Risky Biz News: SVR hackers breach Microsoft, steal emails from the security team
In other news: Chinese APT secretly exploited VMWare zero-day for months; BreachForums admin sentenced; and Zloader returns.
This newsletter is brought to you by Material Security, the company that secures the cloud office with unified email security, user behavior analytics, and data loss prevention for Microsoft 365 and Google Workspace. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
Russian state-sponsored hackers have breached Microsoft's internal network and have stolen emails from the company's senior leadership, legal, and cybersecurity teams.
The intrusion began in late November of 2023 and lasted until January 13, when Microsoft kicked the hackers off its network.
The Redmond-based giant attributed the attack to Midnight Blizzard, one of the cyber units inside Russia's Foreign Intelligence Service (SVR).
In a blog post, Microsoft said the group breached its network after conducting a password spray attack on a non-production test tenant account and then pivoted to its corporate email accounts system.
According to an SEC filing, the threat actor initially searched and stole information about what Microsoft knew of Midnight Blizzard's activities.
Microsoft's disclosure language does not specifically state that this was the only stolen information, but it is worth pointing out that Microsoft is currently hosting the Ukrainian government's entire network on its Azure cloud infrastructure.
The breach has drawn quite an avalanche of criticism and ridicule for Microsoft for various and well-deserved reasons.
First, Microsoft disclosed the breach late on a Friday night— a well-known scummy tactic to hide the incident from extended media coverage.
Second, the breach took place weeks after Microsoft announced, with bells and whistles, its new Secure Future Initiative, a new plan to re-focus the company's engineering efforts to improve the security of its own products. The new initiative was meant to mimic a similar pledge made by Bill Gates in 2002—named Trustworthy Computing—that led to significant changes to Microsoft's security posture and the creation of what we now know as Patch Tuesday.
Third, the new breach took place four months after Microsoft disclosed another state-sponsored hack, this one by China's Storm-0558, which also had access to its internal network.
Fourth, after promoting MFA as the next evolution of online account security, the fact that one of its test accounts got popped via a password spray suggests Microsoft wasn't high on its own supply.
The hack is quite bad, but not for most of you reading this email. It may not have a material impact on day-to-day Microsoft users, but it has quite the reputational damage on Microsoft's position in the cybersecurity market.
Having Russian intelligence services breach your cybersecurity team's email accounts to steal data about themselves four months after the Chinese breached your production systems to steal US government emails is not what this industry calls trustworthy.
At what point, or after which hack, will the US government stop to re-evaluate its giant dependency on Microsoft infrastructure—something that's rubbing a lot of people the wrong way lately.
Breaches, hacks, and security incidents
HHS hack: A threat actor stole $7.5 million from the US Department of Health and Human Services in a security breach that took place between March and mid-November of last year. The attackers are believed to have gained access to an HHS system that processes civilian grant payments using spear-phishing. They then proceeded to hijack payments for five grant recipients before being detected. The investigation to identify the perpetrators is still underway. [Additional coverage in Bloomberg]
Ivanti attacks on federal networks: CISA is investigating potential breaches at US government agencies that could have been carried out through vulnerabilities in Ivanti Connect Secure VPN appliances. The vulnerabilities were disclosed on January 10 by US cybersecurity firm Volexity, which said the bugs were being exploited in the wild by Chinese state-sponsored hackers. Attacks targeting Ivanti products entered a phase of mass exploitation immediately after Volexity's disclosure. CISA issued an emergency directive instructing federal agencies to patch the Ivanti bugs as soon as possible. A CISA spokesperson told reporters that roughly 15 US government agencies were using Ivanti products before the attacks. [Additional coverage in Axios]
GVSU hack: A Ukrainian hacker group named BlackJack has breached and wiped more than 150 systems belonging to the Main Military Construction Directorate for Special Facilities (GVSU), a state-owned company that builds military facilities for the Russian military. The group claims it also downloaded more than 1.2TB of information from the company's servers containing information on more than 500 military objectives. The BlackJack group has been informally linked to the Security Service of Ukraine. Ukraine's Main Directorate of Intelligence, or GUR, praised the attack on Telegram as a major success. [Additional coverage in UkrInform/English coverage in BusinessInsider]
KSU ransomware attack: Kansas State University is dealing with a ransomware attack that impacted some of its IT networks, such as email servers, WiFi networks, and VPN systems.
VF Corp ransomware attack: The personal data of more than 35.5 million customers was stolen in a ransomware attack in December 2023, VF Corp confirmed in an SEC filing. The company operates more than 13 retail brands across the world, such as The North Face, Dickies, Vans, Timberland, and Supreme. The AlphV ransomware group took credit for the attack days before the gang's infrastructure was seized by US law enforcement.
SK data breach: Hackers breached South Korea's National Council of Social Welfare and stole the personal data of more than 1.35 million volunteer workers. [Additional coverage in KBS]
Lockbit claims go wild: The Lockbit ransomware gang took credit for breaching two giant companies—Swift Air and Subway. None of the intrusions have been verified, but it may be worth keeping an eye on the two claims, especially since Swift Air has filed for bankruptcy and will most likely not be in a position to pay.
Healthcare breaches in 2023: More than 115 million US patient records were exposed or stolen through data breaches in 2023, according to Fortified, a healthcare industry cybersecurity provider. The figure is almost double the 2022 numbers when almost 60 million patient records were exposed online. The number of healthcare breaches went down in 2023, suggesting larger providers were hit last year than the year before. In total, Fortified says that more than 489 million patient records were compromised in data breaches across the US over the last decade.
General tech and privacy
Google News failings: Google News is failing to remove AI-written articles copied from legitimate outlets, an investigation has discovered. Questioned on the matter, Google says it doesn't care if the articles are AI or human-written. [Additional coverage in 404 Media]
Firefox sabotage: Mozilla has accused the three major browser makers—Apple, Google, and Microsoft—of sabotaging Firefox. The company says it launched a new issue tracker where we intend to document the ways in which platforms put Firefox at a disadvantage.
Brave removes strict fingerprinting protection: The Brave team has removed its strict anti-fingerprinting protection from its web browser. The team argued the feature is hardly used and is known to cause websites to function incorrectly.
Government, politics, and policy
FTC bans another data broker: The US Federal Trade Commission has banned a US data broker from trading the precise location of American citizens. InMarket Media becomes the second US data broker to receive a ban of this kind. The FTC previously banned data aggregator Outlogic (formerly X-Mode Social) a week before.
CNMF anniversary: Cyber Command's CNMF ( Cyber National Mission Force) has recently celebrated its ten-year anniversary.
CISA pre-ransomware alerts: CISA has sent more than 1,200 notifications to US and international organizations in 2023 about early-stage ransomware activity on their networks. The agency has also sent 1,700 notifications to organizations that had systems vulnerable to common ransomware entry vectors. The two types of notifications were part of a pilot program CISA started in January 2023 to warn organizations of potential ransomware attacks. [Additional coverage in CISA's 2023 Year in Review report]
NCSC Cyber League: The UK NCSC has launched a new project named Cyber League that aims to bring together experts from the NCSC and the private sector to work on the biggest cyber threats facing the UK. The program is modeled after Industry 100 but is open to cybersecurity experts working at smaller companies.
WEF cybersecurity outlook: The World Economic Forum has published a report looking at recent cybersecurity trends and the cybersecurity posture of the world's nations. Some of the main conclusions are below.
Alignment between cyber and business is becoming more common.
The cyber-skills and talent shortage continues to widen at an alarming rate.
Cyber ecosystem risk is becoming more problematic.
There is growing cyber inequity between organizations that are cyber-resilient and those that are not.
Emerging technology will exacerbate long-standing challenges related to cyber resilience.
Sponsor section
In this Risky Business News sponsor interview, Tom Uren talks to Ivan Dwyer of Material Security about how it makes sense to view office productivity suites as an organisation's critical infrastructure.
Cybercrime and threat intel
Pompompurin sentenced: The former administrator of BreachForums has been sentenced to time served and 20 years of supervised release. Known online as Pompompurin, Brian Connor Fitzpatrick will serve the first two years in home arrest with GPS location monitoring and will have to submit to periodic polygraph tests. Fitzpatrick will also have to register as a sex offender after pleading guilty to possession of child pornography materials. The 21-year-old was initially arrested in March 2023, was set free on parole in July, and re-arrested in early 2024 after breaking parole conditions by using a VPN and the internet. The judge's sentence was a major surprise after the prosecution sought a minimum 15-year-old prison sentence. [Additional coverage in DataBreaches.net]
Flint24 charged in the US: US authorities have indicted a Russian national named Aleksey Stroganov for harvesting and selling hundreds of millions of banking and credit card details. Stroganov was known under the hacker name Flint24, and he was part of a cybercrime syndicate that operated tens of underground carding shops. He was detained by the FSB in 2020 after his group sold the data of Russian citizens. His trial is still underway in Russia. One of Stroganov's accomplices—Tim "Key" Stigal—was also indicted in the US as well.
Pegasus research stands in court: A Mexican judge has allowed CitizenLab's research on the Pegasus spyware to stand in court as evidence [PDF]. The judgment comes after the organization's findings were recently contested by an army of no-name researchers and bot networks in support of oppressive regimes.
Ransomware via TeamViewer: Huntress researchers say they've seen several incidents where threat actors broke into corporate networks via TeamViewer connections and deployed ransomware.
Slug ransomware gang: A new ransomware gang has been spotted in the wild. Named Slug, the gang operates a dark web leak site. The gang's site is currentl listing only one victim.
New npm malware: Twenty-eight malicious npm packages were discovered last week. Check out GitHub's security advisory portal for more details. One of them was this package, delivering a RAT on Windows systems.
Walmart fraud: ProPublica has a deep dive into how cybercriminals are abusing Walmart's financial services for fraud, scams, and money laundering—all while Walmart "has resisted taking responsibility while breaking promises to regulators and skimping on training."
2023 internet exploitation: GreyNoise has published its year-in-review report covering internet mass-exploitation trends for 2023.
Telegram crypto-scams: Roughly 40% of posts in Telegram channels dedicated to cryptocurrency were found to be fraudulent, according to a report from Russian security firm Angara Security.
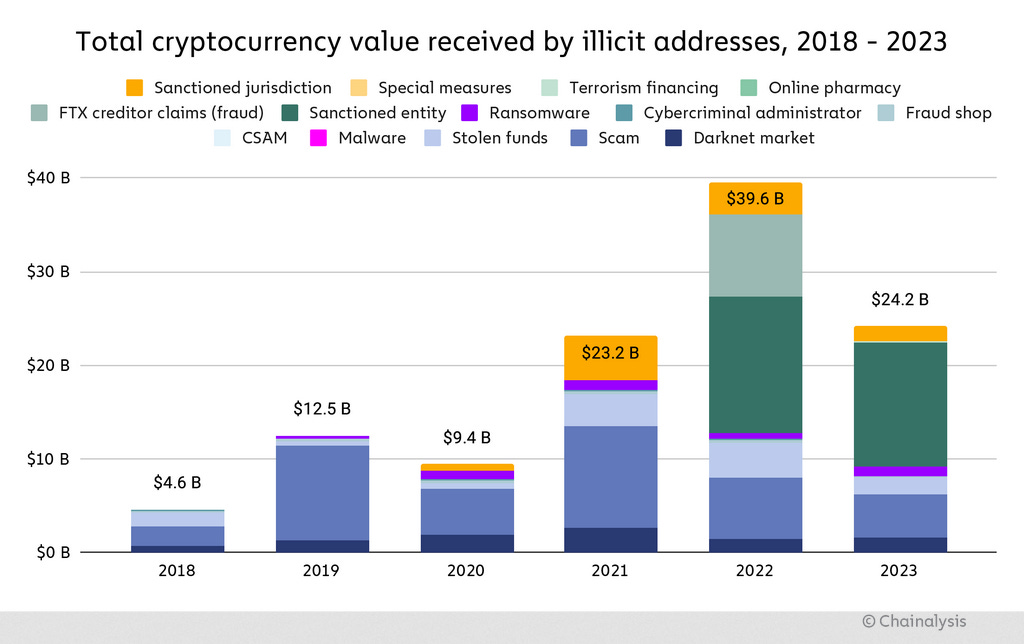
Crypto-crime in 2023: Cryptocurrency transactions linked to illicit activity accounted for $24.2 billion in 2023, down from the $29.6 billion all-time peak of 2022. The 2023 figure represents 0.34% of all cryptocurrency currently in circulation. Ransomware had a record year in 2023, but Chainalysis has not released an exact number. Ransomware payments accounted for $456.8 million the year before, in 2022. [More stats in the Chainalysis' yearly report]
Malware technical reports
New macOS malware: Jamf has discovered a new macOS malware strain hidden inside pirated macOS applications offered online. Researchers haven't named the malware, but they said it's similar to the old ZuRu malware from 2021, as spotted back then by Objective-See and Trend Micro.
DarkGate: Splunk's security team has published a report on DarkGate, one of today's most popular MaaS portals and malware loaders. S2W Talon also recently published a report on the same malware.
Zloader returns: The Zloader (Terdot, DELoader, Silent Night) malware botnet has returned to life after surviving a takedown attempt in April 2022. Security firm Zscaler says it has seen new versions of the malware in September 2023, 14 months after Microsoft and other security vendors seized its old servers. The new Zloader versions include better encryption and a better DGA for its command-and-control servers.
Parrot TDS: Palo Alto Networks looks at Parrot TDS, a botnet that redistributes traffic from hacked sites to malware operations. The botnet has been active since October 2021, and most of its infected sites run a CMS like Joomla, WordPress, or others.
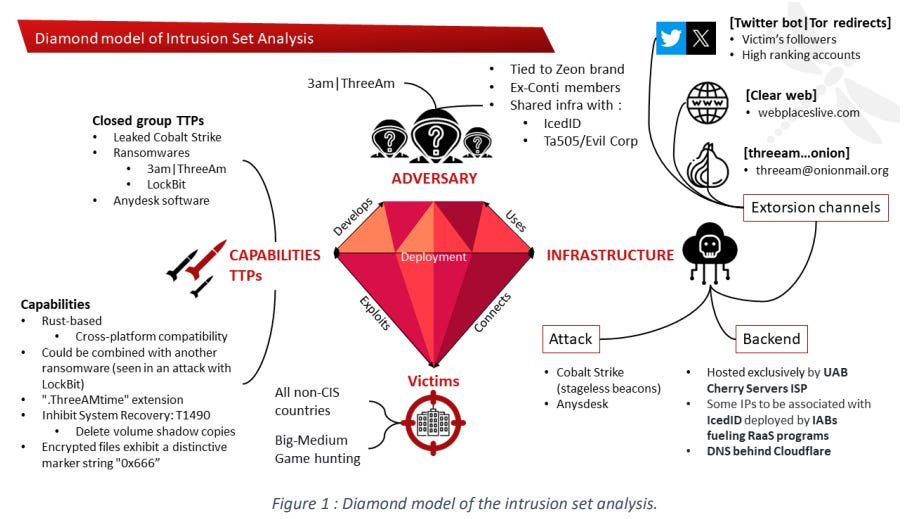
ThreeAM (3AM) ransomware: French cybersecurity firm Intrinsec has linked the new ThreeAM (3AM) ransomware operation to the Royal ransomware, an offshoot of the old Conti gang.
"We assess with a low to medium confidence that, although ThreeAM intrusion sets seem to be a less sophisticated subgroup of Royal, displaying lesser operational security, it could make an impact with a high rate of attacks."
Sponsor Section
A deep dive into what's new with Material Security's Phishing Protection product: New detections, response UX boosters, and more actionable reports.
APTs, cyber-espionage, and info-ops
UNC3886: Google's Mandiant division says that a VMWare vulnerability patched in October of last year was secretly exploited in the wild by Chinese hackers since late 2021. Mandiant linked the attacks to a group it tracks as UNC3886. The group has a long history of going after devices that cannot run EDR security products, allowing their attacks to go undetected for longer. When it patched the vulnerability (CVE-2023-34048) in October, VMWare wasn't aware of active exploitation but released patches even for end-of-life devices.
Vulnerabilities, security research, and bug bounty
German software engineer fined: A German court has fined a software developer €3,000 for using hardcoded credentials he found in a software's source code to access the vendor's database. The developer reported the hardcoded credentials to the vendor and the fact that the database was leaking details on 700,000 of its customers. Instead of thanking the developer, the vendor filed a complaint with the police. A German judge ruled that even if the credentials were exposed in cleartext, the developer was in the wrong for using them. [German coverage in WordFilter/English summary here]
MiraclePtr: Google says the MiraclePtr security feature that the company added to Chrome has mitigated 57% of use-after-free vulnerabilities in the browser's privileged processes, 7% over the 50% estimate its engineers were anticipating in 2022 when they first developed the technology.
Ivanti zero-days update: Security researchers from Assetnote have found new ways to exploit the recent Ivanti zero-days (CVE-2023-46805 & CVE-2024-21887) on older versions of the Connect Secure firmware. According to GreyNoise, exploitation of these zero-days has extended from a Chinese APT to cryptomining botnets. According to Volexity, there are now more than 2,100 compromised hosts.
Chrome bug: Exodus has published a technical write-up on CVE-2024-0517, an out-of-bounds write code execution in Chrome's V8 engine that was patched last week.
Jinja2 vulnerability: There's a major Jinja2 vulnerability that's said to impact thousands of Python projects. Tracked as CVE-2024-22195, the vulnerability is an XSS bug. Since Jinja2 is a template engine, you'll find this one all over the place and in all sorts of flavors.
Infosec industry
New tool—BlueTuxedo: Software engineer Jake Hildreth has released BlueTuxedo, a tool to find and fix misconfigurations in Active Directory-integrated DNS. Last year, Hildreth also released Locksmith, a tool to detect and fix common misconfigurations in Active Directory Certificate Services.
New tool—LogBoost: Varonis security researcher Joseph Avanzato has released LogBoost, a tool designed to help DFIR operators parse and enrich logs.
New tool—Pulse-Meter: Security researcher Rich Warren has released Pulse-Meter, a tool to parse Ivanti Connect Secure system snapshots for new IOCs related to the exploitation of the CVE-2023-46805 and CVE-2024-21887 zero-days.
Tool update—TweetFeed: After going down for several months, the TweetFeed website is back. The site collects IOCs shared on Twitter.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how Stuxnet was an 'inevitability gamechanger,' how much we now know about the operation, and how much the Dutch government should have known at the time.