Risky Biz News: Albania raids Iranian MEK camp for running a "hacker center"
In other news: Reddit confirms ransomware attack; exec sentenced for hacking-back former employee; RocketMQ and VMWare servers exploited in the wild.
This newsletter is brought to you by Nucleus Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Albanian law enforcement raided a refugee camp hosting members of Iranian opposition party Mujahedeen-e-Khalq (People's Mujahedin of Iran, or MEK) on suspicion of operating a "hacker center" that conducted cyber-attacks against foreign institutions.
The raids took place on Tuesday, June 20, and targeted a camp near the city of Manez in Western Albania.
The camp hosts around 3,000 MEK party members that were relocated to Albania in 2013 after their previous camp in Iraq came under attack from Iraqi and Iranian forces.
The Albanian Ministry of Internal Affairs says the MEK broke a 2014 agreement with the Albanian government that the camp be used solely for humanitarian purposes.
Sources told The Albanian newspaper the MEK used the camp as a "hacker center" where they hosted servers that were used to hack foreign institutions.
No details were provided on these cyber-attacks, but they very likely refer to the recent rise of anti-Iranian hacktivism activity. This includes the hack of the Iranian President's Office, the Iranian Foreign Ministry's internal network, and Tehran's CCTV system. In all cases and others, news of the hacks were often published on the MEK's website, which served as some sort of unofficial newswire for various anti-Tehran hacktivist groups.
These hacks would often be accompanied by website defacements that praised the MEK's current leadership and urged the Iranian people to revolt against the current Iranian regime.
A former member of the MEK told Albanian news outlet SOT that the Manez camp was home to many MEK members who "studied cyber and are very good at technology."
Albanian officials did not officially blame the MEK for these hacks, or at least not yet.
Albanian police forces sent into the camp have reportedly seized some of the servers used in the hacks, meaning an official attribution may be soon coming.
The raids did not go as planned, with police forces encountering ardent resistance from MEK members. Albania's Ministry of Internal Affairs denied online rumors that a MEK member lost their life in the raids following violent clashes between the officers and the MEK. Video footage from the raids is available embedded below, courtesy of a local Albanian TV station.
The Albanian government's crackdown on the MEK camp comes nine months after Albania cut diplomatic ties with Iran in September 2022.
Diplomatic ties broke down between the two countries after an Iranian state-sponsored hacking group known Europium (Hazel Sandstorm) deployed ransomware and data wipers on several Albanian government IT systems in July 2022. The effects of the attacks lingered for months and crippled government activity, especially border crossings.
Mandiant classified the attack as politically motivated, with Iranian hackers trying to dissuade Albania from providing a safe haven to the MEK, which the Tehran regime classified as a terrorist organization.
Albania's support for the MEK will most likely continue. The party's members were relocated from Iraq at the request of NATO, of which Albania is a member.
The raids this week are most likely an attempt to tell the MEK to stop its rogue hacktivism spree before Iranian hackers respond with another attack that cripples Tirana's IT systems as they did in 2022.
Breaches and hacks
Cloud AZ Tower incident: Japanese software company Purpose has restored its AZ Tower cloud platform ten days after its security team found malware installed on some of its systems. The incident has had a major impact across Japan, where the AZ Tower service is used by more than 1,100 companies. The biggest impact was in the LPG field, where several gas providers were forced to shut down customer portals and delayed gas meter readings. Purpose says no customer data was accessed in the incident and also denied a rumor that it got hit by the Trigona ransomware.
Reddit ransomware attack: Social media giant Reddit has confirmed that the data breach it disclosed in February was, in fact, a ransomware attack. Reddit confirmed the incident after the BlackCat ransomware gang threatened to publish 80GB of the company's files over the weekend. The threat actor is demanding a $4.5 million ransom. [Additional coverage in The Record]
MOVEit hacks: The victim count is now 84. No, make that 85. New additions to the list include PwC, Ernst & Young, Medibank, Metro Vancouver Transit Police, and Norton LifeLock.
General tech and privacy
Sub Rehab: A new website named Sub Rehab shows where most of the Reddit subreddits have relocated on the Lemmy platform.
Anti-Meta Fedi Pact: The admins of tens of Mastodon instances have agreed to block Meta's upcoming ActivityPub service and prevent Meta users from connecting to most of the Fediverse.
Meta censorship in Vietnam: Two Meta whistleblowers have told the Washington Post the company is censoring posts in Vietnam that may be critical of the country's communist party. [Additional coverage in the Washington Post/non-paywall]
"Meta has adopted an internal list of Vietnamese Communist Party officials who should not be criticized on Facebook, said two former employees in Asia, who, like the others, spoke on the condition of anonymity to avoid retribution. This list, which is kept private even within the company and has not been publicly reported on before, is included in guidelines used in controlling online content and was shaped in large part by Vietnamese authorities, the former employees said. They said such a list of names is unique to Vietnam in East Asia."
LastPass 2FA reset: Password management utility LastPass has reset the 2FA tokens of all its users. Unclear why. Maybe some security steps dealing with last year's hack.
Government, politics, and policy
New UK aid for Ukraine's cyber defense: The UK government has approved a £25 million ($31 million) aid package to help Ukraine boost its cyber defense. The new funding is meant to be used by Ukrainian officials to protect critical national infrastructure and vital services.
Yandex fined in Russia: A Moscow court fined Russian tech giant Yandex 2 million rubles ($24,000) for failing to provide the FSB with information about the users of Yandex.Services portal. [Additional coverage in TASS]
Hartman interview: Maj. Gen. William Hartman, the head of the US Cyber Command's Cyber National Mission Force (CNMF), gave an interview to The Record on CyberCom's hunt-forward missions in Ukraine. Gen. Hartman has been nominated to become the next deputy of US Cyber Command.
New DOJ National Security Cyber Section: The US Justice Department has created a new section in its National Security Division that will investigate cybercrime activity performed by foreign state-sponsored hackers. The new National Security Cyber Section will operate independently from the DOJ's existing Criminal Division which usually handles cybercrime cases. Officials hope the new division will help increase the scale and speed of new prosecutions of foreign cyber threats.
US Army personnel received unsolicited smartwatches: The US Army Criminal Investigation Division (CID) says it received reports that service members have received unsolicited D18 smartwatches in the mail. The agency says the smartwatches auto-connected to WiFi networks and cell phones without prompting their users. CID says the smartwatches could contain malware that could be used to harvest data, record conversations, or access data from connected smartphones. CID issued a security alert earlier this month asking service members not to turn the devices on and to report the incident to their unit's Counterintelligence or Security Manager.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Patrick Garrity, VP of Marketing and security researcher at Nucleus Security, on how the company has been tapping into CISA's KEV database for insights on vulnerability management and prioritization.
Cybercrime and threat intel
Exec sentenced for hacking-back former employee: US authorities have sentenced the CEO and co-founder of Ink Labs to 18 months in prison for SIM swapping a former employee. The DOJ says Jonathan Manzi hacked into the Gmail and Dropbox accounts of the former employee and stole information on his new employer. In a blog post this week, Manzi tried to justify his actions as "hacking back." He says he was only trying to assess what intellectual property the former employee took when he left and joined Wepa, one of Ink Lab's business rivals. Manzi says the former employee was also bad-mouthing Ink Labs in the marketplace, which is why he took information from the employee's hacked accounts and sent anonymous emails to some of Wepa's customers and prospects. "Hacking back" may not be an accurate description of this, though.
DataBox sentenced: An Amsterdam court has sentenced a Dutch hacker to 36 months in prison, of which 12 months are suspended. Twenty-five-year-old Erkan Sezgin was found guilty of selling hacked data on the now-defunct RaidForum, where he operated under the pseudonym of DataBox. He sold the data of more than 9 million Austrians he stole from a tax filing service, the medical information of 4.4 million Colombians, and the user database of e-commerce giant Lazada. In total, Sezgin advertised at least 16 databases, which he sold for a few thousand euros each. He was also found guilty of running phishing operations and laundering more than €700,000 in cryptocurrency. [Additional coverage in DataBreaches.net]
BreachForums clone gets hacked: Do you remember how last week another BreachForums clone launched? Yeah! So, it got hacked! Sadge. Anyway!
ChatGPT accounts for sale: Group-IB researchers say they've identified more than 100,000 accounts on OpenAI's ChatGPT service that have been sold on underground hacking marketplaces over the past year. May 2023 was the peak, with Group-IB spotting more than 28,000 accounts being offered for sale.
RocketMQ exploitation: Threat actors are exploiting a vulnerability in Apache RocketMQ servers. The vulnerability (CVE-2023-33246) allows attackers to update the server's configuration file and remotely execute malicious commands. The RocketMQ team released patches in May. Attacks began this week after a proof-of-concept exploit for the vulnerability was published on GitHub. According to the ZoomEye IoT search engine, more than 6,000 servers appear to have been compromised already, with most located in China.
VMWare exploitation: Also in exploitation news, VMWare says a vulnerability (CVE-2023-20887) it patched earlier this month is now being exploited in the wild. Just like in the RocketMQ case, attacks began after someone posted a PoC on GitHub. The vulnerability and the attacks are targeting VMWare Aria Operations for Networks, formerly known as VMWare vRealize Network Insight.
Bellingcat warning: Investigative journalism outfit Bellingcat is warning that scammers are using the identity of one of its reporters to target its future sources.
Malware technical reports
RDStealer: Bitdefender has published a report on RDStealer, a Go-based malware strain used in an attack against an East Asian IT company.
Resident: eSentire researchers say that since November 2022, a threat actor has been using drive-by downloads and phishing campaigns to infect victims with a new backdoor named Resident. Researchers say the malware appears to have been created by a Russian-speaking hacker-for-hire group Trend Micro spotted back in 2022. The campaign targeted organizations in the manufacturing, commercial, and healthcare verticals.
RecordBreaker: AhnLab has a report on RecordBreaker, the latest version of the RacoonStealer malware.
SeroXen: More on the SeroXen malware from Trend Micro. The company had a first report on it last week.
Tsunami DDoS bot: The same company also has a report on a recent version of the Tsunami DDoS bot, currently being installed on Linux systems following SSH brute-force and dictionary attacks.
Risky Business Demo
Nucleus Security's COO Scott Kuffer shows Risky Business podcast host Patrick Gray their vulnerability management platform. It ingests scan outputs from a number of vulnerability identification tools, normalizes that information, and then allows vulnerability management teams to do things like assign responsibility for certain types of bugs to the correct people.
APTs and cyber-espionage
APT37: Genians has a report on a recent spear-phishing campaign targeting macOS users—campaign conducted by the APT37 North Korean cyber-espionage group.
CL-STA-0043: Palo Alto Networks has documented a cluster of cyber-espionage activity targeting governments in Africa and the Middle East.
SideCopy: Seqrite published a report on the new Action RAT used by the SideCopy Pakistani APT.
APT28 (BlueDelta): Recorded Future and Ukraine's CERT team have identified a campaign carried out by Russia's APT28 (BlueDelta) cyber-espionage group that targeted the RoundCube email servers of Ukrainian organizations. The campaign used malicious code hidden in email messages that exploited vulnerabilities (CVE-2020-35730, CVE-2020-12641, and CVE-2021-44026) in the RoundCube software to grant APT28 control over the entire email server. The campaign targeted Ukrainian government institutions and military entities involved in aircraft infrastructure. Recorded Future says the campaign was carried out by the same APT28 subgroup that used a novel Outlook zero-day (CVE-2023-23397) to target Ukrainian and European government organizations in late 2022.
Vulnerabilities, security research, and bug bounty
Cisco PoC: Security researcher Filip Dragovic has published a proof-of-concept exploit for CVE-2023-20178, an LPE in Cisco's AnyConnect Windows client.
ASUS security updates: Taiwanese hardware vendor ASUS has released a suite of firmware updates to address 18 security-related issues in its gaming and SOHO routers. The updates include patches and new security enhancements, such as better credential storage protections and an improved OTA firmware update.
Zyxel security updates: On the same note, Zyxel has, too, released a security update. This one fixes a pre-authentication command injection in the company's NAS products.
Fortinet vulnerabilities: Code White's Frycos has published a blog post with details on two Fortinet vulnerabilities he discovered in March this year. Both issues lead to RCE. They were patched at the end of May.
Linux Kernel bug analysis: StarLabs researchers have published a detailed write-up on CVE-2023-1829, a use-after-free vulnerability in the Linux kernel.
Apple SIP bug: Google's Ivan Fratric has published details on CVE-2023-32412, a bug in macOS and iOS' telephony client (namely in its SIP message decoder). The issue was patched in mid-May.
Eaton vulnerability: Security researcher Vangelis Stykas has discovered a major vulnerability in Eaton SecureConnect, the cloud backend behind the Eaton smart home alarm systems. Stykas says the vulnerability can allow anyone to register a new account on the Eaton SecureConnect platform and assign it to the "root" user group. This user group grants an attacker access and control over any smart alarm connected to the Eaton platform. Eaton deployed patches to its cloud service earlier this month, on June 1.
Dogness vulnerabilities: Kaspersky researchers have identified vulnerabilities in the Dogness smart pet feeders. The vulnerabilities range from an insecure firmware update mechanism to plaintext communications with its cloud backend and hardcoded root credentials.
Major WP plugin vulnerability: Wordfence security researchers have identified a major vulnerability in Tyche Softwares' Abandoned Cart Lite for the WooCommerce plugin. According to Wordfence, the vulnerability can be exploited to allow threat actors to log in as registered users who abandoned a shopping cart. Patches were released earlier this month. More than 30,000 online stores use the plugin.
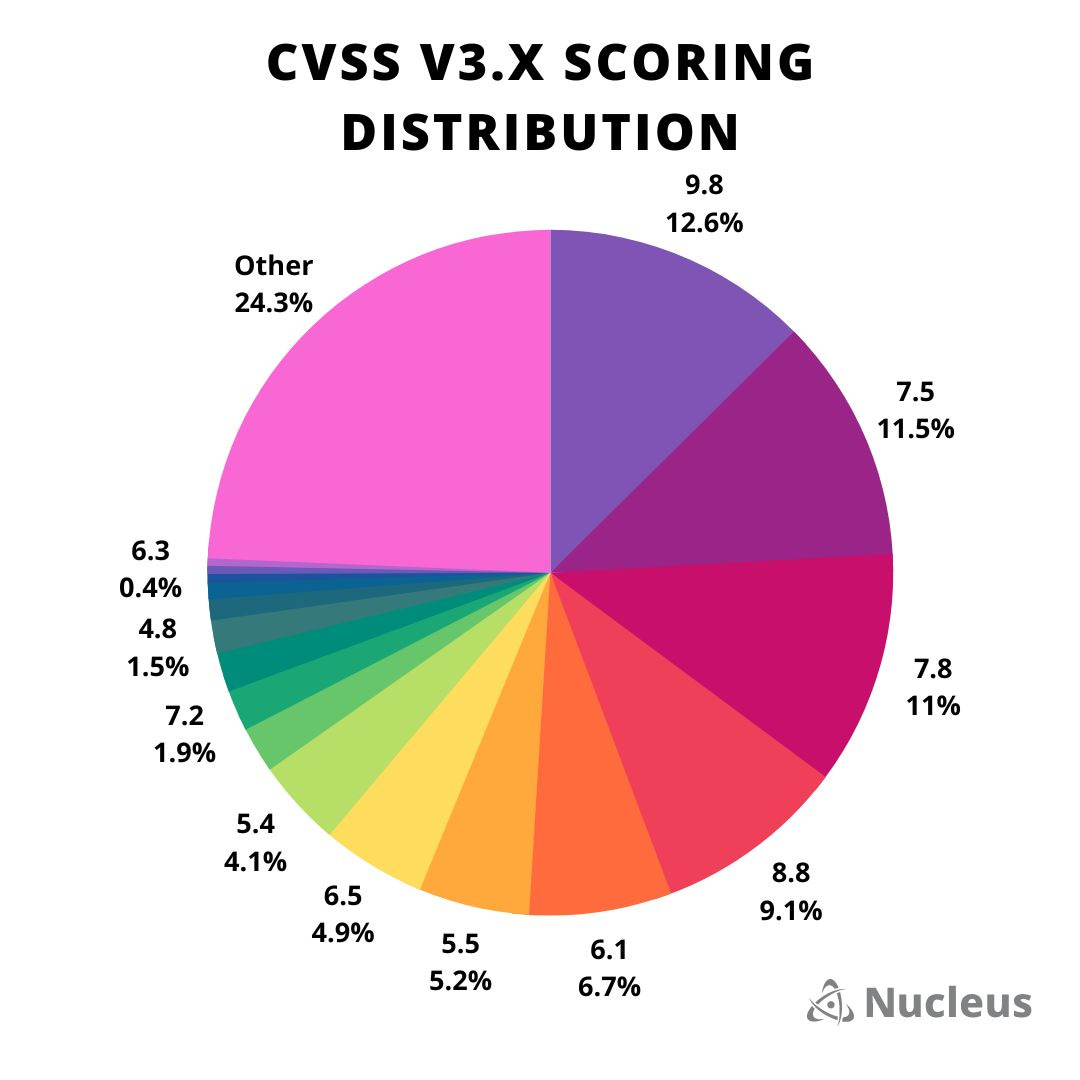
CVSSv3 scores: A chart from Nucleus Security's Patrick Garrity shows that 75% of CVSSv3 ratings use only 17 of the 101 possible scores. This is because of the limited scoring metrics used to compute the score. This is expected to change later this year when CVSSv4 will launch with new basic score metrics and calculator.
"This highlights a challenge faced by many organizations—a lack of score distribution that makes it difficult to determine which vulnerabilities should be prioritized."
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about the elements that make them think an operation is state-backed.