encryption efficiency. The code is not particularly advanced, but the algorithms and implementation are cryptographically secure."
Water Orthrus: Trend Micro says a threat actor named Water Orthrus has been distributing the CopperStealer malware via a pay-per-install (PPI) scheme since at least 2021. Researchers say that throughout the past two years, the group used the malware to inject ads into network traffic, collect personal information from infected devices, and even steal cryptocurrency from victims' accounts. Besides CopperStealer, Trend Micro says it observed the Water Orthrus group also deploy a rootkit named CopperStealth for better persistence and another malware strain named CopperPhish that is capable of phishing victims for credit card information. Trend Micro believes this gang may be connected to the Scranos rootkit, which Bitdefender researchers discovered in 2019.
Risky Business Demo
Proofpoint is one of this newsletter's main sponsors. Below is a product demo Patrick Gray, the host of the main Risky Business podcast, recorded with them last year, where they show off Nexus People Risk Explorer, the company's product for mitigating insider threats:
APTs and cyber-espionage
Russian false flag: BlackBerry security researchers say that the cybercrime group behind the Cuba ransomware and the RomCom RAT are most likely Russian government hackers that are using the two operations as a front for their cyber-espionage activities. BlackBerry says that many incidents where they spotted the group deploying the RomCom RAT took place around geopolitical events related to Russia's invasion of Ukraine. As of now, only BlackBerry has formally linked the group to the Russian government, while other security firms and the Ukrainian government have yet to confirm BlackBerry's attribution. [Additional coverage in TechCrunch]
Andariel's Jupiter: DCSO researchers have published an analysis of Jupiter, a malware strain linked to the North Korean Andariel APT.
OilAlpha: A new APT group named OilAlpha has been seen launching attacks for at least a year against entities across the Arabian Peninsula in support of the pro-Houthi movement in Yemen. Recorded Future has seen the group launch operations against individuals attending Saudi Arabian government-led negotiations and a UAE humanitarian organization. The group uses off-the-shelf malware like ngRAT, SpyMax, and SpyNote, and social engineering attacks via WhatsApp conversations. Most of the group's attacks have used infrastructure associated with PTC, a Yemeni government-owned telco, which may be an indicator of the group's location.
APT31: As Shanon Vavra from The Daily Beast spotted, the latest Intrusion Truth dox [1, 2, 3, 4, 5] appears to be targeting members of the APT31 group.
Lancefly: Broadcom's Symantec division has discovered a new APT group that's been active since 2018, targeting organizations in the aviation and government sectors across South and Southeast Asia. Named Lancefly, the group is using a new backdoor named Merdoor and an updated version of the ZXShell rootkit. Symantec says the group's operations are "highly targeted, with only a small number of machines infected," and their motivations seem to be "intelligence gathering." Evidence suggests the group may have ties with other Chinese threat actors like APT41, APT17, and APT27.
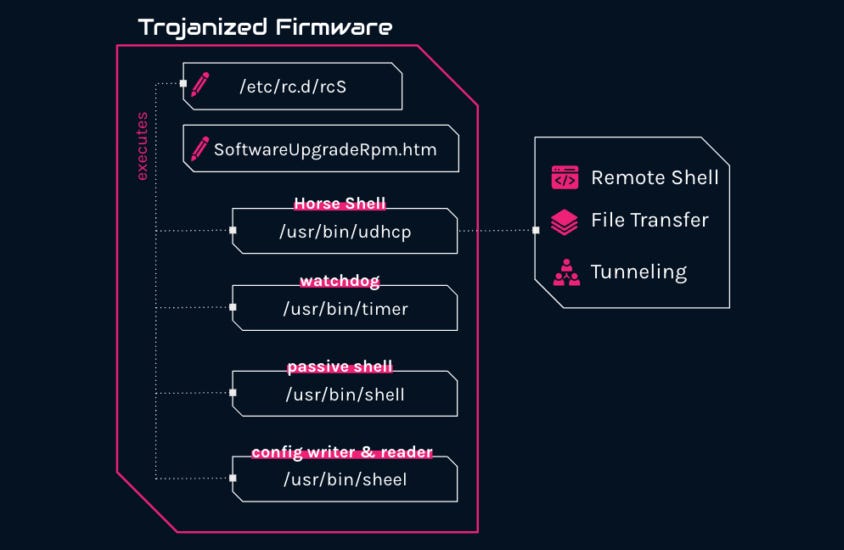
Camaro Dragon: A new Chinese APT group named Camaro Dragon is behind a series of targeted attacks against TP-Link routers installed at European foreign affairs entities. Discovered by security firm Check Point, the attacks used a novel malware strain named Horse Shell. The malware operates as a firmware implant, and researchers say its design is firmware-agnostic, meaning it could also be used to target routers from other vendors. Check Point says it traced back Camaro Dragon attacks as early as January of this year but couldn't discover how the malware was deployed inside the TP-Link router firmware.
Vulnerabilities and bug bounty
Ferrari hack: Char49 researchers have published a write-up on how they exploited an outdated and vulnerable version of the W3 Total Cache plugin to gain access to Ferrari's customer database.
Linux vulnerability: Interrupt Labs has published a technical analysis of CVE-2023-2156, a vulnerability they found in how the Linux kernel handles the RPL network routing protocol.
Wemo vulnerability: Sternum researchers Amit Serper and Reuven Yakar have discovered a vulnerability in the Wemo Mini Smart Plug V2, a popular IoT device that can be used to remote-control any electric device. The vulnerability (CVE-2023-27217) is a buffer overflow in the device firmware that can be exploited via the smart plug's mobile app, named FriendlyName. Belkin, the device's manufacturer, did not release security updates because the product reached EoL.
Teltonika vulnerabilities: Security researchers from Claroty and OTORIO have discovered eight vulnerabilities in the Teltonika RMS platform. Available as a cloud service and an on-premises system, the Teltonika RMS allows companies to remotely manage their industrial equipment using a fleet of Teltonika routers. Claroty and OTORIO researchers say they found vulnerabilities in both the RMS platform and the company's RUT router models. The vulnerabilities could allow threat actors to hijack Teltonika cloud accounts, monitor traffic, steal sensitive data, and access internal networks. One of the vulnerabilities—tracked as CVE-2023-32347—received a score of 10/10 on the CVSSv3 severity scale. Teltokina has released patches for all reported issues, which look pretty bad and will most likely need maximum attention from IT teams asap. This research was also presented at the Black Hat Asia 2023 security conference last week.
Telegram vulnerability: Google software engineer Dan Revah has discovered a vulnerability (CVE-2023-26818) in the Telegram app that can allow threat actors to access the camera on a macOS device. Telegram has not responded to the researcher, so the issue remains unpatched.
Infosec industry
Tool update—Ghidra: The NSA has released version 10.3 of the Ghidra reverse engineering software. Now, with a dark mode and fully customizable UI themes.
New tool—Permhash: Google's Mandiant division has open-sourced a tool named Permhash that can be used to parse permissions declared by a Chrome extension or an Android app.