Risky Biz News: Israel warns citizens of security camera hack risk
In other news: Former Uber CSO appeals conviction; EPA retracts cybersecurity guidance; and Equifax fined in the UK.
This newsletter is brought to you by application allow-listing software maker Airlock Digital. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
In the face of an escalating military conflict with Hamas and Hezbollah forces, the Israeli government has asked citizens to secure home security cameras or shut them down completely, fearing the devices could be hacked and used for espionage and intelligence collection.
In a memo on Friday, Israel's National Cyber Directorate has asked camera owners to change their passwords, enable two-factor authentication if present, and enable automatic security updates.
If camera owners can't change any of their settings, officials have urged owners to either cover camera lenses or shut down devices completely.
Israeli officials aren't taking any chances and have most likely learned a vital lesson from the recent Russo-Ukrainian conflict, where security cameras across Ukraine have been hacked by Russian hackers to track military aid convoys and adjust missile targeting in real-time.
With Israel moving a large part of its military forces across the country, not exposing troop and gear location via someone's home camera feed is a must for the safe movement of its troops.
In addition, there is also a propaganda aspect to take into consideration. Since the initial Hamas attack on October 7, footage taken from hacked security cameras showing Hamas rockets hitting Israeli homes has also been widely shared online.
Securing all those cameras will also be a daunting task, even in a time of heightened attention from the general public to any security recommendations.
According to the government's own data, there were more than 66,000 security cameras across Israel that were vulnerable to some sort of remote attacks.
According to a Calcalist report, hacks of security are already underway, although it's unclear if this is just aimless hacktivism or actual intelligence collection.
One lesson is clear in all of this, though. In the aftermath of both the Russo-Ukrainian and Israeli-Palestinian conflict, security cameras have turned out to be the wild cards in modern-day intelligence collection. Sure, there were cameras in Iraq and Afghanistan in the early 2000s, but they are not as widely installed as they are now, where you can watch over entire towns just by hacking into a few routers that still use their default passwords.
Breaches, hacks, and security incidents
Another Aadhaar leak: One of the Indian local government websites leaked Aadhaar data again. This time it got patched when the issue was reported, unlike in the past, when journalists needed to shame the government into taking action. [Additional coverage in TechCrunch]
UK fines Equifax: The UK's financial regulator fined Equifax £11 million ($13.4 million) for the company's 2017 data breach. The FCA says Equifax UK outsourced the data of UK citizens to its US parent company, which then failed to properly secure it and took six weeks to discover it got hacked. The company's 2017 breach exposed the personal data of 163 million users, including 13.8 million UK consumers.
23andMe gets sued: At least five class-action lawsuits have been filed against DNA and genetic testing service 23andMe in the aftermath of its recent security breach. [Additional coverage in Insurance Journal]
CDW ransomware attack: The LockBit ransomware gang is demanding a whopping $80 million ransom from CDW, one of the world's largest IT service providers. CDW says news of the hack is overblown, and the attack didn't impact any of its operations. The company says the hackers only gained access to the internal network of Sirius Federal, a small subsidiary of one of its subsidiaries. The LockBit gang plans to release CDW's stolen data later this week. [Additional coverage in The Record]
Vercel rogue employee: WebDev platform Vercel has "taken appropriate actions" against an employee who used access to its platform to harass a customer with legal threats about a customer domain that was too similar to a domain owned by the employee. Nothing surprising here since Vercel has been caught releasing "open source" alternatives of other people's commercial apps as part of a marketing stunt.
FSL rug pulls after one day: The developers of the FSL cryptocurrency token have exit-scammed and ran away with customer funds just one day after launching the project. According to blockchain security firm Beosin, the FSL team took 97% of the tokens they created and sent them to TornadoCash, a known money laundering service. The size of the stolen assets is believed to be $1.68 million, and the value of FSL tokens immediately crashed after news of the developers' rug pull. [Additional coverage in PanewsLab/English coverage]
DDOS attack on aid groups: Hacktivists (with the IQ of a box of rocks) are launching DDOS attacks against non-profits providing humanitarian aid to both sides of the Israeli-Palestinian war—because we all know the non-profits are the ones to blame here. DeRp DeRp! [Additional coverage in Reuters]
General tech and privacy
Chrome 118: Google has released version 118 of its Chrome browser. See here for security patches and webdev-related changes. Major changes include a Read Aloud option in Reading Mode, support for storing Chrome passkeys inside the Apple Keychain, a sandboxed network service on Windows, and the automatic disabling of off-Store extensions if users have opted in the Enhanced Safe Browsing mode. The Chrome Safe Browsing interstitials also got a facelift and will now provide users with recommendations.
Windows 10 security updates: Microsoft has fixed an issue where the last Patch Tuesday security updates were not installing on Windows 10 systems. Better check your OS and see if they installed properly.
Ubuntu malicious translation: Canonical has pulled Ubuntu 23.10 installation images after the team discovered offensive language (described as hate speech) in the OS' Ukrainian translation.
Jersey Island outage: Jersey officials blamed "rogue code" for an IT outage that cut off gas supply to the island for almost a week. [Additional coverage in the BBC]
Cookie banner blocking: Mozilla will test a cookie banner blocker in Firefox 120. The test will only include German users (for now).
YouTube's ad-blocking plans: Ad-blocker company AdBlock Plus has criticized Google for its plans to block ad-blockers on YouTube in an effort to shove a metric ton of ads down its users' throats. This is especially annoying for everyone since Google does nothing about malicious ads shown on YouTube.
Microsoft backtracks on OneDrive changes: Microsoft has backtracked on a planned change to its OneDrive service that was meant to go into effect on October 16. After a deluge of negative feedback, the company says that photos stored in the OneDrive Gallery section will not count towards a user's account quota—as it initially intended to do.
Twitter does Musk things: As the EFF's Eva Galperin perfectly explains, in the face of massive misinformation and disinformation campaigns surrounding the war in Israel, Twitter has decided to crack down on sex workers.
Tech-bro-powered AI is dumb, part 391: A recent analysis has found that all those AI data centers working to sustain the current tech-bro-powered AI investment boom consume astronomical quantities of electricity and water, putting even the cancerours cryptocurrency community to shame. All that energy waste just so some dude can use ChatGPT to answer his girlfriend.
Russia's national firewall: The Insider takes a look at how Russia has built its national firewall system, in many cases, with the help of Western companies.
Government, politics, and policy
US EPA rescinds cybersecurity guidance: The US Environmental Protection Agency (EPA) has retracted cybersecurity guidance it published earlier this year in March. The agency rescinded [PDF] the guidance after a joint lawsuit filed by water companies (AWWA and NRWA) and Republican states. The guidance would have had US states carry out period cybersecurity audits of water utilities. The plaintiffs wanted to block the EPA's new rules and argued for rules developed in collaboration with industry groups, similar to how cybersecurity regulation is passed in the electric sector. [Additional coverage in The Record]
Sandvine pulls out of US market: Network intelligence company Sandvine has abandoned plans to sell a new digital surveillance product in the US. Named Digital Witness, the platform can covertly monitor network traffic and track encrypted communications via Signal or WhatsApp. Bloomberg reports that Sandvine has laid off more than 50 employees who were tasked with demoing and preparing the technology for the US market. Sandvine had already provided trials to the US DEA and state and local law enforcement agencies. It's believed the company's past history of working with authoritarian regimes is what led to its exit. The Digital Witness platform is sold to customers in Europe, Asia, North America, and the Middle East, including the likes of Belarus and Azerbaijan. [Additional coverage in Bloomberg/non-paywall]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Airlock Digital founders Daniel Schell and David Cottingham about the recent Microsoft Digital Defense Report and the problem of properly securing PowerShell.
Cybercrime and threat intel
Aviram Azari case: US prosecutors say that an Israeli private investigator named Aviram Azari hired hackers to steal emails from climate activists and leak them to news agencies. The stolen emails were used to write articles criticizing the tactics of climate activists. The articles were then cited in lawsuits involving Exxon Mobil, seeking to dodge investigations about its impact on climate change. US prosecutors have not linked Azari to Exxon Mobile. Prosecutors have asked the judge for a sentence of hundreds of months in prison, while Azari's team is asking for a maximum 60 months prison sentence after he pleaded guilty last year. Azari's sentencing is scheduled this week on October 18. [Additional coverage in Reuters]
Smishing gang detained: Something we missed from August is that Slovenian authorities have detained four Romanians who were running a smishing operation out of the city of Maribor.
Reichsadler Cybercrime Group: Sophos has spotted a new threat actor named the Reichsadler Cybercrime Group using a recent WS_FTP vulnerability (CVE-2023-40044) to breach corporate networks and deploy ransomware.
New npm malware: Forty-three malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details.
RedAlert clones: Cloudflare's security team has spotted malicious websites distributing fake versions of RedAlert, an app that sends rocket alerts to Israeli citizens. The malicious apps contain spyware-like behavior.
DDOS attacks against IL-PS sites: NSFOCUS has published a timeline of all the DDOS attacks that have hit Israeli and Palestinian websites since the start of the most recent conflict.
EvilSln: A security researcher has released a technical write-up and proof-of-concept code on how to hide malicious code in Visual Studio SLN project files—a la North Korea.
Malware technical reports
EtherHiding: Guardio Labs look at how a malware gang named ClearFake is using Binance blockchain smart contracts to hide some of its malicious code. Guardio names this technique EtherHiding—spotted earlier this month by FINSIN.
GuLoader: CERT-Slovenia has published a technical analysis of the GuLoader downloader.
SilverFox: Qihoo 360 has a report on recent SilverFox trojan operations.
Akira ransomware: Fortinet looks at recent versions and operations of the Akira ransomware.
Good Day ransomware: ShadowStackRE has published an analysis of the Good Day ransomware. Researchers say the group has been active since May 2023, and they may be the group behind the Cloak dark web leak site.
Sponsor Demo
Airlock Digital CEO David Cottingham shows Patrick Gray how Airlock's execution control and allowlisting solution works.
APTs and cyber-espionage
Sticky Werewolf: A threat actor named Sticky Werewolf is targeting government organizations in Belarus and Russia. The group uses spear-phishing campaigns for initial access and a commodity remote access trojan named NetWire for data collection and exfiltration. According to Russian security firm BI.ZONE, Sticky Werewolf has been active since April this year and has conducted 30 attacks to date.
Void Rabisu: A Russian cyber-espionage group named Void Rabisu has used a Windows zero-day to target EU politicians working on gender equality. The campaign took place in June and used a zero-day (CVE-2023-36884) in the Windows Search feature that Microsoft later patched in August. The campaign aimed to infect victims with a remote access trojan named PEABOD. Also known as RomCom, the Void Rabisu group is a former financially motivated group that has pivoted to cyber-espionage on behalf of the Russian government after its invasion of Ukraine.
BLOODALCHEMY: Elastic's security team has published a technical write-up of BLOODALCHEMY, a new backdoor used by a cyber-espionage group the company calls REF5961. Elastic discovered this yet-to-be-attributed APT group on the network of a Foreign Affairs Ministry from a member of the Association of Southeast Asian Nations (ASEAN).
WinRAR zero-day abused by APT groups: A WinRAR zero-day that was used to hack stock and crypto-traders earlier this year has now entered the arsenal of at least three APT groups. Groups like DarkPink, Russia's APT28, and North Korea's Konni have been spotted using the former zero-day in spear-phishing operations. Patched at the end of August, the former WinRAR zero-day (CVE-2023-38831) allows threat actors to run malicious code on a target's system when they decompress booby-trapped ZIP files.
Lazarus' Volgmer and Scout: AhnLab has published a report on Volgmer and Scout, two new malware strains used by North Korean hackers in recent campaigns. The first is a backdoor/dropper, while the second is a basic downloader.
Operation Dream Magic: The same AhnLab team has also published a report on what they call Operation Dream Magic, a Lazarus cyber espionage campaign targeting South Korea.
IL-PS dis/misinformation campaign: Alethea has published a report on a network of Twitter troll accounts pushing dis/misinformation about the recent Israel-Palestinian conflict.
"Alethea has detected a likely inauthentic, coordinated cluster of at least 67 accounts on X posting near-identical content about the conflict and promoting misleading and out of context translations of statements from Russian President Vladimir Putin and Foreign Minister Sergei Lavrov. Alethea observed both pro-Palestine and pro-Israel content from these accounts, suggesting the network's aim may be to stoke anger on both sides of the conflict or to simply capitalize on the current interest in the topic."
Vulnerabilities, security research, and bug bounty
iOS zero-days: Google has published a technical dive into CVE-2023-28205 and CVE-2023-28206, two iOS zero-days that were patched in April after being abused by surveillance vendors.
Signal zero-day rumor: There's a rumor about a Signal zero-day. Nothing has been confirmed so far, though. Could also be FUD.
Milesight router vulnerability: A severe vulnerability (CVE-2023-43261) has been discovered in Milesight cellular routers that can allow threat actors to retrieve login credentials from log files. Security firm VulnCheck says it found signs of potential exploitation in the wild, although the attacks don't appear to be taking place at scale. The affected Milesight routers are typically used in OT networks to connect industrial control equipment to the internet. While more than 5,800 routers are currently accessible over the internet, VulnCheck says the vulnerability only affects older models running firmware before March 2021.
"If you have a Milesight Industrial Cellular Router, it's probably wise to assume all the credentials on the system have been compromised and to simply generate new ones, and ensure no interfaces are reachable via the internet."
WP plugin zero-day: A threat actor is exploiting a recently patched vulnerability (CVE-2023-5360) in a popular WordPress plugin to install backdoors, create new admin accounts, and take over websites. The attacks are targeting the Royal Elementor Addons and Templates plugin, installed on more than 200,000 WordPress sites. Researchers at Wordfence say the plugin was exploited since the end of August, well before a patch was released last week.
WP security updates: A security update is available for the WordPress CMS, including one RCE.
Juniper security updates: Networking equipment vendor Juniper dozens of security updates for its products.
XORtigate PoC: Lexfo has released a PoC for the XORtigate, a vulnerability (CVE-2023-27997) in Fortinet devices.
Windows EoP PoC: Filip Dragovic has published a PoC for CVE-2023-36723, an elevation of privilege vulnerability in the Windows Container Manager Service.
Upcoming crypto-wallet bug: Unciphered says it will publish details on a major crypto-wallet vulnerability on November 10.
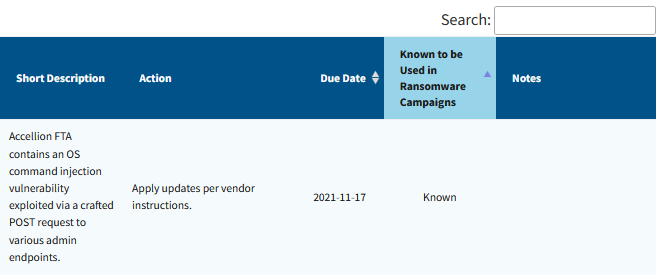
CISA KEV update: CISA has updated the KEV database to show if vulnerabilities have been used in ransomware attacks. The KEV database has recently surpassed the 1,000 entries mark, and the new update is meant to help organizations prioritize patches. The agency has also launched a second database that lists common misconfigurations exploited in ransomware attacks, such as open RDP and VNC ports.
Infosec industry
Former Uber CSO appeals: Former Uber CSO Joseph Sullivan filed an appeal against the DOJ and is seeking a reversal of his conviction and a new trial. Sullivan was sentenced to three years probation for covering up a security breach at Uber in 2016. Sullivan's legal team calls the conviction "profoundly flawed" and claims the DOJ mischaracterized Sullivan's actions. [Additional coverage in SecurityInfoWatch]
New tool—ELITEWOLF: The US NSA has released a GitHub project named ELITEWOLF containing a collection of signatures designed to detect malicious activity on ICS/SCADA/OT networks.
New tool—OpenSSF Malicious Packages: The Open Source Security Foundation has launched the OpenSSF Malicious Packages, a repository containing a list of malicious libraries spotted across the open-source ecosystem.
New tool—QBinDiff: QuarksLab has open-sourced a tool named QBinDiff for binary diffing.
New tool—Stompy: Security researcher Andy Gill has released a tool named Stompy that can timestomp files as part of red-team exercises.
FIRSTCON23 videos: Talks from the FIRSTCON23 security conference, which took place back in June, are available on YouTube.
Legal ransom payment map: Splunk's Ryan Kovar has put together a map with the places where it's legal to pay ransomware groups.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq examine the opportunities that ransomware gangs and business email compromise/romance scammers have to collaborate.